How To Secure All of Your Assets - IT, OT and IoT - With an Exposure Management Platform

Enterprise security teams face serious hurdles to safeguarding their critical OT/IoT infrastructure, including fragmented visibility, unanticipated risks and data silos. Discover how purpose-built solutions for OT/IoT exposure management can help organizations enhance visibility, prioritize cybersecurity efforts and communicate cyber risk effectively across organizational silos.
Building and maintaining a proactive, comprehensive security program that covers a diverse set of IT domains and assets can be overwhelming. As if that wasn’t enough, CISOs are inheriting the responsibility to protect the entire cyberattack surface, which includes business-critical OT/IoT devices. However, deep silos within organizations and blurred lines of ownership and responsibility make this difficult.
Three key challenges limit modern enterprises’ ability to protect their OT/IoT environment:
- Fragmented visibility – Often, many of these technologies are deployed outside the purview of IT and security teams, leaving them unseen and insecure. How can organizations manage inventory and ongoing maintenance with such a diversified mix of OT/IoT equipment? How can you be sure systems are secure and operational as attackers continue to target OT and IoT assets more frequently?
- Unanticipated risk – Many OT technologies are insecure by design, featuring open connectivity for maximum flexibility. Similarly, functionality is prioritized and security is overlooked in the deployment of most IoT devices. Many OT asset owners believe their OT environment is “air-gapped” however, employees and equipment manufacturers often can remotely access OT systems, rendering them vulnerable to potential threats.
- Data silos – As security organizations add point solutions to address specific security gaps, data becomes trapped in silos. Disjointed tools and programs leave security leaders with a limited understanding of their environment and of risk relationships that are needed to shift from reactive threat hunting to proactive identification and remediation of potential threats. How do organizations prioritize security without knowing if risk is in the cloud, corporate network, data center or the OT environment?
This article is the first in a three-part series addressing challenges enterprise security teams face when protecting their OT/IoT infrastructure. We'll also share insights and solutions to help address these challenges. In this article, we’ll explore how organizations can gain complete visibility across the entire cyberattack surface using the latest exposure management strategies and tools.
Building a holistic enterprise exposure management strategy
Enterprise environments are large, complex and can span multiple segments of a network and sites across the globe. Domain-specific security software tools have emerged as point solutions for organizations struggling to build a comprehensive asset inventory, compile vulnerability statuses and detect changes and assess threats. Securing IT, OT and IoT is an enormous undertaking, considering OT/IoT assets are not traditionally owned by IT organizations and are instead managed by operations teams (or not at all for some IoT devices).
While the data and insights gathered from domain-specific tools are valuable for organizations to understand asset-specific risk, many teams continue to struggle to answer critical questions about their security posture: How can you accurately measure risk and exposure for each operating asset or facility, regardless of asset type? What risks do traditional business systems (e.g. ERP systems, Active Directory, remote access jump boxes) create for OT/IoT assets? What are the dependencies between these environments and how could they affect supply chains? How do changes in the OT environment affect other assets within the same facility?
Introducing Tenable One for OT/IoT
For organizations with OT/IoT assets, holistic exposure management unlocks unique capabilities for benchmarking and reporting risk across organizational silos. By aligning exposure management tools to business outcomes, security teams can surpass capabilities of traditional (domain-specific) vulnerability management and OT security tools. This enables better measurement and communication across the enterprise.
Tenable One for OT/IoT provides visibility across the modern cyberattack surface: IT, OT and IoT assets. The platform allows organizations to prioritize efforts to prevent likely attacks and accurately communicate cyber risk to support optimal business performance. The platform also combines the broadest vulnerability coverage spanning IT assets, cloud resources, containers, web apps, identity systems, and OT and IoT assets; builds on the speed and breadth of vulnerability coverage from Tenable Research; and adds comprehensive analytics to help organizations prioritize security actions and communicate cyber risk. If you’d like to take an expert deep dive on these topics, sign up for our upcoming webinar "The Invisible Bridge: Recognizing The Risk Posed by Interconnected IT, OT and IoT Environments."
Informed decision-making with exposure views
Tenable One for OT/IoT moves organizations past point solutions and organizational silos to achieve complete visibility of risk exposures, including for OT and IoT devices. Organizations may choose to measure risk by operating unit or by facility. These environments often contain a diverse set of assets, managed by different internal stakeholders. Tenable’s complete exposure view and unified global exposure scoring system enable focused security efforts with clear insight into an organization’s security posture.
For the first time, security leaders at industrial and non-industrial companies can utilize a single solution to view, assess and manage cyber risk across the entire attack surface. CISOs can overcome data silos with actionable business views of exposure to communicate cyber risk.
OT exposure cards in Tenable One allow users to holistically view, manage and report on risk. Exposure cards represent incoming data from your configured tags and data sources. The platform aggregates and normalizes data to provide a visualization of an organization’s cyber exposure and other important metrics. Users can create custom cards (or use default Tenable-provided cards) to gain insight and guidance on what areas need attention most. Custom exposure cards allow users to specify categories for which they want to see data. Once a custom exposure card is created, users can select it from a central library to view its data in Lumin Exposure View.
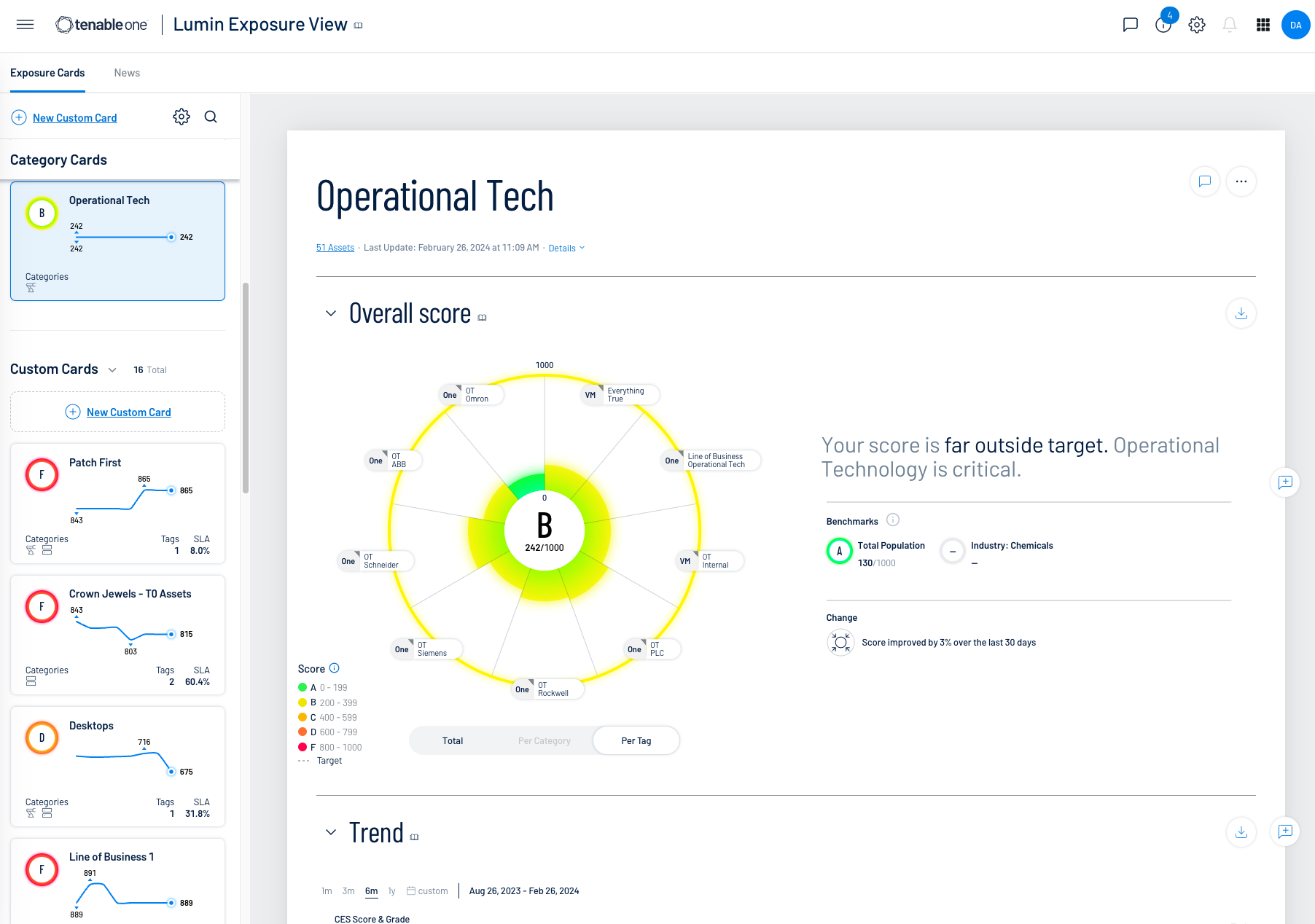
The Lumin Exposure View in Tenable One allows you to quickly view your global Cyber Exposure Score (CES), see changes and trends over time, view important benchmark comparisons, and assess your overall risk. The Lumin Exposure View includes several tools that help you understand your overall security posture as it relates your business context, the criticality of your assets, and the effectiveness of your efforts to remediate vulnerabilities across your workspace.
Before you begin, create a tag to apply to the card.
Follow these steps to create a custom exposure card:
- Access the Lumin Exposure View.
- On the left side of the page, click the Exposure Cards tab. A list of exposure cards appears.
- At the top of the Exposure Cards library or in the Custom Cards section, click the New Custom Card button. The Create Card page appears.
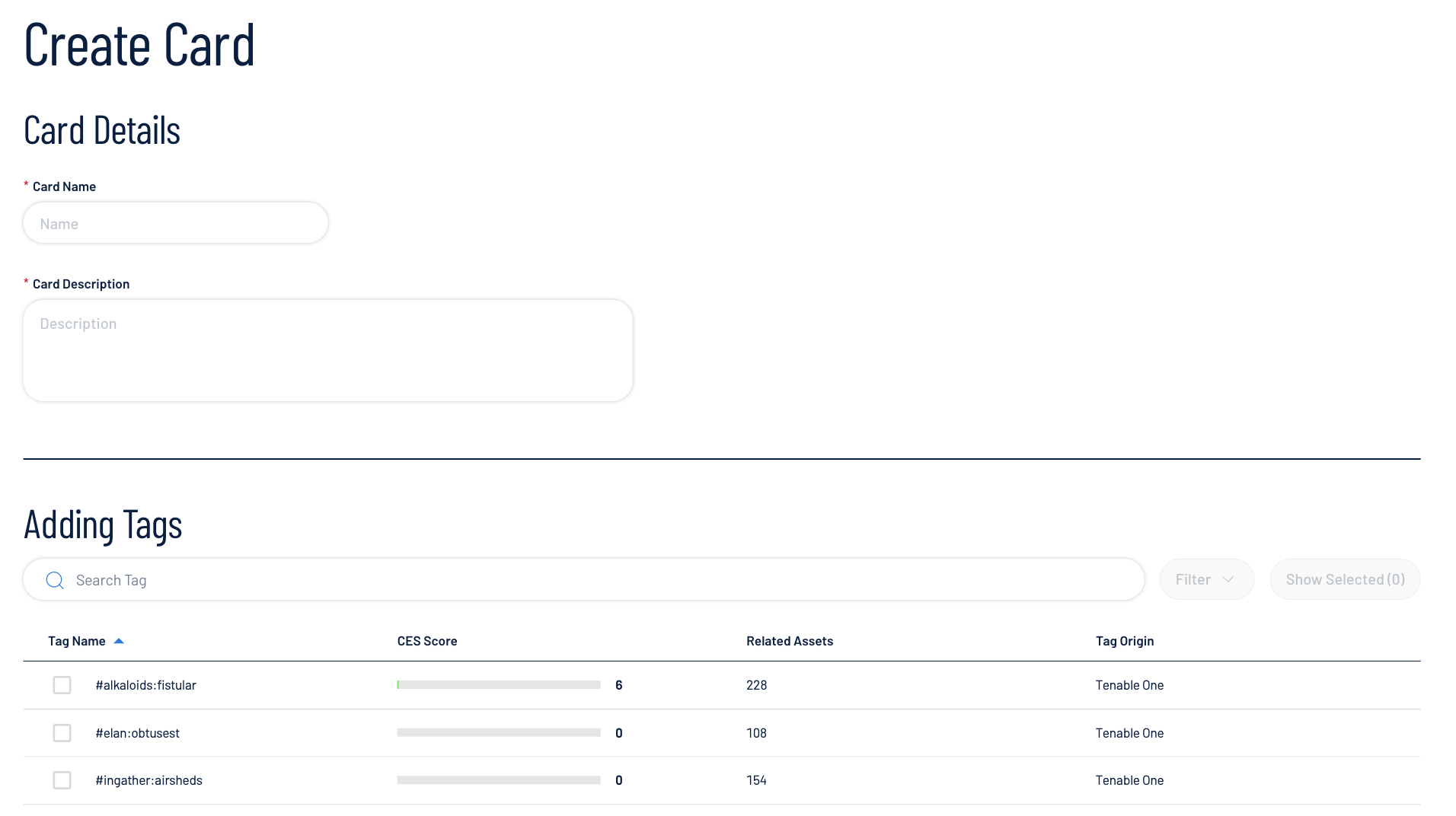
- In the Card Details section, in the Card Name box, type a name for the exposure card.
- In the Card Details section, in the Card Description box, type a name for the exposure card.
- In the Adding Tags section, select the tags you want to use to provide data for the exposure card (e.g., region, facility, specific asset characteristics such as vendor/device type, etc.):
- (Optional) Use the Search box to search for specific tags.
- Select the check box next to each tag you want to use to provide data for the exposure card.
- (Optional) To view only the tags you've added to the exposure card, click Show Selected.
- Click Save. The Lumin Exposure View saves the exposure card and adds it to the Custom Cards section of the Exposure Cards library.
Tenable One for OT/IoT also delivers integration with third-party IT security tools commonly used in enterprise environments, including service management tools, next-generation firewalls (NGFW), and security information and event management (SIEM) products for full situational awareness.
Schedule a free consultation and demo
To sum up, Tenable One for OT/IoT provides complete visibility and security for every asset across the extended cyberattack surface: IT, OT, and IoT assets. The platform enables visibility beyond the IT environment to the modern attack surface, risk intelligence to mitigate operational risks, and actionable planning and decision-making.
In the next post in this three-part series, we’ll explore how Tenable One for OT/IoT enables accurate asset inventory, informed cyber response across the complete cyberattack surface, and more.
Want to see what Tenable One for OT/IoT can do for your organization? Schedule a free consultation to receive a quick technical demo and to discuss how we can help improve your security program and results. To get more information about Tenable One for OT/IoT, please visit tenable.com/products/tenable-one and sign up to join our upcoming webinar "The Invisible Bridge: Recognizing The Risk Posed by Interconnected IT, OT and IoT Environments," where we’ll explore more strategies for organizations to effectively identify the risk posed by interconnected IT/OT/IoT environments.
Learn more
- Exposure Management
- Internet of Things
- OT Security



