by Cody Dumont
November 2, 2022
The Cyber Exposure discipline provides a structured approach to model and analyze cyber risk to make better business and technology decisions. Risk managers need to have consistent and trackable metrics to calculate the organization's cyber risk. This dashboard provides a centralized view of several key metrics that are help close the Cyber Exposure Gap.
Organizations conduct internal security assessments required by many industry standards and government regulations such as the Payment Card Industry Data Security Standard (PCI DSS), the Critical Security Controls (CSC), and many others. The assessment, must include evidence of the assessment execution and parameters. The Nessus Scan Information plugin (19506) provides a scan summary record of the scan parameters. There are several parameters recorded during the scan, such as use of credentials, safe checks, and many other settings.
Risk managers are encouraged to monitor security advisories from different sources. One such source is the National Vulnerability Database (NVD). The NVD is one of the sources for the Common Vulnerabilities and Exposures (CVE). Where appropriate, Tenable.io associates CVE IDs with plugins, allowing risk managers to use the CVE as a good external resource to identify vulnerabilities. The CVE uses the year the vulnerability was published as part of the CVE ID, enabling managers to use simple search patterns supported within Tenable.io to easily identify new or old vulnerabilities.
Managing risk requires several different strategies. In some cases, the strategy is to accept or recast the risk due to a mitigating control. The risk manager may authorize a risk to be mitigated by some other means, for example network device configuration or some other mitigating factor. Mitigation controls need to have a common and accepted practice to account for these mitigations. Tenable.io supports the ability to maintain a record of vulnerabilities that are recast or accepted.
The risk management team and security operations team collaborate to identify and report on risks as part of the overall vulnerability management plan. Working together, they create robust vulnerability scanning and risk assessment processes aligned with the Cyber Exposure Life Cycle. The metrics provided by Tenable.io and correlated in this dashboard, enables risk managers to monitor and report on vulnerabilities by operating system type. This information also allows the risk manager to monitor the performance of the organization against multiple security standards.
Security leaders need to SEE everything, PREDICT what matters most and ACT to address cyber risk and effectively align cybersecurity initiatives with business objectives. Tenable.io discovers and analyzes assets continuously to provide an accurate and unified view of an organization’s security posture. The requirements for this dashboard are: Tenable.io Vulnerability Management, Tenable Web Application Security (WAS), Tenable.cs.
Widgets
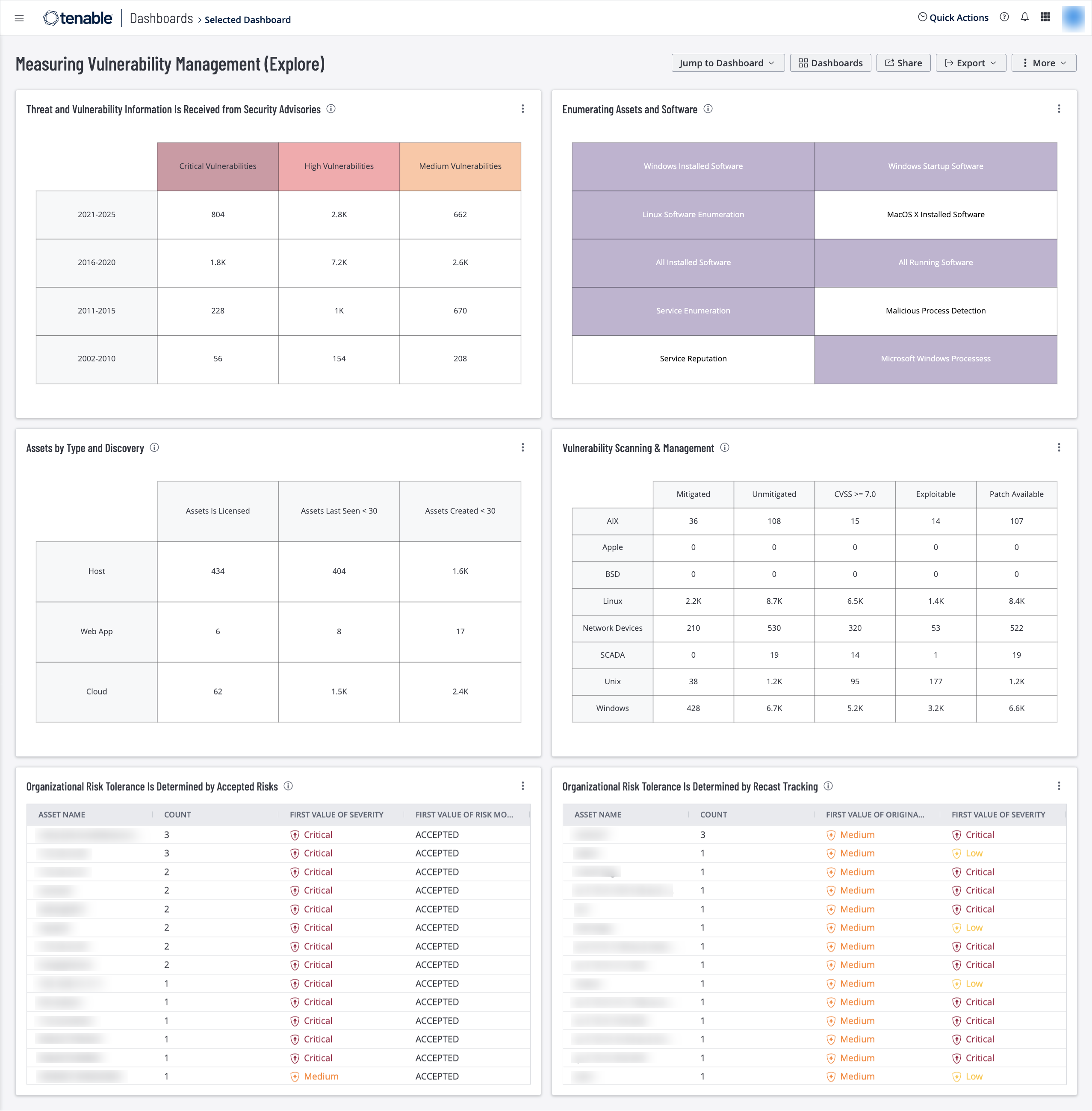
Threat and Vulnerability Information is Received from Security Advisories – This widget provides counts of vulnerabilities by the year the CVE was published and by severity level. CVE IDs have a prefix for the year and can be easily grouped by year. The matrix rows group the vulnerabilities in 5-year ranges according to the year the CVE was released. The columns group the vulnerabilities by severity. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
Enumerating Assets and Software – This widget provides lists of enumerated software assets, running processes and installed software. Tenable.io uses several plugins to extract a complete list of installed software. Additional plugins use key words such as enumeration, installed, reputation, and more to identify software assets located on systems. This data helps risk managers to enumerate assets on the network and evaluate risk appropriately. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
Assets by Type and Discovery – This widget helps track new assets in the environment. The columns display a count of assets that are licensed, how many of those assets have been seen within the past 30 days, and how many were created within the past 30 days. The rows display counts of the types of assets within these categories. Licensed assets are included in the asset count for Tenable.io, which means they are being scanned and managed. This information is useful in tracking software or hardware that has been deployed but is not managed by the IT or security teams of the organization. The requirements for this widget are: Tenable.io Vulnerability Management, Tenable Web Application Security (WAS), Tenable.cs.
Vulnerability Scanning & Management – This widget supports vulnerability scanning and management using plugin families to provide a concise matrix of vulnerability data. Managers and teams can leverage metrics with vulnerability counts to measure progress, beginning with counts of mitigated and unmitigated vulnerabilities. Teams can view the number of vulnerabilities that hold a CVSS score above a threshold of 7.0. In addition, vulnerabilities that are exploitable are presented as a second metric to prioritize mitigation strategies. Tenable recommends prioritizing mitigation of systems with vulnerabilities in this range of CVSS scores as well as vulnerabilities that are found to be exploitable. The last column displays the number of vulnerabilities with patches available for 30 days or more, to enable managers to monitor the patch deployment progress. Tenable.io Vulnerability Management (Nessus, NNM).
Organizational Risk Tolerance is Determined by Accepted Risks – This widget provides a list of vulnerabilities that have been accepted. Accepting risks allows managers to create rules that record vulnerabilities mitigated through some means other than applying the software patch or operating system upgrade. The table provides the host name, severity, and number of accepted vulnerabilities per hosts. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
Organizational Risk Tolerance is Determined by Recast Tracking – This widget provides a list of vulnerabilities that have been recast from one severity level to another. Recasting allows managers to change the severity of a vulnerability based on other mitigating factors that cannot be tracked or tested using Tenable.io. The widget provides the host name, recast severity, original severity, and number of affected recast vulnerabilities present on that host. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).