by Stephanie Dunn
June 20, 2016
As network infrastructures continue to add new devices and services on a network, detecting and managing the growing number of vulnerabilities can be complicated for any organization to handle properly. Many organizations employ vulnerability scanners that perform active scanning, but can miss hosts or devices that may have connected in between scans. Passive listening enables organizations to detect vulnerabilities on hosts or other devices that were inactive or temporarily connected to the network in between active scans. This information can help to detect additional client or server-side vulnerabilities that can leave critical systems at risk. Information presented within this dashboard can assist analysts in discovering the top passively detected vulnerabilities on a network.
As organizations continue to invest in cloud and mobile solutions, having multiple ways to scan the network without overwhelming resources is key in helping to detect and maintain an accurate inventory of network assets. Using both active scanning and passive listening provides organizations with a complete and accurate view of existing hosts and network devices. Both methods can help to detect vulnerabilities with web servers such as Apache, or client-side vulnerabilities such as outdated browsers, or exploits within Flash or Java.
Tenable offers the industry’s broadest coverage of detecting vulnerabilities through active scanning, agent scanning, passive listening, and intelligent connectors. For more information on how Tenable can assist organizations with creating an effective vulnerability management program, please see the Comprehensive Vulnerability Management for a Changing IT Landscape blog post.
This dashboard presents a comprehensive summary of passively detected vulnerabilities on the network. Summary information can help analysts identify the most critical and exploitable vulnerabilities first, which can help to streamline vulnerability remediation efforts. Indicators can alert security teams to potentially unauthorized services in use, misconfigurations, or vulnerabilities on critical systems. Highlighting client and server-side vulnerabilities can help identify existing vulnerabilities by function, and can assist with patch management and prioritization. Using this dashboard, organizations will obtain real-time information that can assist with prioritizing and reducing overall security risks within the enterprise.
This dashboard is available in the Tenable.sc enter Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Discovery & Detection. The dashboard requirements are:
- Tenable.sc 5.3.2
- NNM 5.9.0
Tenable automatically analyzes information from active scanning, intelligent connectors, agent scanning, passive listening, and host data in order to provide continuous visibility and critical context. Active scanning periodically examines hosts within the organization to determine risk. Intelligent connectors leverage other security investments to provide additional context and analysis. Agent scanning enables assessing systems without the need for ongoing host credentials. Passive listening detects hosts that were offline during active scans, and provides real-time monitoring of host activity throughout the network. Host data is analyzed to correlate real-time events, monitor firewall traffic, and identify malicious attacks. The combination of these sensors provides organizations with the tools they need to proactively detect, monitor, and respond to threats within the enterprise.
The following components are included in this dashboard:
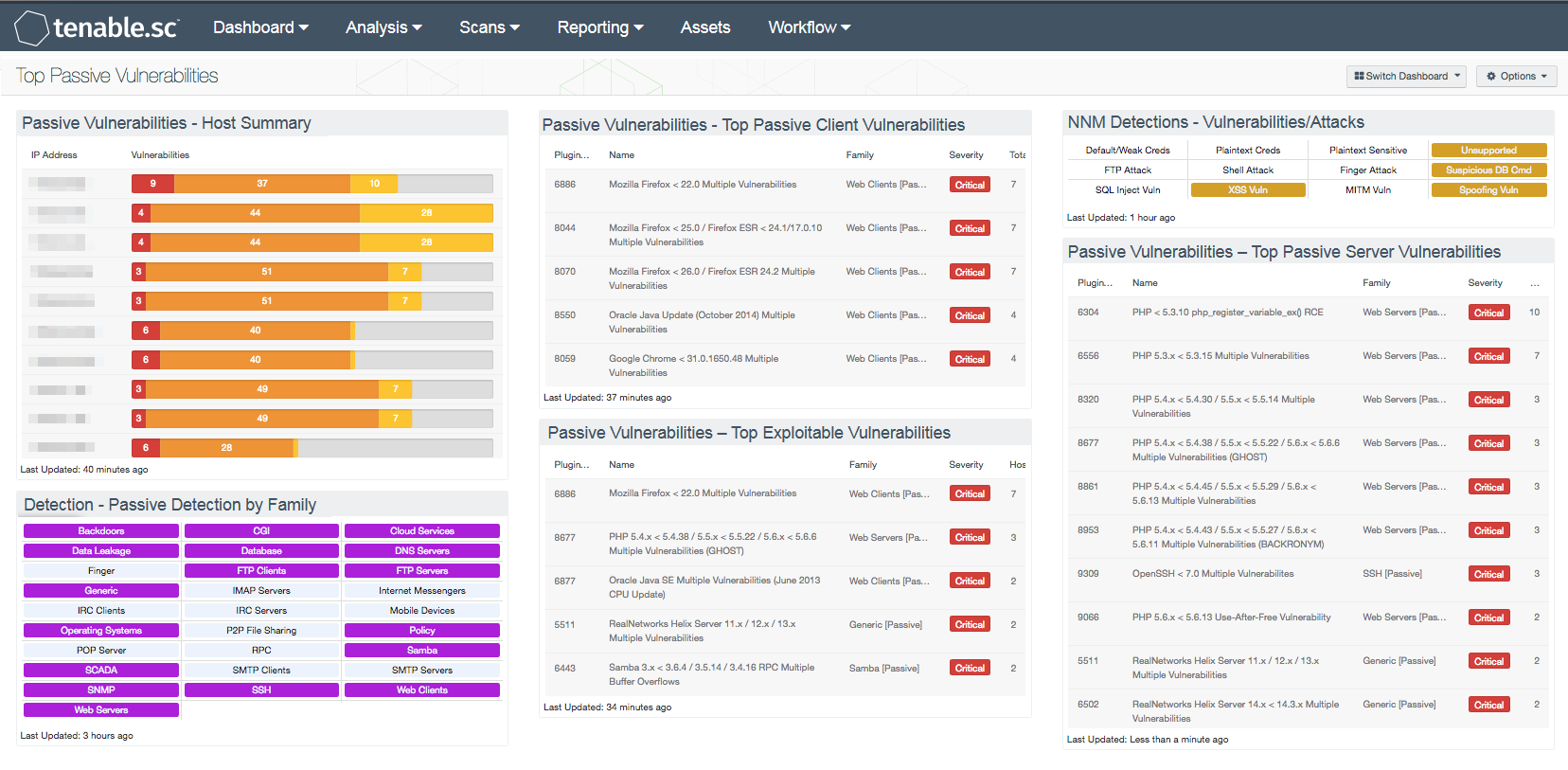
- Passive Vulnerabilities - Host Summary: The Host Summary table presents those hosts that are most vulnerable, in terms of passively detected vulnerabilities. The list of hosts is sorted by score and the bar graphs include Critical, High, and Medium severity level vulnerabilities. This information can help organizations to assess and prioritize current risks.
- Detection - Passive Detection by Family: This matrix component triggers on passive detection plugins. Passive plugins are plugins used by Nessus Network Monitor (NNM) during passive network scanning. The matrix cells provide an indicator filtered by detection plugins along with the passive plugin family. When no alert is present, the indication remains off (or uncolored); if an alert is present, the indication changes to a purple. The analyst may click on the indicator to retrieve a vulnerability list that includes the Plugin ID, Plugin Name, Family, Severity, IP Address, NetBIOS, DNS and MAC address that matches the query.
- Passive Vulnerabilities - Top Passive Client Vulnerabilities: The Top Passive Client Vulnerabilities table presents a list of the top passively detected client vulnerabilities on the network. The list is sorted so that the most critical vulnerability is at the top of the list, and includes the severity and number of hosts affected. Data is reported by the Nessus Network Monitor (NNM), which detects hosts with client-based vulnerabilities such as web browsers, Java, Flash, and more. Analysts can drill down to obtain additional information on the hosts affected, and solutions to remediate the vulnerabilities.
- Passive Vulnerabilities – Top Exploitable Vulnerabilities: The Top Exploitable Vulnerabilities table presents the top exploitable vulnerabilities detected by the Nessus Network Monitor (NNM). The list is sorted so that the most critical vulnerability is at the top of the list, and includes the severity and number of hosts affected. Information presented within this table consist of both client and server-based vulnerabilities that are frequently targeted by attackers. Analysts can drill down to obtain additional information on the hosts affected, and solutions to remediate the exploitable vulnerabilities.
- NNM Detections - Vulnerabilities/Attacks: This matrix displays indicators for vulnerabilities and attacks detected by NNM. These vulnerabilities/attacks include observed issues with credentials and sensitive data, unsupported software, network attacks, suspicious database commands, and common known vulnerabilities of detected applications.
- Passive Vulnerabilities – Top Passive Server Vulnerabilities: The Top Passive Server Vulnerabilities table presents a top 10 list of the most common server vulnerabilities passively detected on the network. Data is filtered to detect hosts with passive server-based vulnerabilities that may include PHP, Samba, Apache, SSH, SQL Server, and more. The list is sorted so that the most critical vulnerability is at the top of the list, and includes the severity and number of hosts affected. This table can provide detailed information to remediate existing vulnerabilities and reduce overall risk.