Leveraging Logins and Login Failures to Track Insiders

I recently had the chance to explain Tenable’s approach to tracking insiders through authentication logs to a new employee. The conversation went something like this:
Q: If I handed you a pile of logs and told you that “Bob” in accounting was an insider threat, what would you do?
A: I’d look through all the logs for accounts that Bob had access to and attempt to audit which systems he accessed and possibly what he did.
Q: Great! Now if I told you that Bob also had access to other company accounts and he may have used those from his system, how would you look for those?
A: I’d look at the logins from Bob’s computer and see if there were any other logins from there that were not Bob.
Q: Also great! Now here is the hard part – we are pretty sure there is an insider on our network, but it could be anybody, even Bob! How would you go about looking for any evidence of someone acting as a malicious insider?
And of course the answer involved a discussion of how Tenable audits accounts and authentications.
Tenable’s approach to this problem has many different components, some provided by Nessus and others provided through log analysis with the Log Correlation Engine (LCE). In the remainder of this blog, we will discuss the various audits, correlations and anomalies that can be used to pinpoint users accessing items in a suspicious manner. We will start out with basic enumeration and tracking of users and then progress to looking for anomalies that could indicate abuse.
Nessus
Nessus can use credentialed audits to enumerate the active user accounts in the operating system as well as some applications. From this list, an audit can be performed to see if the user accounts are authorized or not.
Nessus also performs many different types of tests on the various accounts, including checking to see if the account has ever been used, if the password has been reset and so on. Below is a screen shot of a SecurityCenter dashboard component that shows a LAN segment with a variety of pass and fail tests for Windows user accounts.
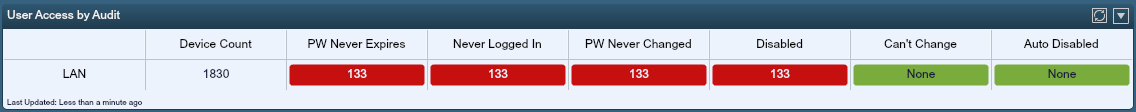
Tracking User Provisioning
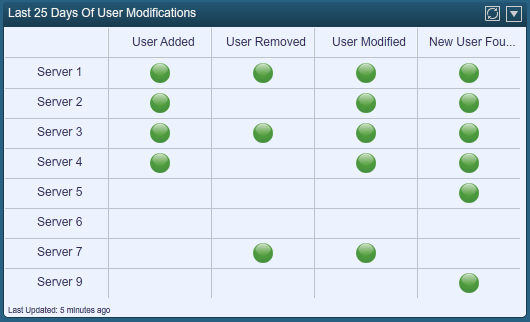
As part of the Log Correlation Engine’s log normalization process, any type of log where a user is added to a system, removed or changed is recognized. This allows long term tracking of new users and data for real-time dashboards.
In the screen shot below, multiple servers have been added to a dashboard and then for each server, indications of users accounts being added, removed or modified in the last 25 days are shown.
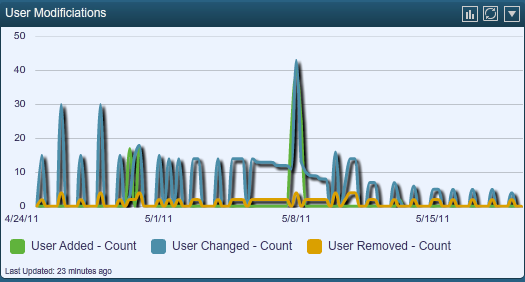
This same data can be displayed as a continuous graph over the same 25-day period.
Tracking Account Activity
Both the Nessus audits and the LCE tracking of user provisioning events are very useful to determine when accounts were provisioned, but they don’t specifically tell you when an account was used or has been potentially abused.
The LCE normalizes authentication logs (both authorized and failed attempts) for hundreds of applications and devices. Below is a screen shot of a typical 24-hour window of login activity at a small IT business.
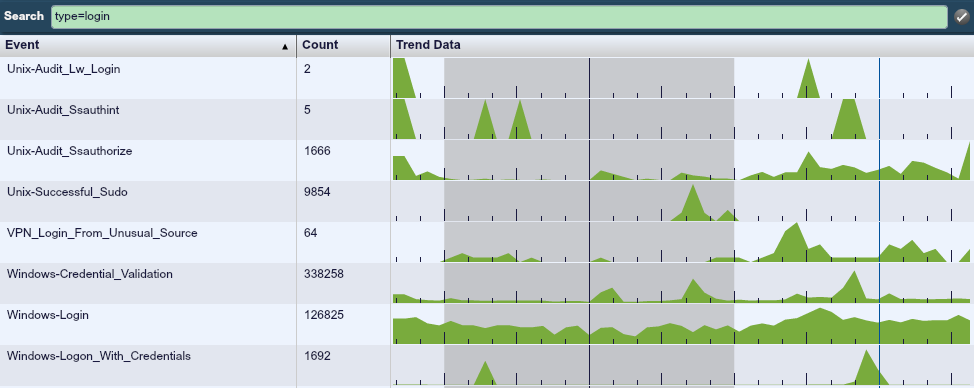
This screen shot shows a variety of Windows and Unix login events.
This data is further enhanced by LCE’s anomaly detection.
For any set of events, including logins, LCE will identify normal usage patterns and then generate an alert if there is a change. When computed for logins or login failures, these anomalies provide indicators of large changes in normal authentication activity.
Following is a screen shot of a dashboard that plots logins and login failures above the actual number of logins and login failures that were anomalistic over a one week period.
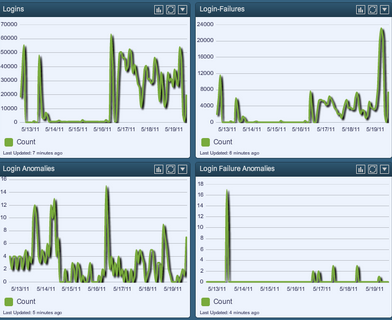
In the login chart, the daily logins ranged from close to zero to 60,000. Login failures also spanned from close to zero through 20,000. However, looking at the anomalies chart for as many authentication events that were logged, there were only around a dozen anomalies logged each day.
The anomalies don’t directly indicate insider activity, but the potential is there. They could indicate a new user forgetting a password and trying to authenticate many multiple times. The point of the logs is they provide an immediate list of issues to audit and analyze further.
Another very useful report that can be performed by SecurityCenter is to show the list of user accounts per system as reported by Nessus and then show the list of active user accounts observed through logs by the Log Correlation Engine.
For example, on one of my home test Windows 7 laptops, LCE has observed these user names:
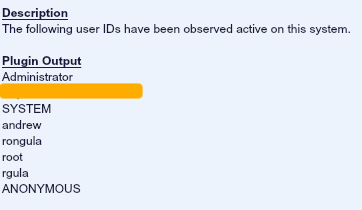
Combining the report with the account names seen in use along with the system accounts installed can help identify accounts that have not been in use and may not be needed.
Advanced User Tracking
Besides tracking actual authentication events, LCE will learn much more about the local network and where user accounts are used. The following list of events is generated by LCE as it learns about each new user and the unique relations to the network and systems.
- New_User – LCE has learned about a user account in use on a specific system.
- New_User_Source – LCE has learned about a source system where an account has originated from for the first time.
- New-Network-User – LCE has observed an authentication log in which the relationship between a user ID and the IP address associated with it has changed.
- VPN_Login_From_Unusual_Source – LCE has seen a VPN authentication occur from a source that is not normal for the user ID.
Each of these is a potential event to investigate, but understanding them in context is more important.
For example, if a user’s system was compromised by malware and then their credentials used to login to a new system not normally accessed, the New_User_Source event will fire. Perhaps various systems at the NSA would have had logs like those shown below for the first time that Ed Snowden used his credentials to access these systems:
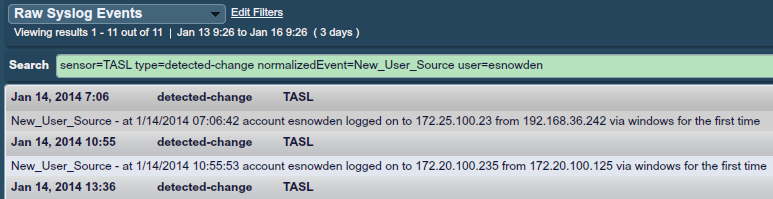
Hunting insiders for abuse patterns is very difficult. In the Ed Snowden case above, one would be correct to state that since this account was already created and he logged in with his access, he really wasn’t “hacking”. What really is happened is that his accounts had too much access and once he started walking through all of the available systems, this could have set off an anomaly alert.
Conclusion
Tracking insiders through log analysis and account auditing is a key component of the SecurityCenter Continuous View solution from Tenable. By combining scanning, sniffing and logging into one platform, detecting insider threats and suspicious users is possible through the use of anomaly detection and auditing.
To learn more about Tenable’s ability to watch employees and detect suspicious activity, please contact our sales team.
- Insider Threats
- LCE
- Log Analysis
- Nessus
- SecurityCenter