by Cody Dumont
June 20, 2016
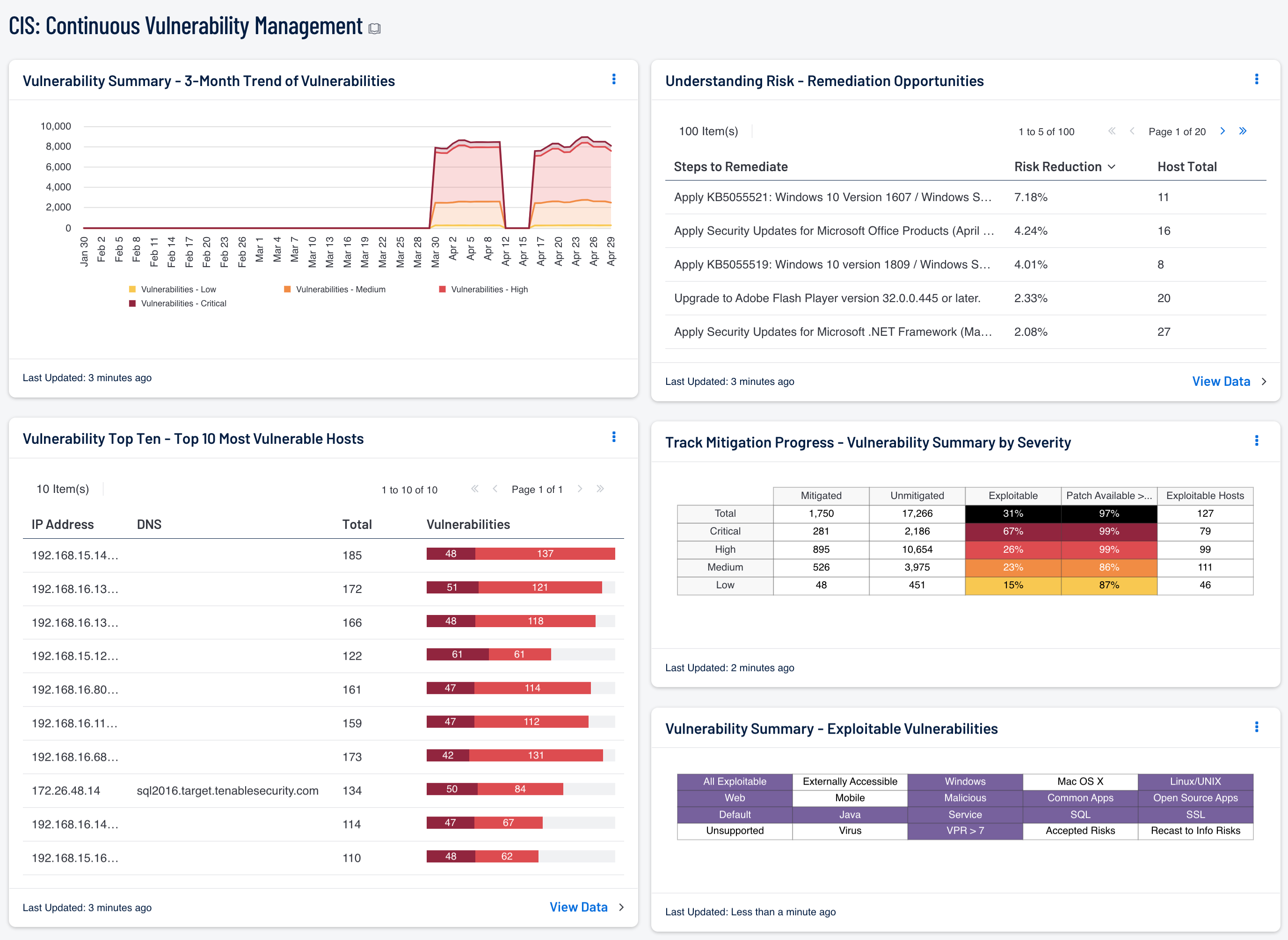
Organizations that don’t continuously look for vulnerabilities and proactively address discovered flaws are very likely to have their network compromised and their data stolen or destroyed. Security Center is an on-premises Cyber Exposure platform which helps organizations reduce risk and manage discovered vulnerabilities. By implementing Cyber Exposure, organizations are able to continuously monitor for new threats on the network.
Undiscovered vulnerable devices and applications pose a great risk to network security and operational stability. Vulnerabilities such as outdated software, as well as overall susceptibility to buffer overflows, risky enabled services, etc. are weaknesses in the network that are often exploited. Organizations that do not continuously look for vulnerabilities and proactively address discovered flaws are very likely to have their network compromised and their data stolen or destroyed. This dashboard provides a high-level overview of an organization's vulnerability management program and assists the organization in identifying vulnerabilities, prioritizing remediations, and tracking remediation progress.
Organizations that implement a Cyber Exposure program using on-premises solutions, such as Security Center are able to align IT operational efforts with the 5 steps in the Cyber Exposure Lifecycle. This dashboard provides high level information on 3 levels of the life cycle, Analyze, Fix, and Measure. As the security operations team moves around the lifecycle model, each step supports and feeds the other steps. To enable analysis over time, Security Center takes nightly snapshots of the vulnerability data and tracks this content over time. The Trending Analysis tools in this dashboard show IT managers progress over time. In this example, over 3 months, there will be spikes every 30 days, which reflect the “Microsoft Patch Tuesday.” Over time, risk managers can use the trending data to better measure progress of risk mitigation efforts.
This dashboard and its components are available in the Security Center Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Security Center Feed under the category Security Industry Trends. The dashboard requirements are:
- Security Center 5.13.0
- Nessus 8.9.0
- NNM 5.11.0
Security Center also provides tools to help mitigate issues using a patch chain. The patch chain is a chain of supersedence where one patch will address other patches. The patch chain is calculated using different algorithms, resulting in the chain of plugins that feed the remediation summary tool. This tool shows the solution notes for the top patch, risk reduced, and the affected hosts. More information can be learned about this process is described in these YouTube videos.
Analysts can also use this dashboard to easily drill down into the data presented by the dashboard components. This enables the analyst to gain more detailed information about the vulnerabilities found on the network, such as which vulnerabilities are the most dangerous. The analyst can also determine information that will benefit vulnerability remediation. This information might include on which hosts a vulnerability is found and what remediations would most benefit a particular group of machines. Knowing these details can enable better and more efficient vulnerability management, patching, and mitigation within the organization. This in turn will help the organization better protect itself from exploitation of network vulnerabilities, and potential intrusions, attacks, and data loss. Tenable's Security Center is the market-defining continuous network monitoring solution. Security Center includes active vulnerability detection with Nessus and passive vulnerability detection with the Tenable Nessus Network Monitor (NNM). Using Security Center an organization will obtain the most comprehensive and integrated view of its network.