The Exploitation of Exploit Frameworks
At the recent Gartner Security and Risk Summit, one of the presenters recommended using an exploit framework to prioritize vulnerabilities. The idea is to use the exploits to automatically verify vulnerabilities as part of the vulnerability management process. Simple in theory, bad in practice.
Tenable’s developers spend a lot of time tuning our scanning technology to yield accurate and effective results without adversely impacting our customer network infrastructures. Exploiting vulnerabilities works against this and introduces undesired political ramifications for our customers. Nessus is 100% auditing and does not make changes to target systems. Removing the “safe checks” flag will attempt to run limited exploit code in some plugins, but only for the purpose of improving plugin accuracy (typically in lieu of credentialed scanning).
Beyond the politics, exploiting vulnerabilities is just misdirecting remediation efforts. While exploitability information should be a consideration (and is included with Nessus), the availability of automated exploit tools should not dictate prioritization as they represent a very small subset of exploitable vulnerabilities. To confirm this, I setup a matrix dashboard in SecurityCenter Continuous View at a research site:
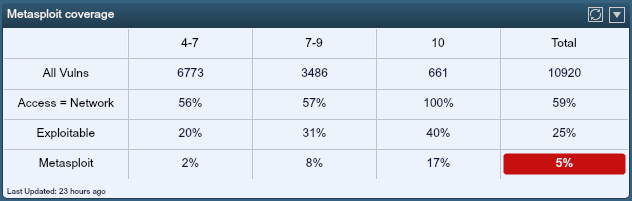
The top line (All Vulns) is the current count of active/passive vulnerabilities for this site split out in columns by CVSS scores. I then filtered for network-based vulnerabilities using reported CVSS factors from the National Vulnerability Database with "AV:N", or Access Vector = Network, as shown in the 2nd line. Additionally, the Tenable research team flags plugins with “public exploit” code available, which is filtered on the third line. Finally, the team also includes references to popular exploit frameworks which are useful to the penetration testing community. This final line reports all the vulnerabilities with exploit code available in the Metasploit platform.
The data illustrates several points. Rows 2-4 are percentages using the first row (All Vulns) as the base. In the first column, we have 6,773 Medium vulnerabilities, of which 56% are network accessible, 20% exploitable, and 2% exploitable in the Metasploit platform. As we move to the right, the numbers increase, which is not surprising as both exploitability and network access are included in the CVSS scoring . However, as you can see, if you were to prioritize using Metasploit capabilities, you would be ignoring a large subset of network accessible/exploitable vulnerabilities.
How does Tenable prioritize vulnerabilities?
What the security analyst needs is more context for vulnerabilities. With the addition of passive scanning, SecurityCenter Continuous View gains awareness of traffic flows on the network and uses this information to place network context on vulnerabilities, or the vulnerability attack paths. More specifically, Tenable’s Passive Vulnerability Scanner (PVS) can identify Internet facing services. When combined with exploitability, these bring true risk exposure into focus. The dashboard below was generated off the same set of vulnerabilities.
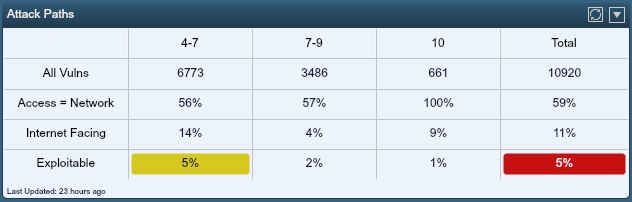
The "Internet Facing" row is the filtered set of vulnerabilities based on Internet exposure. The last row represents exploitable vulnerabilities on servers with Internet exposure, certainly the highest risk vulnerabilities. What is interesting to note is that while the total Internet-facing, exploitable vulnerabilities sees a slight uptick to 5%, the emphasis shifts from critical vulnerabilities to mediums. Without this context, these medium vulnerabilities would most likely be prioritized lower for remediation.
Where does that leave exploit frameworks?
Nessus is used extensively by penetration testers worldwide, but penetration testing can’t be accomplished through tools alone. Effective penetration testing is a methodology that combines several elements of IT security to include human factors. Penetration testers spend a lot of time honing their skills with the execution of current exploit code in a responsible, safe manner. Many standards bodies (PCI, NIST) are catching on to the misuse of automated exploit tools to satisfy penetration testing requirements and are expected to provide definitive guidance that emphasizes methodology over tools.
For genuine penetration testing activities, all of the major exploit frameworks can import Nessus data, and most can launch Nessus scans from directly within the framework. In addition, the PVS collects data that is directly relevant to penetration testing activities. This includes visibility of servers/services beyond engagement scope/timeframe, vulnerability exposure, client-side vulnerabilities, website identification, and more.
Tenable will continue to support the penetration testing community through the continuous improvement of vulnerability and compliance scanning. We know that penetration testing is an important part of a security process that is constantly challenged by advancing technologies and evolving threats, but we also know that it requires skill and responsibility, and doesn't belong in an automated vulnerability management process.