Tenable Bolsters Its Cloud Security Arsenal with Malware Detection

Tenable Cloud Security is enhancing its capabilities with malware detection. Combined with its cutting-edge, agentless vulnerability-scanning technology, including its ability to detect anomalous behavior, this new capability makes Tenable Cloud Security a much more complete and effective solution. Read on to find out how.
In the ever-evolving landscape of cloud computing, security remains paramount. Even though cloud adoption has become mainstream, many threats and attack tactics still rely on malware payloads. Thus, cloud security programs must include the ability to detect them.
Tenable Cloud Security can now find malware in many different cloud workloads. This ability will help make cloud security easier and more effective for our customers.
This feature significantly enhances our cloud security solution by not only providing detection of malware but also by offering the ability to remediate the underlying misconfigurations before bad actors can exploit them.
It doesn’t matter where the infected file originates from: a container image, an infected machine imageI or the activity of the machine itself. If it's running somewhere, we’ll find it!
Bridging preventive and detection security measures
Tenable excels in preventative security measures, helping clients to identify and mitigate risks before they escalate. The addition of malware detection enhances this approach. Malicious binaries are seldom accidental, and our service's integration with SIEM solutions facilitates rapid response from security teams. This is in addition to our existing anomaly detection capabilities, which allow you to identify potential attack patterns that deviate from a baseline of normal behavior.
How malware detection fits In
Understanding the full scope of potential risks in cloud infrastructure is complex. Tenable Cloud Security’s new malware detection capabilities integrate seamlessly with our existing suite of services, including vulnerability management, network configuration, and identity and entitlements analysis. This synergy helps users easily achieve a robust security posture by swiftly pinpointing and prioritizing the most critical issues, while still having all discrete data points easily available.
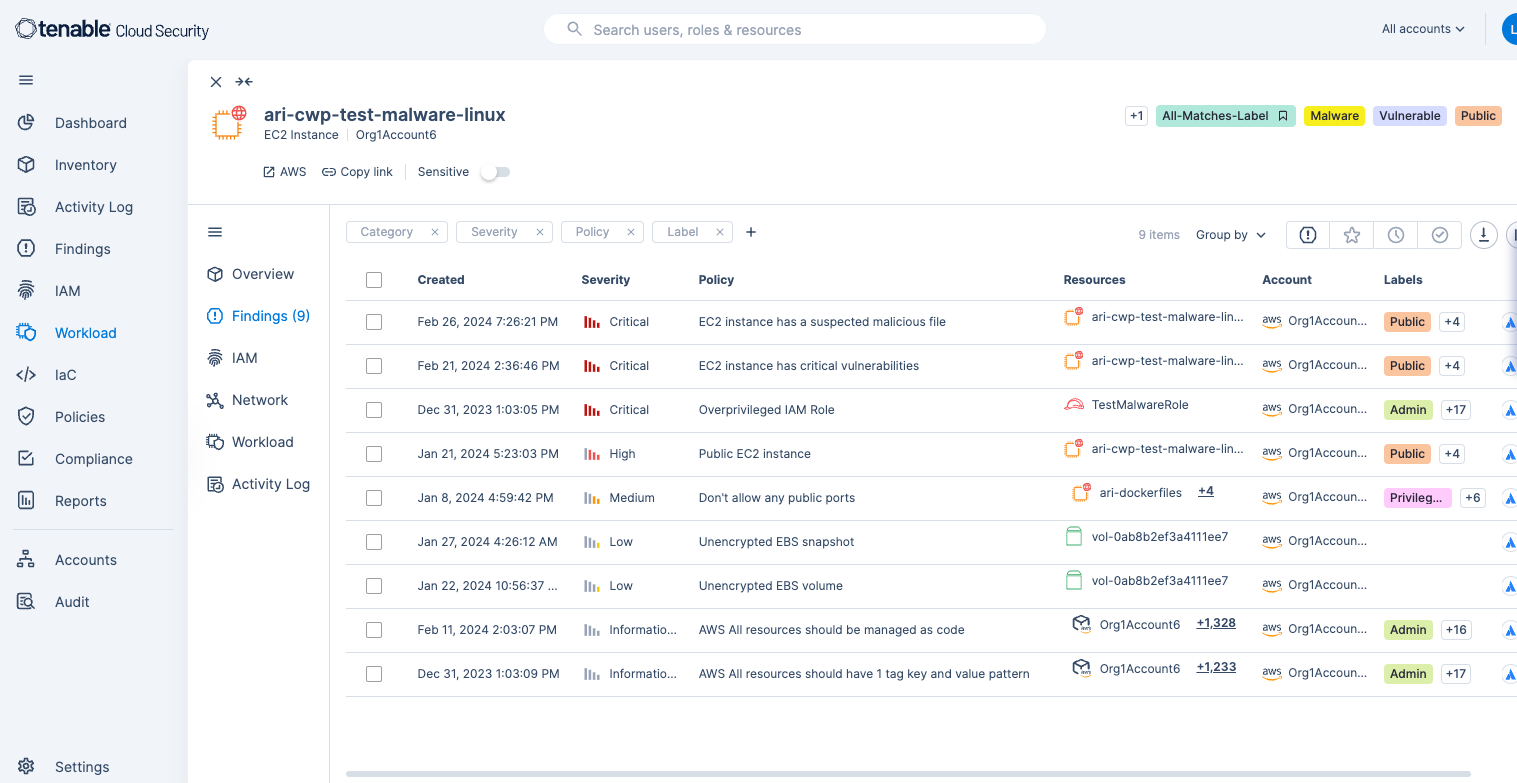
For example, in Figure 1 we can see that malicious files were found in addition to critical vulnerabilities, an overprivileged IAM role and the machine is public to the internet. All that put together makes up what we call a “toxic combination.” Being able to surface those findings is extremely important in prioritizing what actions to take.
Diversity in detection: From webshells to APTs
Tenable Cloud Security’s malware detection capability is exceptionally versatile, able to identify a wide spectrum of problematic files from simple webshells. advanced persistent threats (APTs) in multiple formats, including Portable executable (PE) files, Executable and Linkable Format (ELFs), and various script types. This malware detection feature spans multiple operating systems like Linux and Windows and is compatible with leading cloud service providers such as Azure, GCP, and AWS.
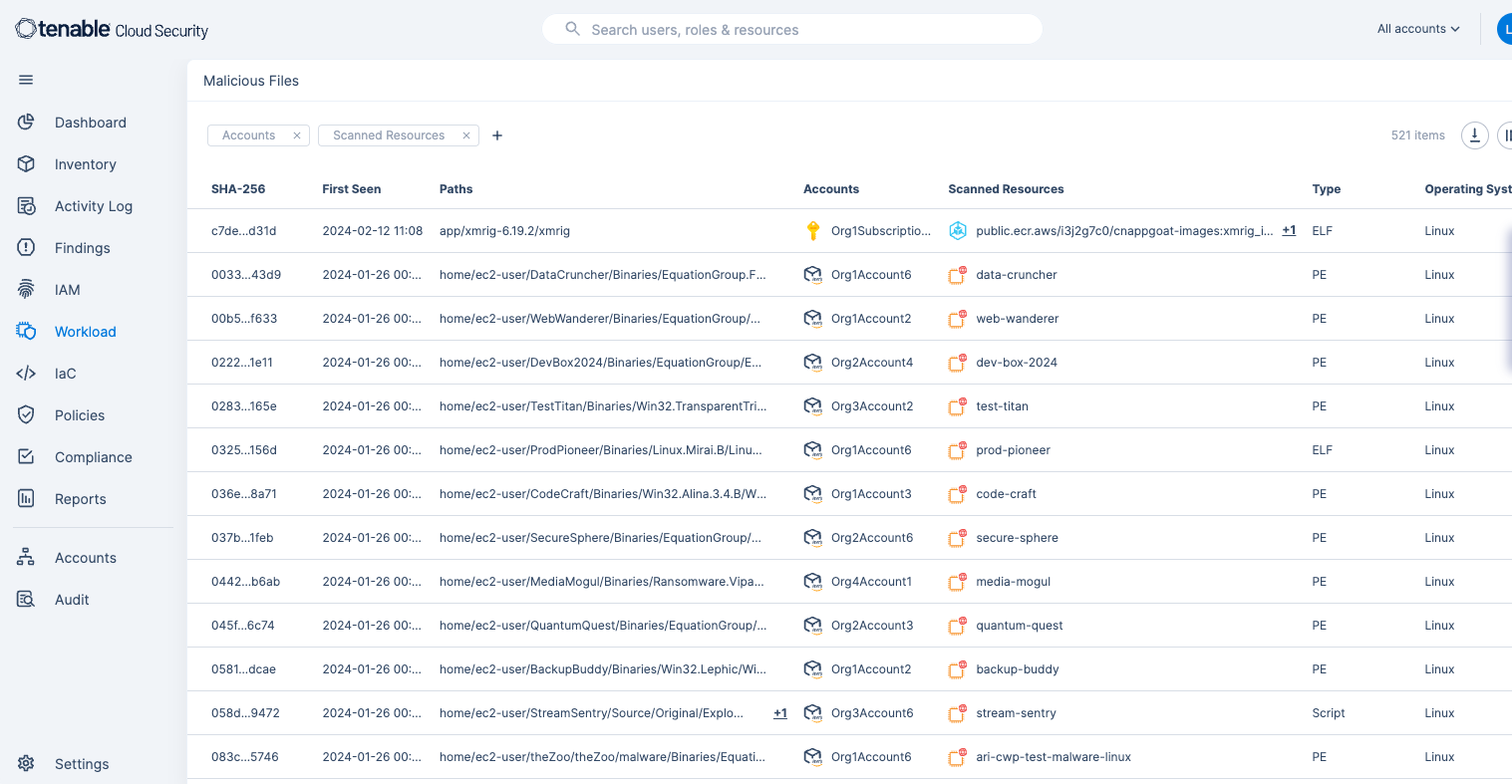
Leveraging advanced intelligence
Our approach is data-driven, utilizing dozens of intelligence sources, augmented by Tenable’s unique analytical methods. This robust analysis framework ensures an accurate assessment of the potential risk posed by each infected file, enhancing the overall security landscape for our clients.
Always look at the intent: Admin tool flags
Sometimes what separates malicious tools used by attackers from legitimate administration software is only the intent of who deployed it. Think about it for a moment: Is a command and control (C&C) server used by attackers technically any different from the remote control software used by your IT department?
For this reason, Tenable Cloud Security goes a step further by identifying tools that, while not inherently malicious, can be exploited for nefarious purposes. For example, tools like WinEXE, which facilitate cross-platform management, are scrutinized for potential misuse, ensuring comprehensive coverage of all security aspects.
These tools may be there for a good reason, but it’s important to know of their existence in correspondence with other issues such as vulnerability exposures, network configurations that allow external access, permissive identities and so on. This context allows you to understand the threat these tools may pose if they were to be accessed by an attacker.
Your next step in cloud security
In summary, Tenable Cloud Security’s new malware detection is extremely powerful, because now our solution combines this detection functionality with our existing preventive capabilities.
Cloud security is not just about having a holistic view of your cloud environment’s security posture or just about detecting threats. It’s about both, at the same time, all the time.
We invite you to experience the future of cloud security. Get a demo of Tenable Cloud Security today and empower your organization with cutting-edge malware detection and comprehensive security management.
- Cloud
- Exposure Management
- Malware



