How Exposure Management Moves Beyond Vulnerability Scans to A Unified View of Risk

Each Monday, the Tenable Exposure Management Academy provides the practical, real-world guidance you need to shift from vulnerability management to exposure management. In this post, we look at the results of a survey taken during a recent Tenable webinar on the level of familiarity with exposure management. You can read the entire Exposure Management Academy series here.
For decades, the foundation of many security programs has been a familiar cycle: scan, patch, repeat.
This has been a necessary, if often overwhelming, part of cyber hygiene. But in an era of interconnected systems and multi-faceted attacks, simply counting vulnerabilities is no longer enough.
Amid this industry shift, a poll during a recent Tenable webinar, Security Without Silos: Gain Real Risk Insights with Exposure Management Upsized, showed that nearly half of all organizations are actively exploring or implementing a more advanced approach: exposure management.
Familiarity with exposure management
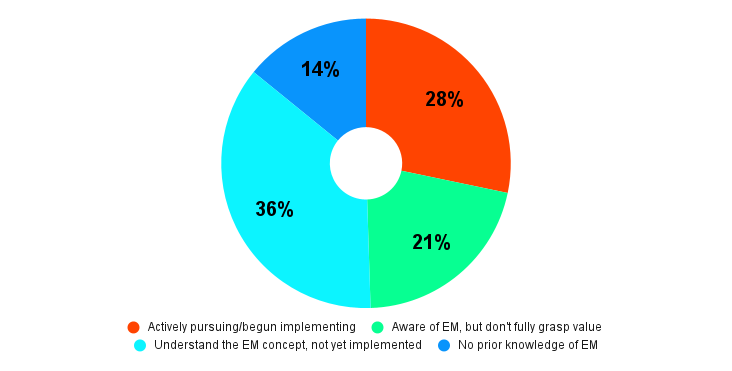
Source: Tenable webinar poll of 85 respondents, April 2025
When asked about their familiarity with exposure management, attendees painted a clear picture of a community on a journey.
Nearly half of all attendees are already in the process of implementing or understanding the concepts behind what exposure management is, while another 40% are just getting familiarized with it. This means the majority of respondents are moving away from legacy, siloed methods. With many on this path, it's critical to understand the destination: a truly unified, proactive, and intelligent view of risk.
Moving beyond silos
But what does this next evolution of security actually look like in practice?
What becomes possible when you move beyond siloed vulnerability scans and create a truly unified view of risk? With exposure management, you can finally start asking the critical questions that were previously impossible to answer.
The journey begins with a foundational shift: moving from disparate lists of assets to a single, unified and deduplicated inventory. This isn't just a list of IPs and hostnames. A true exposure management platform creates a rich, contextualized view by aggregating data from all of your sensing tools — including those from Tenable as well as third-party, cloud, identity and OT systems.
This unified inventory becomes the canvas upon which you can paint a complete picture of your attack surface.
With the ability to separate the signal from the noise, you can move beyond simple vulnerability queries and start investigating complex, multi-domain risk scenarios. Plus, you’ll be able to prioritize the list of truly critical exposures so that your IT and dev teams will have a manageable workload. This is where the strategic value of exposure management becomes clear. As the webinar discussed, a unified platform enables you to ask questions that cut across traditional security silos to find toxic risk combinations.
Imagine asking your security tools a question like this: "Show me all user accounts with breached passwords that are actively logging into devices that also have actively exploitable vulnerabilities."
The difference between data and intelligence
This single question connects three distinct domains: identity exposure (breached passwords), device access (login activity) and IT vulnerability management (exploitable CVEs). But answering the question is impossible when your identity tools don't talk to your vulnerability scanner.
In a unified exposure management platform, this query is simple and can immediately reveal high-risk scenarios where a compromised identity has a direct path to vulnerable, exploitable assets. This is the difference between raw data and rich intelligence.
The goal is to see your organization not as you've built it, but as an attacker sees it — as a web of interconnected opportunities. The most powerful capability of a mature exposure management program is the ability to visualize these connections as potential attack paths. The webinar showcased a compelling example of this in action.
The platform identified an externally facing asset in the cloud, discovered via an attack surface management scan. It then showed how an attacker could use remote desktop protocol on that machine to pivot to an internal subnet and compromise a critical email server that was vulnerable to a specific CVE.
This isn't a theoretical exercise. It’s a visual, evidence-based map of a likely breach path, constructed by automatically connecting the dots between your cloud, network and vulnerability data. Seeing this allows you to move upstream and proactively sever the connection — disabling a service, patching the vulnerability, or hardening the cloud instance — before an attacker ever gets the chance to exploit it.
Takeaways
True exposure management is not about getting a better list of problems to fix.
It’s about achieving a comprehensive understanding of the relationships between your assets and exposures. It transforms security from a reactive, volume-based patching operation into a proactive, intelligence-driven function that precisely identifies and neutralizes the most critical threats to your business.
Learn more
- Check out the Tenable exposure management resource center to discover the value of exposure management and explore resources to help you stand up a continuous threat exposure management program.
- Exposure Management
- Exposure Management Academy


