by Josef Weiss
January 29, 2026
Public-key cryptography is the invisible trust fabric which secures web browsing, VPN connectivity, cloud authentication, software updates, and identity verification. For decades, the global economy, national security apparatus, and critical infrastructure have relied on asymmetric cryptography—specifically RSA and Elliptic Curve Cryptography (ECC)—to secure this data. Their security rests on the mathematical difficulty of factoring large integers or solving discrete logarithm problems within any realistic timeframe. Quantum computing changes that assumption. Quantum computers utilize qubits, which combined with quantum entanglement, allows for massive parallelism in calculation. Tenable’s Research team has developed a series of plugins to help identify an organization's progress in mitigating this future threat.
While quantum systems, capable of shattering current encryption standards may be years away, there is a significant threat operational today, through a strategic doctrine of "Harvest Now, Decrypt Later" (HNDL). Adversaries can identify and capture and store encrypted data now, awaiting for future decryption when quantum decryption becomes readily available, and the data can be decrypted retroactively. For security leaders this creates a familiar strategic problem. Public-key cryptography is embedded everywhere: certificate authorities, TLS stacks, VPN gateways, secure email, identity providers, firmware signing, code pipelines, and cloud key management. The implications are catastrophic for current standards:
- RSA-2048 and RSA-4096: Completely broken.
- ECDH and ECDSA (Elliptic Curve): Completely broken.
- Diffie-Hellman: Completely broken.
Tenable has a number of plugins that assist organizations, including:
- 277650 - Remote Services Not Using Post-Quantum Ciphers.
- 277652 - Target Cipher Inventory.
- 277653- Remote Services Using Post-Quantum Ciphers.
Understanding the impact of the transition to using Post Quantum Ciphers is where security teams need actionable insight, understanding where vulnerable cryptographic algorithms are deployed across their infrastructure. To support this visibility, Tenable provides the Post Quantum Ciphers Dashboard. This Tenable Vulnerability Management dashboard is designed to help organizations identify systems relying on cryptographic algorithms that will be vulnerable in a post-quantum world. Key features are the identification where RSA and ECC are currently deployed across your infrastructure, supporting prioritization of modernization efforts. Information within the dashboard assists organizations identify remote services using/not using post-quantum ciphers, including the identification of ciphers in Web Application Scanning (WAS) environments, and identifies potentially vulnerable ciphers, certificates and assets.
Organizations need a coherent operational strategy to navigate the migration. Based on NIST SP 1800-38 and CISA guidance, the following phased approach is recommended.
Phase 1: Automated Discovery -> Phase 2: Prioritization and Risk Assessment -> Phase 3: Remediation and Crypto-Agility -> Phase 4: Continuous Verification
This approach begins with establishing the baseline. Tenable Plugin 277652 (Target Cipher Inventory) Extends detection capabilities to cover cryptographic ciphers and algorithms discovered during the scan as a machine parsable JSON file attachment. Tenable Plugins 277653 (Remote Services Using Post-Quantum Ciphers) and 277650 (Remote Services Not Using Post-Quantum Ciphers) help filter the signal from the noise. Identify systems with the highest risk and the most critical data, allowing organizations to move quickly into the remediation phase. Regression is prevented naturally with Tenable’s ability to provide Continuous Verification by incorporating this assessment into regular scanning intervals.
Bottom line, these tactics allow for the surfacing of cryptographic dependencies across the environment, security teams gain the operational intelligence needed to begin structured migration planning today. Organizations that begin assessing exposure now, establish migration roadmaps, and integrate post-quantum readiness into security strategy will move through this transition deliberately and safely.
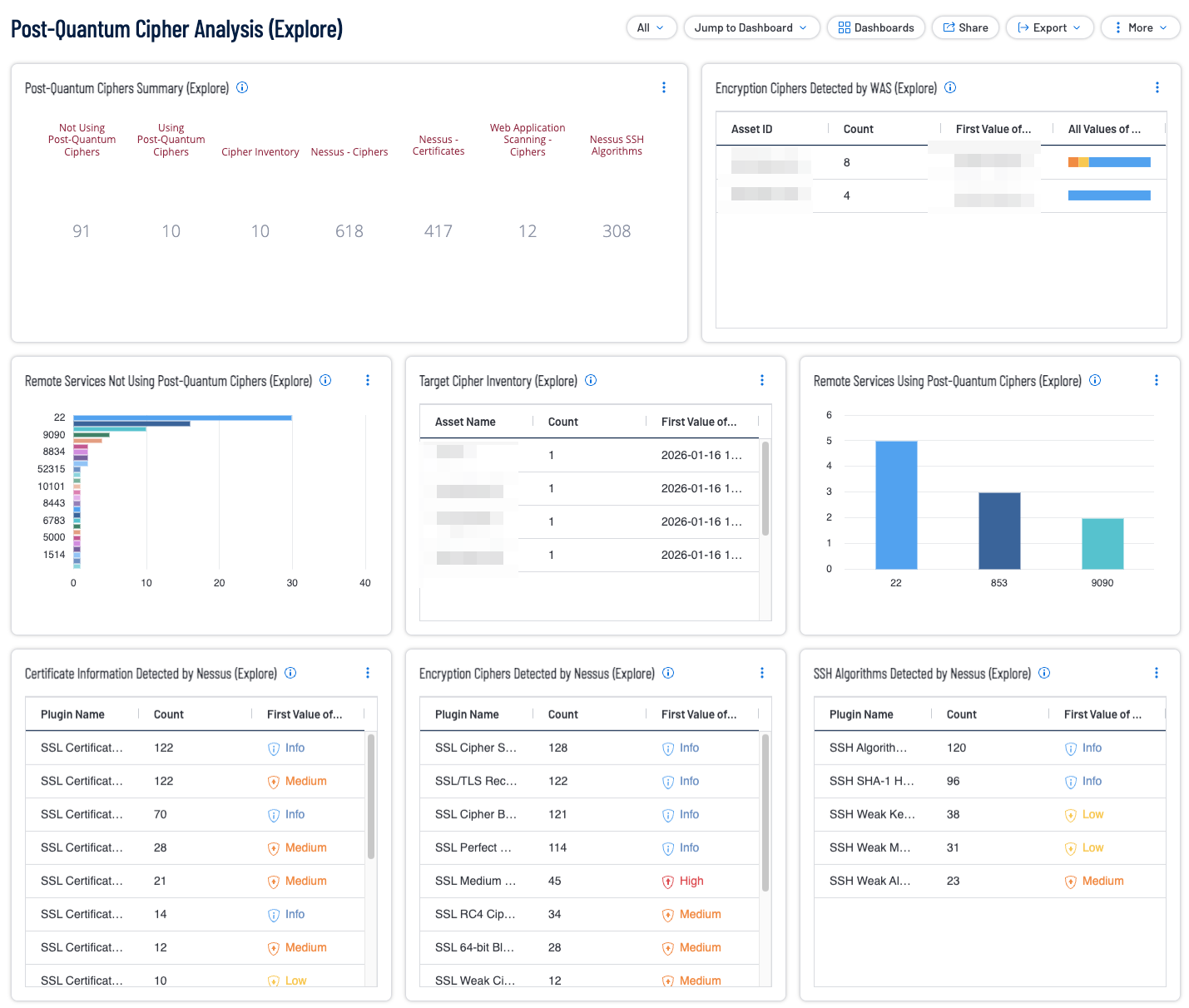
This Dashboard contains the following widgets:
- Post-Quantum Ciphers Summary (Explore) - This widget displays a summary count of Post Quantum Cipher related queries. Each indicator represents a different query, from left to right the queries are; Remote Services Not Using Post-Quantum Ciphers (Plugin ID 277650), Remote Services Using Post-Quantum Ciphers (Plugin ID 277653), Cipher Inventory (277652), Nessus - Cipher (Regex match on plugin name), Nessus - Certificates(Regex match on plugin name), Web Application Scanning - Ciphers (Match on plugin name), Nessus SSH Algorithms (Regex match on plugin name).
- Encryption Ciphers Detected by WAS (Explore)- The following table displays all the SSL/TLS plugins which were detected by WAS. The widget displays this information by using the plugin name filter to look at plugin names containing ‘SSL/TLS’ in the name.
- Remote Services Not Using Post-Quantum Ciphers (Explore) - This Bar Chart utilizes the Remote Services Not Using Post-Quantum Ciphers plugin which reports network services that do not offer post-quantum ciphers. Tenable makes no attempt to determine whether the remote service would be vulnerable to a post-quantum attack.
- Target Cipher Inventory (Explore) - This Table utilizes the Target Cipher Inventory plugin which collects cryptographic ciphers and algorithms discovered during the scan as a machine parsable JSON file attachment. Being grouped by Asset Name, this widget provides a per asset inventory of ciphers and algorithms.
- Remote Services Using Post-Quantum Ciphers (Explore) - This bar chart utilizes the Remote Services Using Post-Quantum Ciphers plugin which reports network services that offer post-quantum ciphers and enumerates the post-quantum ciphers that they offer. Tenable makes no attempt to determine whether the remote service is actually hardened against a post-quantum attack.
- Certificate Information Detected by Nessus (Explore) - The Certificate Information Detected by Nessus widget displays any detected SSL Certificate plugins that were seen by Nessus. The widget utilizes the Plugin Name filter to match on plugin names that contain 'SSL Certificate'.
- Encryption Ciphers Detected by Nessus (Explore) - The Encryption Ciphers Detected by Nessus widget displays any detected Cipher plugins that were seen by Nessus. The widget utilizes the Plugin Name filter with a regex match on ‘(Cipher Suites)|(SSL Ciphers)|(Weak Kerberos)’ this ensures the plugin names displayed show detected Ciphers.
- SSH Algorithms Detected by Nessus (Explore) - The SSH Algorithms Detected by Nessus widget displays any detected SSH algorithm plugin that was seen by Nessus. The widget utilizes the Plugin Name filter with a regex match on 'SSH.*Algorithm' this ensures the plugin names displayed show detected SSH algorithms.