From Managing Vulnerabilities to Managing Exposure: The Critical Shift You Can’t Ignore

Vulnerability management remains core to reducing cyber risk — but as the attack surface grows, teams need a risk-driven strategy that looks beyond vulnerabilities to see the bigger picture. Discover how exposure management unifies data and prioritizes real exposures — keeping teams proactive and ahead of cyber threats.
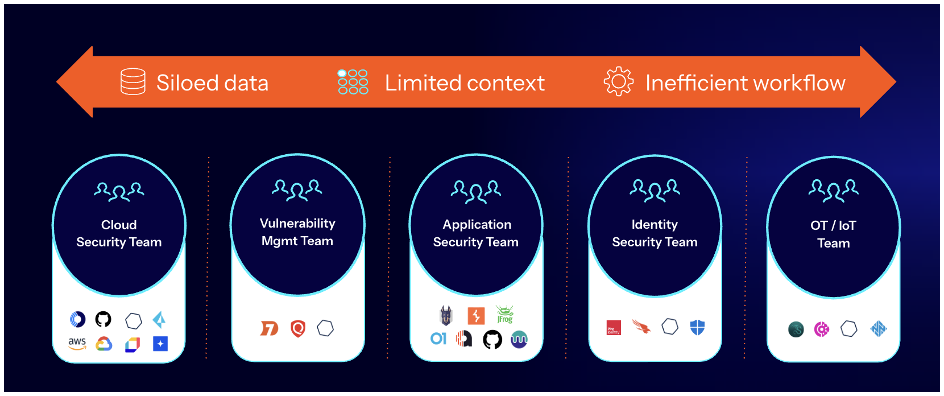
The limits of siloed security
Over the years, the attack surface has grown significantly with the rise of cloud computing, software as a service (SaaS), internet of things (IoT), operational technology (OT), AI and other emerging technologies. The COVID-19 pandemic accelerated this shift, with many companies adopting hybrid, remote-office models, even as many, in recent years, have instituted return-to-office policies.
As digital infrastructure expanded, security teams added more tools to combat emerging cyber threats, leading to tool sprawl. Now, many organizations juggle dozens of different security tools, resulting in inefficiencies, especially when managing risk data and coordinating remediation efforts.
On the data side, cybersecurity teams are stuck with siloed, disorganized and often duplicate risk data. Without context, prioritization becomes a guessing game, making it hard to identify the most critical risks to address. At the same time, security leaders struggle to answer basic questions like, “How exposed are we to an attack?”
The operational challenge is equally concerning. Domain-specific practices remain manual and coordination between IT, DevOps, SecOps and CloudOps is hindered by fragmented tools and misaligned priorities. This fragmented approach leaves critical issues unaddressed for weeks or even months, significantly increasing exposure.
This is the reality of security operations today — fragmented data, inefficient workflows and a lack of comprehensive context leave security teams not only struggling to mitigate risks but also to fully understand their true level of exposure.
The evolution to exposure management
For years, vulnerability management has been key to cybersecurity, providing crucial visibility into weaknesses across IT environments. It’s the first and most essential step in securing digital assets — helping security teams identify and catalog vulnerabilities across systems, applications and networks. However, as enterprise ecosystems expand and interconnect, vulnerabilities represent just one piece of a much broader risk landscape.
Today, risk spans every corner of the attack surface — from misconfigurations in cloud environments to excessive permissions and exposed identities. These risks often create greater exposure than vulnerabilities alone, underscoring the need for a more holistic, contextual approach to managing cyber risk.
When it comes to exposure management vs. vulnerability management, the difference is clear: vulnerability management tells you where security gaps exist — exposure management helps you understand the risk and prioritize action. By shifting from a reactive, vulnerability-centric approach to a broader, risk-driven strategy, organizations can focus on the exposures that truly matter, making their security programs more efficient than ever.
To effectively reduce exposure, security teams need more than just a list of vulnerabilities; they need context to understand which exposures truly matter in their unique environment, how they connect and their potential impact on the business. This is where exposure management comes in.
Exposure management vs. vulnerability management
Exposure management builds on vulnerability management, but takes it a step further by breaking down silos and adding context for a complete view of risk across the attack surface.
When it comes to exposure management vs. vulnerability management, the difference is clear: vulnerability management tells you where security gaps exist — exposure management helps you understand the risk and prioritize action. By shifting from a reactive, vulnerability-centric approach to a broader, risk-driven strategy, organizations can focus on the exposures that truly matter, making their security programs more efficient than ever.
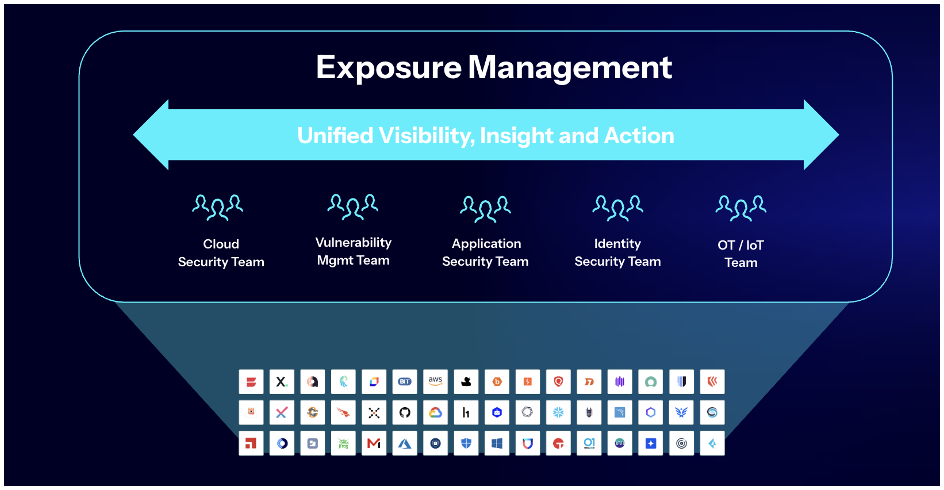
Unified visibility is the foundation for exposure management
To achieve effective exposure management, organizations need a comprehensive view of their entire attack surface. This means pulling together all available data from across their security tools, including those for applications, cloud, identity, OT, endpoint, asset inventories, CMDBs, threat intelligence feeds and more.
By combining insights from these diverse data sources, security teams can see the bigger picture, connecting the dots between assets, vulnerabilities, misconfigurations and existing compensating controls across multiple environments.
Consolidating security data from siloed tools facilitates a unified, holistic view of risk. This approach enables organizations to:
✔ Manage risk from one place: Break down silos and gain unified visibility across the entire attack surface.
✔Prioritize real exposure: Uncover attack paths and toxic risk combinations across all security data for effective cross-domain prioritization.
✔ Remediate with context: Identify choke points and pinpoint the most effective remediation strategies to address critical risks across the entire security landscape.
✔ Create holistic reports: Achieve a single source of truth for holistic reporting on risks and exposure findings across all environments.
By breaking down data silos and integrating insights from multiple security tools, organizations can reduce the likelihood of a breach and minimize risk exposure across the attack surface. Instead of viewing risks in isolation, security teams can connect the dots — understanding how attackers see their environment and taking smarter, more proactive action to reduce exposure.
Bringing exposure management to life
Now that we’ve covered the fundamentals of exposure management, let’s explore how to put this approach into practice and build an effective program that drives real security outcomes.
- Leave no blind spots — Continuously scan your entire attack surface to uncover all potential risks and ensure full visibility.
- Break down data silos — Unify security data from all sources into a single, consolidated view to understand your organization’s true risk exposure.
- Incorporate relevant context — Enrich raw scan data with business context and threat intelligence to understand which exposures matter most.
- Focus on what matters — Prioritize risks based on real business impact, so teams can address the most dangerous weaknesses first.
- Streamline collaboration — Ensure IT and development teams can take swift action by integrating exposure insights directly into their workflows.
- Continuously measure and improve — Track progress, refine processes and optimize security efforts to stay ahead of evolving threats.
By following these best practices, organizations can move beyond reactive security and take a proactive approach — one that not only identifies risk but actively reduces exposure, strengthening their overall cyber resilience.
Learn more
- Exposure Management


