Cybersecurity Snapshot: Insights on Log4j, Memory Attacks, Cloud Security, Ransomware

Get the latest on an APT’s Log4Shell exploit; tips to prevent memory attacks; cloud security trends; metaverse security; and more!
Dive into 6 things that are top of mind for the week ending Nov. 18.
1 - CISA Advisory: Iranian APT exploits Log4Shell to breach U.S. government agency
In a high-profile public exploit of Log4Shell, an advanced persistent threat (APT) group from Iran leveraged the dreaded Log4j vulnerability to breach a U.S. government agency.
How did they do it? They compromised an unpatched VMware Horizon server. The breach occurred in February and wasn’t discovered until mid-year when the Cybersecurity and Infrastructure Security Agency (CISA) investigated suspicious APT activity at the unnamed agency.

After exploiting Log4Shell, the attackers “installed XMRig crypto mining software, moved laterally to the domain controller, compromised credentials, and then implanted Ngrok reverse proxies on several hosts to maintain persistence,” reads a joint advisory issued by CISA and the FBI this week.
The advisory, titled “Iranian Government-Sponsored APT Actors Compromise Federal Network, Deploy Crypto Miner, Credential Harvester,” details the APT group’s tactics, techniques and procedures, and its indicators of compromise. CISA and the FBI urge all organizations with vulnerable VMware systems to assume they’ve been compromised and launch threat hunting efforts.
For more information, read the CISA/FBI advisory, their official announcement and a malware analysis report. You can find more coverage and analysis from The Register, SecurityWeek, The Record, TechCrunch and Silicon Angle.
You can also check out Tenable’s Log4j page, which has a wealth of information and resources about Log4Shell, which was discovered almost one year ago.
2- How’s cloud security going for you?
Security is top of mind for any organization adopting cloud, so at our recent webinar “Cloud Security Roundtable: Scaling Cloud Adoption without Sacrificing Security Standards” we took the opportunity to poll attendees about their main challenges, approaches and priorities for cloud security. Check out the results below.
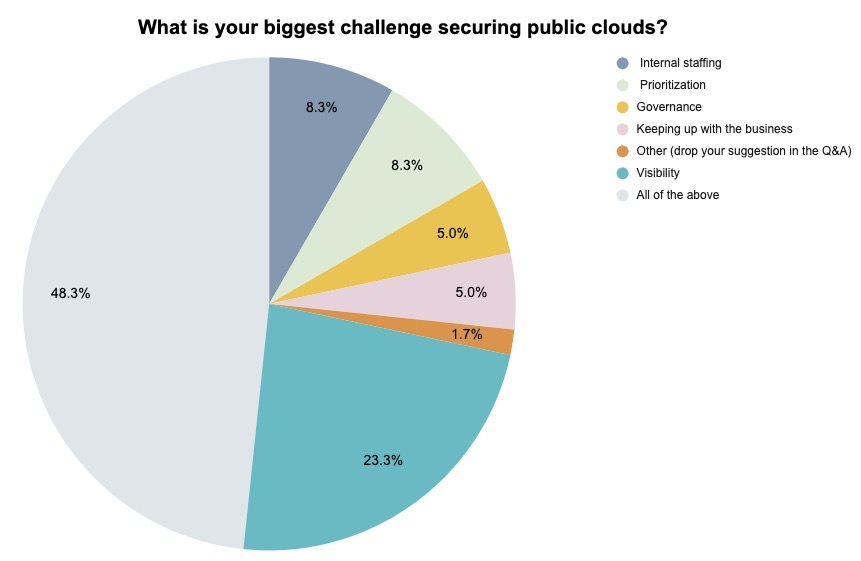
(60 respondents polled by Tenable, October 2022)
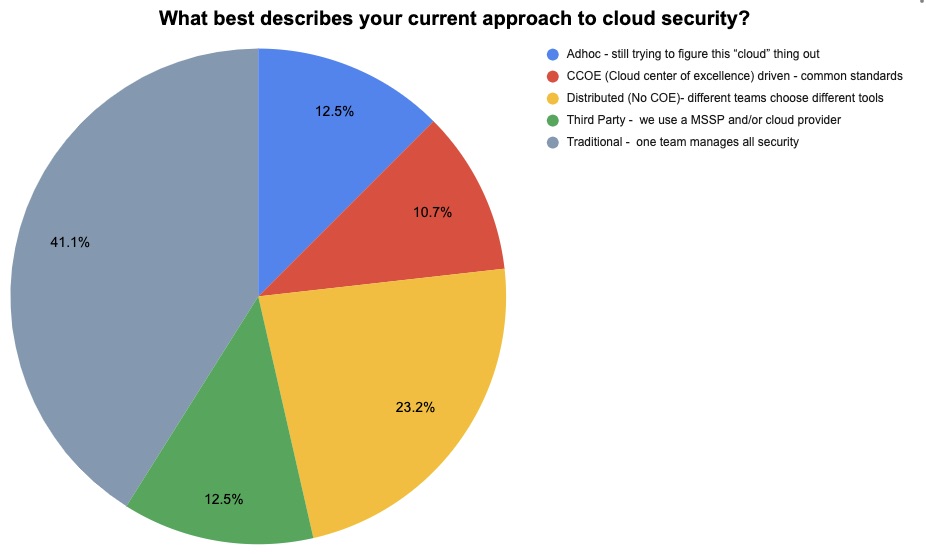
(56 respondents polled by Tenable, October 2022)
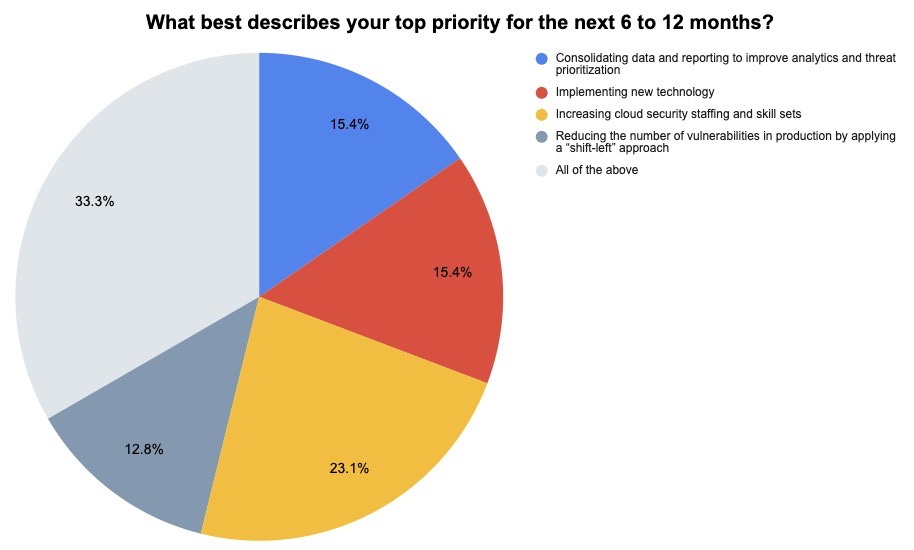
(39 respondents polled by Tenable, October 2022)
For more information about cloud security, check out these Tenable resources:
- “Mind the (Communication) Gap: How Security Leaders Can Become Dev and Ops Whisperers”
- “A Practical Approach for Shifting Left”
- “3 Ways Security Leaders Can Work With DevOps to Build a Culture of Security”
- “The Four Phases of Cloud Security Maturity”
- “CNAPP: What Is It and Why Is It Important for Security Leaders?”
- “SANS 2022 DevSecOps Survey: Creating a Culture to Significantly Improve Your Organization’s Security Posture”
3 - Excess user privilege: A cloud security weak link
Giving users more permissions than they need is a common configuration mistake organizations make in their cloud deployments because, in case of a breach, it helps intruders move laterally and compromise additional assets.
That’s one of the findings from the “2022 IBM Security X-Force Cloud Threat Landscape Report,” which found this problem of “excess privilege” for cloud identities in a whopping 99% of analyzed penetration tests.
Here are other findings from the report, which is based on an analysis of threat intelligence data, pen testing results, incident response results, dark web insights and other information compiled between July 2021 and June 2022:
- More than 100,000 cloud accounts were found being peddled on the dark web, a 200% jump from 2021. Access to most (76%) is sold through remote desktop protocol, followed by compromised/stolen credentials (19%.)
- Cryptominers and ransomware are the top malware types used to target cloud environments.
- 26% of the cloud compromises analyzed resulted directly from exploiting a vulnerability, as cloud vulnerabilities have surged 540% in the last six years, while also increasing in severity.
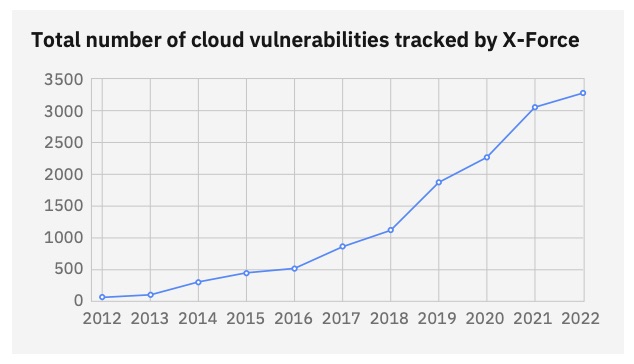
(Source: “2022 IBM Security X-Force Cloud Threat Landscape Report,” October 2022)
For more details, check out this summary of the report.
Here’s more information about cloud security:
- “Security Guidance for Critical Areas of Focus in Cloud Computing” (Cloud Security Alliance)
- “The Ultimate Guide to Cloud Security Best Practices” (EC-Council)
- “Cloud Security: Visibility and Insight into All of Your Cloud Infrastructure” (Tenable)
- “11 top cloud security threats” (CSO Magazine)
- “Cloud Security Principles” (Tenable)
- “The Four Phases of Cloud Security Maturity” (Tenable)
4 - Report highlights ransomware threat against U.S. banks
U.S. banks reported the highest number of ransomware-related incidents ever, as well as the largest amount of actual or demanded ransomware payments, to the U.S. Treasury Department in 2021. According to a report, the department’s Financial Crimes Enforcement Network (FinCEN) received almost 1,500 reports worth nearly $1.2 billion, up 188% from $416 million in 2020. The report also notes that during the second half of 2021, the majority of the ransomware variants reported to FinCEN could be related to Russian cyberattackers.
“Today’s report reminds us that ransomware — including attacks perpetrated by Russian-linked actors — remain a serious threat to our national and economic security,” said FinCEN Acting Director Himamauli Das in a statement.
FinCEN’s detection and mitigation recommendations for financial institutions include:
- To actively block suspicious activity, feed indicators of compromise from threat data sources into intrusion detection systems and security alert systems.
- If you identify ransomware activity, report it right away to law enforcement, including CISA, the FBI, FinCEN, the U.S. Secret Service and the Office of Foreign Assets Control.
- Be on the lookout for “red flag” indicators of ransomware-related financial activity, such as IT activity detected in system log files or network traffic that points to known ransomware indicators or actors.
For more guidance and best practices:
- “Advisory on Ransomware and the Use of the Financial System to Facilitate Ransom Payments” (U.S. Treasury Department)
- “FinCEN Combats Ransomware” (U.S. Treasury Department)
- “Stop Ransomware” (CISA)
- “Detecting and Responding to Ransomware and Other Destructive Events” (U.S. National Institute of Standards and Technology)
5 - Europol: Police chiefs need to get hip to the metaverse
The metaverse is still under construction, but the time is now for law enforcement agencies to get ready to police it. So says Europol, which just released a report that explains what the metaverse is, how it could be used by cybercriminals and what steps law enforcement agencies can take to prepare.

Titled “Policing in the metaverse: what law enforcement needs to know,” the report highlights key areas for potential criminal activity in the metaverse, including:
- Identity, because the metaverse will exponentially enrich digital identities, making them more valuable to cybercriminals
- Finance, because it will create a fertile environment for fraud and money laundering as financial transactions involve decentralized cryptocurrencies
- Harassment, abuse and exploitation, including of children, as the boundary between a person’s physical and digital identity further blurs in virtual reality
- Terrorism, because the more immersive experience of the metaverse will allow terrorist organizations to intensify their recruitment and training activities
- Mis- and disinformation, as the metaverse offers much more precise data to target specific demographics with propaganda
Europol advises law enforcement agencies to build an online presence in the metaverse; experience the metaverse and its related technologies; and engage with companies that are creating it.
“Having an understanding of what is being developed will be essential for engaging all relevant actors and building a picture of the needs and responsibilities of law enforcement in the metaverse,” reads the report.
For example, the report highlights the examples of Norway, which since 2015 has been putting “internet patrols” on various social media, gaming and streaming platforms as a resource for users; and of France, where law enforcement set up an online presence in Fortnite to help children who face abuse there.
For more information, read the report and watch this Europol video:
Check out additional coverage and analysis of metaverse security from VentureBeat, ZDNet, TechTarget, MIT Technology Review and Wired, as well as this video report from Minneapolis TV station KARE 11: https://www.youtube.com/watch?v=p8QV0j5uUv4
6 - NSA zeroes-in on software memory vulnerabilities
Developers should use programming languages that are less likely to yield applications vulnerable to software memory attacks like buffer overflows. That’s the advice from the U.S. National Security Agency (NSA), which just released a guide focused on software memory safety.
In it, the NSA discourages developers from using languages such as C and C++, because they offer too much “freedom and flexibility” when it comes to memory management, and put the onus on the developer to ensure the application isn’t vulnerable to software memory attacks.
“Software analysis tools can detect many instances of memory management issues and operating environment options can also provide some protection, but inherent protections offered by memory safe software languages can prevent or mitigate most memory management issues,” the guide reads.
The NSA recommends using “memory safe” languages, including C#, Go, Java, Ruby, Rust and Swift. If a developer must use an unsafe memory language, the NSA encourages them to use static and dynamic application security testing tools to flag memory use problems.
In addition, “anti-exploitation” steps can be taken to harden compilation and execution environments via features and techniques like control flow guard (CFG), address space layout randomization (ASLR) and data execution prevention (DEP).
For more information:
- “What is buffer overflow?” (TechTarget)
- “Memory leak” (OWASP)
- “Analysts Welcome NSA's Advice for Developers to Adopt Memory-Safe Languages” (Dark Reading)
- “NSA to developers: Think about switching from C and C++ to a memory safe programming language” (ZDNet)
- “NSA Publishes Guidance on Mitigating Software Memory Safety Issues” (SecurityWeek)
- Cloud
- Cybersecurity Snapshot
- Exposure Management
- Government


