TL;DR: The Tenable Research 2020 Threat Landscape Retrospective

Tenable’s Security Response Team takes a look back at the major vulnerability and cybersecurity news of 2020 to develop insight and guidance for defenders.
Søren Kierkegaard, the Danish philosopher, once wrote that “life can only be understood backwards” but “it must be lived forwards.” Tenable’s Security Response Team is tasked with looking at the threat landscape on a day-to-day basis and, while that provides us with the ability to see things in the moment, it’s only when we look back at the year that was that we can see the bigger picture.
As we were finalizing our inaugural 2020 Threat Landscape Retrospective (TLR) report, the most notable cybersecurity event in 2020 — and arguably the last decade — was revealed in December. The breach of SolarWinds and its Orion Platform software captivated our collective attention in the final weeks of 2020. While the full picture of the breach and its impact remains incomplete, we believe that as additional information emerges throughout 2021, our ability to truly grasp the full effects and impact will be realized.
SolarWinds became the most significant event of 2020, but for the broader industry, there are many pressing matters to be addressed, such as the top 5 vulnerabilities exploited throughout 2020. These include three legacy vulnerabilities in virtual private network solutions from Citrix, Pulse Secure and Fortinet. These top 5 vulnerabilities, as well as other key takeaways and insights from the year in vulnerabilities, are outlined in the TLR, which security professionals can use to move forward in 2021 with a greater sense of clarity.
The 2020 Threat Landscape Retrospective
The report begins with an overview of the vulnerability landscape. There were 18,358 new CVEs assigned in 2020, a six percent increase from 2019. From 2015 to 2020, the number of reported CVEs increased at an average annual percentage growth rate of 36.6%.
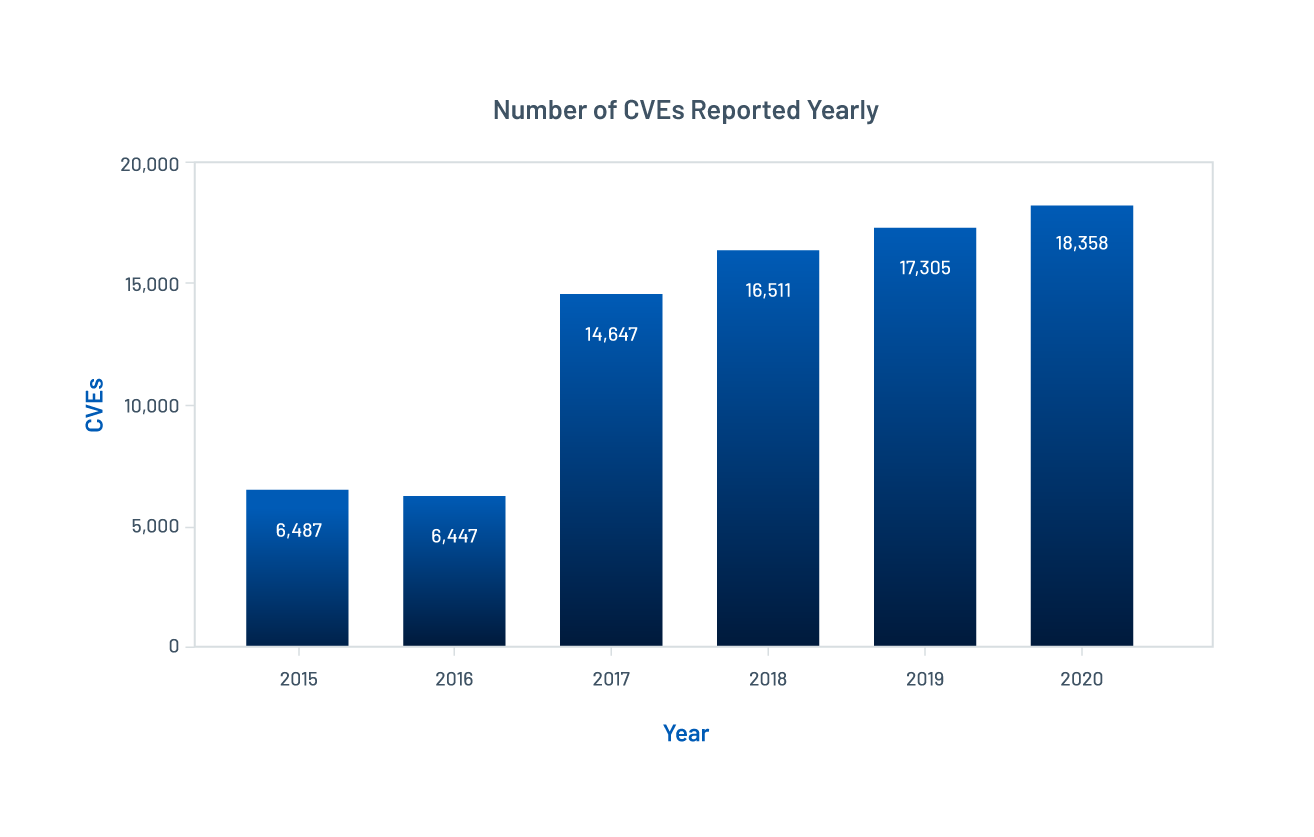
Source: National Vulnerability Database (NVD) as of January 5, 2021
While the numbers are daunting, they don’t really tell the full story. The TLR explores the nuances of vulnerabilities disclosed last year: noteworthy vulnerabilities, whether or not they were branded; zero-day disclosures from attackers and researchers; the whirlwind summer months and all of the challenges brought on by the COVID-19 pandemic.
Next, we explore the threat landscape in 2020. How were attackers leveraging the vulnerabilities disclosed in 2020, and several that were significantly older? Troublingly, the primary theme of the threat landscape was that threat actors are relying on unpatched vulnerabilities in their attacks. This isn’t anything new but this year, government agencies issued several advisories warning about attackers leveraging vulnerabilities that have patches available and yet remain unmitigated. The TLR explores key insights from these government alerts along with ransomware attacks and major breaches throughout the year.
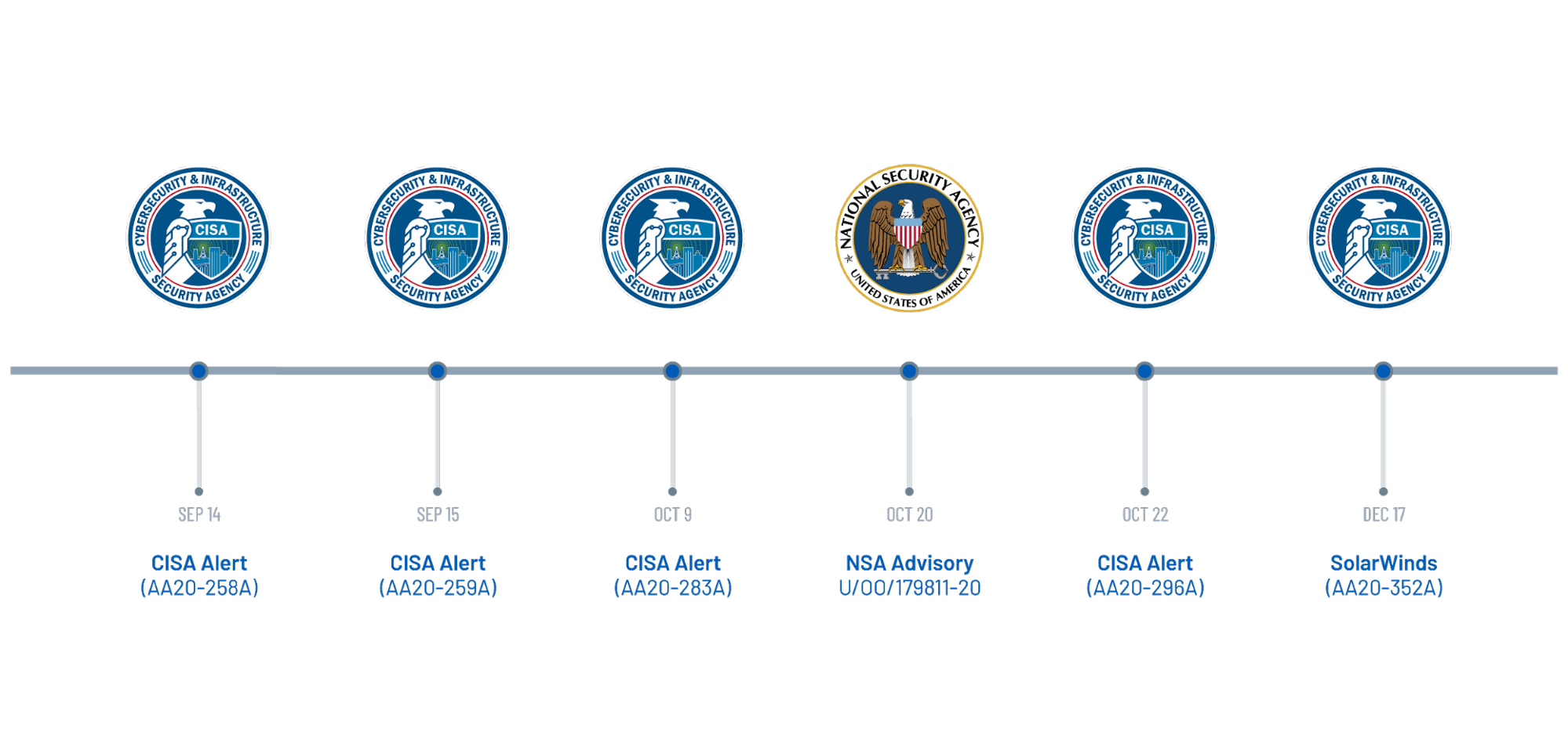 Timeline of Notable Government Alerts in 2020
Timeline of Notable Government Alerts in 2020
The final section of this report will likely be of particular use to security practitioners. It offers a digest of the key vulnerabilities in 2020 — the technical details, whether and how they’ve been exploited, all categorized by vendor or product. If you ever need to describe a vulnerability to a key stakeholder, this is your resource.
How to use Tenable’s 2020 Threat Landscape Retrospective report
- Understand some of the pitfalls from the shift to the remote workforce
- Learn how ransomware gangs are breaching organizations and the tactics they’re employing to extract ransom demands
- Learn some of the common ways data breaches occur and what your organization can do to prevent them from happening
- Identify and patch any of the vulnerabilities referenced in the report
Learn more
- Download the full report here
- Attend the webinar: Tenable Research 2020 Recap and Defender’s Guidance for 2021
- Research Reports
- Threat Intelligence
- Vulnerability Management

