Building a Successful Industrial Security Strategy in a Converging IT-OT World

Plant managers and IT technicians traditionally occupy different parts of the organization. But as connected technology brings new industrial devices online, both sides must work together to mitigate cyber threats across the expanding attack surface.
There has been quite a lot of buzz the past few years around IT (information technology) and OT (operations technology) security convergence.
Much of the discussion has centered around opportunities to improve efficiency and availability – or the cybersecurity risks associated with IT/OT network convergence. But organizations are also struggling to balance mutually exclusive or overlapping projects, requirements, budgets, objectives, people and technology.
Trying to find common ground between IT staff and engineers on the plant floor is a tough endeavor. But it’s the only viable option when aligning IT and OT networks with enterprise-level goals.
The culture clash between IT and OT environments
Delivering successful IT projects is quite different than in OT environments. Regulations, standards, project management, equipment, manufacturers, partners, technology and goals all draw from two different sides of the knowledge spectrum.
Even their work cultures are different. IT is a dynamic environment, with systems that are patched, upgraded and replaced on a regular basis. IT is concerned about data confidentiality, integrity, and availability (i.e. “CIA”). Conversely, OT environments prioritize stability, safety and reliability. Their jobs involve the maintenance of complex and sensitive environments such as oil refineries, chemical plants and water utilities. Often the legacy systems underlying these operations were implemented long ago and haven’t changed for decades. The OT motto often goes, “if it works, don’t touch it.”
This tension runs both ways. Engineers don’t want to be involved with IT, nor do they want IT coming into their space. And IT teams don’t want to be in the plant; their world is the data center. Neither side wants to cede control to the other, and for good reason. You wouldn’t want IT controlling the safety systems of the chemical plant. You obviously can’t “reboot” a complex and potentially explosive industrial chemical process. But you also wouldn’t want the plant engineer running your perimeter firewalls.
And yet, despite these clashes in culture, it’s more and more common that we see business objectives that require a holistic IT/OT approach, utilizing both information and operations technology.
Case study: Water utility pumping stations
Take, for example, the situation faced by one of our customers: a water utility with hundreds of pumping stations distributed across acres of land. Its engineering team is tasked with monitoring the vibrations of these pumps as a means to detect malfunctions. Yet, the IT team refuses to enable remote connectivity due to cybersecurity concerns, unless a VPN (or virtual private network) connection is utilized.
Concerned that a VPN solution would take a long time to approve and implement, the engineers decide to purchase a cheap, disk-on-key cell modem from eBay and connect the programmable logic controller (PLC) directly to the internet. This enables them to log in from their home laptops to perform monitoring and maintenance.
Voila! In their minds, the cell modem solves the problem, and there is no need to involve or seek approval from IT. This is how engineers are trained to think - to solve problems and work through obstacles. However, creative solutions can introduce other problems and cybersecurity issues, and they often can’t scale to meet business needs.
Meanwhile, the IT department, hundreds of miles away, is unaware of the creative solution implemented by the engineers. They are debating how best to enable remote connectivity – by installing Ethernet or Wi-Fi in the water plant. Each has advantages and drawbacks. But planning without feedback from the plant engineers would be foolish.
If IT implements a Wi-Fi solution without knowledge of the pump’s monitoring sensor requirements, it may not solve any issues for the engineer. Ethernet connectivity to the pumps might enable engineers to monitor vibration, but it also requires running Ethernet to every single pump, which can’t accommodate changes if a pump location is moved.
It’s easy to see from this example that having experts who can speak both languages – IT and OT – is already a make-or-break factor in the successful application of technology in the industrial world. This is especially true when it comes to industrial cybersecurity projects, which almost always require both IT and OT specialists.
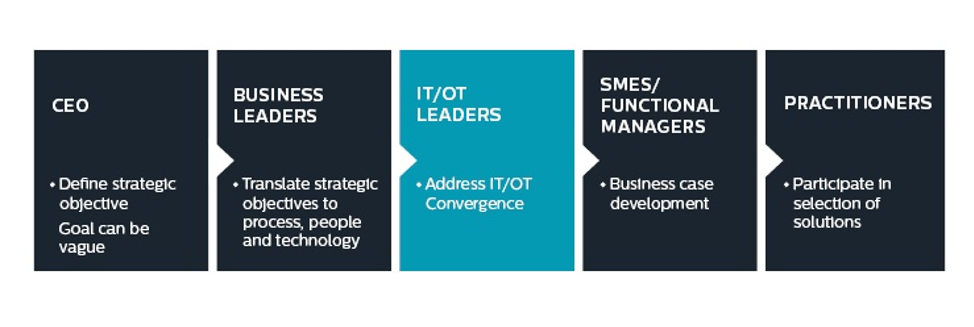
Appointing an IT-OT convergence champion
Organizations are more likely to succeed if they have a role built into the organization that can translate strategic objectives from business leaders to IT/OT subject matter experts.
Successful deployment of industrial cybersecurity projects will leverage resources from both IT and OT. Business-level oversight and leadership ensure that the different cultures don’t clash but instead work together, and eventually complement each other to provide even greater value to the organization.
To enact this vision, organizations are taking senior, experienced engineers from the various OT business units, which usually report into the chief operations officer, and moving those individuals under the chief information officer hierarchy, resulting in leadership roles that can straddle both sides of the IT/OT fence.
In our water utility example, if the customer had an IT/OT leader in place, that person would be responsible for providing a solution that addresses the needs of the engineers and IT staff, as well as the overall business. This person would lead an overarching IT/OT security convergence strategy that addresses everything from cybersecurity and safety to ongoing maintenance and procedures, resulting in sustainable, industrial-grade, enterprise-wide solutions.
Some organizations have taken this even further. Instead of building IT roles under the CIO, they create a new, C-level role to facilitate this strategy. It’s no longer uncommon to find a chief digital officer on the leadership team who helps bridge the gap between the COO and chief technology officer.
The higher up the organizational ladder that IT/OT convergence decisions are being made, the higher the chances for success, and the more likely your team can minimize future security risks while capitalizing on the upside of digital transformation.
For more information and best practices on improving cross-team collaboration, check out our whitepaper, “Mind the Gap: A Roadmap to IT/OT Alignment.”
- SCADA


