Prevent runtime vulnerabilities with registry scanning
Identify vulnerabilities in container images, registries and running workloads
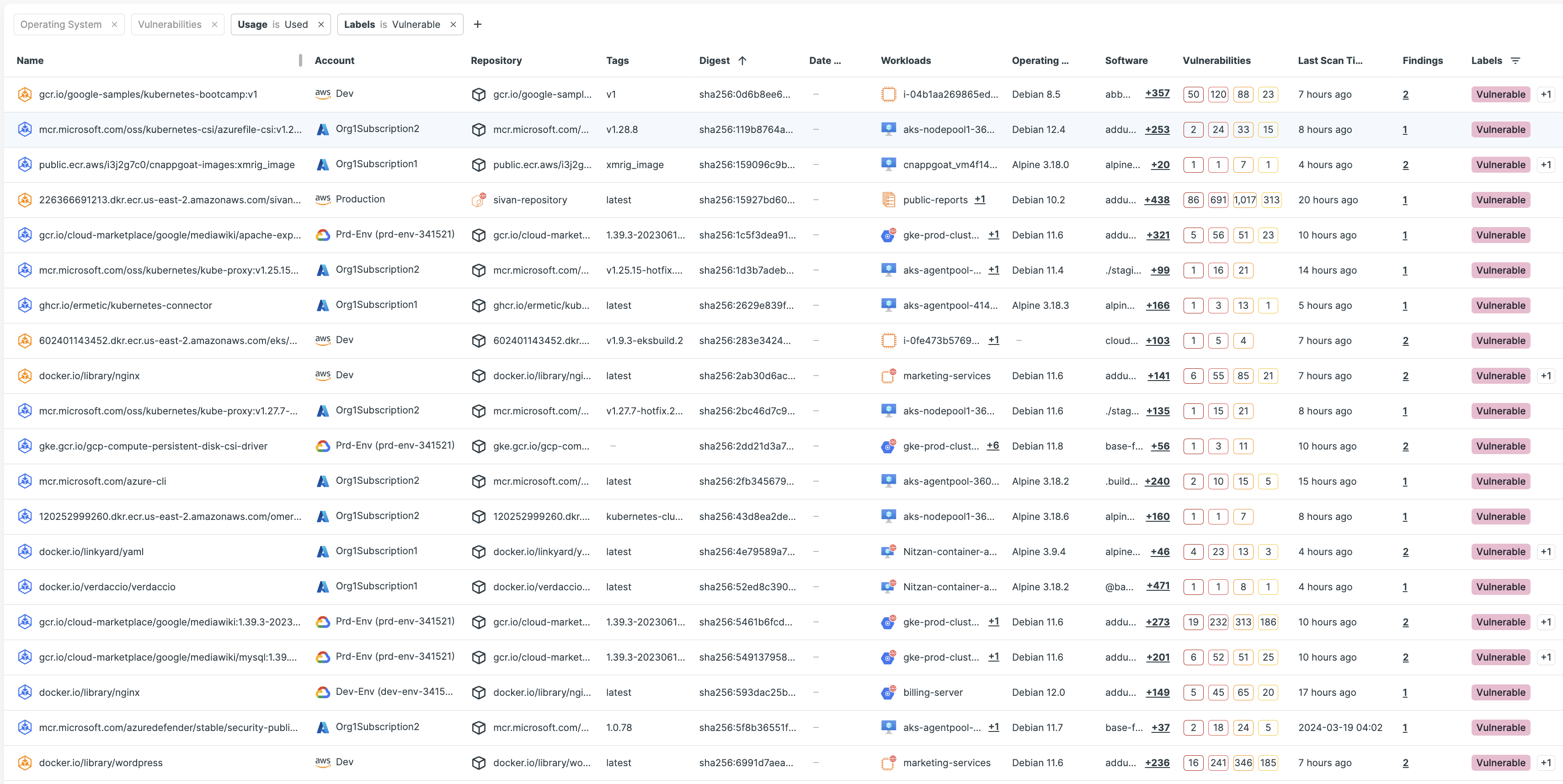
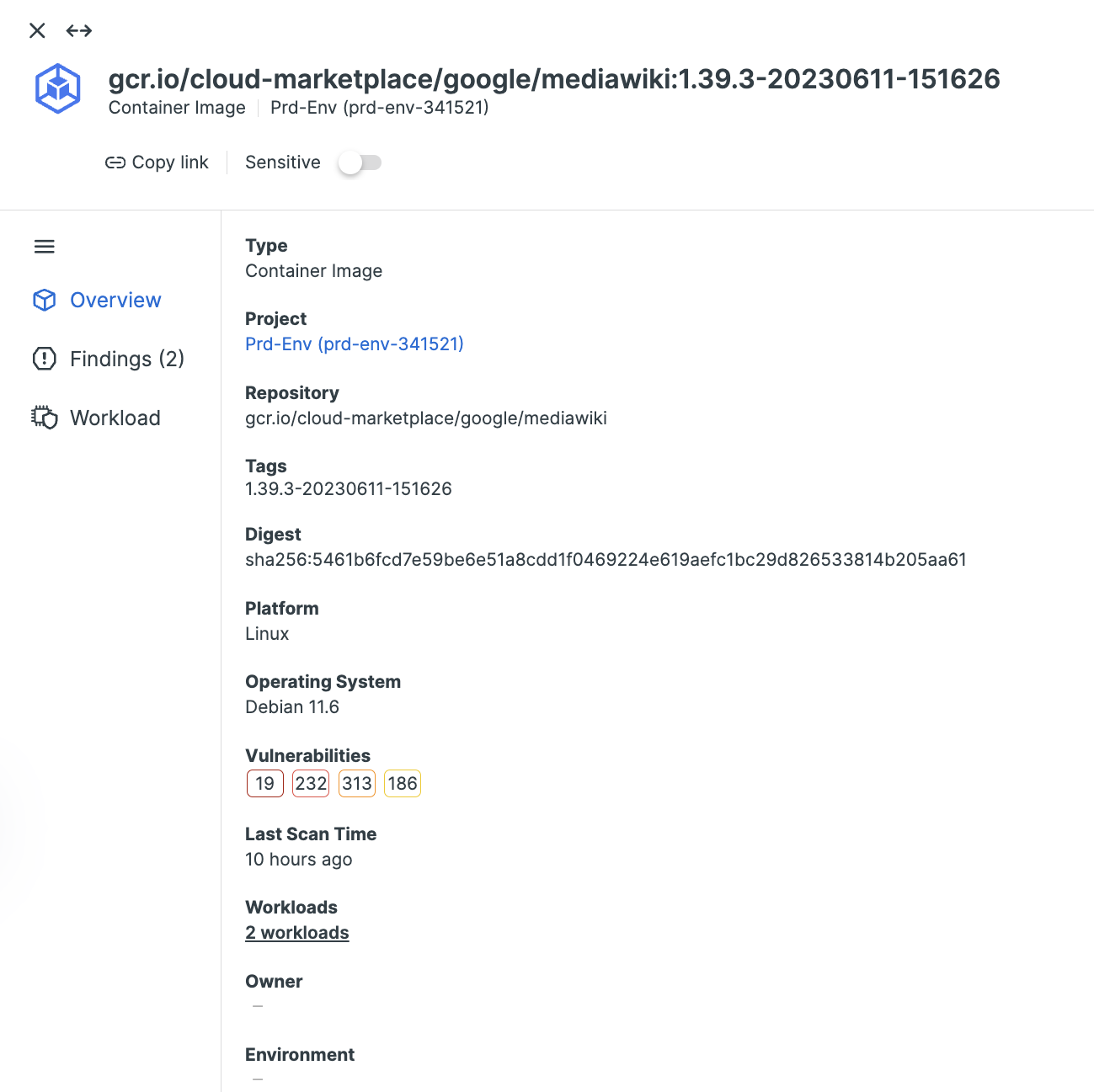
Gaining pre-production visibility into containers is critical to understanding potential risks in containerized applications. Give DevOps teams the information they need to quickly remediate vulnerabilities and misconfigurations in container images and registries early in the development process.
See how
Preventive security integrated into your container ecosystem
With container security insights integrated into the Tenable One Exposure Management Platform, you get comprehensive visibility, context and prioritization of your entire attack surface.
Get end-to-end visibility and risk context across containers
Eliminate vulnerabilities early
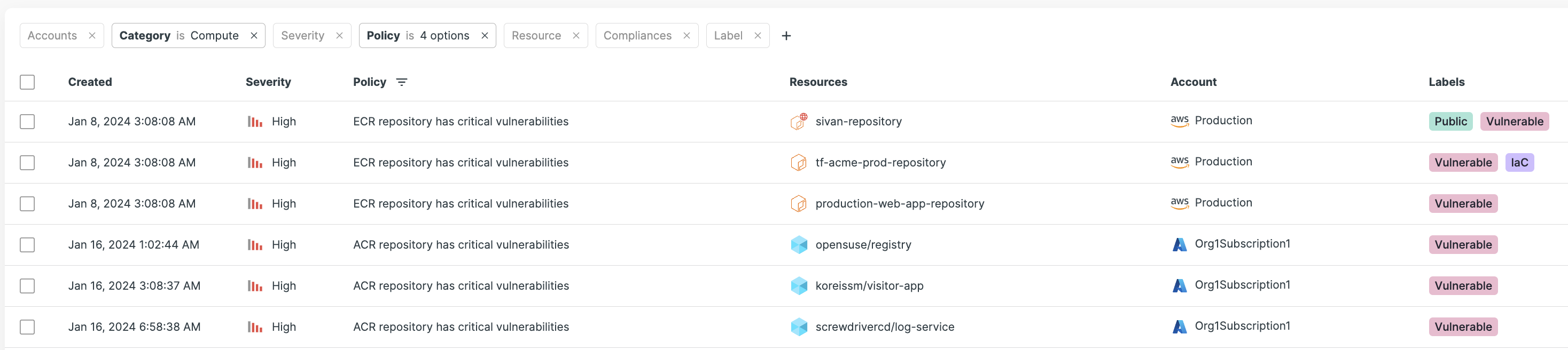
Tenable Cloud Security delivers end-to-end visibility into public and private container registries, providing vulnerability assessment, malware detection and policy enforcement across the software development lifecycle (SDLC) — from development to deployment. By integrating with developer build systems, Tenable Cloud Security brings proactive visibility to solve the complex security challenges in your hybrid and multi-cloud environments.
Improved DevSecOps workflows
Tenable Cloud Security seamlessly and securely enables DevSecOps processes by integrating with the tools you already know and trust. Get visibility and context into all types of vulnerabilities across the development lifecycle and empower developers and cloud architects to produce secure and compliant code.
Customizable policy enforcement
Ensure containers comply with policies and that they have not drifted from approved baselines before you release them into production. Notify developers immediately with specific remediation advice when container images exceed risk thresholds and know which vulnerabilities in your environment you need to remediate first. Easily create custom policies with Tenable’s no-code policy editor and ensure your workloads are compliant with corporate and industry standards.
Learn more about Tenable Cloud Security
Using [Tenable Cloud Security] automation allowed us to eliminate exhaustive manual processes and perform in minutes what would have taken two or three security people months to accomplish.
- Tenable Cloud Security