Microsoft’s November 2021 Patch Tuesday Addresses 55 CVEs (CVE-2021-42321)

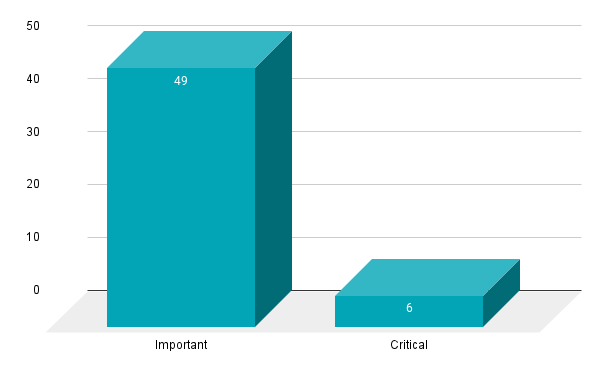
- 6Critical
- 49Important
- 0Moderate
- 0Low
Microsoft patched 55 CVEs in the November 2021 Patch Tuesday release, including six rated as critical, and 49 rated as important.
This month’s update includes patches for:
- 3D Viewer
- Azure
- Azure RTOS
- Azure Sphere
- Microsoft Dynamics
- Microsoft Edge (Chromium-based)
- Microsoft Edge (Chromium-based) in IE Mode
- Microsoft Exchange Server
- Microsoft Office
- Microsoft Office Access
- Microsoft Office Excel
- Microsoft Office SharePoint
- Microsoft Office Word
- Microsoft Windows
- Microsoft Windows Codecs Library
- Power BI
- Role: Windows Hyper-V
- Visual Studio
- Visual Studio Code
- Windows Active Directory
- Windows COM
- Windows Core Shell
- Windows Cred SSProvider Protocol
- Windows Defender
- Windows Desktop Bridge
- Windows Diagnostic Hub
- Windows Fastfat Driver
- Windows Feedback Hub
- Windows Hello
- Windows Installer
- Windows Kernel
- Windows NTFS
- Windows RDP
- Windows Scripting
- Windows Virtual Machine Bus
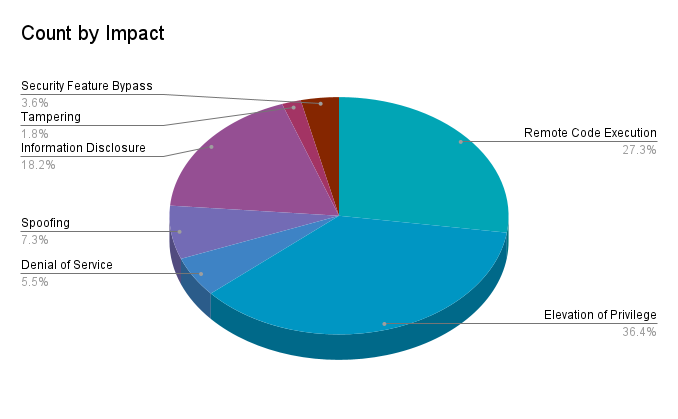
Elevation of privilege (EoP) vulnerabilities accounted for 36.4% of the vulnerabilities patched this month, followed by remote code execution (RCE) vulnerabilities at 27.3%.
CVE-2021-42321 | Microsoft Exchange Server Remote Code Execution Vulnerability
CVE-2021-42321 is a RCE vulnerability in Microsoft Exchange Server. The flaw exists due to the improper validation of command-let (cmdlet) arguments. To exploit this vulnerability, an attacker would need to be authenticated to a vulnerable Exchange Server. Microsoft says they are aware of “limited targeted attacks” using this vulnerability in the wild. Additionally, this appears to be the same vulnerability in Exchange Server that was exploited at the Tianfu Cup, a Chinese cybersecurity contest.
Several notable vulnerabilities have been disclosed in Microsoft Exchange Server throughout 2021, starting with ProxyLogon and associated zero-days in March, later followed by ProxyShell. Organizations that run Exchange Server on-premises should apply security updates in a timely manner to prevent future exploitation once proof-of-concept code becomes publicly available.
CVE-2021-42292 | Microsoft Excel Security Feature Bypass Vulnerability
CVE-2021-42292 is a security feature bypass zero-day in Microsoft Excel that received a 7.8 CVSSv3 score and has been exploited in the wild. Discovery of this flaw is credited to the Microsoft Threat Intelligence Center (MSTIC) but no further information on the vulnerability or the detected exploitations has been published at this time. Microsoft specifically notes that the Preview Pane is not an attack vector for this vulnerability, which means the victim would need to open a malicious Excel document for exploitation to occur. Microsoft notes that patches for Office for Mac are still in progress.
CVE-2021-38666 | Remote Desktop Client Remote Code Execution Vulnerability
CVE-2021-38666 is a RCE vulnerability in the Remote Desktop Client that received a CVSSv3 score of 8.8. The vulnerability can be exploited when a victim machine connects to an attacker-controlled Remote Desktop server, allowing the attacker to execute arbitrary code on the victim's machine. While no public exploit appears to exist at this time, Microsoft has designated this flaw as “Exploitation More Likely” according to Microsoft’s Exploitability Index.
Microsoft also provided two other patches for Windows Remote Desktop Protocol (RDP) this month which could be used in a related scenario. If an attacker is able to take control of an account with RDP server administrator privileges, they could exploit CVE-2021-41371 or CVE-2021-38631 to read Windows RDP client passwords. Both CVE-2021-41371 and CVE-2021-38631 were publicly disclosed, according to Microsoft.
The attacker would need to control a Remote Desktop server prior to exploitation of any one of these three CVEs.
CVE-2021-43208 and CVE-2021-43209 | 3D Viewer Remote Code Execution Vulnerability
CVE-2021-43208 and CVE-2021-43209 are RCE vulnerabilities found in 3D Viewer, a 3D object viewer and augmented reality application for Windows. According to Microsoft, these vulnerabilities have both been publicly disclosed and are attributed to Mat Powell of Trend Micro Zero Day Initiative. While no additional details are available at this time, Microsoft’s advisory does note that affected customers should receive updates automatically from the Microsoft Store. Customers that have automatic updates disabled will have to take action in order to receive this update.
Tenable Solutions
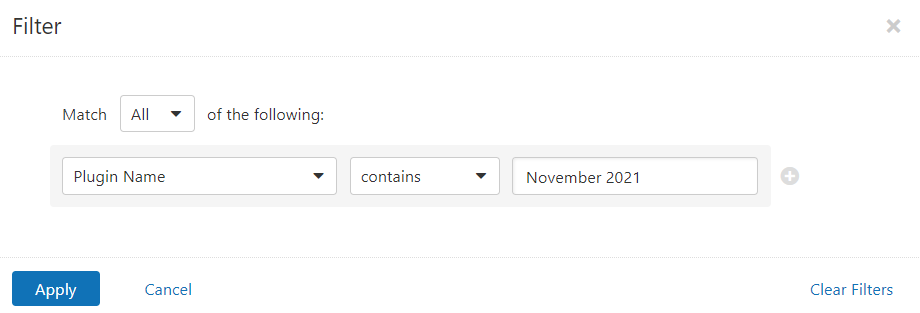
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains November 2021.
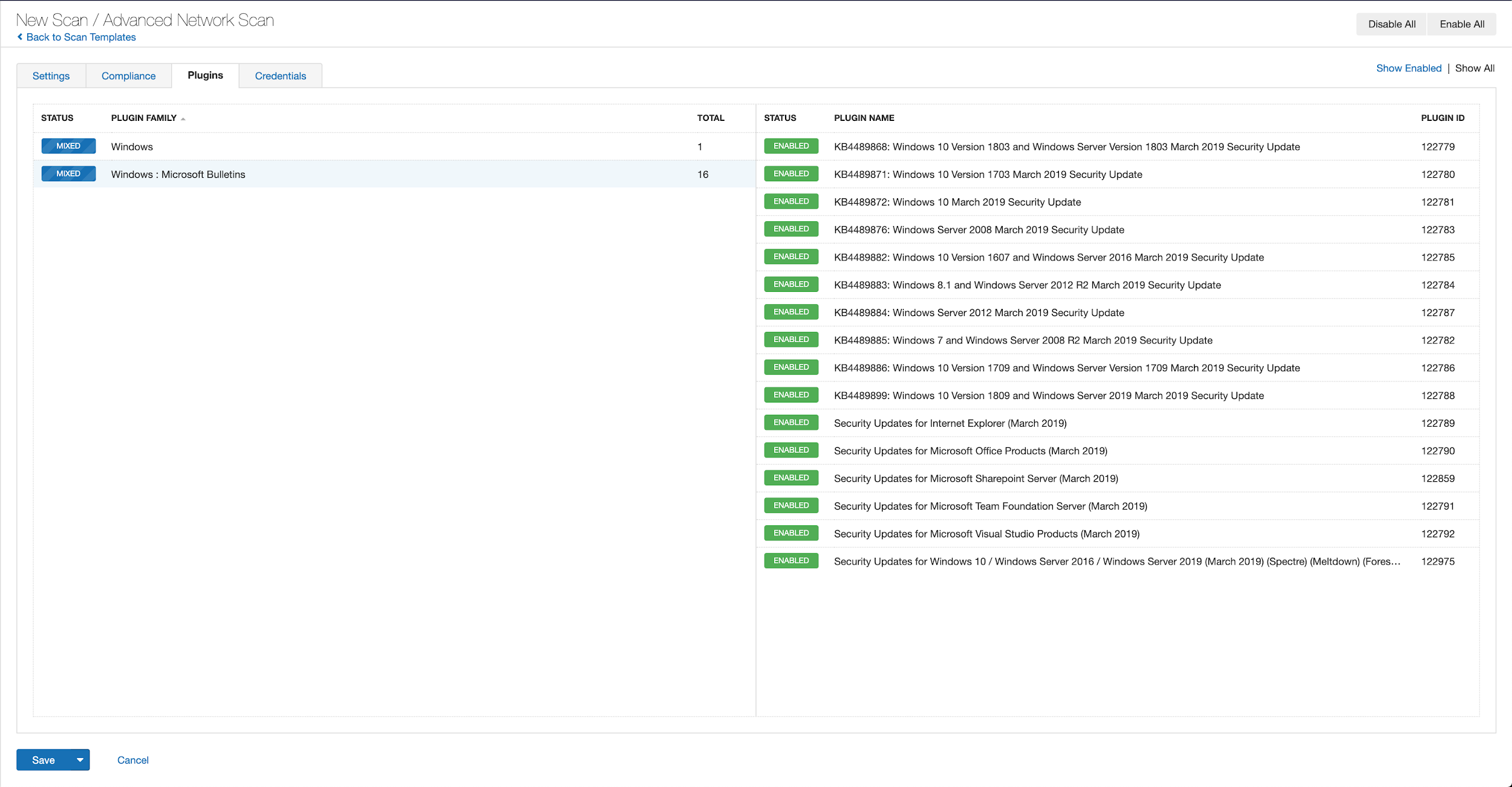
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from Tenable.io:
A list of all the plugins released for Tenable’s November 2021 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Get more information
- Microsoft's November 2021 Security Updates
- Tenable plugins for Microsoft November 2021 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management

