What is an exposure assessment platform (EAP)?
Last updated | January 27, 2026 |
Why your modern attack surface needs an EAP
Your security tools show you thousands of problems. An exposure assessment platform shows you the one story that matters: how an attacker will breach you. Seeing that full story is the key to preventing it.
Table of contents
- EAP defined
- What is the role of EAPs in a CTEM program?
- What use cases do EAPs support?
- Which top exposure management vendors have EAPs?
- What security challenges drive EAP adoption?
- How are EAPs different from traditional proactive security tools?
- The evolution from vulnerability management to exposure management
- What are the key differences between exposure assessment and vulnerability assessment?
- What are the key differences between exposure management and vulnerability management?
- EAP capabilities: How does an exposure assessment platform work?
- Selecting the right EAP: What to look for in an exposure assessment platform
- How Tenable EAP delivers a unified view of exposure
- Frequently asked questions about exposure assessment platforms
- Disclaimers
- EAP resources
- Exposure Assessment Platforms
EAP defined
“Exposure assessment platforms (EAPs) continuously identify and prioritize exposures, such as vulnerabilities and misconfigurations, across a broad range of asset classes. They natively deliver or integrate with discovery capabilities, such as assessment tools, that enumerate exposures, like vulnerabilities and configuration issues, to increase visibility." - Gartner Peer InsightsTM
An exposure assessment platform (EAP) is also commonly referred to as an exposure management platform or continuous threat exposure management (CTEM) platform. Gartner® created the EAP term to refer to a specific set of tools that support a CTEM program.
"EAPs use techniques like threat intelligence (TI) to analyze an organization’s attack surfaces and weaknesses, and prioritize treatment efforts for high-risk exposures by incorporating threat landscape, business and existing security control context. Through prioritized visualizations and treatment recommendations, EAPs help provide direction for mobilization, identifying the various teams involved in mitigation and remediation. EAPs are primarily delivered as self-hosted software or as a cloud service, and may use agents for exposure information collection.”
What is the role of EAPs in a CTEM program?
An effective exposure assessment platform helps shift your security program from a reactive stance to a proactive, exposure-centric approach. It delivers unified visibility and actionable context to support a CTEM process and program.
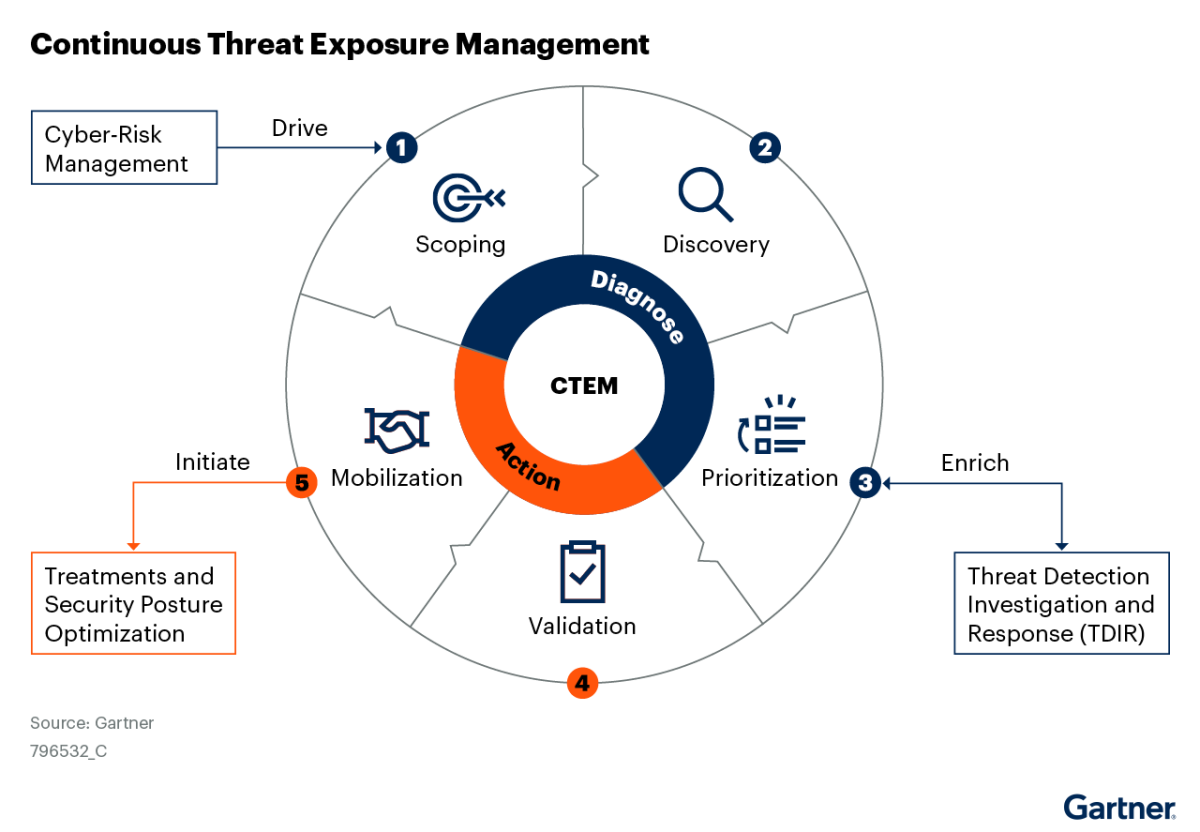
CTEM programs consist of five key stages:
1. Scoping to define which systems, assets and business processes to assess, starting with the most critical.
2. Discovery to identify all assets and risks, including vulnerabilities, misconfigurations and rogue systems across your environment.
3. Prioritization to rank exposures by likelihood of exploitability and potential business impact to focus efforts where they matter most.
4. Validation to test and simulate attacks to confirm which exposures are real threats and refine your response.
5. Mobilization to act on validated risks by remediating, mitigating or isolating them through coordinated response across teams.
EAPs typically support three of the five stages, although that can vary somewhat depending on the specific EAP vendor platform.
EAPs offer:
- Discovery of your assets and risks.
- Prioritization of exposure in context based on potential impact.
Mobilization of teams with remediation guidance and metrics to track program effectiveness and optimize investments.
What use cases do EAPs support?
Below is an overview of how EAPs enable key use cases:
Discovery
- Build a trusted, unified asset inventory with rich context that covers vendor, type, software, configuration, associated risks, users and more across your entire attack surface.
- This step supports deeper insights through relationship mapping (e.g., attack paths, business connections) for more informed decisions.
- Cyber hygiene with pre-built policies to surface common hygiene issues and customizable options to uncover unique risk patterns.
- Helps teams track hygiene trends, investigate impacted assets and prioritize remediation.
Prioritization
- Exposure prioritization applies consistent scoring across domains while correlating asset, identity and risk data to highlight viable attack paths.
- Enables early mitigation of threats targeting high-value assets before breaches begin.
Mobilization
- Exposure analytics to generate business-aligned dashboards and reports that quantify cyber exposure and track key performance indicators (KPIs) to improve communication with stakeholders and guide strategic investment.
- Emergency response for real-time visibility into zero-day and critical threat events, down to the level of affected and remediated assets. Includes integrated threat intelligence from hundreds of sources to support rapid response.
- Threat investigation to empower threat hunters and incident response teams with detailed asset and risk intelligence, including attack path data and potential business impact, to accelerate investigations and remediation.
Which top exposure management vendors have EAPs?
The 2025 Gartner Magic Quadrant (MQ) for Exposure Assessment Platforms (EAPs) evaluates 20 major vendors that help organizations continuously identify, prioritize and reduce cyber exposures across the attack surface.
Gartner positions each vendor in the quadrant based on performance across two key axes:
Evaluation criteria:
- Ability to execute: Measures how well a vendor delivers reliable products, meets customer needs and performs in today’s market.
- Completeness of vision: Reflects the vendor’s understanding of future market requirements and the strength of its strategy to meet them.
These are based on detailed evaluation criteria and determine which of the four quadrants each vendor occupies.
Magic Quadrant placement
- Leaders deliver strong execution and a well-articulated, forward-looking vision.
- Challengers excel in current capabilities but lack a compelling long-term vision.
- Visionaries bring innovative ideas but have yet to fully demonstrate execution strength.
- Niche players focus on specific segments or regions, but are limited in scale or roadmap maturity.
Tenable among 2025 Magic Quadrant Leaders
Among the EAP vendors recognized as Leaders in 2025 are Tenable, Rapid7 and Qualys.
Tenable is at the forefront, recognized for its comprehensive exposure management capabilities through the Tenable One Exposure Management Platform.
Tenable One enables your organization to see your attack surface from a threat actor’s perspective by providing:
- A complete, unified inventory of all assets and potential access points.
- Visibility into attack paths and toxic risk combinations that adversaries could exploit
- Business-aligned risk context to identify which threats matter most
- The ability to proactively dismantle attack chains before attackers gain a foothold
The scope of cross-domain visibility and contextual risk-based prioritization that Tenable offers are key reasons it earned a leadership position in Gartner’s analysis.
What security challenges drive EAP adoption?
To effectively secure your organization, you must look beyond just IT assets. Your true attack surface is a complex, interwoven map of IT, cloud infrastructure, operational technology (OT), and identity systems.
These domains are not isolated. They are deeply connected and create complex attack paths that adversaries can exploit.
A compromised identity, for example, could give an attacker access to your critical cloud data or the ability to disrupt physical OT processes.
To manage risk, you first need a holistic view of how these environments converge and which new exposures they create.
How are EAPs different from traditional proactive security tools?
Your security stack likely includes a variety of trusted and specialized solutions: vulnerability management, cloud native application protection platform (CNAPP), web app scanning, identity and access management and so on.
These proactive security tools focus on specific technology domains, IT, cloud, identities, OT, IoT, applications, and risk types like vulnerabilities, misconfigurations and permissions.
According to a recent (ISC)² Cybersecurity Workforce Study, security teams are often stretched thin, and this siloed approach forces your analysts to manually connect dots across different consoles. This process is slow, inefficient and error-prone.
Attackers, however, see your organization as one interconnected system and are experts at exploiting the security gaps between your siloed defenses. It’s precisely the challenge an EAP solves.
Data from the Verizon Data Breach Investigations Report consistently shows that attackers don't just use the highest-scoring vulnerabilities. They use the ones that give them the easiest path to their objective.
Without the context of asset criticality and attack path analysis that an EAP gives you, your team risks spending valuable time fixing issues that don't meaningfully reduce your business risk.
EAPs unify data across disparate tools for a unified view of your attack surface. They map asset, identity and risk relationships to give you a step-by-step visualization of attack paths and MITRE techniques attackers can exploit to compromise crown jewel assets.
Armed with the attacker’s perspective, your security analysts can focus on breaking the attack paths that can significantly impact your organization.
The evolution from vulnerability management to exposure management
One of the most common questions raised by security leaders looking to implement a CTEM program is: Where do we start?
While EAPs provide the tooling needed to support an exposure management program, there are also important people and process considerations.
Most established organizations have an existing vulnerability management program, often ahead of other security domains like the cloud or OT. As a result, vulnerability management programs are typically more mature than others. For this reason, industry analysts recommend evolving your vulnerability management program to become an exposure management program.
To do this effectively, you should expand the mission of your team to include all asset and risk types, security policies and workflow across your attack surface. This is an evolution from siloed vulnerability management practices to cross-domain exposure management as the core responsibility of your vulnerability management team. The intent is to centralize how your organization addresses critical functions to free domain teams to focus on their core competencies.
Want to know more? Check out this blog, “Who owns threat and exposure management in your organization?”
EAPs play a critical role in this evolution by aggregating data from all your tools into one place and adding critical technical and business context needed to identify exposure across the attack surface. Exposure management teams can then provide targeted views of exposure, recommended actions, reporting and metrics aligned to individual owners and business units.
This journey from traditional vulnerability management to a comprehensive exposure management program is one of the most important strategic shifts your security organization can make.
What are the key differences between exposure assessment and vulnerability assessment?
Vulnerability assessment identifies and patches known vulnerabilities like software flaws (common vulnerabilities and exposures (CVEs)) on IT assets. Its goal is to find and fix individual weaknesses based on technical severity.
Exposure assessment is broader. It looks beyond CVEs to include misconfigurations, identity issues and potential attack paths. Exposure assessment includes the full context of how an attacker could combine these exposures to cause a breach and helps you prioritize them based on actual risk to your business.
What are the key differences between exposure management and vulnerability management?
| Category | Vulnerability Management | Exposure management |
| Primary focus | Identifying and patching known CVEs | Holistically managing all exposures that could lead to a breach |
| Score of coverage | Software vulnerabilities (CVEs) on IT assets | Includes CVEs plus more |
| Asset Types | Primarily IT (servers, endpoints) | IT, OT, cloud, IoT, identity, external attack surface |
| Risk context | Limited to CVSS score, sometimes asset criticality | Includes business impact, exploitability, control gaps, relationships |
| Prioritization | Based on severity + asset value | Prioritizes based on attack paths and potential to compromise crown jewels |
| Validation | Rarely validated; assumes vulnerability = exploitable | Supports validation (e.g. choke point analysis, attack simulation, purple teaming) |
| Remediation support | Often manual or ticket-based | Automated workflows with ownership mapping, SLA tracking, and AI remediation suggestions |
| Program objective (primary) | Patch fast to reduce known vulnerabilities | Break attack chains and reduce break likelihood across all exposure types |
| Measurement of success | Patch fast to reduce known vulnerabilities | Business-aligned KPIs and board-level risk posture visibility |
Get the IDC Worldwide Device Vulnerability and Exposure Management Market Shares report.
EAP capabilities: How does an exposure assessment platform work?
An effective exposure assessment platform moves your security program from reactive to proactive, enabling continuous security posture validation.
Now, let's explore how EAP capabilities come together to support an overall program:
See everything, everywhere
The foundational capability of an exposure assessment platform gives your security teams a comprehensive and continuously updated asset inventory. It’s more than traditional network scans. It includes discovering IT assets, cloud services, web apps, containerized environments and critical identity systems.
EAPs also integrate directly with domain-specific security tools to collect relevant asset and risk information. It aggregates and normalizes this data to create a single, unified view of all assets across your attack surface to reduce blind spots attackers often exploit.
Security teams can run specific AI queries using natural language search to identify common security hygiene issues, such as missing agents, end-of-life software, missing multi-factor authentication (MFA), or any combination of unique attributes.
Separate exposures from noisy findings that static vulnerability scores create
Once an EAP discovers an asset, it analyzes vulnerabilities, misconfigurations and excessive permissions. It enriches the analysis with layers of critical context.
It aggregates risk data for each asset and normalizes it across security domains to come up with an overall asset exposure score (AES).
AES factors in key variables, including an asset's business criticality, accessibility by threat actors, the exploitability of a specific weakness, such as CISA Known Exploited Vulnerabilities (KEV) Catalog and up-to-the-minute threat intelligence. It distills this down to a single, understandable metric that communicates asset risk at a glance. This makes it possible to quickly understand which assets pose the greatest overall risk.
This is where an exposure assessment platform differentiates itself. Instead of just identifying assets and weaknesses, it also maps relationships.
Teams can instantly visualize the asset, identity and risk relationships. These attack paths allow an attacker to leverage a series of seemingly low-risk exposures to reach a crown-jewel asset.
It business-aligns and prioritizes attack paths so your teams can focus on fixing exposures that pose the highest potential risk to your organization.
AI-powered remediation guidance finds specific choke points in attack paths. By understanding these chains, which often mimic common adversary TTPs, and choke points, your team can proactively disrupt the most likely breach scenarios before they happen.
EAPs also integrate with technologies like breach and attack simulation and pen testing tools, a category Gartner refers to as adversarial exposure validation (AEV) (Gartner, Market Guide for Adversarial Exposure Validation, By Eric Ahlm, Dhivya Poole et al., 11 March 2025). You can then actively test and validate if attack paths are a theoretical risk or a real, exploitable threat to your environment.
Act on and quantify exposure and communicate impact to stakeholders
Once you have validated an exposure, EAPs play a critical role in orchestrating the remediation lifecycle. The platform can automatically determine the appropriate asset owner and trigger workflow actions like opening tickets in tools like JIRA, ServiceNow, or Slack.
Choke point details and AI-driven remediation guidance accelerate response by suggesting appropriate patches, configuration changes or compensating controls.
EAPs continuously track the remediation status, monitor SLA compliance and ensure accountability across teams.
Finally, an EAP can help your organization with cyber risk quantification to answer the critical question, “How secure are we?”
Instead of presenting leadership with tactical KPIs, such as the number of patched vulnerabilities, EAPs provide a business-aligned cyber exposure score.
You can then track exposure trends over time, compare performance across business units or peer organizations and benchmark against internal targets or industry standards.
Business-aligned dashboards make it easy to communicate risk posture to executives and boards and justify required investments.
Learn more in our blog, “How Exposure Management Has Helped Tenable Reduce Risk and Align with the Business.”
Selecting the right EAP: What to look for in an exposure assessment platform
There are many important criteria to look for in an EAP:
- Buyer guides, like the Tenable Buyer Guide for Exposure Management Platforms, detail component markets and required features that comprise exposure assessment platforms along with other strategic considerations for platform selection.
- Analyst reports like the 2025 Gartner Magic Quadrant for Exposure Assessment Platforms and IDC MarketScape: Worldwide Exposure Management, 2025 Vendor Assessment are strong resources for looking at a wide range of criteria beyond platform capabilities.
Buyer's checklist: Exposure assessment platform
- Comprehensive coverage: Unified view across IT, cloud, identity, and OT.
- Exposure prioritization: Context-aware risk scoring and attack path analysis.
- Actionable reporting: Clear remediation guidance and business-level dashboards.
- Seamless integrations: Robust APIs for SIEM, SOAR, and ITSM platforms.
How Tenable EAP delivers a unified view of exposure
If you want to move away from a reactive security approach to a proactive strategy, you must turn exposure management best practices into a practical reality. That requires the right exposure assessment platform.
Tenable delivers this capability through a comprehensive approach that helps your organization build and execute a modern, proactive program of continuous threat exposure management (CTEM).
See how Tenable One can give you a unified and contextual view of exposure across your entire attack surface. Request a demo today.
Frequently asked questions about exposure assessment platforms
As exposure assessment platforms become more common in cybersecurity, questions will arise which many security professionals are frequently asking. Let's take a look and answer some of those questions:
What is the main difference between exposure management and vulnerability management?
The main difference between exposure management and vulnerability management is that exposure management is a holistic strategy that assesses all types of assets, weaknesses and their relationships for a prioritized view of attack paths and potential business exposure. Vulnerability management focuses on finding and prioritizing individual CVEs without this broader context.
How does an exposure assessment platform help with attack surface management?
An exposure assessment platform helps with attack surface management by providing a comprehensive view of assets across your attack surface, their associated risks and relationships and contextual insights to optimize security hygiene and reduce potential business exposure.
What types of exposures can EAPs find?
EAPs can find a wide range of exposures, including software vulnerabilities (CVEs), cloud misconfigurations, insecure user permissions, exposed web application services and flaws in identity systems, to name a few.
Why is CVSS not enough for prioritization?
A CVSS score focuses on technical severity and lacks important variables that enrich prioritization, such as accessibility, exploitability, threat intelligence and business context. EAPs factor in these additional variables.
How do exposure assessment platforms help CISOs?
An EAP translates complex technical data into clear business risk metrics so CISOs can more effectively communicate security and business risk to the board and executives to justify security investment.
See how Tenable One can give you a unified view of your entire attack surface. Request a demo today.
Disclaimers
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally, PEER INSIGHTS is a registered trademarks of Gartner, Inc. and/or its affiliates and are used herein with permission. All rights reserved.
Gartner Peer Insights content consists of the opinions of individual end users based on their own experiences, and should not be construed as statements of fact, nor do they represent the views of Gartner or its affiliates. Gartner does not endorse any vendor, product or service depicted in this content nor makes any warranties, expressed or implied, with respect to this content, about its accuracy or completeness, including any warranties of merchantability or fitness for a particular purpose.
This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from Tenable.
EAP resources
Exposure Assessment Platforms
Cybersecurity news you can use
- Tenable One
