All your security data.
All in one place.
Unlock the power of exposure management with a single, prioritized view of risk when you connect all of your third-party data with Tenable One.
Exposure management news and resources
Unify to defy risk
Radically unify security visibility, insight and action across the attack surface with Tenable One, the world’s leading exposure management platform. Eradicate priority cyber weaknesses and protect against attacks—from IT infrastructure to cloud environments to critical infrastructure and everywhere in between.


Comprehensive inventory
Dynamic attack path mapping
Predictive prioritization
Mobilization & remediation
Advanced analytics & reporting

Accelerate search, insight and action with generative AI that uncovers hidden risks and amplifies security expertise across your environment.
Gain a unified view of all your assets and risk across your attack surface: unseen assets, IT, OT, IoT, cloud, identities and applications.
Understand attacker accessibility through visualizations of cross-domain relationships, enabling you to block the most critical attack paths.
Focus your efforts on what matters most: the critical exposures that are most likely to be exploited in an attack.
Accelerate response with automated workflows and prescriptive guidance that streamline remediation efforts.
Streamline measurement and communication of cyber exposure with business-aligned views that help you optimize decision making and investments.
Access the most comprehensive threat and vulnerability knowledgebase, combining insights from Tenable Research, NVD and trusted third-party sources.
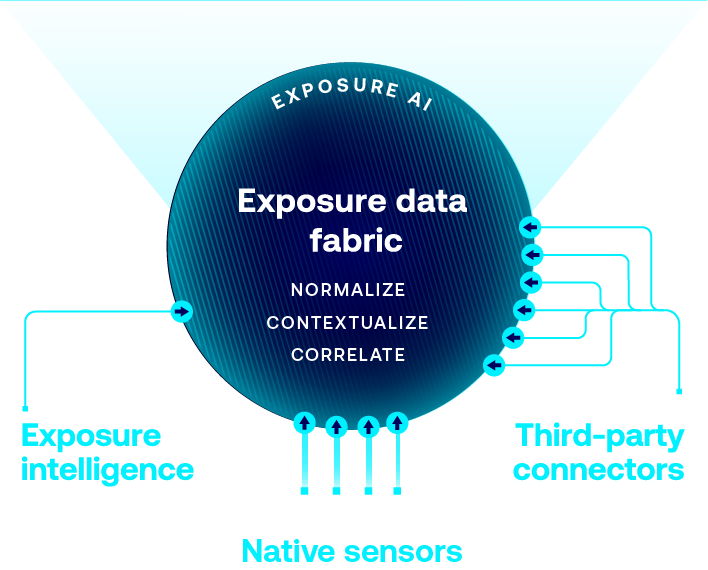
Native attack surface discovery for cloud, identities, IT, IoT, OT, applications, containers, kubernetes, etc., that is fueled by Tenable product sensors.
Seamlessly connect asset and exposure data from your existing tools to enrich Tenable intelligence and deliver comprehensive exposure context.
Leverage the world’s largest repository of asset, exposure, and threat context that powers ExposureAI’s unparalleled insights.
Organize data to reduce redundancy and improve integrity, consistency and efficiency.
Enrich data with additional insights, making it more actionable and useful.
Identify and surface critical relationship context to core business services and functions.
Close cloud exposure
With the actionable cloud security platform for cloud risk
Know your cloud resources.
Collapse fragmented views and reveal your 360-degree cloud resource reality.Expose critical cloud risks.
See how cloud risks are combining and escalating across your attack surface.Close cloud exposure.
Reduce cloud risk by closing priority exposures with top speed and surgical precision.
Close vulnerability exposure
With the world’s #1 vulnerability management solution
Know all types of vulnerabilities.
Reveal impactful vulnerabilities across your IT environment.Expose priority gaps.
Quickly spot priority exposures with a high likelihood of attack and business impact.Close critical exposures.
Take rapid, decisive action to close critical exposures and execute remediations.
Close OT exposure
With the unified security solution for converged OT/IT environments
Know every OT/IT asset.
See every asset in your converged environment from a single interface.Expose your lethal gaps.
Proactively identify weak points that pose a threat to your business.Close priority exposures.
Eradicate your high risk exposures before they’re exploited.
Close identity exposure
With the essential solution for the identity-intelligent enterprise
Know your complete identity reality.
Unify all identities across Active Directory, hybrid and Entra ID.Expose your top identity gaps.
Uncover how cloud risks are interacting and escalating across your attack surface.Close identity-based exposures quickly.
Rapidly close security gaps with the highest likelihood of identity-based exploits.
Collective insight, individual might
Keep your enterprise ahead of threats with cyber risk insights from Tenable Research, the largest exposure management research organization in the industry. Review common vulnerabilities and exposures (CVEs) from around the world and access the threat intelligence, data science insights, alerts and security advisories that matter.
Explore the latest research99K K
Vulnerabilities assessed
with 251,000+ plugins
733
Vulnerabilities disclosed
by Tenable Research
< 24 hrs
Median time for coverage
of high profile issues
Trusted by more than 44,000 customers

Recognized for excellence
As the pioneer and world leader in exposure management, we never rest until we set the bar for what’s next.
View more awards
Tenable research
What's your exposure?
Across the thousands of vulnerabilities keeping you up at night, only 3% are true exposures that put your business at risk. But how do you know what matters? A new watershed report from Tenable Research uncovers the truth about where enterprises are exposed and what they can do to close it.
See Tenable in action
Want to see how Tenable can help your team expose and close the priority cyber weaknesses that put your business at risk?
Complete this form for more information.




