Is Mr. Robot in Your Network?

In Season 2 Episode 6 of Mr. Robot, Darlene and Angela continue with infiltration of the FBI and E-Corp, while Elliot is otherwise detained. Because Angela must plant the femtocell in E-Corp, members of F-Society help her learn the commands that are needed. They also offer an alternative called a “Rubber Ducky,” a USB device that registers itself as a Human Interface Device (HID) or keyboard. Since all systems trust HIDs, they are able to bypass policies that don’t allow USB storage devices. However, the infiltration plan is executed as planned with the femtocell device.
Angela makes her way to the 23rd floor, where the FBI team is working, and sets up the femtocell in the restroom. As she exits the restroom, a young FBI agent notices her unfamiliar face. Instead of checking her ID or other credentials, he takes the opportunity to ask for a date. Knowing she is almost caught, Angela plays his game and sets up a lunch date. Angela then makes her way to a cube where a small switch is located and puts the femtocell on the network. Darlene sees the femtocell collecting data, but then the data stops. As Angela re-enables the wireless network interfaces on the femtocell, Agent DiPierro interrupts her.
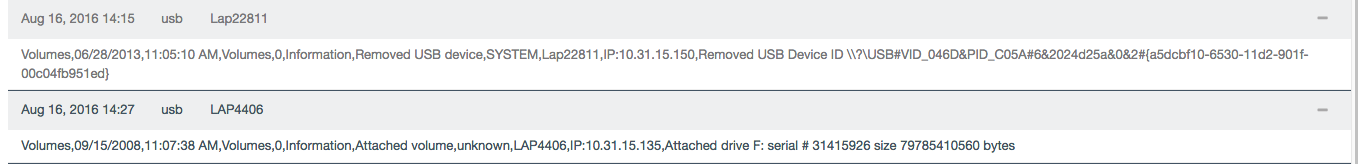
USB device tracking
Angela did not use the Rubber Ducky, but the threat of such a device is very real. Tenable SecurityCenter Continuous View™ (SecurityCenter CV™) supports two methods of detecting USB device installation.
The first method uses active scanning of a Windows host and provides a full history of USB devices. There are three plugins that provide a record of USB devices attached to a system:
- USB Drives Enumeration (24274)
- Microsoft Windows USB Device Usage Report (35730)
- Microsoft Windows Portable Devices (65791)
The plugins analyze the registry and native commands to report on USB devices such as storage devices, multimedia devices and human interface devices.
SecurityCenter CV also includes USB analysis with the Log Correlation Engine™ (LCE®). For Windows hosts running the LCE Agent, the installation and removal of a USB device is detected within 15 minutes of the aforementioned action. Each time a USB device is connected to a system, the LCE agent sends a log notification to LCE.
Detecting new devices on the network
There are many solutions in the marketplace to detect when a new device is on the network, called Network Access Control (NAC) systems. Many of these NAC systems run some type of a RADIUS server and interact with network systems and wireless systems. The RADIUS server then performs authentication against Active Directory or other type of user repository. While these systems are great for detecting obvious attempts to gain access, what about attempts that are not so obvious; do more stealthy attempts get tracked in the same manner?
SecurityCenter CV uses several methods of detecting systems on the network and can alert both help desk and security operations when such an event occurs. The LCE provides SecurityCenter users the ability to track when a new account is detected on a computer, when a device first connects to a network, and when a user runs a command for the first time. These three events are only a small sampling of the Never Before Seen (NBS) events that can be used when creating alerts within SecurityCenter. When SecurityCenter and LCE are fully implemented to monitor DHCP servers and network devices, there are other events such as switch port state changing, new MAC address tracking, and DHCP lease tracking, that can also track network access events.
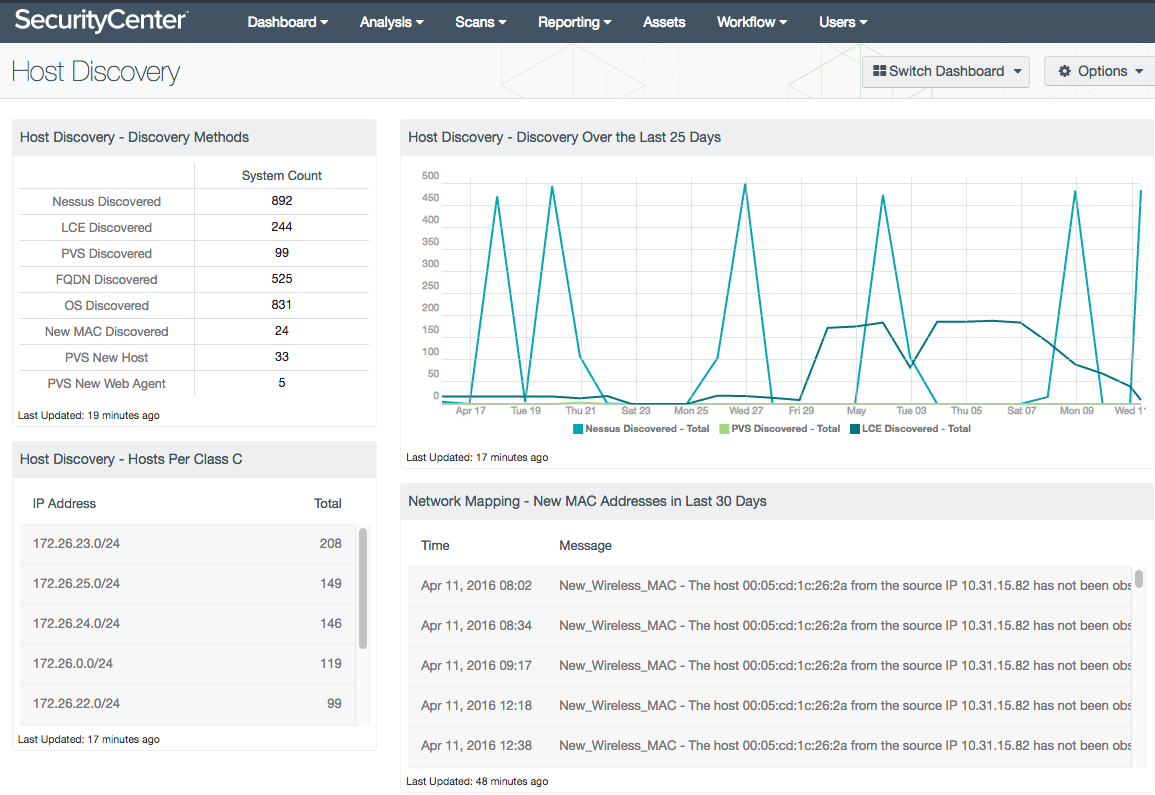
The Daily Host Alerts and Host Discovery dashboards provide valuable information about new host activity from many sources. The filters in these dashboards can be converted into alerts to assist the security operations team in identifying new devices on the network. By monitoring the switch and DHCP server used by the femtocell, SecurityCenter could send email alerts when these new devices are present and security ops could begin to investigate if the system is authorized or not.
Additionally, SecurityCenter alerts can launch scans of the systems and provide more information about them. In this episode, as Angela boots her computer off the thumb drive, SecurityCenter would have used the Passive Vulnerability Scanner™ (PVS™) to detect a new OS that had not been scanned before. SecurityCenter would have launched a scan if there were no Linux systems authorized in the subnet, and then a further alert would be emailed to the security ops team.
When a security operations team fully embraces SecurityCenter CV, there are many layers of detections available to identify unauthorized systems on the network. Whether the attack vector is unauthorized computers, network probes, or USB devices, Tenable SecurityCenter CV combats the attacks to protect the security of your organization.
But what about Angela? Is she caught red-handed, or has she eluded capture by the FBI yet again?
- LCE
- SecurityCenter
- Threat Management