When It Comes to Industrial Cybersecurity, Follow The Data

A cyberattack at India’s largest nuclear power plant reveals the risks of outdated workstations and the need to upgrade industrial security systems.
The postmortem analysis of most cyberattacks often reveals that indicators of compromise were present leading up to the incident, but the dots were not connected early enough. In October of this year, the nuclear reactor complex at India’s Kudankulam Nuclear Power Plant (KNPP) suffered what the government has now termed a cyberattack. Originally it was not characterized as such. To be clear, an attack like this can happen to any organization. KNPP was just the latest victim. When it comes to this type of security breach, it is really quite simple. The data doesn't lie.
Reported malware infection at KNPP nuclear facility
On October 29, the Nuclear Power Corporation of India released a statement denying reports that one of its power plants had suffered a cyberattack. Officials stated, “any cyberattack on the nuclear power plant control system is not possible.”

The next day, KNPP leadership reversed their position. They issued a second communique revealing that malware was found in the system at the KNPP facility and was traced to an “infected PC that belonged to a user who was connected to the internet for administrative purposes.”
Almost immediately, experts including Pukhraj Singh, a former security analyst for India's National Technical Research Organization (NTRO), took to social media stating that the security incident went deeper than reported by the company.
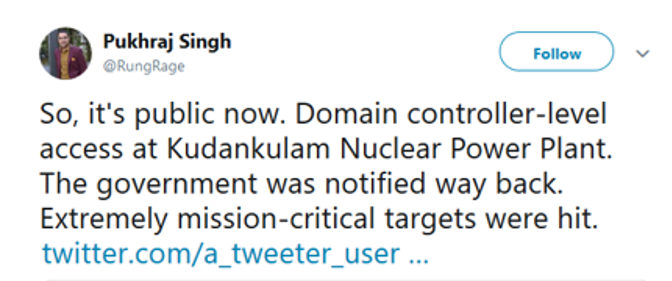
In the ensuing three-week period, new data “dots” have been revealed, including the fact that KNPP had issued a tender earlier this year to purchase Windows-based PCs. In the ensuing time period, several of the facility's reactors needed to be shut down due to what was reported as an “SG level low” alarm.
Media reports issued this week attributed the attack to North Korea and to date pundits in the field have been quoted in the press describing the lack of transparency on what actually happened with the cyberattack.
KNPP is not alone or unique in its response to what has been verified as a cyberattack on a nuclear plant. In many ways, it should be recognized that KNPP was able to respond and avoid any catastrophic failure at the plant. The question is, could they have known about the attack earlier?
More than ever, cyberattacks on critical infrastructure are occurring with frightening regularity. Rogue factions and “unfriendly” governments are taking advantage of the convergence between IT and operationally technology (OT) systems, which has eroded the traditional air gap and compromised industrial networks that often lack the same level of security as their sister IT networks. Once hackers gain access, they can perform reconnaissance and gain “red button” functionality to modify industrial processes in ways that can cause more damage than a traditional missile attack.
Preventing future cyber attacks
One of the lessons we can learn from the KNPP incident is the need for situational awareness when it comes to securing OT environments, including the ability to maintain a real-time inventory of assets. To complement this visibility, active threat hunting can be achieved through “device integrity” tests or actively querying devices such as programmable logic controllers (PLCs) and distributed control systems (DCSs) in their native language to detect unauthorized changes.
Meanwhile, the introduction of IoT (internet of things) technology in OT environments exposes industrial assets to new risks. Maintaining an up-to-date inventory of deployed assets along with granular detail such as the make, model number and manufacturer, patch levels and configurations can provide deep insight into what devices are operational at any point in time, which need to be updated due to vulnerability disclosures, and which require maintenance or rotation out of the OT environment.
In terms of detecting potential malware, OT should adopt the “onion” approach commonly used in IT security. This requires a multi-threat detection engine that searches for policy violations and also looks for anomalous behavior that is unique and specific to each environment. It also includes the practice of “crowd-sourcing” data on new threats, which can be accomplished by centralizing anonymized intelligence across multiple companies and industries to uncover indicators of emerging attacks and provide participating organizations with “digital inoculation” against them earlier.
A robust and forward-leaning approach to securing critical infrastructure and manufacturing environments requires the same rigor as we have deployed in IT for decades. The combination of constant employee training, deploying the right security with cooperation between IT and OT, and the perpetual examination and reexamination of policies and procedures will help organizations gain the situational awareness needed to identify security threats earlier and protect themselves against industrial cybersecurity risk.
To learn more about securing your critical infrastructure against cyber threats, see our Tenable.ot whitepaper, “Industrial Cybersecurity in the New Era of Distrust.”
- SCADA


