by Ben Smith
March 12, 2020
The United Arab Emirates’ (UAE) National Electronic Security Authority (NESA) Information Assurance Standards state that an organization should have appropriate vulnerability management in place. The NESA standard includes many controls related to vulnerability management across a wide variety of devices. Tenable.sc includes active scan aggregation and vulnerability management. This dashboard provides risk managers with clear visibility into the state of vulnerability across the organization.
A critical focus of NESA compliance is identifying vulnerabilities in the environment. NESA requires identifying and remediating vulnerabilities throughout the network. To aid in this process, Tenable.sc tracks when vulnerabilities are mitigated and provides two metrics: patch rate and patch date. Patch rate shows how long vulnerabilities took to patch. Patch date shows the number of days since the patch was applied. Several NESA controls require patching vulnerabilities within a reasonable amount of time where the timeline is determined by the organization and by the organization’s risk ranking or cost-benefit analysis. These controls include M2.1.1, M2.2, M2.4, T4.2.5, T7, T7.5.1, T7.7, T7.8.6, and T8.3. Tenable.sc can also show exploitable vulnerabilities to help aid in the risk ranking process.
The first stage in a successful Cyber Exposure program requires discovery of assets on the network. NESA controls T1.2, T2.3.3, and T5.4.3 each require knowledge of assets and the appropriate identification, categorization, and protection of these assets. Tenable.sc shows identification and aids in analysis by grouping assets by the plugin families reported. The asset categories can then be prioritized based on vulnerability criticalities, classification, and the organization’s own risk ranking.
Knowing the types of assets on the network also aids in another NESA requirement, for example NESA T4.2.5. Identifying known vulnerabilities in administrative, accounting, and business communications systems. Vulnerability assessments should be performed frequently and after any risk assessment or control implementation. Tenable.sc allows aggregation of regular scan data, assisting the consultant in verifying that such requirements are met. Similarly, NESA controls T7.5.1 and T7.8.2 require software to be maintained at a level supported by the supplier. Tenable.sc shows plugins related to unsupported applications and operating systems, assisting in identification. Additionally, NESA controls T3.4, T3.4.1, T3.6.2 and T5.7.2 require assets to be protected from malware. Tenable.sc can use local checks and active plugins to show assets that have out-of-date definitions and other antimalware and endpoint protection related vulnerabilities.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Executive.
The dashboard requirements are:
- Tenable.sc 5.12.0
- Nessus 8.9.0
- Compliance Data
Tenable.sc Continuous View (CV) is the market-defining On-Prem Cyber Exposure Platform. Tenable.sc CV provides the ability to continuously Assess an organization’s adherence to best practice configuration baselines. Tenable.sc provides customers with a full and complete Cyber Exposure platform for completing an effective Cyber Hygiene program prescribed by NESA standard.
This dashboard contains the following components:
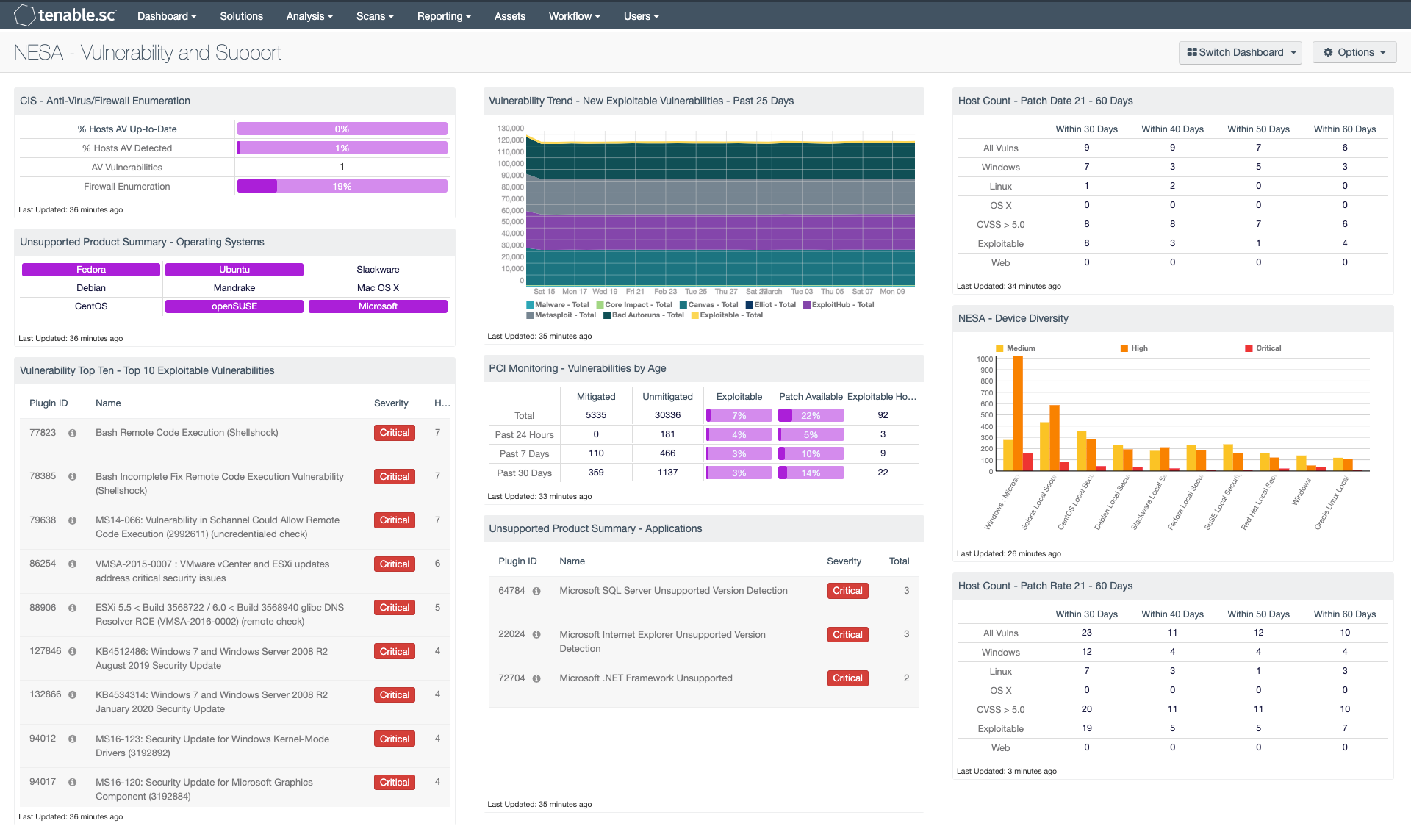
CIS - Anti-Virus/Firewall Enumeration: This matrix assists the organization in monitoring anti-virus (AV) solutions and firewall settings. The "% Hosts AV Up-to-Date" column displays the percentage of total systems that have AV installed and are working properly; the "% Hosts AV Detected" column displays the percentage of total systems on which AV has been detected, whether or not the AV is working properly. The "AV Vulnerabilities" column displays the number of detected vulnerabilities related to AV. The Firewall Enumeration provides all the devices where the host based firewall rules have been collected. Clicking on a highlighted indicator will bring up the analysis screen to display details on the detections for further investigation.
Unsupported Product Summary - Operating Systems: This indicator matrix reports on operating systems that are no longer supported. The matrix displays popular operating systems but is easily modified to fit organizational requirements. Plugin ID #33850, with vulnerability text filters that filter for the appropriate operating system name in the plugin output, alert on Unix-based operating systems that are no longer supported. Keyword filters, along with a CPE string for Microsoft, is used to alert on end-of-life Microsoft operating systems by turning the indicator purple when a vulnerable asset is present.
Vulnerability Top Ten - Top 10 Exploitable Vulnerabilities: This table displays the top 10 exploitable vulnerabilities on the network. The list is sorted so that the most critical vulnerability is at the top of the list. For each vulnerability, the severity and the number of hosts affected is shown. This will be helpful for those getting started with SecurityCenter.
Vulnerability Trend - New Exploitable Vulnerabilities - Past 25 Days: The Vulnerability Trend – New Exploitable Vulnerabilities – Past 25 Days area chart shows the trend of exploitable vulnerabilities over the past 25 days. Trends for seven exploit frameworks are displayed, along with an overall exploitable trend. The data presented is based on vulnerabilities observed in a 24-hour span. This component helps analysts to understand which exploit frameworks their network is most susceptible to in addition to whether hardening efforts against various frameworks are effective over time.
PCI Monitoring - Vulnerabilities by Age: The “PCI Monitoring - Vulnerabilities By Age” matrix component displays an overview of vulnerabilities over time. Each row focuses on vulnerabilities first detected within a specific timeframe, in order to allow analysts to monitor vulnerabilities over time. The first two columns show the totals of vulnerabilities that have been and have not been mitigated. The matrix also shows the percentages of vulnerabilities that are exploitable, the percentage of vulnerabilities that have patches available, and the count of hosts with exploitable vulnerabilities. Analysts can use this matrix to identify and monitor vulnerabilities in context.
Unsupported Product Summary - Applications: The table displays unsupported applications by name and sorted by severity. Displayed is the plugin ID, application name, plugin family, severity, and the total host count found. This component utilizes the keyword “unsupported” in the plugin name field. Additionally the table filters based on severity, dropping any informational results, and presents them via the Vulnerability Summary tool.
Host Count - Patch Date 21 - 60 Days: This component has 4 columns, showing a range of patch dates from 21 - 60 days. Each column has an explicit date range. They are:
Within 30 days - 21 to 30
Within 40 days - 31 to 40
Within 50 days - 41 to 50
Within 60 days - 51 to 60
The patch date refers to the 'Days Since Mitigation' filter. The 'Days Since Mitigation' allows the user to filter results based on when the vulnerability was mitigated.
NESA - Device Diversity: This component shows the breadth of device types in the environment. Broken down by vulnerability severity, the component details devices by plugin family. This is especially useful to understand which classes of device to remediate first.
Host Count - Patch Rate 21 - 60 Days: This component has 4 columns, showing a range of patch rates from 21 - 60 days. Each column has an explicit date range. They are:
Within 30 days - 21 to 30
Within 40 days - 31 to 40
Within 50 days - 41 to 50
Within 60 days - 51 to 60
The component displays the patch rate referring to the 'Days to Mitigate'. The 'Days to Mitigate' filter allows the user to track the number of days since a vulnerability was moved to the mitigated database.