Managed Kubernetes: Is It Right for My Organization?

As an organization grows its usage of containers, managing them becomes more complex. A common response is to adopt Kubernetes for container orchestration. But how do you properly secure your Kubernetes clusters? And should your organization host its Kubernetes deployments or instead choose a managed option? Here’s what you need to know.
Today, many organizations have adopted container technology to streamline the process of building, testing and deploying applications. Container technology offers benefits such as greater resource efficiency, portability, consistency and scalability. However, as the number of containers deployed increases, so does the management overhead. Kubernetes has become the de facto standard for container orchestration to deal with the management overhead problem. In this article, we will explore Kubernetes security, and some of the reasons you should choose a managed Kubernetes service instead of managing it in-house.
What is Kubernetes?
Kuberenetes is an open-source system to automate deployment, scaling and management of containerized applications. Kubernetes was originally developed by Google, then later donated to the Cloud Native Computing Foundation. Kubernetes consists of a control plane and worker nodes. The control plane makes global decisions about the cluster such as scheduling; runs processes to ensure the actual state of applications matches the desired state; and provides an API server for management. The worker nodes run the containerized application workloads within the cluster and are managed by the control plane.
Some of the benefits organizations realize through the use of Kubernetes include:
- Predictable and repeatable application deployment, with less downtime
- Matching of actual states with desired states via declarative configuration
- Greater availability through self healing
- More efficient use of resources
Managed or self-hosted?
Choices abound when it comes to deploying Kubernetes. There are currently over 90 certified Kubernetes offerings, including customized distributions, managed environments and installers. Organizations choose either to self-host or to leverage managed Kubernetes services from the major cloud providers such as: Amazon Elastic Kubernetes Service (EKS), Azure Kubernetes Service (AKS) and Google Kubernetes Engine (GKE).
Self-hosted Kubernetes requires the organization to manage the complete environment. With managed Kubernetes, the cloud service provider manages the Kubernetes control plane components - including hardening, patching, availability, consistency of dependencies, scaling, and backup management. In some cases such as Google Kubernetes Engine (GKE) Autopilot clusters, GKE also handles node management, provisioning and scalability.
Many organizations choose managed Kubernetes and the shared responsibility model because this option provides the increased flexibility of the cloud, while still managing certain aspects of the environment. A managed Kubernetes cluster will have additional security configurations applied and managed by the service provider in comparison to a default self-hosted configuration.
The Center for Internet Security (CIS) has created benchmarks for self-hosted Kubernetes, as well as for major cloud-provider Kubernetes offerings such as: Amazon’s EKS, Azure’s AKS and Google’s GKE. The CIS guidance is an excellent place to start when securing Kubernetes and can be found at https://www.cisecurity.org/benchmark/kubernetes
The CIS Kubernetes Benchmark contains close to 70 recommendations for control plane components (master node configuration files, API server, controller manager, scheduled, and more) in self-hosted Kubernetes environments. The recommendations include:
- Ensure proper permission and ownership of control plane configuration files, and data directories. By doing so, you can ensure configuration files and data directories are configured with permissions that prevent unauthorized access or modification.
- Ensure TLS security is configured for control plane service communications. Enabling TLS security protects communications between Kubernetes services from unauthorized access or manipulation.
- Ensure various API server admission-control plugins are either set or not set. In this way, admission control plugins can limit requests to create, delete, and modify objects.
- Ensure API server authorization mode is restricted. By restricting authorization mode, you ensure that not all requests are authorized.
- Ensure API server logging parameters such as path, age and size are set. With this configuration, you can collect security-relevant log records for activities performed by individual users, administrators or components of the system.
These recommendations are not included in the managed CIS Kubernetes Benchmarks for cloud service providers, because they are the responsibility of the service provider. In short, by going with a managed Kubernetes offering, you don’t have to take on the task of applying these CIS recommendations.
In addition, many managed Kubernetes providers offer integrations with services such as:
- Identity and access management. This allows administrators to manage identities and to authorize who can perform what actions on resources.
- Key and secrets management. This includes the management of SSL/TLS certificates, application secrets, and more.
- Image registry and image scanning. These capabilities offer a private registry for container images, with the ability to scan container images for vulnerabilities.
- Load balancing. Software-defined load balancing for Kubernetes traffic.
- Elastic provisioning and scalability. This feature gives you visibility into available capacity and the ability to increase/decrease resources in a timely manner.
- Cluster networking. This allows cluster node network connectivity across the zone or region, depending on cluster type.
- Logging and monitoring. With this capability, logs and events related to Kubernetes resources and dependent services are stored and accessible for querying, alerting and monitoring.
Organization maturity
Another consideration is your organization’s experience and expertise with Kubernetes. Maintaining Kubernetes clusters and their supporting technologies can be time- and resource-intensive. Many managed Kubernetes providers have central web interfaces for managing cluster and worker-node settings for all of your clusters. Users can direct their attention to deploying and managing their containerized applications, instead of worrying about managing the underlying infrastructure. Clusters can be easily scaled by adding or removing worker nodes to handle changes in workloads and traffic. This can either be done manually or by configuring elastic scaling, which will increase or decrease the number of nodes based on load. Similarly, pods and workloads can be auto-scaled horizontally as well.
Protecting Kubernetes workloads
Whether you choose self-hosted or managed Kubernetes, make sure you protect Kubernetes nodes from the running workloads. Workload privileges and access can be reduced by applying security context settings to minimize the admission of:
- Privileged containers. Privileged containers have access to all Linux Kernel capabilities and devices.
- Containers sharing the host process ID, IPC, or network namespaces. These containers can inspect and interact with processes outside the container, or access traffic to and from other pods.
- Containers with allowPrivilegeEscalation. This setting can allow a process to obtain more rights than it started with.
- Root containers. This allows the container process to run as root, which has an increased likelihood of container breakout.
- Containers with added capabilities or capabilities assigned. This permits certain root actions without granting full root privileges.
How Tenable can help
When organizations decide to adopt Kubernetes, there are a lot of considerations. One of the most significant is whether to go with managed Kubernetes, or to self-host. For many organizations the benefits of managed Kubernetes outweigh the flexibility of self-hosted Kubernetes.
Whether you choose managed or self-hosted, auditing your Kubernetes environment with Tenable based on the security best practices defined by CIS gives you insight into the security posture of the environment. With this knowledge, you are able to remediate any misconfigurations detected, reducing risk to your environment.
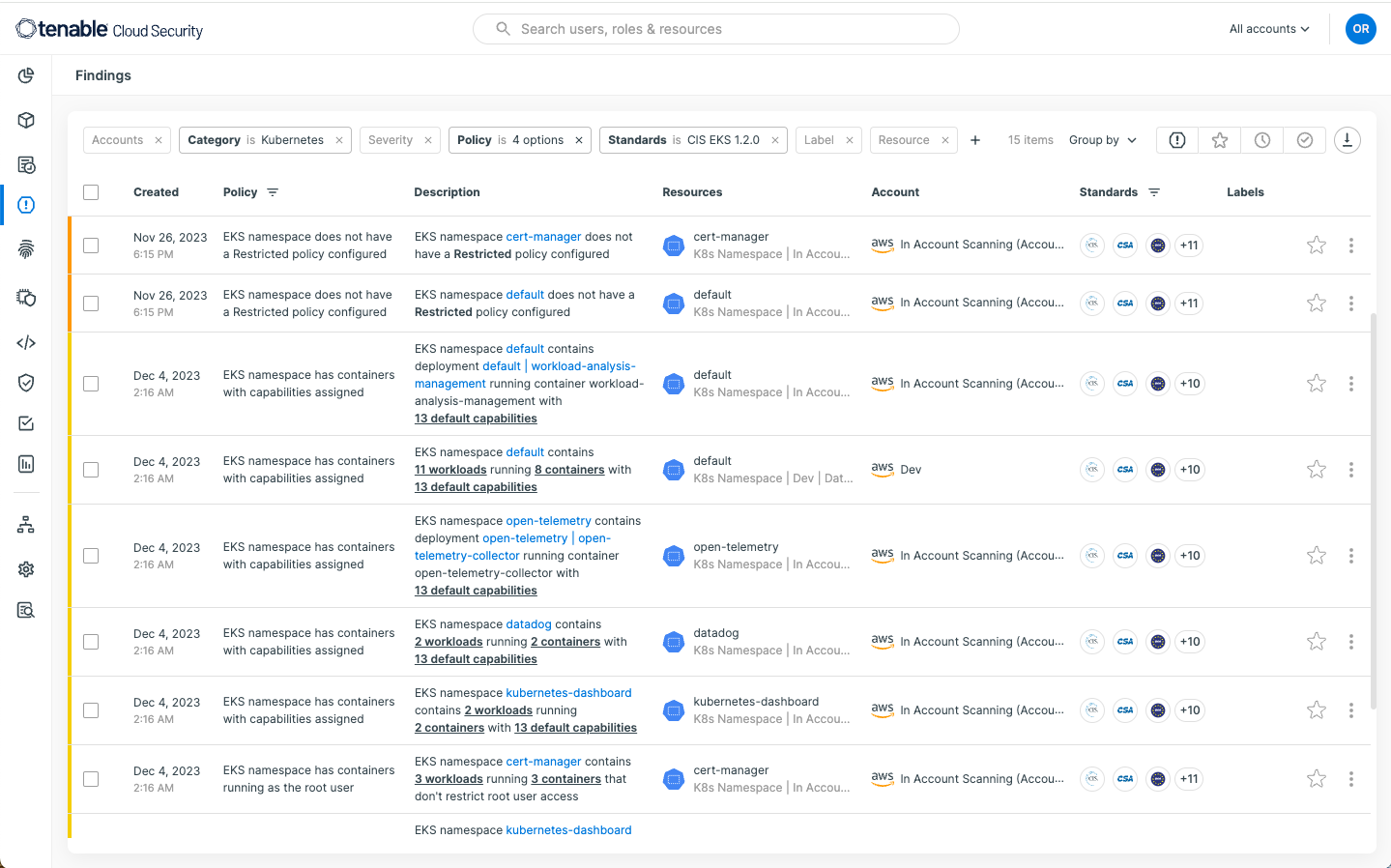
For example, the policies within Tenable Cloud Security can identify workloads that may have excessive privileges.
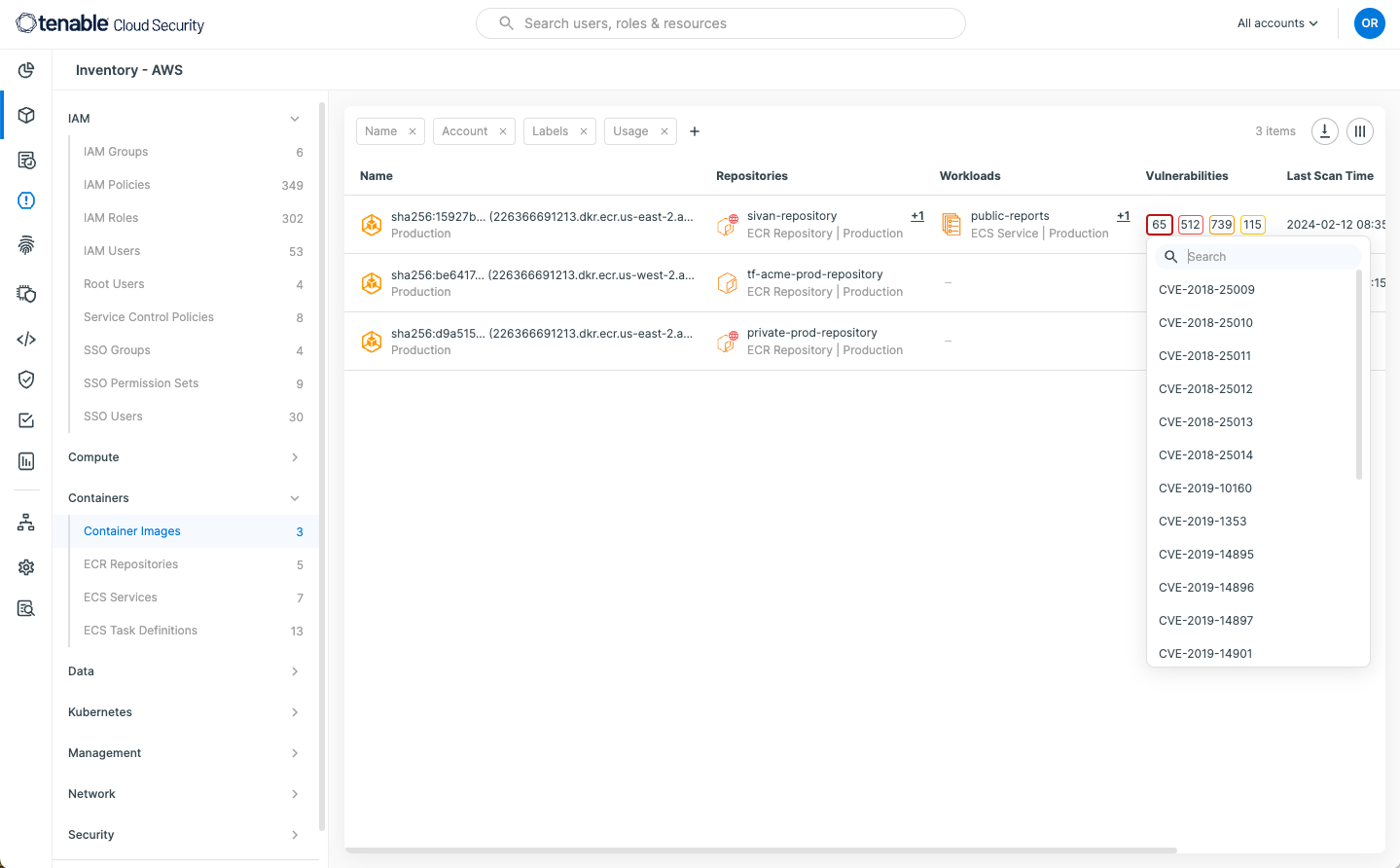
Another critical step in reducing the attack surface is to ensure container images are free from vulnerabilities, and to have a strategy to monitor running images for vulnerabilities. Below is an example from Tenable Container Security displaying images with vulnerabilities.
In closing, Tenable Cloud Security gives full, contextual visibility into multi-cloud Kubernetes resources, including nodes, namespaces, deployments, servers and service accounts. With fine-grained accuracy, Tenable detects, prioritizes and remediates Kubernetes compliance violations, misconfigurations, and other security gaps that can lead to breaches.
Visit the Tenable Cloud Security page to learn how Tenable can help you secure your Kubernetes clusters.
- Cloud
- Container security



