New Nessus Vulnerability Modifications Now Available
Nessus now provides the ability to modify vulnerability findings in scan results. These new granular vulnerability modification options combined with other recent enhancements, including the ability to email actionable reports at the completion of a scan, enhance the power of Nessus for daily vulnerability management.
The vulnerability modification settings provide Nessus users with the ability to change the severity of findings, or hide them completely for a single host, a single scan, all future scans, or a specific time period. Nessus users may wish to modify vulnerability finding for a variety of reasons, including:
- The vulnerability may be mitigated without patching.
- The value or exposure of the vulnerable asset may require a higher or lower vulnerability rating.
- The finding may be a false positive from a non-credentialed scan.
- Time may be needed to remediate a vulnerability in production systems.
Configuration
To modify a finding from an existing report, click the “Modify” button in the upper-right corner of the report details section:
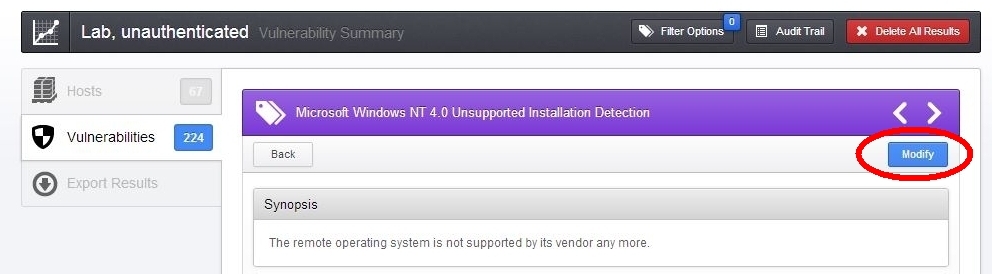
Nessus users can now choose to modify the vulnerability’s severity or hide the result:
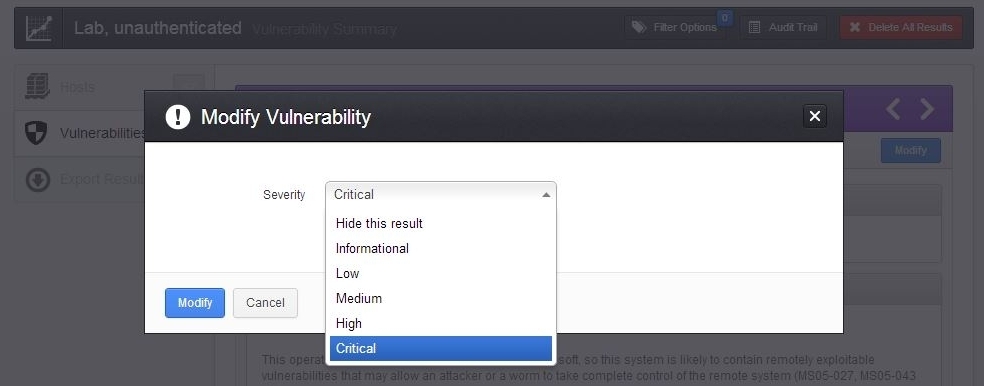
The modification can be applied to the existing report or all future reports, or the change can be set to expire on a specified date. Setting an expiration date is useful for allowing time for remediation of known issues while ensuring the findings are automatically restored to the appropriate severity after the specified remediation period.
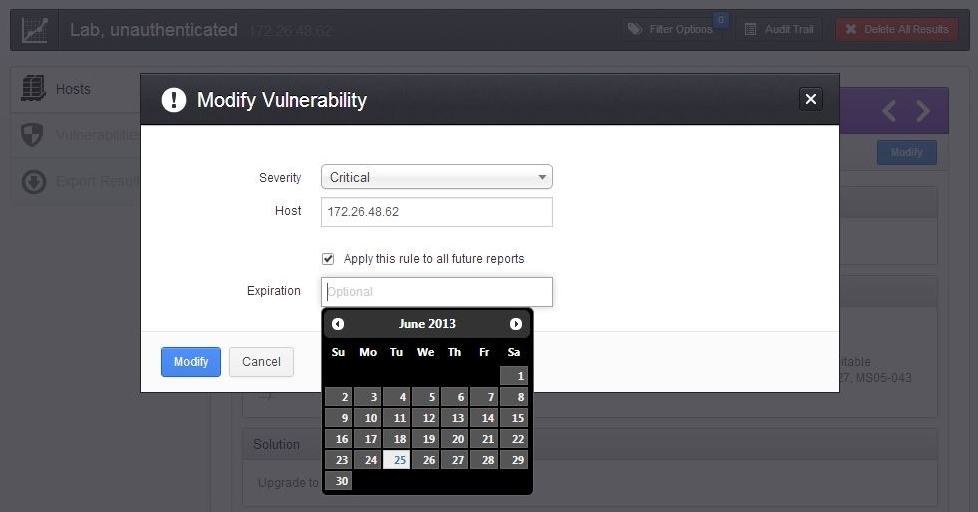
If the modification is made from the "Hosts" section of the report, it can be applied to a single host or to all hosts.
Modifications can also be added, removed, or edited through the new "Results Settings" section under the "Configuration" tab:

Managing the ability to edit scan results is performed as it has been for the existing ability to delete specific findings. The "Allow Post-Scan Report Editing" checkbox in the "Policy General Settings" tab allows Nessus users to enable or disable vulnerability modification:
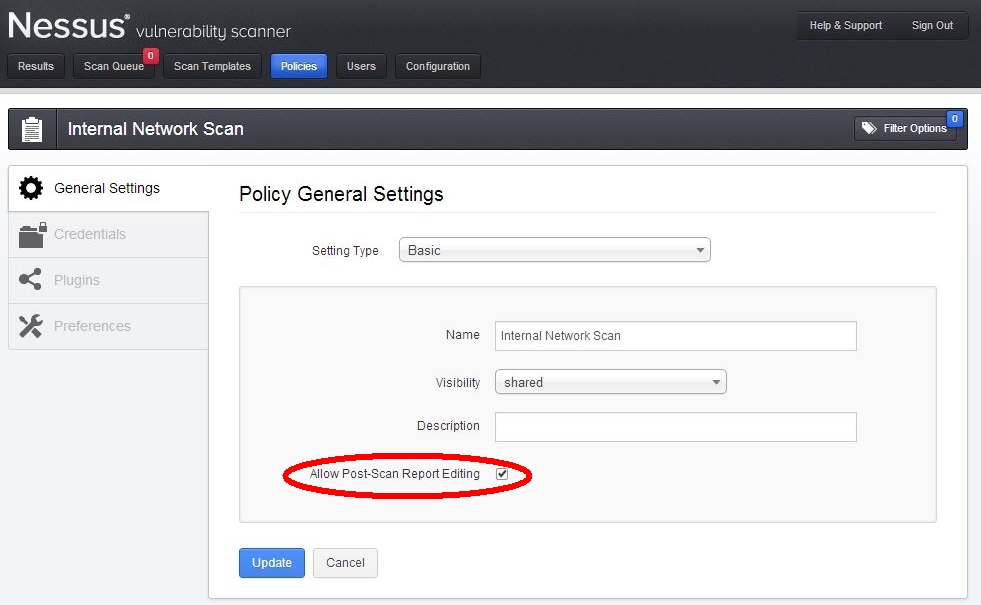
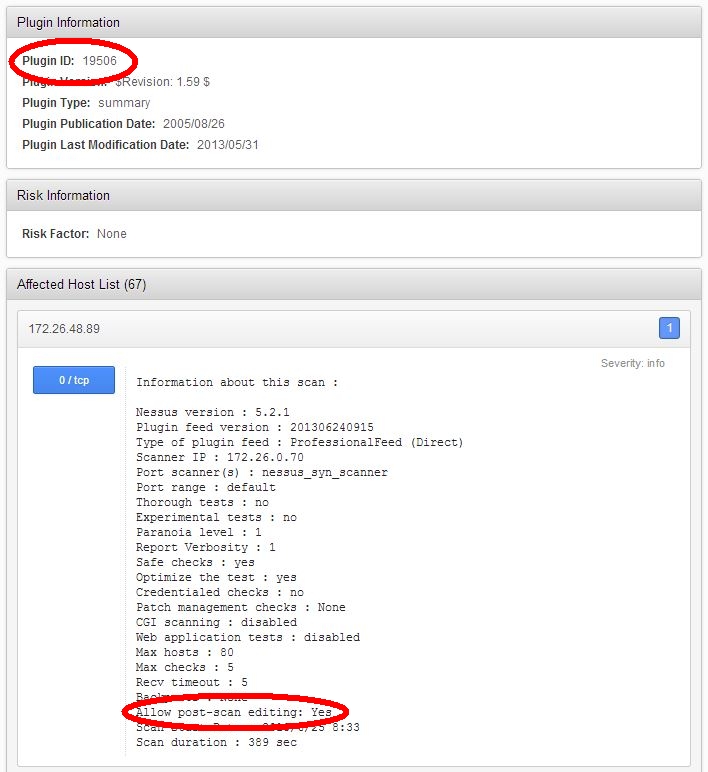
Nessus plugin ID #19506, Nessus Scan Information, reports whether post-scan editing is enabled for the current results:
Conclusion
Nessus ProfessionalFeed, Perimeter Service, and HomeFeed users can immediately take advantage of the new modification features. If you have any questions, please visit the Tenable Support Portal or pose a question on the Tenable Discussions Forum.
- Nessus

