Microsoft’s August 2020 Patch Tuesday Addresses 120 CVEs (CVE-2020-1337)

Microsoft patched 120 CVEs in August, marking the sixth month in a row of addressing over 100 CVEs
Microsoft, for the sixth month in a row, patched over 100 CVEs in the August 2020 Patch Tuesday release, including 17 CVEs rated critical. For the first time in three months, this update includes patches for two vulnerabilities that were observed being actively exploited in the wild. This month’s update includes patches for Microsoft Windows, Microsoft Edge, Microsoft ChakraCore, Internet Explorer, Microsoft Scripting Engine, SQL Server, Microsoft Jet Database Engine, .NET Framework, ASP.NET Core, Microsoft Office and Microsoft Office Services and Web Apps, Microsoft Windows Codecs Library and Microsoft Dynamics.
CVE-2020-1337 | Windows Print Spooler Elevation of Privilege Vulnerability
CVE-2020-1337 is an elevation of privilege vulnerability that exists when the Windows Print Spooler service improperly allows arbitrary writing to the file system. This vulnerability was found as a bypass of the patch for CVE-2020-1048 (also known as PrintDemon), a previous Windows Print Spooler Elevation of Privilege Vulnerability, both of which were identified by researchers Peleg Hadar and Tomer Bar of SafeBreach Labs. The pair recently presented at both the Black Hat USA and DEF CON conferences, where they discussed this new zero-day vulnerability as part of their talk, A Decade After Stuxnet's Printer Vulnerability: Printing is Still the Stairway to Heaven. While an attacker must have the ability to execute an application on a host to exploit this vulnerability, their research demonstrates how this vulnerability could be chained with additional vulnerabilities to further compromise a device and propagate across a network. A proof-of-concept (PoC) is expected to be released soon on their GitHub page.
CVE-2020-1464 | Windows Spoofing Vulnerability
CVE-2020-1464 is a spoofing vulnerability that exists when Windows improperly validates file signatures. An attacker who exploits this flaw could bypass security features intended to prevent improperly signed files from being loaded. According to Microsoft, this vulnerability has been observed to be exploited in the wild. Microsoft's patch corrects the issue by addressing how Windows validates file signatures.
CVE-2020-1494, CVE-2020-1495, CVE-2020-1496, CVE-2020-1498 and CVE-2020-1504 | Microsoft Excel Remote Code Execution Vulnerability
CVE-2020-1494, CVE-2020-1495, CVE-2020-1496, CVE-2020-1498, and CVE-2020-1504 are remote code execution vulnerabilities in Microsoft Excel. An attacker would need to convince a user to open a maliciously crafted Excel file in order to exploit this vulnerability. Successful exploitation would allow an attacker to execute code as the current user.
CVE-2020-1539, CVE-2020-1540, CVE-2020-1541, CVE-2020-1542, CVE-2020-1543, CVE-2020-1544, CVE-2020-1545, CVE-2020-1546, CVE-2020-1547, CVE-2020-1551 | Windows Backup Engine Elevation of Privilege Vulnerability
CVE-2020-1539, CVE-2020-1540, CVE-2020-1541, CVE-2020-1542, CVE-2020-1543, CVE-2020-1544, CVE-2020-1545, CVE-2020-1546, CVE-2020-1547, and CVE-2020-1551 are elevation of privilege vulnerabilities in Windows Backup Engine. An attacker with the ability to execute code on a system would be able to exploit this vulnerability to elevate privileges on a vulnerable host with specially crafted code. In a likely scenario, an attacker could exploit a different vulnerability that gives them restricted user access, and then exploit this vulnerability to gain elevated privileges.
CVE-2020-1568 | Microsoft Edge PDF Remote Code Execution Vulnerability
CVE-2020-1568 is a remote code execution vulnerability that exists when Microsoft Edge PDF Reader improperly handles objects in memory. Successful exploitation of this vulnerability would allow an attacker to corrupt memory in such a way that they could execute arbitrary code in the context of the current user. To exploit this vulnerability, an attacker could host a website with specially crafted PDF content and convince a victim to visit the website. Alternatively, an attacker could upload a specially crafted PDF to websites that accept or host user-provided content, still requiring them to convince a victim to visit said websites.
CVE-2020-1473, CVE-2020-1557, CVE-2020-1558 and CVE-2020-1564 | et Database Engine Remote Code Execution Vulnerability
CVE-2020-1473, CVE-2020-1557, CVE-2020-1558, and CVE-2020-1564 are remote code execution vulnerabilities that exist when the Windows Jet Database Engine improperly handles objects in memory. Successful exploitation of these vulnerabilities would allow an attacker to execute arbitrary code on an affected system. To exploit this vulnerability, an attacker must convince a victim to open a specially crafted file or visit a malicious website.
CVE-2020-1380 | Scripting Engine Memory Corruption Vulnerability
CVE-2020-1380 is a remote code execution vulnerability that exists in the way that the scripting engine handles objects in memory in Internet Explorer. Successful exploitation of this vulnerability would allow an attacker to corrupt memory in such a way that they could execute code in the context of the current user. According to Microsoft, this vulnerability has been observed to be exploited in the wild. Exploitation of this vulnerability requires an attacker to convince a victim to visit a specially crafted website or compromised website containing malicious code that exploits this vulnerability in Internet Explorer. Alternatively, an attacker could convince a victim to open a crafted document containing a malicious embedded ActiveX control marked as “safe for initialization” in an application or Microsoft Office document that hosts the Internet Explorer rendering engine.
CVE-2020-1472 | Netlogon Elevation of Privilege Vulnerability
CVE-2020-1472 is an elevation of privilege vulnerability in Netlogon when an attacker establishes a secure channel connection to a domain controller. An unauthenticated attacker could use MS-NRPC to connect to a domain controller as a domain administrator. Microsoft adds an important note to their advisory that this patch is only the first of two patches to fix this vulnerability, and the second patch is slated to be released in Q1 2021.
CVE-2020-1509 | Local Security Authority Subsystem Service Elevation of Privilege Vulnerability
CVE-2020-1509 is an elevation of privilege vulnerability in the Local Security Authority Subsystem Service (LSASS). A remote authenticated attacker could use a malicious authentication request to elevate privileges on a vulnerable system.
CVE-2020-1585 | Microsoft Windows Codecs Library Remote Code Execution Vulnerability
CVE-2020-1585 is a remote code execution vulnerability in Microsoft Windows Codecs Library. Exploitation of this vulnerability would require a program to access a crafted image file which could allow the attacker to take control of the system. While this would require user interaction in order to exploit, Microsoft still rates this as critical.
CVE-2020-1554 | Media Foundation Memory Corruption Vulnerability
CVE-2020-1554 is a memory corruption vulnerability in Windows Media Foundation. Exploitation of this vulnerability would require a user to interact with a malicious document or web page. Successful exploitation would grant the attacker full administrative rights over the affected system.
CVE-2020-1555 | Scripting Engine Memory Corruption Vulnerability
CVE-2020-1555 is a remote code execution vulnerability that exists in the way that the scripting engine handles objects in memory in Microsoft Edge (HTML-based). Successful exploitation of this vulnerability would allow an attacker to corrupt memory in such a way that they could execute code in the context of the current user. To exploit this vulnerability, an attacker would need to convince a victim to visit a website that contains malicious code to exploit this vulnerability through Microsoft Edge (HTML-based). Alternatively, an attacker could host the exploit code on websites that accept or host user-provided content or advertisements, convincing their victim to visit one of these websites.
Tenable solutions
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains August 2020.
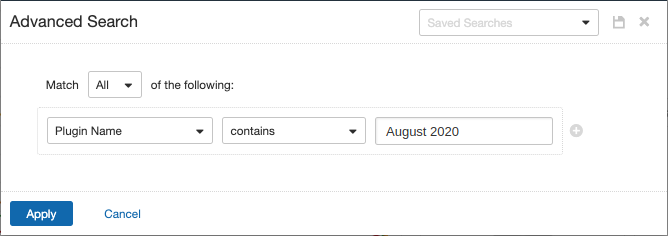
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from Tenable.io:
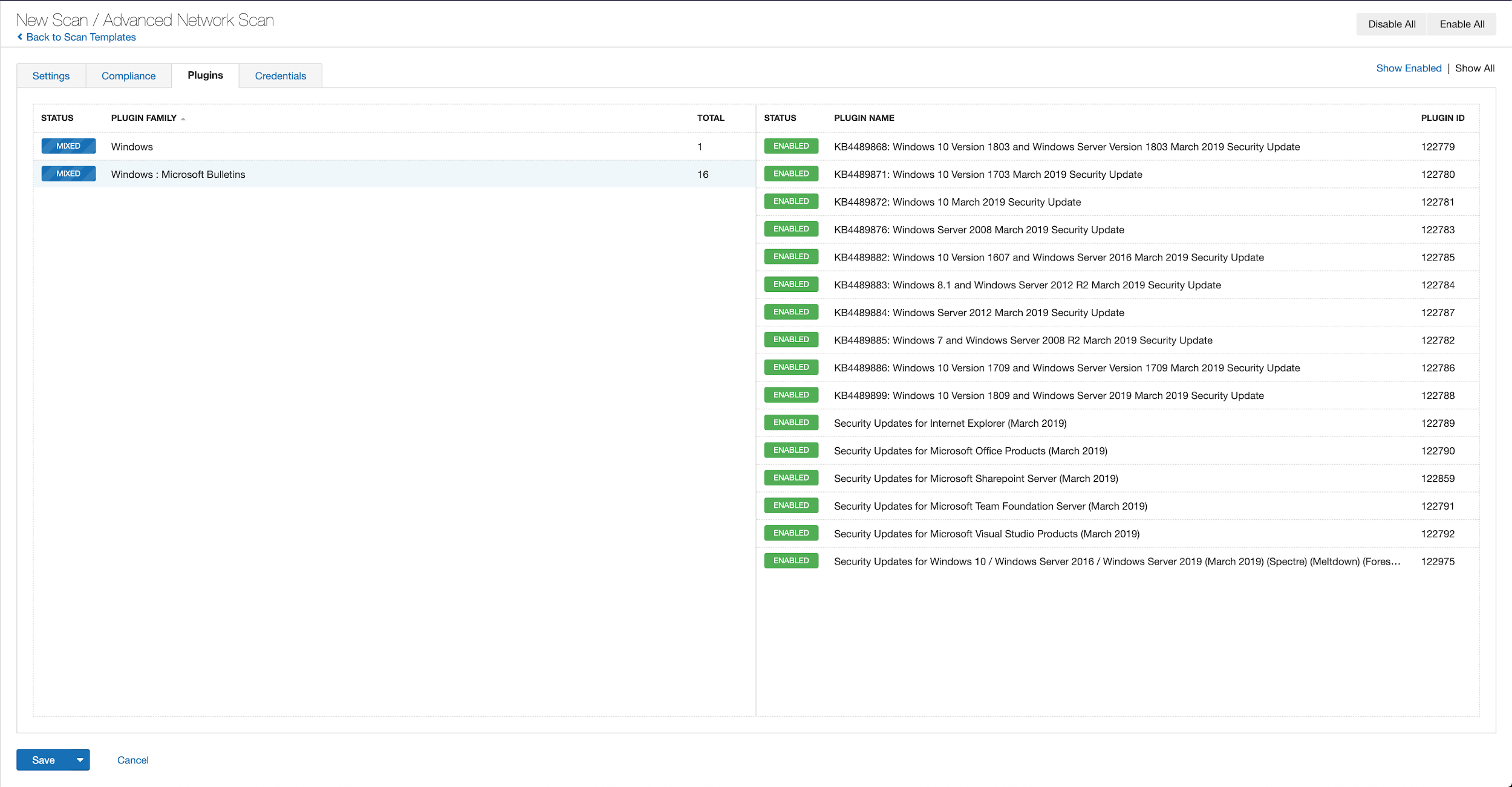
A list of all the plugins released for Tenable’s August 2020 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Get more information
- Microsoft's August 2020 Security Updates
- Tenable plugins for Microsoft August 2020 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management


