by Ben Smith
March 26, 2020
The United Arab Emirates’ (UAE) National Electronic Security Authority (NESA) Information Assurance Standards state that an organization should have appropriate inventory management in place. Tracking asset inventory and authorizing new assets is a key component required by the NESA standard. Security Center includes active scan aggregation and vulnerability management. This dashboard allows a risk manager to easily see the organization’s new assets, mobile assets, wireless assets, and drill into details of each.
The discovery stage of the cyber exposure lifecycle includes identifying and mapping every asset across any computing environment. In order to maintain proper authorization for assets, the risk manager must understand when new assets are added to the network and keep an inventory of all of them. Security Center can use active scan results to show existing assets and to identify when new assets are added. Security Center can also identify the appropriate configuration and authorization for mobile devices. Mobile Device Management (MDM) data can be utilized to determine what mobile devices exist and when they were provisioned. Controls M1.3, T1.2, T1.2.3, T2.3.3, T2.3.8, T5.1.1, T5.4.3, and T5.7 are relevant here.
In order to maintain an asset inventory, assets need to be appropriately categorized. Detailed information should also be available to help answer questions about the asset. Where is it? What does it do? Who owns it? Security Center has plugins that collect asset information including asset name, type, IP address, MAC address, and sometimes location, serial number, and tag number. Device category can also be exposed in Security Center via specific device type plugins. Both sets of data can be used in performing risk ranking of assets. Controls M1.2.1, M2.1.1, T1.2, T2.3.3, T4.5, and T5.4.3 are relevant.
Security Center tracks the First Discovered and Last Observed date for plugins. The First Discovered date indicates the date an asset is first seen by Security Center, while the Last Observed date indicates the most recent time the same asset was observed. Insight into scanning health can be gained when these two are compared over time. A normal scanning program will show First Discovered assets covering a fairly even spread over time. Assets that have similar First Discovered and Last Observed times are new, while assets with older Last Observed dates may no longer be present in the environment or are not being scanned. T7.7 requires both a regular vulnerability scanning program and a remediation timeframe chosen by the organization and are subject to a risk ranking. The comparison of First Discovered and Last Observed dates can help achieve these NESA goals.
Keeping in line with authorizing new assets, T4.5.4, T5.4.7 require strict controls around wireless usage. Security Center utilizes active scan plugins to show a variety of wireless device information. Suspected wireless devices, access points, wireless vulnerabilities, and more can all be shown using active plugin searches. Compliance data can also be mined for related configuration settings.
The dashboard and its components are available in the Security Center Feed, a comprehensive collection of dashboards, reports, assurance report cards, and assets. The dashboard can be easily located in the Security Center Feed under the category Executive.
The dashboard requirements are:
- Security Center 5.12.0
- Nessus 8.9.0
- Compliance Data
- MDM Data
Security Center is the market-defining On-Prem Cyber Exposure Platform and provides the ability to continuously Discover an organization’s assets. Customers benefit from a full and complete Cyber Exposure platform for completing an effective Cyber Hygiene program prescribed by NESA standard.
This dashboard contains the following components:
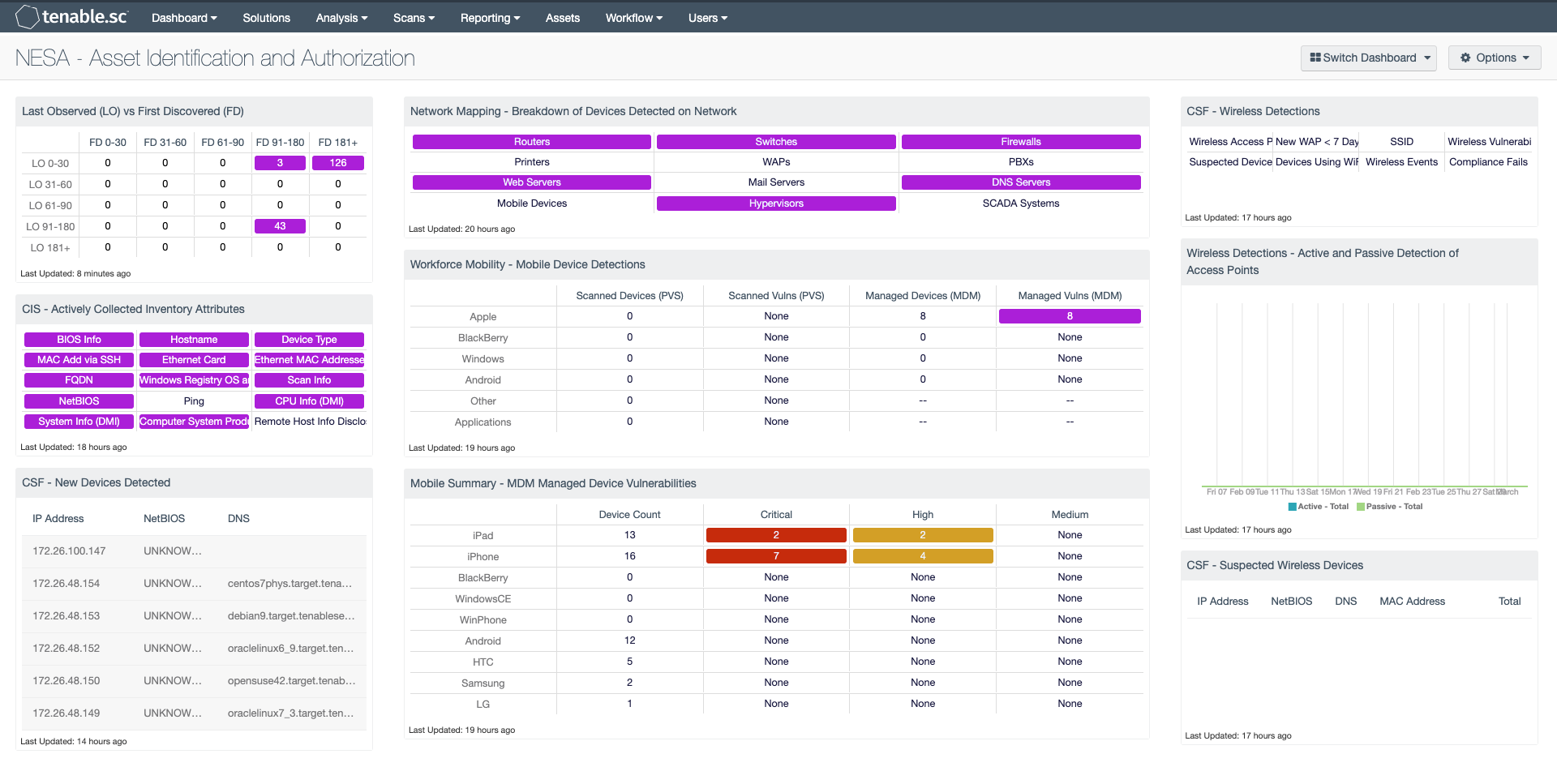
Last Observed (LO) vs First Discovered (FD): The First Discovered date indicates the date an asset is first seen by Security Center while the Last Observed date indicates the most recent time the same asset was observed. Insight into scanning health can be gained when these two are compared over time. A normal scanning program will show First Discovered assets covering a fairly even spread over time. Assets that have similar First Discovered and Last Observed times are new, while assets with older Last Observed dates may no longer be present in the environment or are not being scanned. Typically, the first row should be well populated, while results toward the lower right may indicate scanning issues. The bottom left half should be populated with zeros and will turn red if an impossible scenario occurs, indicating a problem.
CIS - Actively Collected Inventory Attributes: This matrix provides a series of saved searches that contain hardware attributes, collected actively as part of a hardware inventory. Each indicator, when purple, will provide a list of IP addresses with the respective content. Analysis can then pivot using the "Vulnerability Detail List" tool to view the details of each discovered attribute. Other tools can also be used such as the “Class C” or “User Responsibility” tool to further analyze the data.
CSF - New Devices Detected: New hosts detected within the last 48 hours. Includes PVS and Nessus Data. PVS is not required for this component to function, but it does provide additional functionality.
Network Mapping - Breakdown of Devices Detected on Network: This matrix presents a breakdown of detected network systems by type. A purple indicator denotes that systems of that type were detected; clicking on the indicator will bring up information on each of the detected systems, including IP address and MAC address. This information can assist an organization in maintaining an accurate inventory and detecting any unauthorized systems.
The type of the network system is determined either based on its operating system (OS) or by the actively or passively detected vulnerabilities it has. Indicators are included for routers, switches, firewalls, printers, wireless access points (WAPs), PBXs, web servers, mail servers (IMAP, POP, and SMTP servers, as well as other specific servers such as Microsoft Exchange), DNS servers, mobile devices, hypervisors (virtual machines), and SCADA systems.
Workforce Mobility - Mobile Device Detections: This component presents counts of mobile devices and associated vulnerabilities detected passively by the Tenable Nessus Network Monitor (NNM) and via Mobile Device Management (MDM) systems. The rows break down the detected devices by OS/Vendor. The last row presents those mobile devices and vulnerabilities detected via mobile applications. Clicking on a highlighted indicator will bring up the vulnerability analysis screen to allow further investigation.
Mobile Summary - MDM Managed Device Vulnerabilities: This component contains a list of managed mobile devices by device count, along with detected vulnerabilities by critical, high, and medium severity levels. The basis of each cell query within the matrix is the 'Model' type. Please note that this field is case sensitive. As an example, if the model type is set to 'ipad', the returned result will be 0. To ensure the correct values are displayed, use the Analysis Mobile Model Summary to view the current device models present.
CSF - Wireless Detections: This component presents a breakdown of detected wireless access points, wireless vulnerabilities, and wireless event activity on the network. Indicators will turn purple when an event or vulnerability is detected. Analysts can drill down to obtain additional information, including IP addresses and MAC addresses. This information can assist an organization in maintaining an accurate inventory and detecting any unauthorized wireless devices.
Wireless Detections - Active and Passive Detection of Access Points: The Active and Passive Detection of Access Points chart displays a trend over the last 25 days of all wireless access points detected actively or passively. Wireless devices are identified for both passive and active detections over a 24-hour period, trending for 25 days. Spikes in trend activity for active detections usually depict when active Nessus scanning on the network has occurred, while passive detections occur immediately when devices are detected by Tenable’s Nessus Network Monitor.
CSF - Suspected Wireless Devices: Along with wireless devices, many stand-along devices today include wireless access capabilities such as printers, digital cameras, and more. This component presents detected suspected wireless devices on hosts within a network. Analysts can drill down to obtain additional information on the suspected wireless device, and determine whether the device is authorized for use on the network.