by Josef Weiss
June 15, 2015
With many devices connecting to the network, compliance to organizational standards is sometimes a difficult item to track. Endpoint security tends to be relatively simple such as personal firewalls, anti-virus software, or keeping patches up to date. Windows end point devices that are vulnerable and not compliant with organizational policy based or current accepted standards present great risks to an organization, including the threats of network intrusion and data disclosure. Non-protected end point devices running vulnerable applications may become a target and entry point for malicious attacks against the organization.
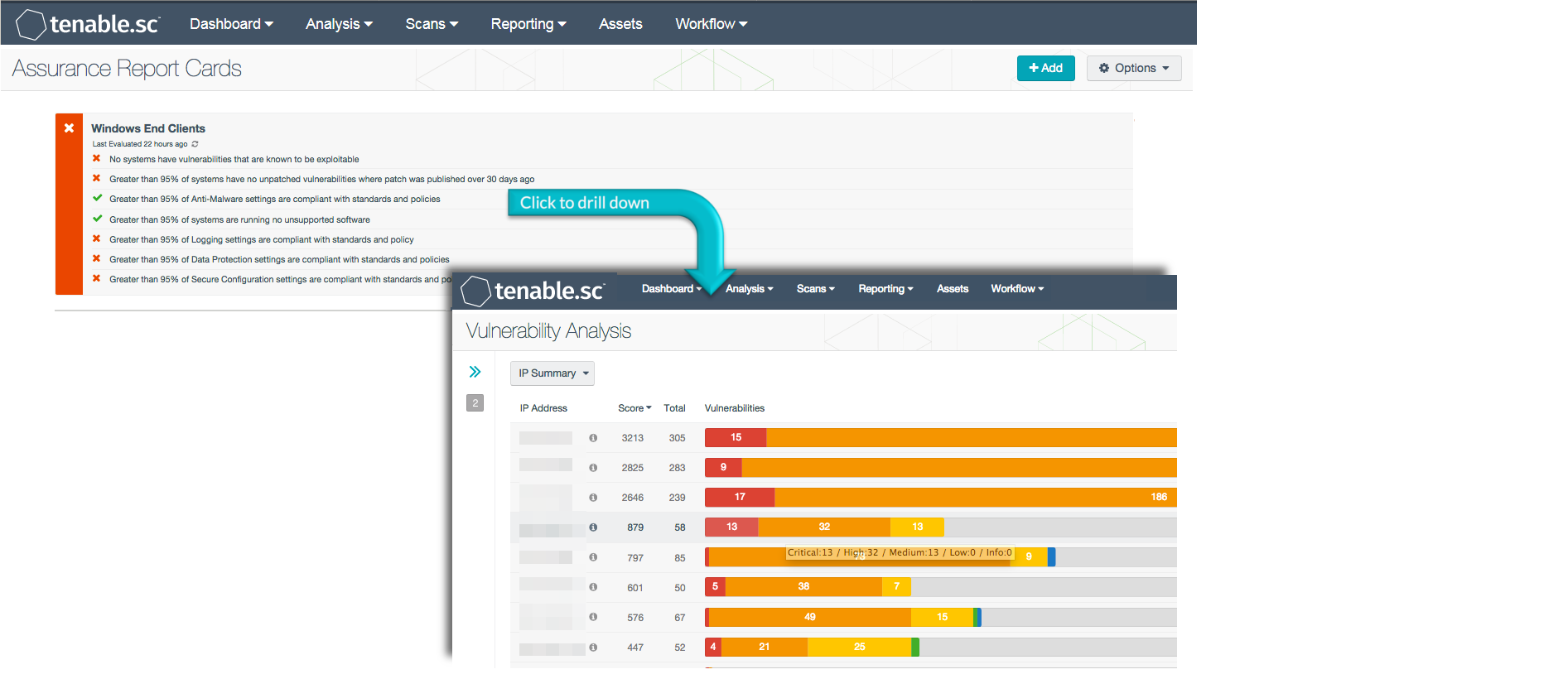
The Windows Client Assurance Report Card (ARC) presents policy statements that provide configuration details on Windows operating systems that are not considered servers. This is accomplished utilizing assets that define all Windows operating systems and Windows Server operating systems. Filters are then utilized to remove predefined Windows Server systems from the complete host list. The remaining hosts are analyzed as end point devices.
This ARC makes use of standards such as NIST 800-53, DoD Instruction 8500.2, and the PCI Data Security Standard to highlight compliance failures on Windows clients. These checks against organizational policies such as secure configurations, malware, unsupported software/applications, and data protection are conducted in an effort to present Compliant/Non-Compliant conditions to highlight conditions that may lead to exploit based attacks, and identify unpatched vulnerabilities in the environment. Organizational policies should be based on appropriate current accepted standards.
The information in this ARC will allow the Compliance Manager to continuously monitor policy compliance for Windows end point clients, so that weak policies and weak policy enforcement can be identified and corrected and the network made more secure.
More details on each of the policy statements included in the ARC are given below. The Compliance Manager can click on a policy statement to bring up the analysis screen to display details on any compliance failures related to that policy statement. In the analysis screen, setting the tool to IP Summary will display the systems on which the compliance failures are present.
This ARC relies both on audit results obtained from Nessus scans of the systems on the network using appropriate audit files, and on vulnerability information collected by Nessus and Nessus Network Monitor (NNM). The descriptions of the policy statements below include information on what details are used to find those checks relevant to the policy statement and what the percentage pass rate must be to be considered compliant. The audit files and ARC policy statement parameters are guides that can be customized as necessary to meet organizational requirements.
More details on each of the policy statements included in the ARC are given below. This ARC is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The ARC requirements are:
- Tenable.sc 5.0
- Audit results
- Nessus 8.5.1
- NNM 5.9.0
Tenable's Tenable.sc Continuous View (Tenable.sc CV) is the market-defining continuous network monitoring platform. Tenable.sc CV includes active vulnerability detection with Nessus and passive vulnerability detection with Tenable's Nessus Network Monitor (NNM), as well as log correlation with Tenable's Log Correlation Engine (LCE). Using Tenable.sc CV, an organization will obtain the most comprehensive and integrated view of its network, in order to best measure compliance against complex standards.
ARC Policy Statements:
- No systems have vulnerabilities that are known to be exploitable. This policy statement displays Compliant in green if no Windows end point devices have vulnerabilities that are known to be exploitable.
- Greater than 95% of systems have unpatched vulnerabilities where patch was published over 30 days ago. This policy statement displays Compliant in green if 95% or more of Windows end point devices have no unpatched vulnerabilities where the patch was published over 30 days ago.
- Greater than 95% of systems are running unsupported software. This policy statement displays Compliant in green if 95% or more of Windows end point devices are running no unsupported applications or software.
- Greater than 95% of Secure Configuration settings are compliant with standards and policies. This policy statement displays Compliant in green if 95% or more of the compliance checks on Secure Configuration settings have passed.
- Greater than 95% of Anti-Malware settings are compliant with standards and policies. This policy statement displays Compliant in green if 95% or more of the compliance checks on Anti-Malware settings have passed.
- Greater than 95% of Data Protection settings are compliant with standards and policies. This policy statement displays Compliant in green if 95% or more of the compliance checks on Data Protection settings have passed.
- Greater than 95% of Logging settings are compliant with standards and policy. This policy statement displays Compliant in green if 95% or more of the compliance checks on Logging settings have passed.