Why Early Visibility Matters: Risk Lurks in the Vulnerability Disclosure Gaps

It seems pretty obvious: If an attacker can exploit a vulnerability before you can patch it, your organization is at risk. Yet the gaps between different phases of the vulnerability disclosure process continue to leave security teams in the dark.
Key takeaways:
- Of the 63,862 CVEs issued between Jan. 1, 2024 and Sept. 30, 2025, 2.6% had a public proof-of-concept (PoC) published.
- More than half of these (56%) had a PoC published in less than seven days.
- Yet, it takes on average 15 days for a vulnerability to be published to the National Vulnerabilities Database, which is used as the core data source for a number of scanning tools, leaving security teams at risk.
Vulnerability management is often described as a race against the attackers. If an attacker can exploit a vulnerability before you can patch it, the results can be devastating.. This is why the time lapse between vulnerability disclosure to exploitation is critical; the longer defenders go without visibility into new vulnerabilities, or awareness that those vulnerabilities are being exploited, the greater the risk that their organizations will be compromised.
There are several key phases in the typical vulnerability timeline that are worth noting:
- Publication of a vulnerability advisory, at which time the common vulnerabilities and exposures (CVE) number issued by a CVE Naming Authority is typically initially made public. The CVE catalog is managed by MITRE.
- Publication to the National Vulnerabilities Database (NVD). While a CVE number can be assigned immediately upon publication of an advisory, more detail is needed before it can be evaluated by NIST and assigned a score on the NVD.
- The publication of a proof-of-concept (PoC), often considered an important first step in a vulnerability being leveraged by attackers.
- Disclosure of a functional exploit to one of the major exploit frameworks.
- Disclosure of known exploitation.
The gaps in time between when a CVE is made public, when it appears in MITRE, and when that CVE is published on NVD create blind spots for cybersecurity organizations. Additional risk lurks in the time lapses between each of the subsequent phases of a vulnerability's lifecycle.
In this article, we look at timelines for CVEs from 2024 and 2025, analyzing key points along those timelines and showing how Tenable is often at the leading edge of visibility whether a vulnerability is newly disclosed or being exploited in the wild or at any point in between.
Between Jan. 1, 2024 and September 30, 2025 there were 63,862 CVEs disclosed. Of these:
- 774 received a CVSSv3 severity rating of High and 478 were Critical
- 2.6% (1,665) have a known public PoC published — specifically exploit code that has been publicly disclosed.
- .5% (314) have documented evidence of active exploitation in the wild, slightly more than the 253 in the CISA Known Exploited Vulnerabilities (KEV) catalog.
Relying on disclosure to NVD introduces risky gaps
While NVD is used by a number of scanning tools as a core data source and it is sometimes seen as the starting point in disclosure, in reality it is typically at the tail end of CVE publication. It is only after a CVE has been reserved by a CNA, issued by that CNA, published to MITRE, and then further analyzed by NIST that it is then published to NVD.
It is true that progress has been made on this process, particularly for some vendors, but our analysis of CVEs published in 2024 and 2025 shows there is still a fairly significant lag. For this analysis, we focused on CVEs that Tenable covered, as these will typically have better data on initial disclosure. We found that the average delay from initial vulnerability disclosure to NVD was 15.2 days. This means anyone dependent on NVD for vulnerability information is over two weeks behind the curve, on average, before they learn about a vulnerability.
This lag becomes even more concerning when we look at the time between disclosure and PoC or, even worse, exploitation in the wild — both events that correspond to a significant increase in risk.
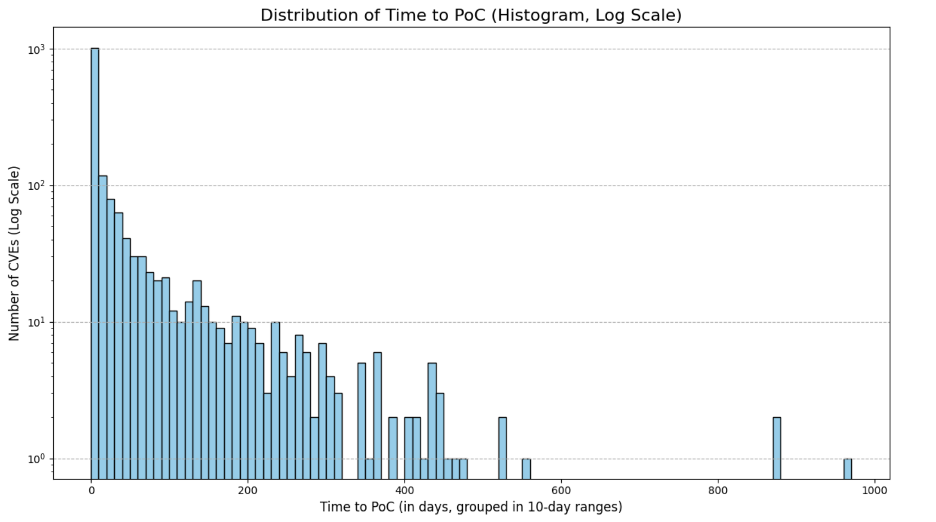
Disclosure to PoC puts attackers on alert
One of the major events that can occur in the lifecycle of a vulnerability is the publication of a PoC. The reality is that a vast majority of published CVEs never have a PoC published and even fewer are actually exploited, with our analysis showing evidence of PoC for 1,665 of the CVEs in the set we analyzed. The publication of a PoC is often considered an important first step in a vulnerability being leveraged by attackers. PoC code, no matter how rudimentary it is, can provide details about the vulnerability and how to exploit it. Attackers can take this code, adjust it, improve it, then use it as part of an attack.
The lag time to NVD is even more concerning when we consider how quickly PoCs are published. More than half (56%) of the 1,665 CVEs we analyzed had a PoC published in less than seven days. That's half the time, on average, that it takes for CVEs to be published to NVD.
On average, it took 43 days for a PoC to be published, but that number is heavily skewed by the small set of vulnerabilities that did not see a PoC published until many months after initial disclosure.
Disclosure to functional exploit: less common, no less concerning
We consider an exploit to be functional in cases where it is added to one of the major exploit frameworks but not necessarily being actively exploited in the wild. The disclosure of a functional exploit is another maturity step that lowers the bar for attackers because the code for these is typically more mature and has a higher success rate. Interestingly, both the average and median time to functional exploit is significantly lower than the time to PoC, but this is likely because far fewer vulnerabilities get a functional exploit, skewing the results. The average time between publication of a CVE and publication of a functional exploit is around 21 days while the median is only three days.
Disclosure to known exploitation: the most significant risk
Most critically, the active exploitation of a vulnerability is where we see the most significant risk. This means that the vulnerability is being leveraged in active attacks, as opposed to simply having published exploit code that may or may not function.
For this analysis we looked at two data sets — the widely known CISA KEV as well as Tenable’s own Vulnerability Intelligence database, which is curated independently of CISA. For each, we looked at the average time between when a vulnerability is first disclosed and when it is identified as having known exploitation in the wild.
| Source | Days |
|---|---|
| Average time to Tenable Known Exploited | 42 |
| Average time to CISA Known Exploited | 50 |
| Median time to Tenable Known Exploited | 5 |
| Average time to CISA Known Exploited | 10 |
Source: Tenable Research, October 2025
The above table reflects the fact that some CVEs skew the average number of days quite high. If we look at the median, we see it took 10 days for a CVE to be added to the CISA KEV; this means that, for those relying on NVD, a vulnerability could have been actively exploited a full five days before it appeared in the NVD.
Further, based on our own tracking, we can see that active exploitation often happens even sooner than when the CVE is added to the CISA KEV catalog. The Tenable KEV shows that the median time to active exploitation for the CVEs we analyzed was only five days.
The bottom line? If you are driving your vulnerability management programs off NVD you may not even be aware of the existence of a vulnerability before it is exploited in the wild.
What this all means for security teams
With time-to-exploitation taking days, not weeks, timely awareness of vulnerabilities and the risk they present is critical. Because Tenable drives its coverage directly from vendor advisories, a majority of our coverage is available within 12-24 hours of the initial disclosure of a vulnerability. This ensures that, with the exception of zero days, Tenable customers have the ability to find and remediate vulnerabilities much more quickly, thereby reducing risk. Tenable Research is constantly monitoring the threat landscape to ensure that we identify the most critical vulnerabilities — those with known active exploitation — as soon as that exploitation begins.
Learn more
Relying on EDR for Exposure Management: What You Need to Know
Study: Tenable Offers the Fastest, Broadest Coverage of CISA's KEV Catalog
Mind the Gap: How Waiting for NVD Puts Your Organization at Risk
- Exposure Management
- Vulnerability Management



