Break down data silos to prioritize true exposure
Security teams rely on siloed tools that score risks differently, making it hard to see the big picture. Disconnected data delays action and makes it difficult to prioritize the exposures that truly matter.
Use context across the organization to pinpoint top exposures
Reduce the noise and blend technical and business context for better exposure prioritization across your dynamic attack surface.
Prioritize and manage critical exposures across domains
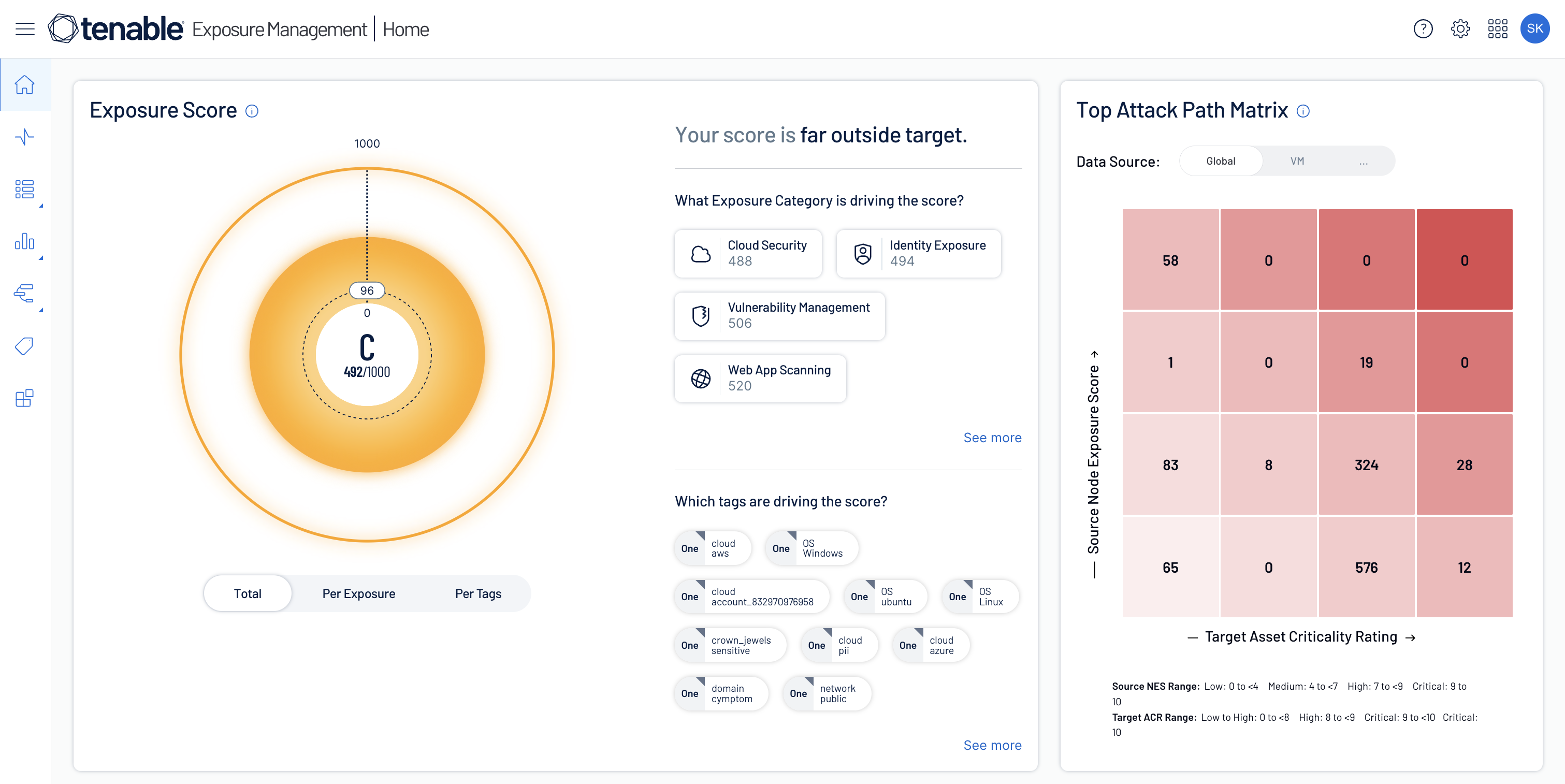
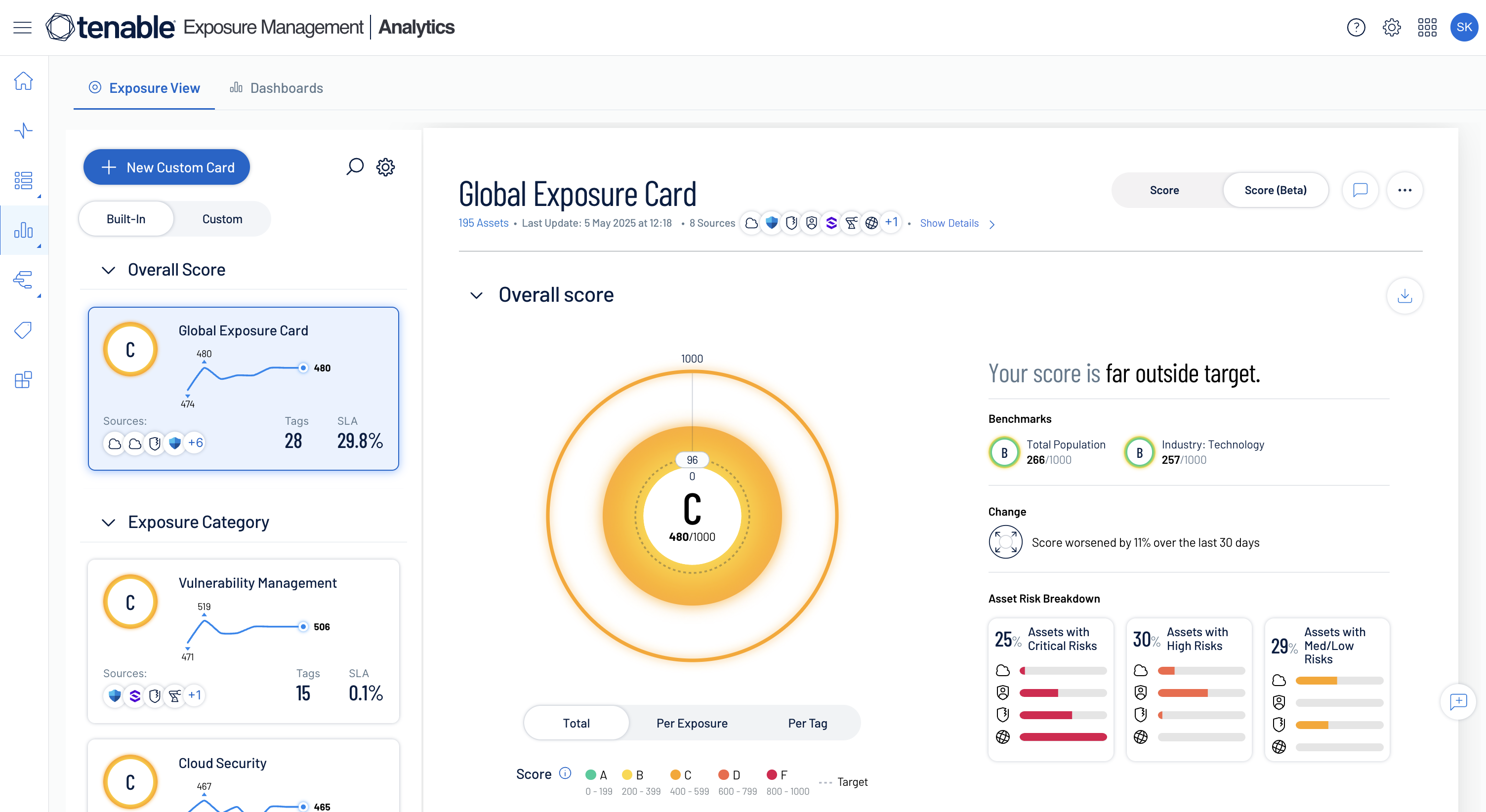
Begin with a top-down view of exposure
Ensure exposure analysts have a fully integrated, top to bottom view of cyber exposure -- from critical business services and processes, down to supporting assets, identities and risks.
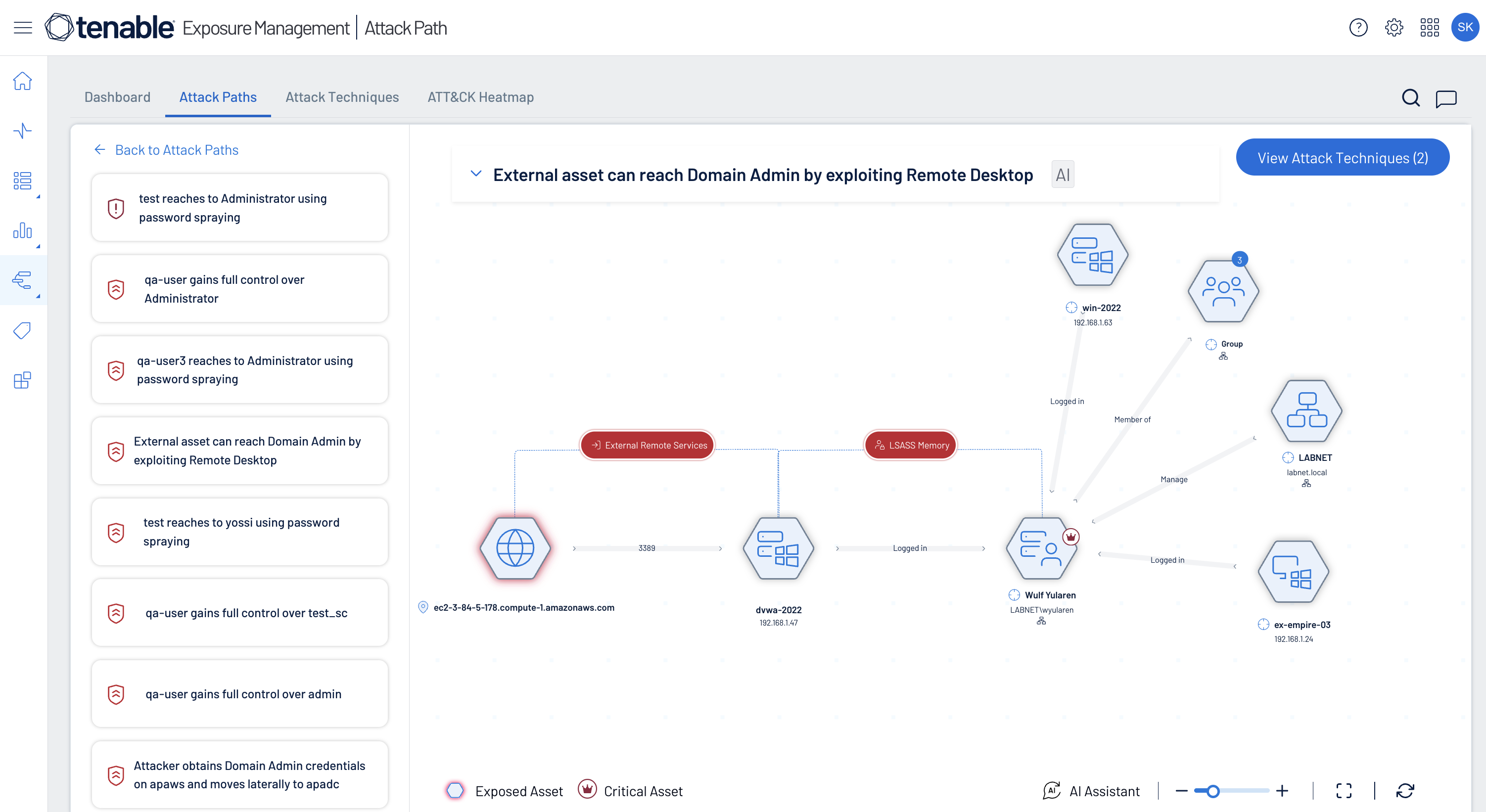
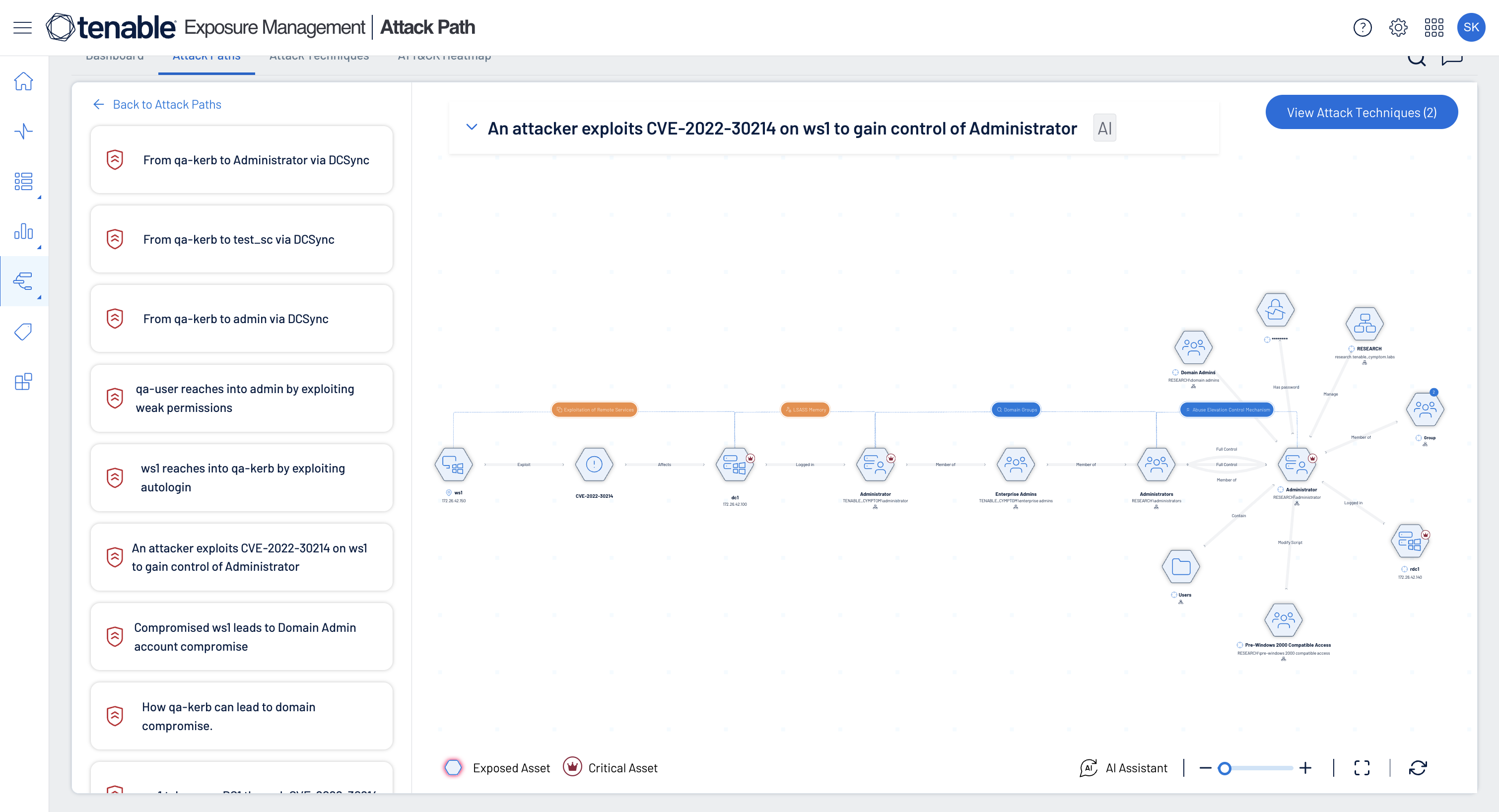
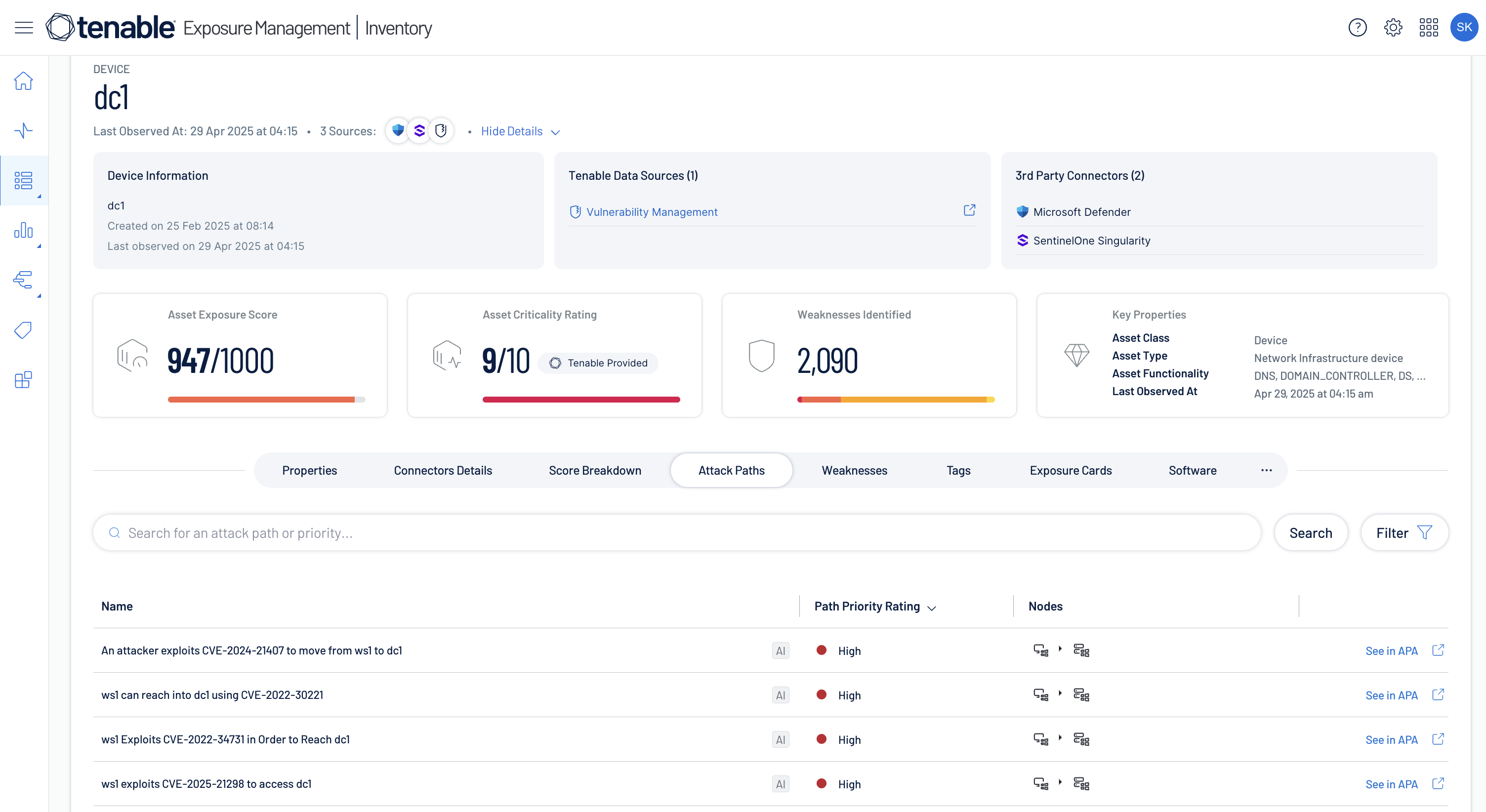
Stay a step ahead of attackers
Proactively visualize attack paths that lead to your critical business assets, identify choke points and close exposures before attacker's can exploit them.
Gain holistic risk prioritization
Unify data from Tenable sensors and other security tools for a comprehensive, big-picture view of risk, with normalized scoring for consistent cross-domain prioritization.
Accelerate insights powered by AI
Leverage ExposureAI and machine learning to prioritize cyber risk, accelerate analysis and drive faster decision-making for improved security outcomes.
Explore how Tenable One can help you
-
Simplify risk insights
Use business-aligned exposure insights for proactive risk mitigation and strategic alignment with your organization’s priorities.
Learn more about exposure analytics -
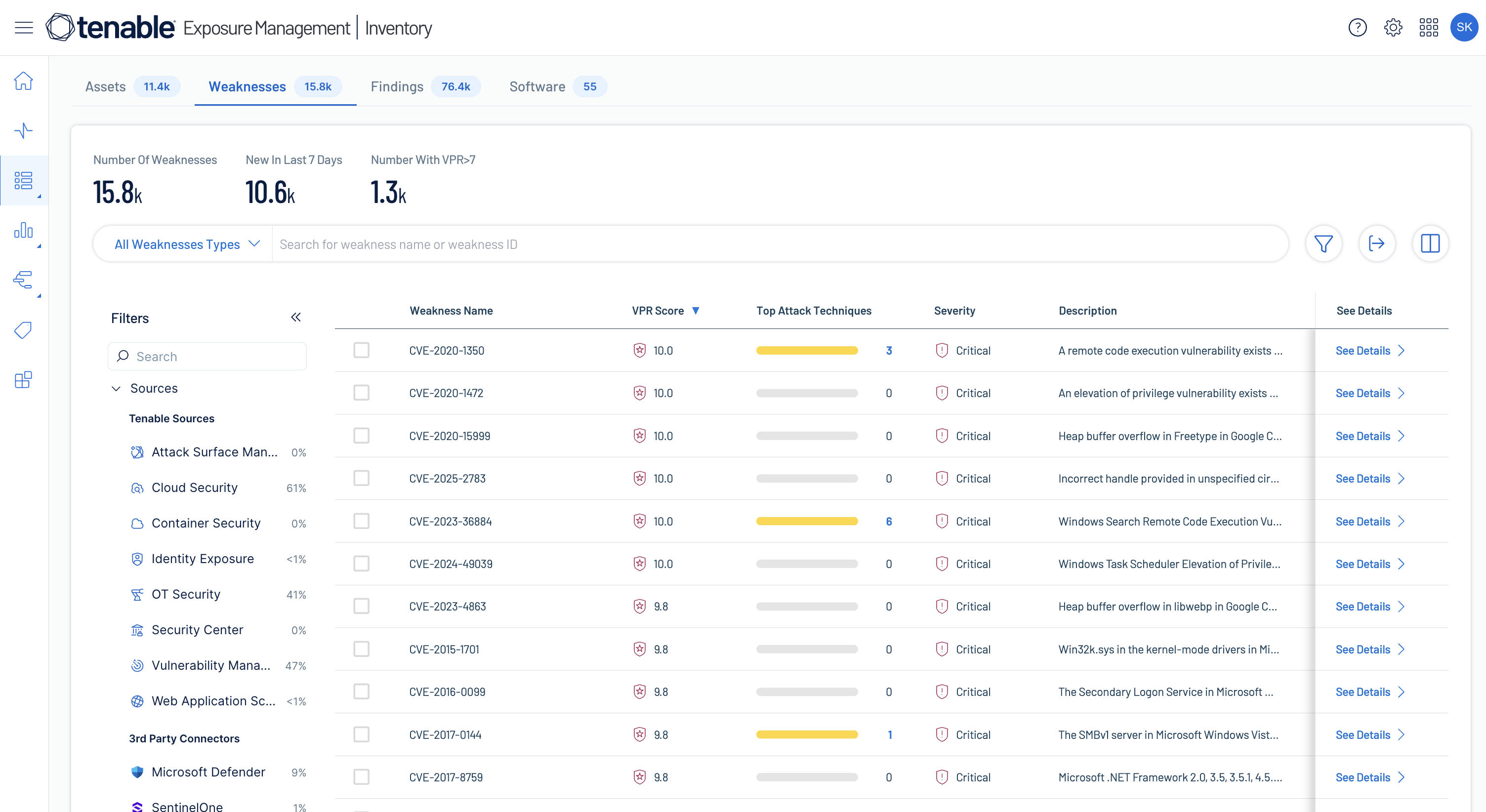
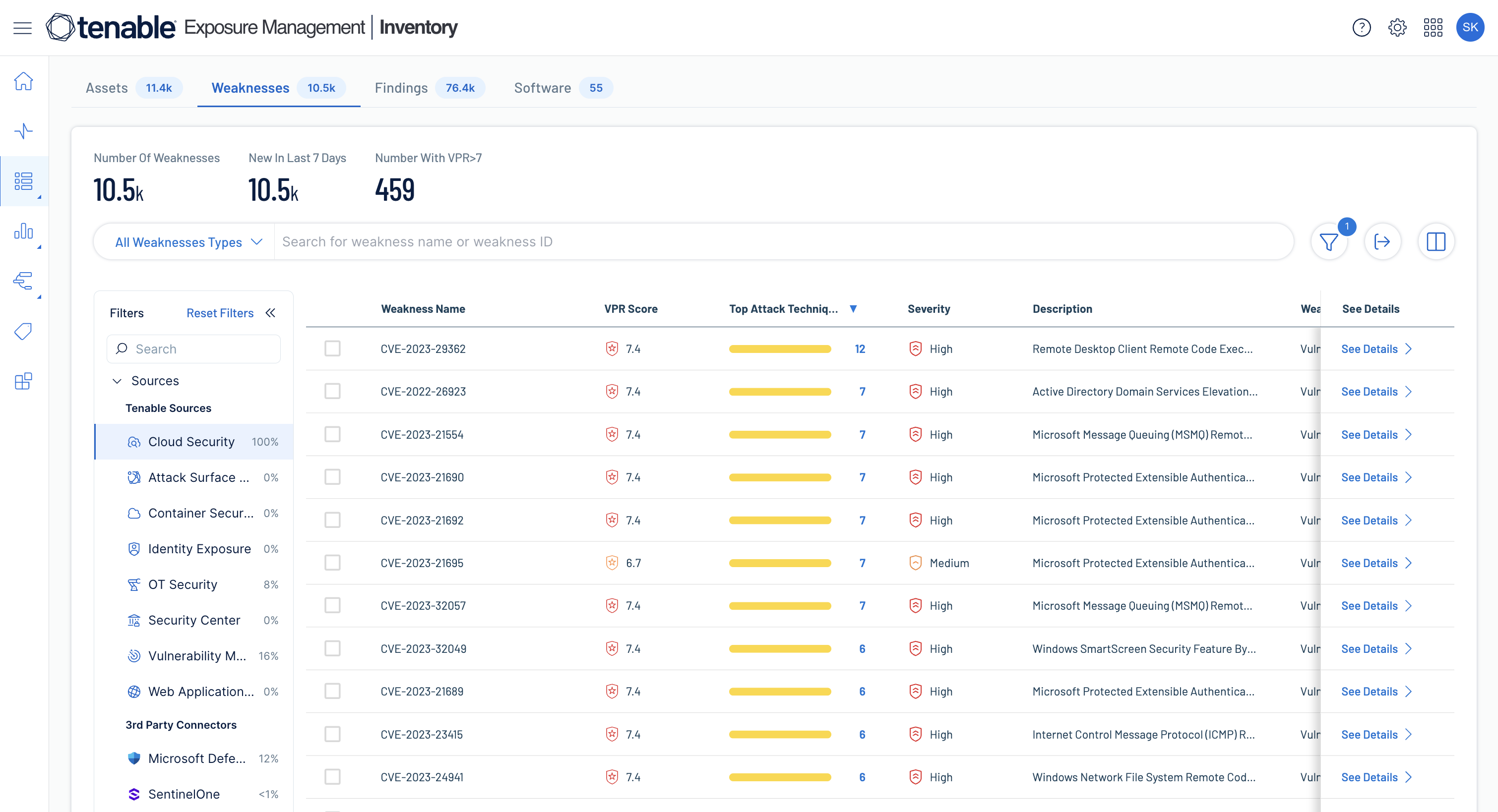
Know your attack surface
Get complete, contextualized asset visibility across your entire attack surface to unify risk assessments for faster remediation.
Learn more about asset inventory -
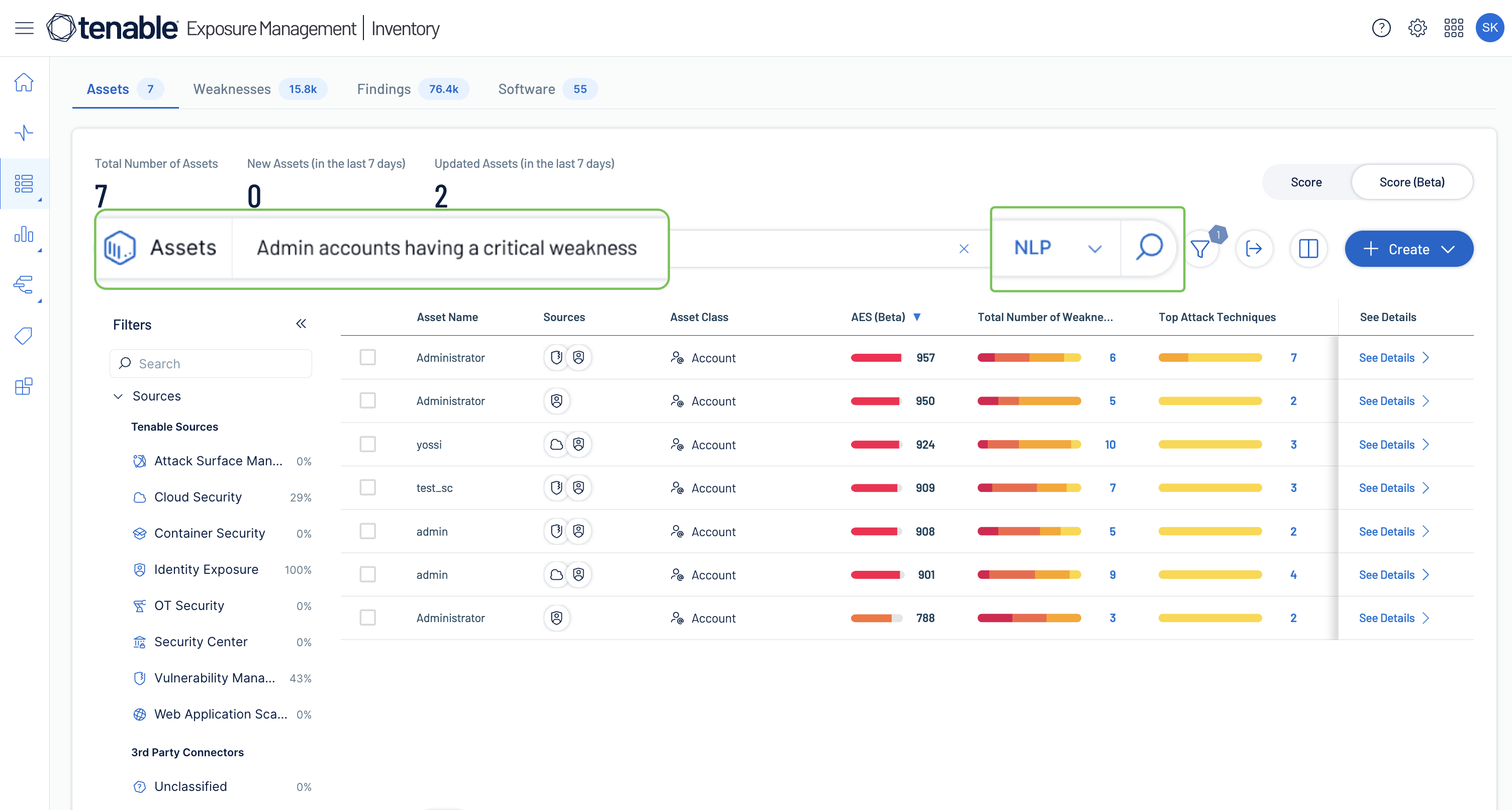
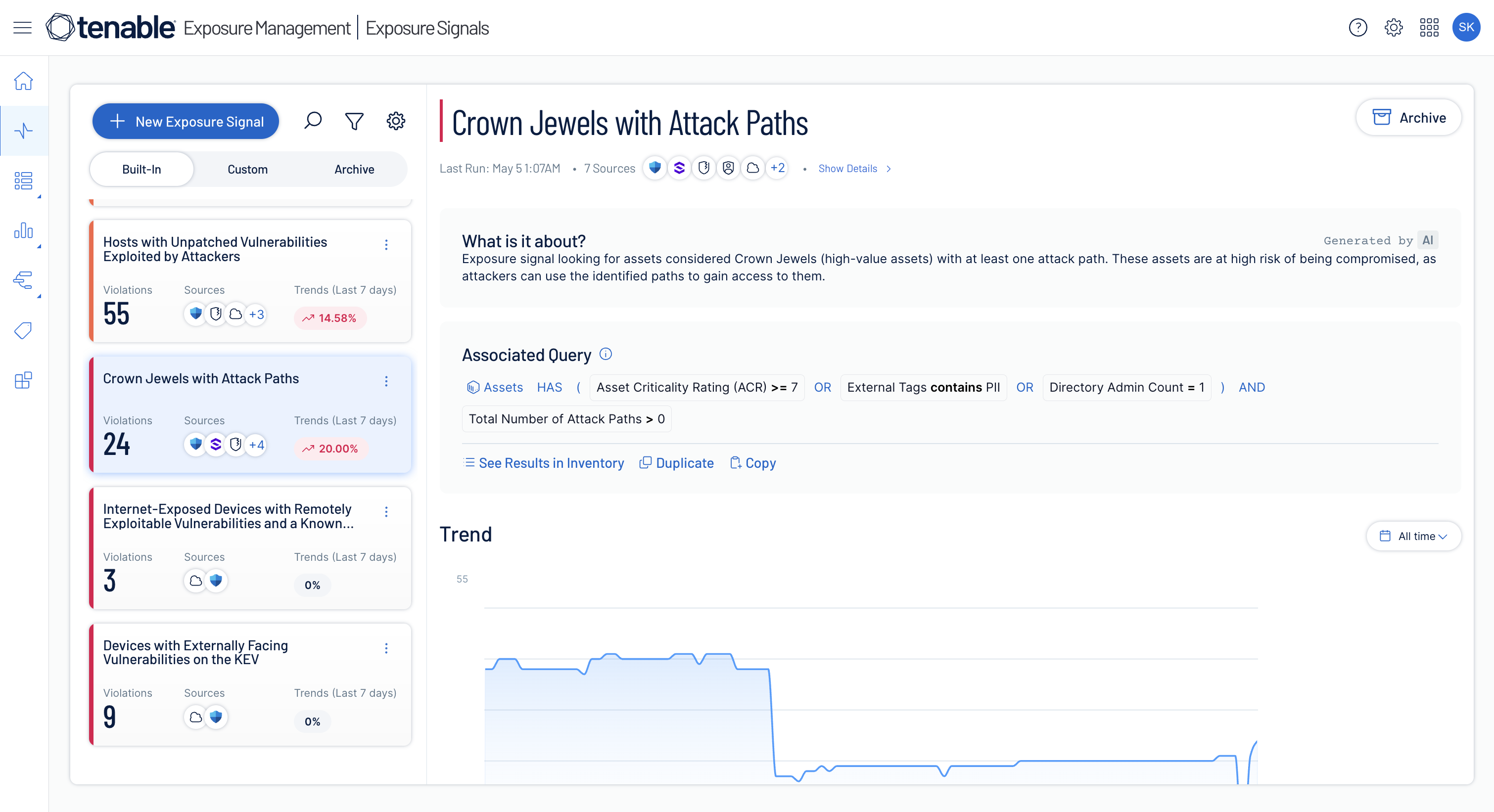
Prioritize exposures that matter
Normalize risk scoring across domains to pinpoint critical attack paths and toxic risk combinations, ensuring prioritized remediation aligned with business needs.
-
Streamline risk management
Use a dynamic policy engine to map and track risks, enabling tailored hygiene policies and rapid violation prioritization.
Learn more about cyber hygiene -
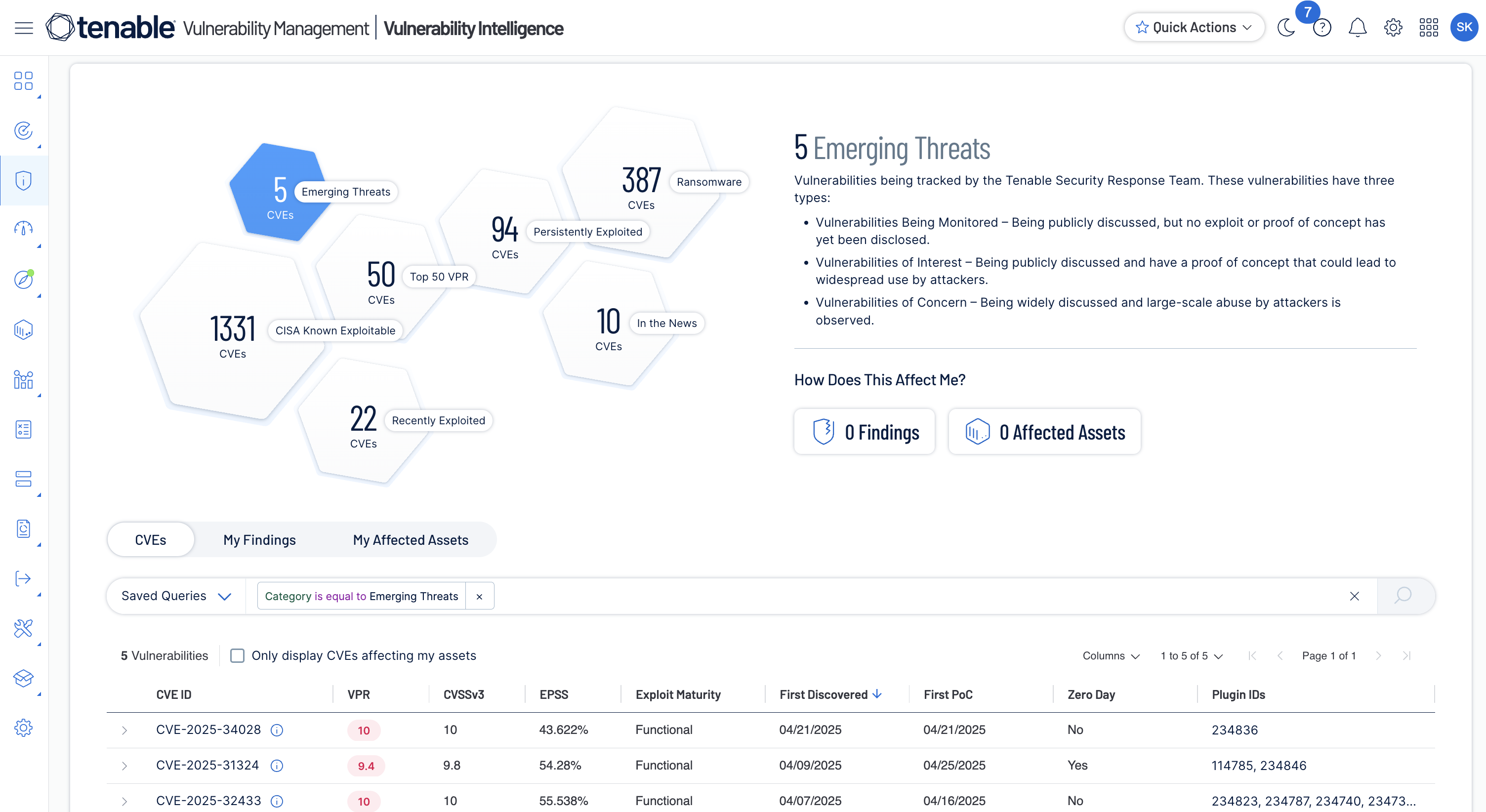
Respond to emerging threats
Track exposures in real time with historical threat context to streamline vulnerability prioritization and remediation efforts.
Learn more about emergency response -
Accelerate threat analysis
Unify asset visibility and contextual risk intelligence to accelerate investigations while reducing response time, tuned for all roles.
Learn more about threat investigation
Realize better outcomes with Tenable One
Tenable One customers see measurable improvements in security posture and business outcomes.
with technology
Related resources
Get Started with Tenable One
Tenable One has helped our engineers reduce the time spent on manual tasks by 75%, which allows them to focus on actual engineering work.
- Tenable Cloud Security