by Josef Weiss
March 23, 2021
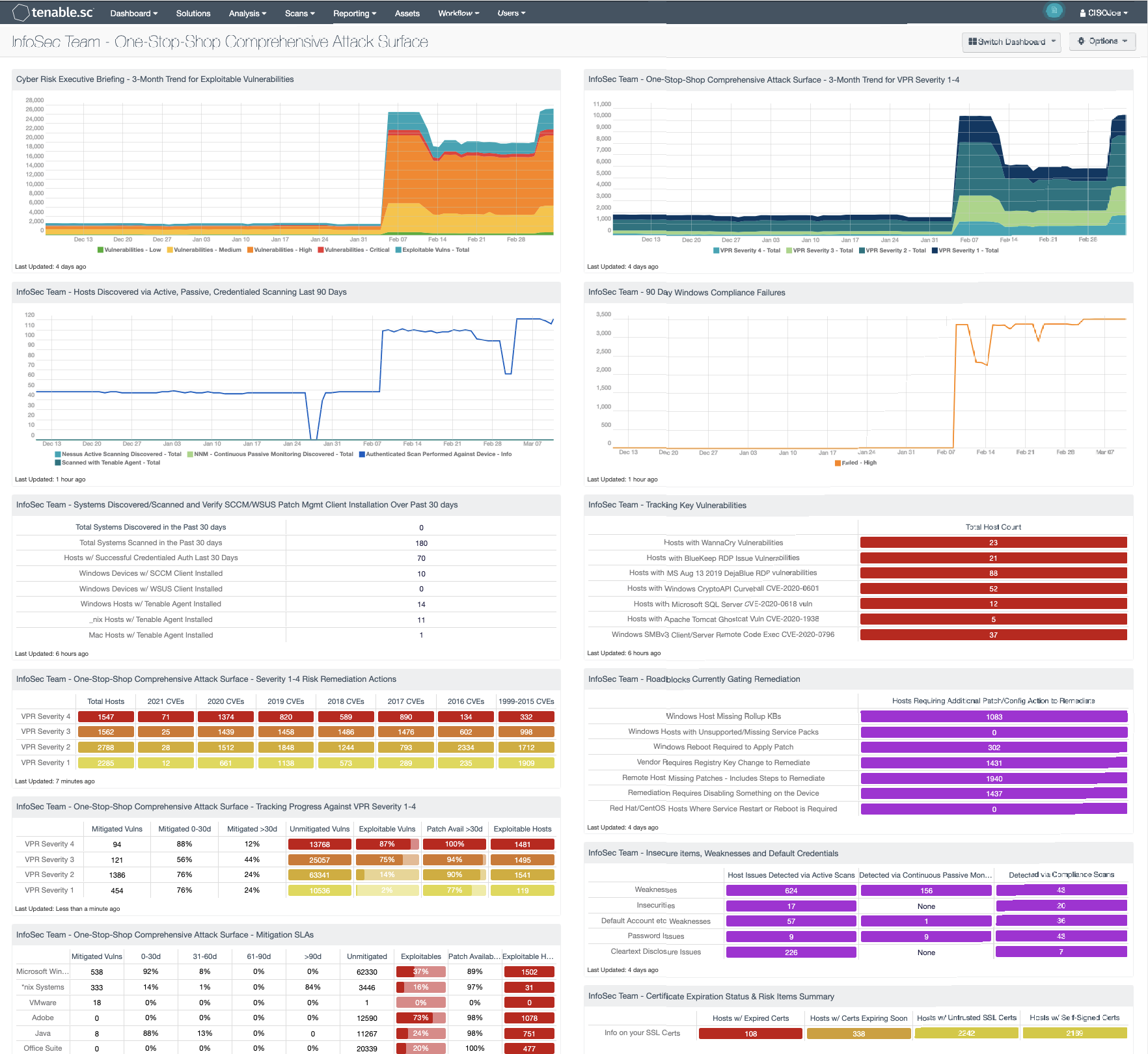
An efficient cybersecurity program is an ongoing process of identifying emerging threats, cyber risks, and implementing mitigation strategies. With a thorough understanding of security best practices, the organization can better utilize the controls that balance confidentiality, integrity, and information availability. InfoSec teams are often asked to present findings to allow the CISO to visualize how effectively the organization is achieving vulnerability management objectives. Tenable.sc supports these visualization strategies by focusing on the organization's overall risk posture and immediate threats and remediation efforts.
Organizations that follow information security best practices and maintain a high level of awareness to maintain vigilance against always present threats. The InfoSec teams are responsible for monitoring and protecting the organizations' infrastructure, including all data, devices, and networks. These teams require information to be presented that focuses on findings that should be prioritized and mitigated first by leveraging the Vulnerability Priority Rating (VPR). The VPR score is an output of Predictive Prioritization, which allows cybersecurity leaders to focus on items that help drive key performance indicators by combining research insights, threat intelligence, and vulnerability ratings to reduce noise. Effective vulnerability remediation becomes easier as vulnerabilities are presented to visualize vulnerability remediation programs and provide measures against established goals and SLAs. By utilizing VPR-based analysis, organizations are better positioned to visualize the modern attack surface to align remediation efforts with defined goals and objectives.
With the principles of Cyber Exposure Management in mind, this dashboard helps the InfoSec team maintain a high level of awareness and vigilance. The filters and components are tailored to guide teams in detecting, predicting, and acting to reduce risk across their entire attack surface. Analysts within information security teams are empowered to analyze findings, remediate identified risks, track progress, and measure success against the organization's charter and SLAs.
Organizations often have teams that focus on the detailed information relevant to the teams' assets; or operational focus areas, such as Windows, Linux, databases, or network infrastructure. The dashboard components do not require specific asset list filters to be applied before use. However, organizations with teams that focus on a specific group of assets benefit from using custom asset lists. Information security teams can visualize findings against assets that are "owned by" or "assigned to" specific teams within the organization using this method. Additionally, an Output Assets filter can be set to provide greater insight into where additional resources need to be allocated to mitigate vulnerabilities.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Threat Detection & Vulnerability Assessments.
The dashboard requirements are:
- Tenable.sc 5.15.0
- Nessus 8.11.1
- Asset: Microsoft Active Directory Domain Controllers
- Asset: Microsoft SQL Servers