Cybersecurity Snapshot: New Standard for AI System Security Published, While Study Finds Cyber Teams Boost Value of Business Projects

Check out ETSI’s new global standard for securing AI systems and models. Plus, learn how CISOs and their teams add significant value to orgs’ major initiatives. In addition, discover what webinar attendees told Tenable about their cloud security challenges. And get the latest on properly decommissioning tech products; a cyber threat targeting law firms; and more!
Dive into six things that are top of mind for the week ending May 30.
1 - ETSI publishes global standard for AI security
What is the proper way to secure your artificial intelligence models and systems? Are you confused by all the different AI security recommendations and guidance? The European Telecommunications Standards Institute (ETSI) is trying to bring clarity to this issue.
ETSI, in collaboration with the U.K. National Cyber Security Center (NCSC) and the U.K. Department for Science, Innovation & Technology (DSIT), has published a global standard for AI security designed to cover the full lifecycle of an AI system.
Aimed at developers, vendors, operators, integrators, buyers and other AI stakeholders, ETSI’s “Securing Artificial Intelligence (SAI); Baseline Cyber Security Requirements for AI Models and Systems” technical specification outlines a set of foundational security principles for an AI system’s entire lifecycle.
Here's an overview of the five stages of an AI system and the 13 security principles that must be adopted:
- Secure design stage
- Raise awareness about AI security threats and risks.
- Design the AI system not only for security but also for functionality and performance.
- Evaluate the threats and manage the risks to the AI system.
- Make it possible for humans to oversee AI systems.
- Secure development stage
- Identify, track and protect the assets.
- Secure the infrastructure.
- Secure the supply chain.
- Document data, models and prompts.
- Conduct appropriate testing and evaluation.
- Secure deployment stage
- Communication and processes associated with end-user and affected entities.
- Secure maintenance stage
- Maintain regular security updates, patches and mitigations.
- Monitor system behavior.
- Secure end-of-life stage
- Ensure proper data and model disposal.
- Ensure proper data and model disposal.
Each one of the 13 security principles is further broken down into multiple provisions that detail more granular requirements.
For example, in the secure maintenance stage, ETSI calls for developers to test and evaluate major AI system updates as they would a new version of an AI model. Also in this stage, system operators need to analyze system and user logs to detect security issues such as anomalies and breaches.
The 73-page companion technical report, “Securing Artificial Intelligence (SAI): Guide to Cyber Security for AI Models and Systems,” offers significantly more technical detail about each provision.
Together the technical specification and the technical report “provide stakeholders in the AI supply chain with a robust set of baseline security requirements that help protect AI systems from evolving cyber threats,” reads an NCSC blog.
For more information about AI security, check out these Tenable resources:
- “Harden Your Cloud Security Posture by Protecting Your Cloud Data and AI Resources” (blog)
- “Tenable Cloud AI Risk Report 2025” (report)
- “Who's Afraid of AI Risk in Cloud Environments?” (blog)
- “Tenable Cloud AI Risk Report 2025: Helping You Build More Secure AI Models in the Cloud” (on-demand webinar)
- “Securing the AI Attack Surface: Separating the Unknown from the Well Understood” (blog)
2 - Report: CISOs and cyber teams pump value into business projects
Cybersecurity teams’ involvement in large-scale organizational initiatives yields significant monetary benefits – especially if CISOs are incorporated early into these efforts.
That’s a key finding from Ernst & Young’s “2025 EY Global Cybersecurity Leadership Insights Study,” which surveyed 550 C-suite and cybersecurity leaders globally from organizations with more than $1 billion in annual revenue.
Specifically, the study found that cybersecurity teams contribute a median of $36 million to every enterprise-wide initiative they’re involved in. That’s equivalent to between 11% and 20% of the value of each project.
“CISOs who are involved early in cross-function decision-making generate more value than those who were consulted late or not at all,” the report reads.
“CEOs, CFOs and boards should take steps to more meaningfully integrate cybersecurity into transformations and other strategic initiatives,” it adds.

The finding points to how CISOs and their cybersecurity teams are expanding their scope from managing security, risk and compliance to becoming “key enablers of business growth.”
Unfortunately, over the past two years, cybersecurity budgets have shrunk as a percentage of annual revenue, and only 13% of surveyed CISOs said they get looped in early into critical business decisions.
Using a framework, the report concluded that cybersecurity adds considerable value to these six key types of initiatives:
- Adopting and building technology
- Strengthening brand trust and reputation
- Improving customer experience
- Transforming and innovating across the business
- Expanding to new markets
- Developing new products and services
For more information about how CISOs and their cyber teams add value to business ventures:
- “Better metrics can show how cybersecurity drives business success” (CSO)
- “Build CISO Strategic Impact and Visibility” (IANS Research)
- “Nearly half of CISOs now report to CEOs, showing their rising influence” (Help Net Security)
- “CISOs embrace rise in prominence — with broader business authority” (CSO)
- “How leading CISOs build business-critical cyber cultures” (CIO)
3 - Tenable poll zooms in on cloud security
During our recent webinar “Confident in the Cloud: How to Overcome Complexity and Get AWS Security Right,” we asked attendees about their cloud security practices and challenges. Check out what they said.
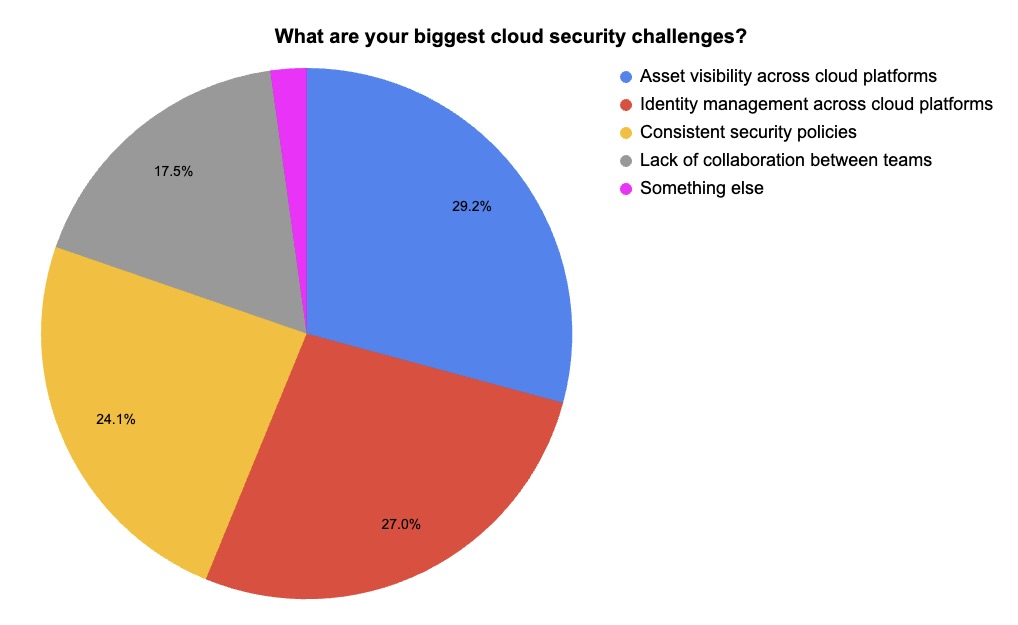
(137 webinar attendees polled by Tenable, May 2025)
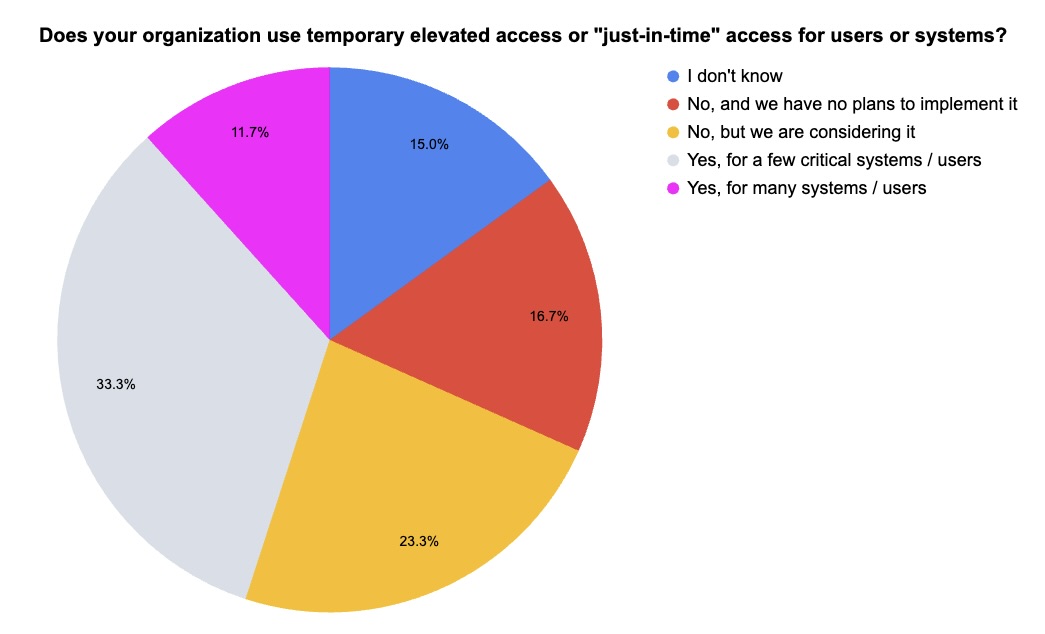
(60 webinar attendees polled by Tenable, May 2025)
Interested in learning about proven best practices for how to control and secure your AWS environment? Watch this webinar on-demand!
4 - Guide: How to safely decommission tech products
It’s important to properly dispose of software and hardware products after removing them from your IT environment.
To help organizations with this process, the U.K. National Cyber Security Centre (NCSC) has published guidance on how to securely retire obsolete technical wares.
“Decommissioning can be highly expensive and complex, with potentially severe repercussions if not executed properly,” the NCSC document reads. “Outdated or unsupported assets can pose an unacceptable risk to the organisation.”

For example, an improperly decommissioned IT product could allow unauthorized people to access confidential data and could be used to breach services and devices.
The NCSC guidance, titled “Decommissioning assets,” addresses topics including:
- How to plan the decommissioning process
- How to carry out the decommissioning of obsolete assets
- What to do after the decommissioning process is completed
For more information about properly disposing of obsolete hardware and software:
- “How to Decommission IT Hardware” (Techbuyer)
- “Why end-of-life IT is ruining innovation and how to fix it” (OliverWyman)
- “Cybersecurity guidance: Obsolete products (Canadian Centre for Cyber Security)
- “The Top 5 Risks of Using Obsolete and Unsupported Software” (IT Convergence)
- “Managing the risks of legacy IT” (Australian Cyber Security Centre)
5 - FBI warns law firms about Silent Ransom threat
Hacker group Silent Ransom is targeting law firms via phishing calls and emails aimed at tricking employees into granting it remote access to their computers. Once they gain remote access, the attackers steal confidential data and use it to extort the victims.
So said the U.S. Federal Bureau of Investigation (FBI) in an alert titled “Silent Ransom Group Targeting Law Firms.”
Silent Ransom, also known as Luna Moth, Chatty Spider and UNC3753, employs two different schemes:
- It emails its targets offering fake, inexpensive subscriptions, and when victims request that the subscription be cancelled, the attackers email them a link that downloads remote access software on their computers.
- A Silent Ransom attacker calls a law firm employee and, pretending to be a member of the IT department, asks the victim to join a remote access session.
Detecting a Silent Ransom attack is difficult. Its hackers don’t leave behind traditional attack indicators because they use legitimate remote-access and systems-management tools. Thus, to spot a Silent Ransom breach, the FBI recommends looking for:
- New, unauthorized downloads of systems-management and remote-access tools
- A WinSCP or Rclone connection made to an external IP address
- Anonymous emails or calls claiming data was stolen
- Emails regarding how to cancel a subscription service
- Unsolicited calls from individuals claiming to work in the law firm’s IT department
To mitigate the threat, FBI recommendations include:
- Train staff on recognizing and resisting phishing attempts.
- Establish and relay policies for when and how your law firm’s IT department will reach out to employees and prove their identities.
- Regularly back up company data.
- Adopt multi-factor authentication for all employees.
For more information about remote access attacks:
- “12 remote access security risks and how to prevent them” (TechTarget)
- “Guide to Securing Remote Access Software” (CISA)
- “Remote-access tools the intrusion point to blame for most ransomware attacks“ (Cybersecurity Dive)
- “Avoiding Ratting – Remote Access Trojans” (Get Safe Online)
- “RDP and Other Remote Login Attacks” (Ransomware.org)
6 - New, updated CIS Benchmarks for Kubernetes, Microsoft and Red Hat products
The Center for Internet Security has updated its CIS Benchmarks for Kubernetes, Azure Kubernetes Service and Microsoft Intune, and has released a new CIS Benchmark for Red Hat Enterprise Linux Security Technical Implementation Guide (STIG).
These are the CIS Benchmarks updated in April:
- CIS Azure Kubernetes Service (AKS) Benchmark v1.7.0
- CIS Kubernetes Benchmark v1.11.1
- CIS Microsoft Intune for Windows 10 Benchmark v4.0.0
- CIS Microsoft Intune for Windows 11 Benchmark v4.0.0
Meanwhile, the brand new Benchmark is CIS Red Hat Enterprise Linux 9 STIG Benchmark v1.0.0.

Organizations can use the CIS Benchmarks’ secure-configuration guidelines to harden products against attacks. Currently, there are more than 100 Benchmarks for 25-plus vendor product families in categories including:
- cloud platforms
- databases
- desktop and server software
- mobile devices
- operating systems
To get more details, read the CIS blog “CIS Benchmarks May 2025 Update.” For more information about the CIS Benchmarks list, check out its home page, as well as:
- “How to use CIS benchmarks to improve public cloud security” (TechTarget)
- “How to Unlock the Security Benefits of the CIS Benchmarks” (Tenable)
- “CIS Benchmarks Communities: Where configurations meet consensus” (HelpNet Security)
- “CIS Benchmarks: DevOps Guide to Hardening the Cloud” (DevOps)
CIS Benchmarks
- Center for Internet Security (CIS)
- Cloud
- Cybersecurity Snapshot
- Federal
- Government
- Malware
