Microsoft’s October 2022 Patch Tuesday Addresses 84 CVEs (CVE-2022-41033)

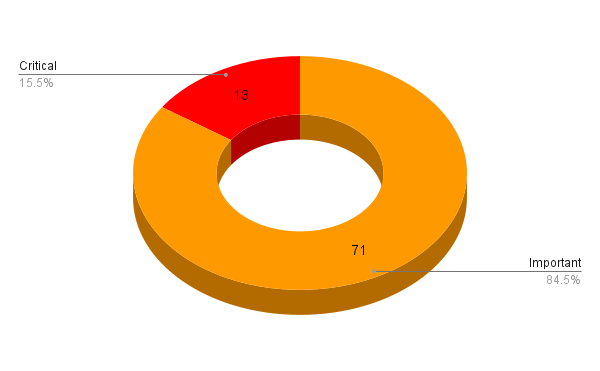
Microsoft addresses 84 CVEs in its October 2022 Patch Tuesday release, including 13 critical flaws.
- 13Critical
- 71Important
- 0Moderate
- 0Low
Microsoft patched 84 CVEs in its October 2022 Patch Tuesday release, with 13 rated as critical and 71 rated as important.
This month’s update includes patches for:
- Active Directory Domain Services
- Azure
- Azure Arc
- Client Server Run-time Subsystem (CSRSS)
- Microsoft Edge (Chromium-based)
- Microsoft Graphics Component
- Microsoft Office
- Microsoft Office SharePoint
- Microsoft Office Word
- Microsoft WDAC OLE DB provider for SQL
- NuGet Client
- Remote Access Service Point-to-Point Tunneling Protocol
- Role: Windows Hyper-V
- Service Fabric
- Visual Studio Code
- Windows Active Directory Certificate Services
- Windows ALPC
- Windows CD-ROM Driver
- Windows COM+ Event System Service
- Windows Connected User Experiences and Telemetry
- Windows CryptoAPI
- Windows Defender
- Windows DHCP Client
- Windows Distributed File System (DFS)
- Windows DWM Core Library
- Windows Event Logging Service
- Windows Group Policy
- Windows Group Policy Preference Client
- Windows Internet Key Exchange (IKE) Protocol
- Windows Kernel
- Windows Local Security Authority (LSA)
- Windows Local Security Authority Subsystem Service (LSASS)
- Windows Local Session Manager (LSM)
- Windows NTFS
- Windows NTLM
- Windows ODBC Driver
- Windows Perception Simulation Service
- Windows Point-to-Point Tunneling Protocol
- Windows Portable Device Enumerator Service
- Windows Print Spooler Components
- Windows Resilient File System (ReFS)
- Windows Secure Channel
- Windows Security Support Provider Interface
- Windows Server Remotely Accessible Registry Keys
- Windows Server Service
- Windows Storage
- Windows TCP/IP
- Windows USB Serial Driver
- Windows Web Account Manager
- Windows Win32K
- Windows WLAN Service
- Windows Workstation Service
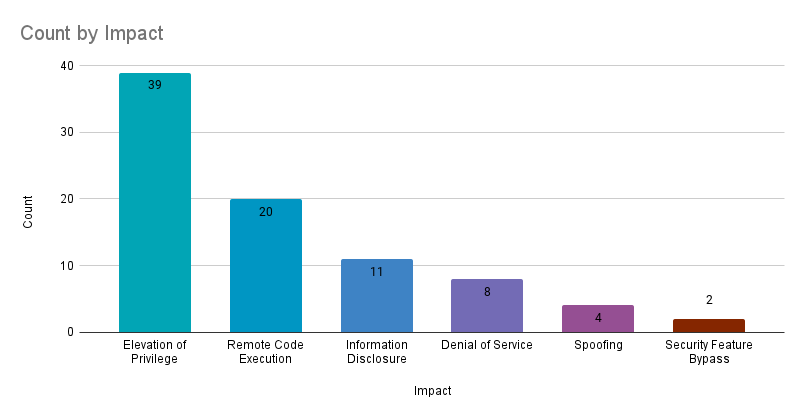
Elevation of privilege (EoP) accounted for 46.4% of the vulnerabilities patched this month, followed by remote code execution (RCE) vulnerabilities at 23.8%.
Note: Microsoft has not included patches for the two zero-day vulnerabilities in Microsoft Exchange, CVE-2022-41040 and CVE-2022-41082, that were disclosed on September 28 in this release.
CVE-2022-41033 | Windows COM+ Event System Service elevation of privilege vulnerability
CVE-2022-41033 is an EoP vulnerability in the Windows COM+ Event System Service, which enables system event notifications for COM+ component services. It received a CVSSv3 score of 7.8. An authenticated attacker could exploit this vulnerability to elevate privileges on a vulnerable system and gain SYSTEM privileges.
Microsoft says that this vulnerability has been exploited in the wild, though no additional information was shared.
CVE-2022-37968 | Azure Arc-enabled kubernetes cluster connect elevation of privilege vulnerability
CVE-2022-37968 is an EoP vulnerability in Microsoft’s Azure Arc, affecting the cluster connect feature of Azure Arc-enabled Kubernetes clusters. With a CVSSv3 score of 10, the highest possible rating, an unauthenticated attacker could exploit this vulnerability in order to gain administrative privileges for a Kubernetes cluster. While updates have been released, users that do not have auto-upgrade enabled must take action to manually upgrade Azure Arc-enabled Kubernetes clusters. Microsoft’s security advisory provides additional information and steps to upgrade and how to check your current version. In July, Tenable disclosed a vulnerability in Azure Arc wherein passwords were being logged in plaintext. You can read more about the disclosure on the Tenable Techblog.
CVE-2022-38028 | Windows Print Spooler elevation of privilege vulnerability
CVE-2022-38028 is an EoP vulnerability in Windows Print Spooler components that received a CVSSv3 score of 7.8 and was rated “Exploitation More Likely” according to Microsoft’s Exploitability Index. Exploitation would allow an attacker to gain SYSTEM privileges. The flaw was disclosed to Microsoft by the National Security Agency. This marks the third EoP vulnerability in Windows Print Spooler credited to the NSA this year, following CVE-2022-29104 and CVE-2022-30138 in May.
CVE-2022-38053, CVE-2022-41036, CVE-2022-41037 and CVE-2022-41038 | Microsoft SharePoint Server remote code execution vulnerability
CVE-2022-38053, CVE-2022-41036, CVE-2022-41037 and CVE-2022-41038 are RCE vulnerabilities in Microsoft SharePoint Server that all received a CVSSv3 score of 8.8. All except CVE-2022-41037 were rated “Exploitation More Likely,” and CVE-2022-41038 is the only one that has a critical rating. To exploit these vulnerabilities, a network-based attacker would need to be authenticated to the target SharePoint site with permission to use Manage Lists.
CVE-2022-37988, CVE-2022-37990, CVE-2022-37991, CVE-2022-37995, CVE-2022-38022, CVE-2022-38037, CVE-2022-38038 and CVE-2022-38039 | Windows Kernel elevation of privilege vulnerability
CVE-2022-37988, CVE-2022-37990, CVE-2022-37991, CVE-2022-37995, CVE-2022-38022, CVE-2022-38037, CVE-2022-38038 and CVE-2022-38039 are EoP vulnerabilities in the Windows Kernel. With the exception of CVE-2022-38022, all the CVEs received CVSSv3 scores of 7.8 and could allow an attacker to elevate their privileges to SYSTEM. CVE-2022-38022 was scored CVSSv3 of 2.5 and would only allow an attacker to delete empty folders as SYSTEM. The attacker would not be able to view or edit files, nor delete folders that were not empty.
CVE-2022-41043 | Microsoft Office information disclosure vulnerability
CVE-2022-41043 is an information disclosure vulnerability affecting Microsoft Office for Mac. While exploitation requires local access to the host, this was the only publicly disclosed vulnerability patched this month. It is credited to Cody Thomas with SpecterOps.
CVE-2022-37976 | Active Directory Certificate Services elevation of privilege vulnerability
CVE-2022-37976 is an EoP vulnerability affecting Active Directory Certificate Services. According to the advisory, a malicious Distributed Component Object Model (DCOM) client could be used to entice a DCOM server to authenticate to the client, allowing an attacker to perform a cross-protocol attack and gain domain administrator privileges. While Microsoft rates this as “Exploitation Less Likely,” ransomware groups often seek out vulnerabilities and misconfigurations in Active Directory to leverage for spreading malicious payloads across an organization's network. As highlighted in Tenable’s Ransomware Ecosystem report, Active Directory plays a pivotal role in ransomware attacks.
Tenable Solutions
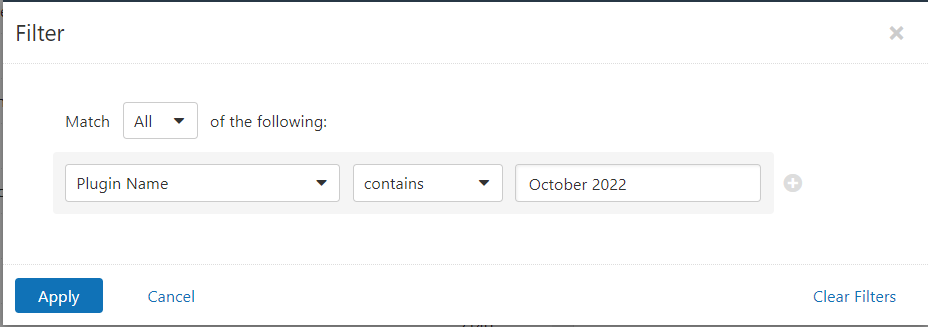
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains October 2022.
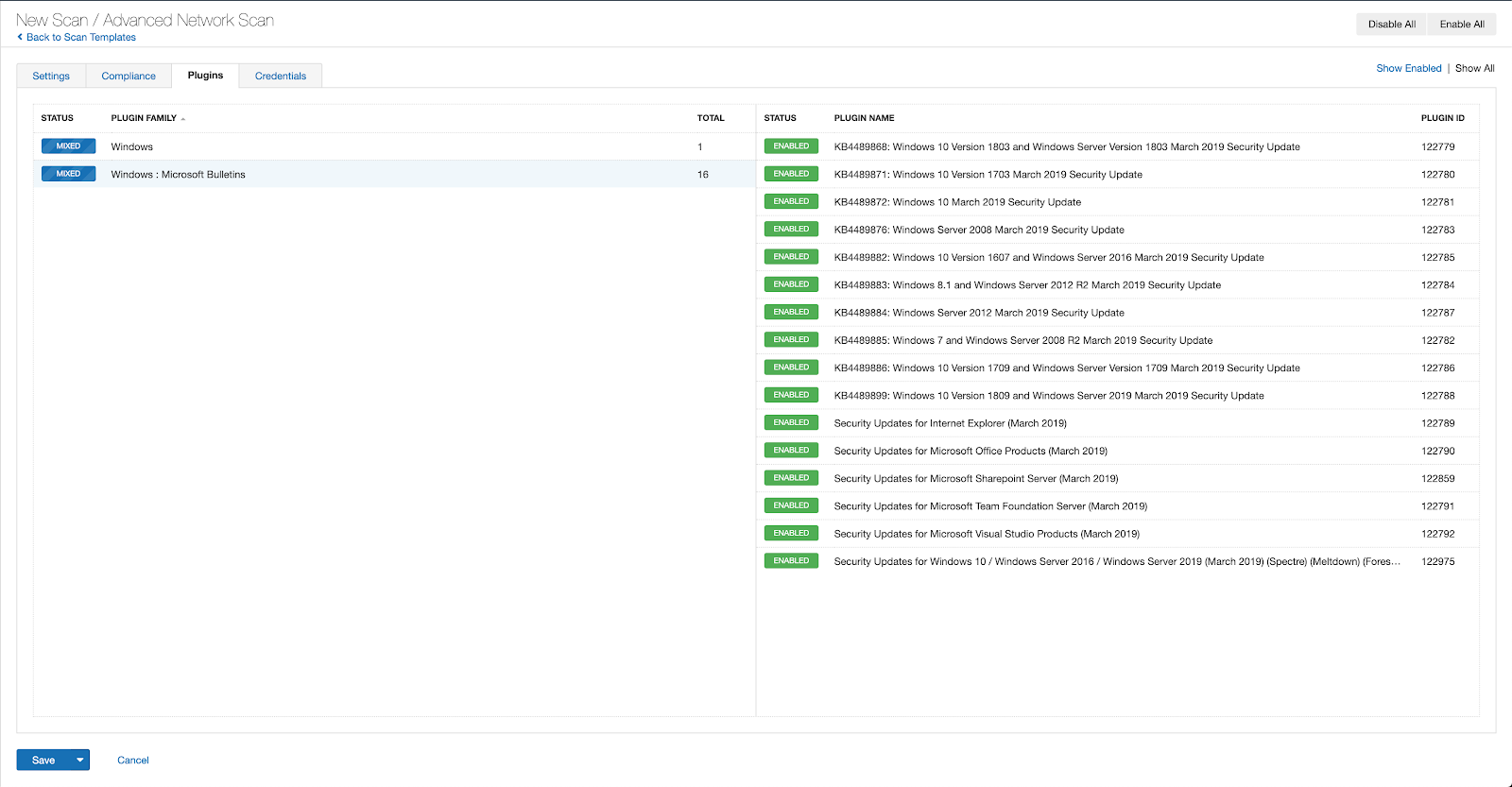
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from Tenable.io:
A list of all the plugins released for Tenable’s October 2022 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Get more information
- Microsoft's October 2022 Security Updates
- Tenable plugins for Microsoft October 2022 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Exposure Management
- Vulnerability Management


