Cybersecurity Snapshot: 6 Things That Matter Right Now

Topics that are top of mind for the week ending Sept. 30 | Are you ready for the quantum threat? | Tips for protecting critical infrastructure from cyberattacks | How to prevent MFA fatigue attacks | “FiGHT” to secure 5G networks | And much more!
1. MFA fatigue in the spotlight
The social engineering attack known as multi-factor authentication (MFA) fatigue is in the spotlight after a cybercriminal used it successfully against Uber.
This is the typical scenario: A hacker steals credentials for an MFA-protected account and tries to annoy the user into approving the login attempt via a barrage of mobile push notifications.

In the Uber case, the hacker reportedly took his efforts to another level by actually contacting the targeted user – a Uber contractor – via Whatsapp, saying he was a Uber IT staffer.
So how can your organization prevent MFA fatigue attacks? Here are some recommendations from MITRE:
- Block login attempts from locations that are suspicious or don’t match the location of the MFA smart device.
- Restrict the number of MFA request prompts that can be sent to users.
- Educate users so that they only approve login requests they initiated and report unsolicited prompts.
For more information:
- “MFA fatigue attacks are on the rise: How to defend against them” (CSO)
- “High-Profile Hacks Show Effectiveness of MFA Fatigue Attacks” (SecurityWeek)
- “Quick Tip: MFA Fatigue Attacks” (Princeton Univ.)
- “MFA Fatigue: How Hackers Breached Uber, Microsoft, and Cisco” (Tech.io)
2. U.S. Congress tackles open source software security
Highlighting the U.S. government’s grave concern about the security of the software supply chain, new legislation focused on open source software (OSS) has just been introduced.
The bipartisan “Securing Open Source Software Act of 2022” was sponsored by two senators – Gary Peters (D-MI) and Rob Portman (R-OH) – and comes in response to the shocking discovery in November 2021 of the Log4Shell vulnerability in the ubiquitous Log4j open source component.

The bill, whose sponsors hold leadership positions in the Senate’s Homeland Security and Governmental Affairs Committee, calls for tasking the Cybersecurity and Infrastructure Security Agency (CISA) with:
- Creating a risk framework to assess how the federal government uses OSS
- Evaluating how this framework could be used by critical infrastructure operators
- Hiring experienced OSS developers so the government and the OSS community can collaborate and address future situations like the Log4j vulnerability
- Establishing a software security advisory subcommittee
To get more details, you can read:
- The full text of the bill
- The sponsors’ press release
- Commentary and analysis from the Open Source Security Foundation, The Washington Post, NextGov and Axios.
- “Apache Log4j Flaw: A Fukushima Moment for the Cybersecurity Industry” (Tenable)
3. Rinse and repeat: Cyberthreats top business concerns
In a survey of 1,200 U.S. business decision makers, cyberthreats topped all business concerns, specifically suffering a system breach and becoming a ransomware victim.
The “2022 Travelers Risk Index,” from the namesake insurance provider, also found gaping holes in respondents’ cyber preparedness, including an absence of:
- Endpoint detection and response (64%)
- Vendor cyber assessments (59%)
- Incident response plans (53%)
- Multi-factor authentication (48%)

Significantly, 26% said their company had suffered a data breach or a cyber event, with about half of those incidents happening in the past 12 months. Among these respondents, 71% have been successfully attacked more than once.
Still, a whopping 93% of respondents expressed confidence about their organizations’ ability to prevent or mitigate a cyber incident via the implementation of best practices, although 57% said it’s inevitable they’ll suffer a future cyberattack.
For more information about establishing strong cybersecurity foundations:
- NIST Cybersecurity Framework
- Cloud Security Alliance Cloud Controls Matrix
- Center for Internet Security’s Critical Security Controls
- MITRE ATT&CK Framework
- National Cyber Security Centre’s Cyber Essentials
4. Quantum computing’s security threat looms
Is quantum computing’s security threat on your risk radar screen yet? The drumbeat of concerns about the technology’s threat to data security and privacy is getting louder. The latest indication comes from a Deloitte online poll of 400-plus professionals who have assessed the benefits and downsides of quantum computers.
These systems don’t exist yet, but when they become available – maybe around 2030 – they’ll be able to decrypt data protected with today’s public-key cryptographic algorithms. While “quantum resistant” algorithms are in the works, cybercrooks are stealing data now to decrypt it later with quantum computers – a scheme known as “harvest now, decrypt later.”
About 50% of survey respondents said they believe their organization is at risk for this type of attack. When asked if their organization has conducted a quantum risk assessment, 45% said they either completed one or plan to conduct one within the next year. Another 16% plan to conduct one in two to five- years and 6% in six to 10 years. About 7% don’t plan to do one.
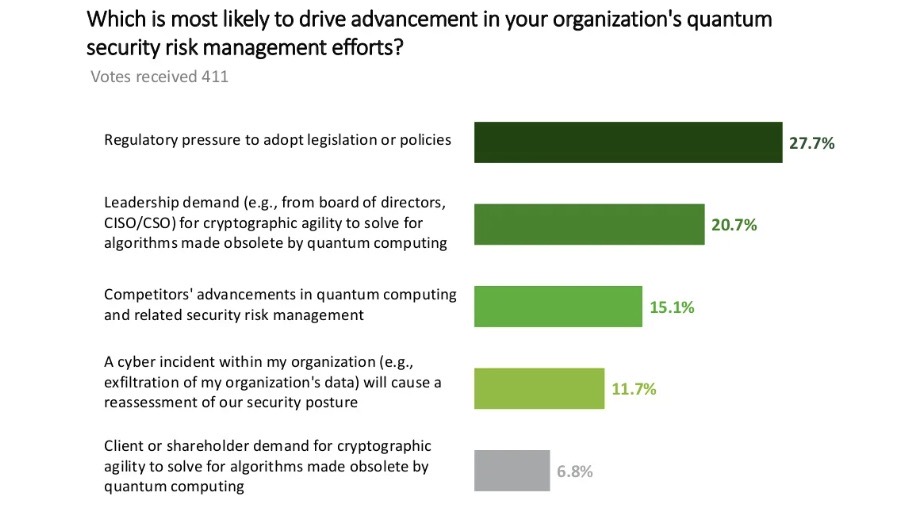
(Source: “Harvest Now, Decrypt Later Attacks Pose a Security Concern as Organizations Consider Implications of Quantum Computing” report from Deloitte, September 2022)
Recommendations from Deloitte include:
- Making a cryptographic inventory
- Sharpening data governance
- Managing certificates
For more information:
- “Quantum apocalypse: Experts warn of ‘store now, decrypt later’ hacks” (Silicon Republic)
- “Now Is the Time to Plan for Post-Quantum Cryptography” (DarkReading)
- “Four new defenses against quantum codebreakers” (Politico)
- “Getting Ready for Post-Quantum Cryptography” (U.S. National Institute of Standards and Technology)
- “Preparing for Post-Quantum Cryptography” (U.S. Department of Homeland Security)
5. CISA/NSA: Tips to protect critical infrastructure from cyberattacks
The U.S. government is warning about cyberthreats faced by critical infrastructure facilities via vulnerable IT and operational technology / industrial control systems (OT/ICS) environments.
In an advisory, the government explains why these environments are increasingly at risk to cyberattacks; details how attackers – including advanced persistent threat (APT) groups – target them; and offers mitigation strategies.

The document from the National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) lists the steps attackers typically follow:
- Based on their motivation, such as financial, political or military, they pick a desired effect (disrupting, disabling or destroying) and select a target.
- They collect intelligence via multiple avenues, including by breaching the facility’s IT network and by gathering publicly available information.
- They then develop techniques and tools to breach the system, often by building a mock-up of the target system.
- They gain initial access to the system, typically via remote access points that are often poorly secured.
- Once they have access to the targeted OT/ICS system, they’ll disrupt the operator’s ability to monitor and control it; tamper with the system; and more.
“Using these techniques, cyber actors could cause various physical consequences. They could open or close breakers, throttle valves, overfill tanks, set turbines to over-speed, or place plants in unsafe operating conditions,” the document reads.
Recommended mitigation measures include:
- Limit exposure of system information, such as by avoiding offering details of its hardware, firmware and software in public forums.
- Identify and secure remote access points by creating a full inventory of them and limiting and hardening assets exposed to the internet.
- Restrict tools and scripts only to users authorized to perform tasks on the control system.
- Conduct regular security audits to validate all connections, review patching procedures, monitor system logs, and more.
- Implement a “dynamic network environment” by adding firewalls and routers from different vendors, modifying IP address pools and upgrading hardware and software.
For more information:
- “Stop Malicious Cyber Activity Against Connected Operational Technology” (CISA/NSA)
- “Control System Defense: Know the Opponent” (CISA/NSA)
- “IT/OT Convergence: Now Is the Time to Act” (Tenable)
- “CISA, NSA Guidance Tries to Reduce Alternatives for Securing ICS” (NextGov)
- “Accidental Convergence: A Guide to Secured IT/OT Operations” (Tenable)
6. A new framework for 5G network security
Attacks against 5G systems will ramp up as deployments of this mobile network technology increase, so securing them properly is critical. To that end, MITRE and the U.S. Defense Department have released a framework called “5G Hierarchy of Threats,” or FiGHT for short, intended for securing 5G ecosystems.

FiGHT contains three types of adversary tactics and techniques: theoretical, proof of concept and observed. It can be used to assess threats, emulate attacks and plan cyber investments.
Modeled after the MITRE ATT&CK framework, FiGHT is aimed primarily at telecom providers, manufacturers and cybersecurity researchers.
For more information about 5G security challenges and best practices:
- “5G Implementation Security Risks” (CISA)
- “5G Cybersecurity” (NIST)
- “Secure 5G” (U.S. National Telecommunications and Information Administration)
- “Tackling Security Challenges in 5G Networks” (EU Agency for Cybersecurity - ENISA)
- “Security Implications of 5G Technology” (DHS)
- Cybersecurity Snapshot
- Government
- Legislation
- Mobile Security
- NIST
- OT Security
- Research Reports
- Security Frameworks
