Cybersecurity Snapshot: U.K. NCSC’s Best Cyber Advice on AI Security, the Quantum Threat, API Risks, Mobile Malware and More

In this special edition of the Cybersecurity Snapshot, we bring you some of the most valuable guidance offered by the U.K. National Cyber Security Centre (NCSC) in the past 18 months. Check out best practices, recommendations and insights on protecting your AI systems, APIs and mobile devices, as well as on how to prep for post-quantum cryptography, and more.
In case you missed it, here are six NCSC recommendations to help your organization fine-tune its cybersecurity strategy and operations.
1 - How to migrate to quantum-resistant cryptography
Is your organization planning to adopt cryptography that can resist attacks from future quantum computers? If so, you might want to check out the NCSC’s “Timelines for migration to post-quantum (PQC) cryptography,” a white paper aimed at helping organizations plan their migration to quantum-resistant cryptography.
“Migration to PQC can be viewed as any large technology transition. In the guidance, we describe the key steps in such a transition, and illustrate some of the cryptography and PQC-specific elements required at each stage of the programme,” reads a companion blog.

At a high-level, the NCSC proposes these three key milestones:
- By 2028
- Define the organization’s migration goals.
- Assess which services and infrastructure need to have their cryptography upgraded to PQC.
- Draft an initial migration plan that includes, for example, the highest priority migration steps; the necessary investment; and what you’ll need from your suppliers.
- By 2031
- Execute the first, most important PQC migration steps.
- Refine the PQC migration plan to ensure the roadmap will be fulfilled.
- Ensure your infrastructure is ready to support PQC.
- By 2035
- Complete your PQC migration.
Organizations need to migrate to PQC because quantum computers will be able to decrypt data protected with today’s public-key cryptographic algorithms. These powerful quantum computers are expected to become generally available at some point between 2030 and 2040.
The U.S. National Institute of Standards and Technology (NIST) last year released three quantum-resistant algorithm standards that are ready to be adopted. A fourth one is slated for release next year, and a fifth one, announced in March of this year, should be available in 2027.
For more information about how to protect your organization against the quantum computing cyber threat:
- “How to prepare for a secure post-quantum future” (TechTarget)
- “Moody’s sounds alarm on quantum computing risk, as transition to PQC ‘will be long and costly’” (Industrial Cyber)
- “Companies Prepare to Fight Quantum Hackers” (The Wall Street Journal)
- “US unveils new tools to withstand encryption-breaking quantum. Here's what experts are saying” (World Economic Forum)
- “Quantum is coming — and bringing new cybersecurity threats with it” (KPMG)
- “Quantum and the Threat to Encryption” (SecurityWeek)
2 - Why hardening your API security is key
After several high profile application programming interface (API) breaches, the NCSC published the guide “Securing HTTP-based APIs,” which urges organizations to update their methods for securing their APIs, including by using stronger authentication.
“Strengthening API security should not simply be seen as a protective measure; it can also enable organisations to enhance agility, simplicity and productivity,” reads a companion NCSC blog titled “New guidance on securing HTTP-based APIs.”

Unfortunately, many organizations rely on outdated API-security practices, including:
- Use of basic authentication
- Lack of rate-limiting and user-throttling capabilities
- Unprotected endpoints
- Code-stored credentials
- Use of URLs to transmit sensitive data
- Lax input validation
- Unencrypted API traffic via HTTPs
- Weak logging and monitoring
NCSC offers detailed recommendations to boost the security of your HTTP-based APIs in areas including:
- Development practices
- Authentication and authorization
- Protection of in-transit data
- Input validation
- Denial-of-service attack mitigation
- Logging and monitoring
- Exposure limitation
For example, NCSC recommends adopting strong authentication frameworks like OAuth 2.0 or token-based authentication. It also suggests doing a threat modeling analysis of your API design.
Another recommendation is to develop APIs’ applications in a secure development and delivery environment; and to use secure standards, such as JSON for data exchange and TLS cryptography for in-transit data.
For more information about API security:
- “OWASP API Security Project” (OWASP)
- “13 API security best practices to protect your business” (TechTarget)
- “4 Main API Security Risks Organizations Need to Address” (Dark Reading)
- “API security maturity model to assess API security posture” (TechTarget)
- “99% of Organizations Report API-Related Security Issues” (Infosecurity Magazine)
3 - Beware of global spyware campaign targeting mobile devices
The NCSC joined other cyber agencies to issue a warning about a spyware campaign aimed at infecting mobile devices of individuals and groups tied to causes that the Chinese government opposes.
However, all mobile users should take heed because the campaign is global and aggressive, meaning anyone could become a victim, according to the NCSC and cyber agencies from Australia, Canada, Germany, New Zealand and the U.S.
“The indiscriminate way this spyware is spread online also means there is a risk that infections could spread beyond intended victims,” reads the NCSC advisory.
Attackers are targeting supporters of various China-related movements with the BadBazaar and Moonshine spyware variants. Those targeted include journalists, non-governmental organizations, businesses and representatives of groups associated with:
- Taiwanese independence
- Tibetan rights
- Uyghur Muslims
- Hong Kong democracy advocacy
- Falun Gong movement

Moonshine and BadBazaar are two types of trojan malware, meaning attackers hide them in legit-looking mobile applications that users voluntarily download. In this particular campaign, attackers are embedding Moonshine and BadBazaar in applications designed to appeal to the intended victims, such as a Uyghur keyboard app and a Tibet-related app.
Once a user inadvertently installs a malicious app, attackers use it to obtain the mobile device’s location data in real-time; access its microphone and camera; retrieve stored messages and photos; and more.
Mitigation recommendations include:
- Don’t root or jailbreak your mobile device, as this leaves it more vulnerable to cyber attacks.
- Only download apps from trusted app stores like those from Google and Apple.
- Periodically review your installed apps and their permissions, deleting apps you no longer use and restricting excessive permissions.
- Be careful with links, files and apps shared on social media sites, online forums and messaging tools. Scan links with a URL reputation service before clicking on them, and upload suspicious files or apps to a malware analyzer.
To get more information, check out these NCSC resources:
- The announcement “NCSC and partners share guidance for communities at high risk of digital surveillance”
- The advisory “BadBazaar and Moonshine: Spyware targeting Uyghur, Taiwanese and Tibetan groups and civil society actors”
- The technical advisory “BadBazaar and Moonshine: Technical analysis and mitigations”
For more information about protecting mobile devices against spyware attacks:
- “How to find and remove spyware from your phone” (ZDNet)
- “Did you know a VPN can protect you from spyware? Here's how” (Yahoo Tech)
- “Your Android phone could have stalkerware — here’s how to remove it” (TechCrunch)
- “Apple: Mercenary spyware attacks target iPhone users in 92 countries” (BleepingComputer)
- “Why rebooting your phone daily is your best defense against zero-click attacks” (ZDNet)
4 - How corporate boards can boost their cyber governance
With cybersecurity governance now one of their main responsibilities, boards of directors need strong cybersecurity knowledge — but many are lacking in this area. That’s why the NCSC published a package of cyber governance resources for board members.
“From my experience of working with senior leaders across private and public sectors, I know that strong cyber governance is key to resilience, growth, and long-term success. Board members play a vital role in making this happen,” NCSC CEO Richard Horne wrote in a blog.

The NCSC cyber governance resources for board members include:
- The “Cyber Governance Code of Practice,” which outlines the board’s responsibilities in these five key governance areas:
- Risk management
- Strategy
- People
- Incident planning, response and recovery
- Assurance and oversight
- The “Cyber Governance Training” document, which provides five interactive training modules, each focusing on one of the “Code of Practice” principles
- The “Cyber Security Toolkit for Boards,” which explains how to implement the five key cyber governance areas
For example, the risk management the toolkit unpacks how to identify the organization’s critical assets and how to collaborate with its supply chain partners. In the strategy area, it goes into how to embed cybersecurity into the organization and what cybersecurity regulations are relevant to boards.
For more information about cyber governance guidance for boards of directors:
- “Principles for Board Governance of Cyber Risk” (Harvard Law School)
- “NACD Director's Handbook on Cyber-Risk Oversight” (National Association of Corporate Directors)
- “A cybersecurity guide for board directors” (Corporate Governance Institute)
- “How boards can effectively oversee AI to drive value and responsible use” (PwC)
- “Guidelines on the Corporate Governance of Cybersecurity” (Board Foundation)
5 - Why AI will boost the quantity and intensity of cyber attacks
The volume and impact of cyber attacks, including ransomware, will grow as malicious actors of all stripes incorporate AI into their toolboxes.
Still, how the bad guys use AI and what benefits they get from it will depend on their level of skill and knowledge, the NCSC said in its January 2024 report “The near-term impact of AI on the cyber threat.”
Here’s a table with a nice breakdown of how the NCSC projects that AI will supercharge the cyber attack capabilities of cyber criminals with different levels of sophistication by the end of 2025.
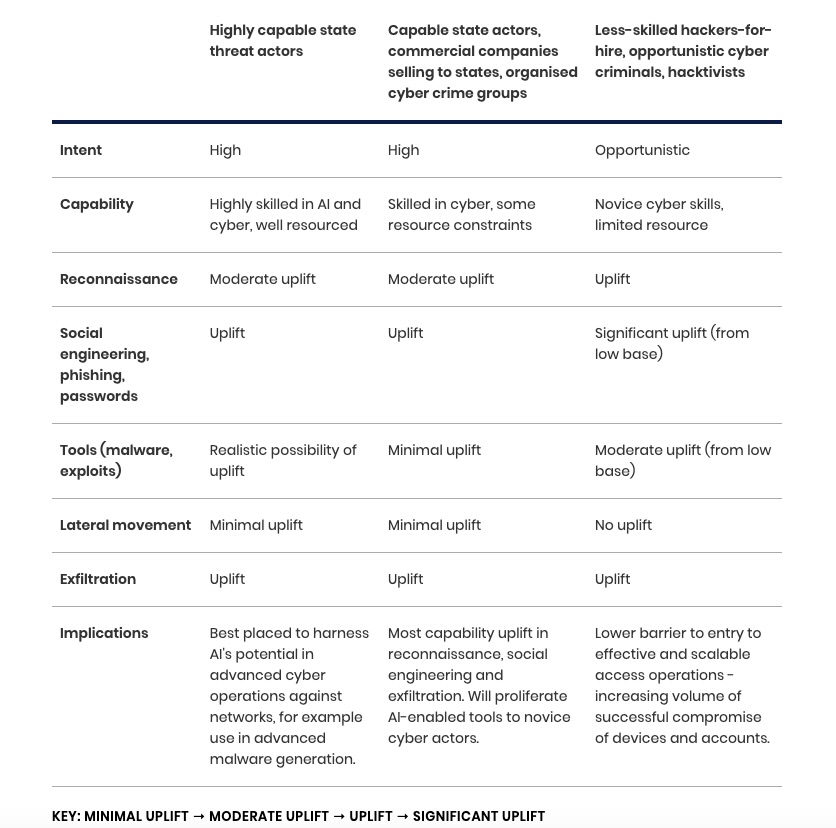
(Source: NCSC’s “The near-term impact of AI on the cyber threat” report, January 2024)
In a companion statement, the NCSC highlighted how AI will likely heighten the already critical threat from ransomware by making it easier in particular for unskilled hackers to launch more effective cyberattacks.
“This enhanced access, combined with the improved targeting of victims afforded by AI, will contribute to the global ransomware threat in the next two years,” the NCSC statement reads.
For more information about how to address AI-powered cyberattacks:
- “Skilling up the security team for the AI-dominated era” (CSO Online)
- “How Zero Trust Can Protect Systems Against Generative AI Agents” (Dark Reading)
- “How to combat AI-produced phishing attacks” (SC Magazine)
6 - How to secure network edge devices
The NCSC recently joined fellow cyber agencies to provide insights and best practices for preventing and mitigating cyber attacks against network edge hardware and software devices, which have become a major target in recent months.
“In the face of a relentless wave of intrusions involving network devices globally our new guidance sets what we collectively see as the standard required to meet the contemporary threat,” NCSC Technical Director Ollie Whitehouse said in a statement.
“In doing so we are giving manufacturers and their customers the tools to ensure products not only defend against cyber attacks but also provide investigative capabilities require post intrusion,” Whitehouse added.
Devices at risk include routers, VPN gateways, IoT devices, web servers and internet-facing operational technology (OT) systems.

These are the new guides:
- Security Considerations for Edge Devices, led by the Canadian Centre for Cyber Security (CCCS), includes:
- A description of common threats to edge devices, such as misconfigurations and mismanagement; vulnerability exploitation; and denial of service attacks
- Examples of edge device compromises
- Recommendations for mitigating threats to edge devices
- Digital Forensics Monitoring Specifications for Products of Network Devices and Applications, led by the U.K.’s National Cyber Security Centre (NCSC), explains why and how edge devices should support event logging and forensic data acquisition.
- Mitigation Strategies for Edge Devices: Executive Guidance and Mitigation Strategies for Edge Devices: Practitioner Guidance, two guides led by the Australian Cyber Security Centre (ACSC), focus on threat mitigation and are aimed, respectively, at executives responsible for enterprise network security; and at operational, cybersecurity and procurement staff for edge devices.
For more information about network edge vulnerabilities, check out these Tenable blogs:
- “New CISA Hardening Guidance Provides Valuable Insights for Network Security Engineers”
- “Verizon 2025 DBIR: Tenable Research Collaboration Shines a Spotlight on CVE Remediation Trends”
- “Volt Typhoon: U.S. Critical Infrastructure Targeted by State-Sponsored Actors”
- “CVE-2025-0282: Ivanti Connect Secure Zero-Day Vulnerability Exploited In The Wild”
- “CVE-2024-21762: Critical Fortinet FortiOS Out-of-Bound Write SSL VPN Vulnerability”
- “CVE-2023-20198: Zero-Day Vulnerability in Cisco IOS XE Exploited in the Wild”
- Cloud
- Cybersecurity Snapshot
- Endpoint security
- Federal
- Government
- Malware
- Mobile Security


