by Ben Smith
March 3, 2020
The United Arab Emirates’ (UAE) National Electronic Security Authority (NESA) Information Assurance Standards state that an organization should have appropriate configuration management in place. Tenable.sc includes audits files based on the CIS Benchmarks which are mapped to a wide variety of compliance standards including NESA and ISO 27000. This dashboard provides risk managers with a clear visibility into configuration hardening and overall compliance status.
A critical focus on NESA compliance is ensuring devices conform to generally accepted hardening standards. Tenable.sc provides visibility into system configuration policies and vulnerability management controls. When implementing a successful Cyber Exposure program, organizations will be able to deploy and report on standard configurations and other related best practices, closing gaps previously hidden by disjointed configuration and vulnerability management. Using compliance and vulnerability data collected by Tenable.sc during active scans, the Security Director is able to reliably report on the status of vulnerability mitigation efforts and the related to configurations.
Audit files are comprised of several compliance checks that are searchable using keywords to group issues by common configuration areas, such as logging or account management. NESA requires common configuration across similar devices and these search patterns show areas of the network where the configuration may be out of alignment with a baseline. The Security Director is able to easily track and visualize the current state of compliance. The operations team is able to use this same information to gain insight into systemic configuration issues.
In adopting any configuration standard or baseline, the organization should review current best practices. Tenable.sc provides the capability to visualize individual hosts with compliance concerns that may not be in line with current best practices. Utilizing a view of audit checks indicating compliance failures, a consultant is able to quickly gain an understanding of which hosts are out of compliance and identify optimized paths to remediate.
When establishing a baseline or configuration management program, the operations team must establish a series of configuration changes, and implement said changes. Tenable.sc provides a series of audit files based on the CIS Benchmarks, which are cross referenced against many standards, to include NESA, ISO 27000, NIST. Tenable.sc provides the ability to group and report on this data together in one location.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Executive.
The dashboard requirements are:
- Tenable.sc 5.12.0
- Nessus 8.9.0
- Compliance Data
Tenable.sc Continuous View (CV) is the market-defining On-Prem Cyber Exposure Platform. Tenable.sc CV provides the ability to continuously Assess an organization’s adherence to best practice configuration baselines. Tenable.sc provides customers with a full and complete Cyber Exposure platform for completing an effective Cyber Hygiene program prescribed by NESA standard.
This dashboard contains the following components:
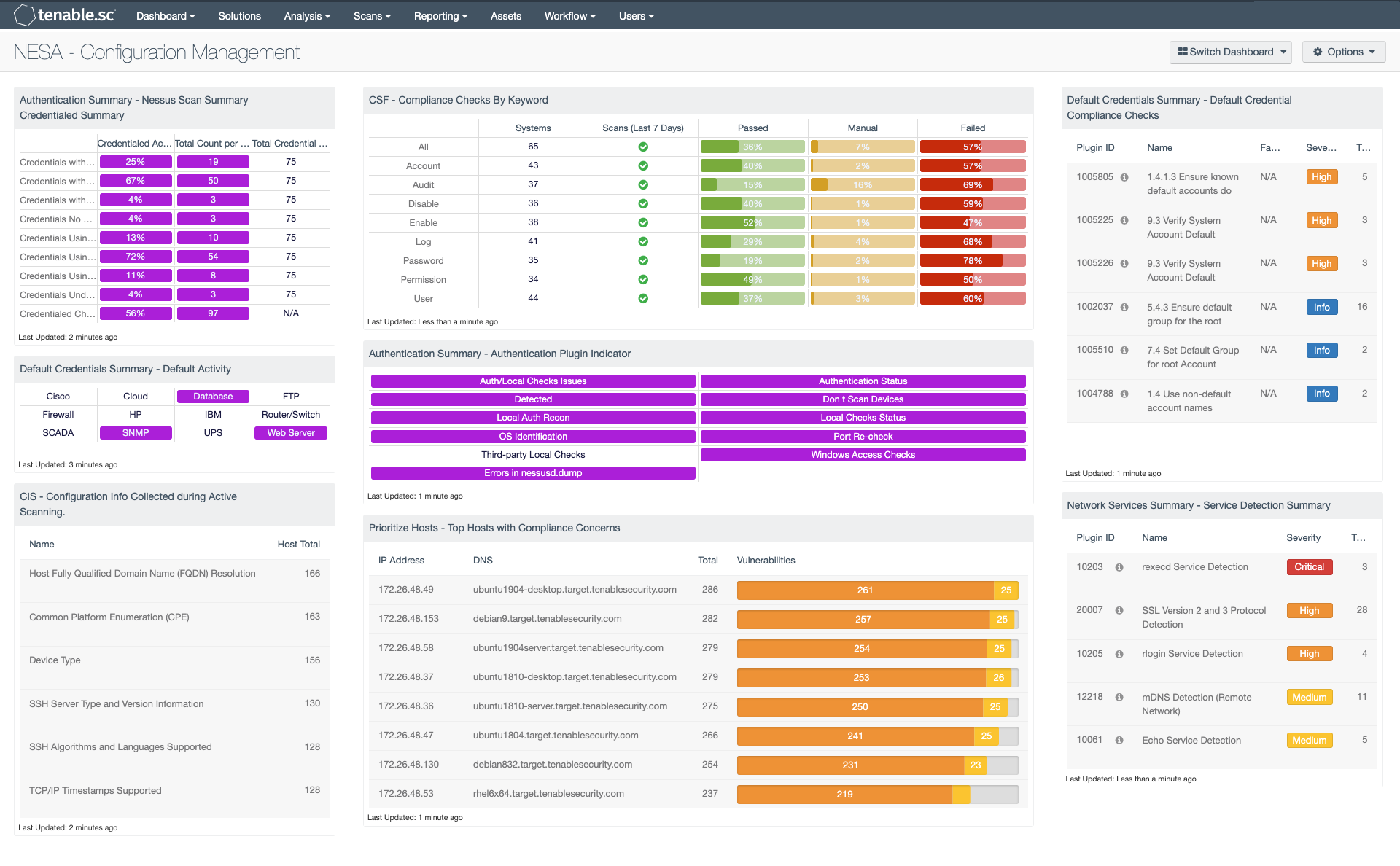
Authentication Summary - Nessus Scan Summary Credentialed Summary: This component displays a matrix providing a count of credentials used while scanning the network. . The rows show which credentials are being used by percentage, and a total count for each credential. The SMB protocol is used to provide credentials for all Windows systems. The SSH protocol is used to provide credentials for all *nix Nessus scans, including the root and admin accounts. Localhost is where the Nessus scanners are on the same system being scanned and use the localhost account to enumerate the list of missing patches. The no account name indicator will show all Nessus scans that are using an older version of Nessus, which does not capture the type of credentials that are being used.
Default Credentials Summary - Default Activity: The Default Activity Matrix presents a list of devices, services, and applications utilizing default credentials. Ideally devices, services, and applications on a network should not have any default usernames, passwords, or credentials in use. If the vulnerability is detected, the indicator will change color to purple. Clicking on a highlighted indicator will bring up the analysis screen, where more detailed information such as IP addresses, possible solutions, and additional information on affected systems can be obtained. This component can be modified to include specific or additional plugins that detect default credentials.
CIS - Configuration Info Collected during Active Scanning: This component is a summary of informational plugins that assist with configuration verification. By excluding port scan plugins, and other plugins related to services, the Vulnerability Summary tool provides a list of all other informational plugins. These plugins contain several system configuration attributes that are useful in assessing the configuration or detecting misconfigurations.
CSF - Compliance Checks By Keyword: This component uses results from the compliance audit to trigger on specific plugin keywords. Each column includes the respective keyword along with the host count, scans performed in the last 7 days, and whether the checks have passed, failed, or require manual verification. Passed checks are green, failed are red, and checks that require manual verification are in orange. This component will allow the analyst to readily identify specific compliance vulnerabilities. The keywords can be modified to suit organizational needs.
Authentication Summary - Authentication Plugin Indicator: The plugins in this component are used in many environments to understand and troubleshoot authentication problems. Authentication by a Nessus scan is performed over a network protocol (such as SMB, SSH, HTTPS, SNMP) in order to gain access to the remote target system. Keep in mind each of these plugins could be triggered on each protocol, meaning an asset can have an authentication success and authentication failure. Use these plugins to assist and to better understand how Nessus is accessing the target assets and what improvements are possible using different credentials.
Prioritize Hosts - Top Hosts with Compliance Concerns: This table displays the top hosts on the network that have either compliance failures or compliance checks that must be performed manually. The list is sorted so that the host with the worst compliance concerns is at the top. A count of compliance concerns and a bar graph indicating the severity of the concerns are given for each host. Use this table to determine the hosts most out of compliance on the network.
Default Credentials Summary - Default Credential Compliance Checks: The Default Credential Compliance Checks table presents a list of audit checks performed to detect default usernames, passwords, and credentials on a network. High severity denotes checks that have failed to meet the compliance threshold. Medium severity shows checks that need to be manually reviewed to assess their compliance state. Compliance failures in this table can be the result of services using default credentials, devices with vendor-supplied passwords, default operating system accounts, and more. Organizations should review current security policies and compliance requirements that are relevant to the organization.
Network Services Summary - Service Detection Summary: This component presents a list of services detected on internal network hosts. Services presented within this table can include network protocols, databases, servers, remote desktop services, and more. Some of this information can also include insecure protocols such as FTP, Telnet, and SSL protocols. The table is sorted by severity which will allow for quick detection and remediation of insecure protocols by analysts. Analysts can modify the table to report on specific information per organizational requirements.