by Cody Dumont
November 1, 2022
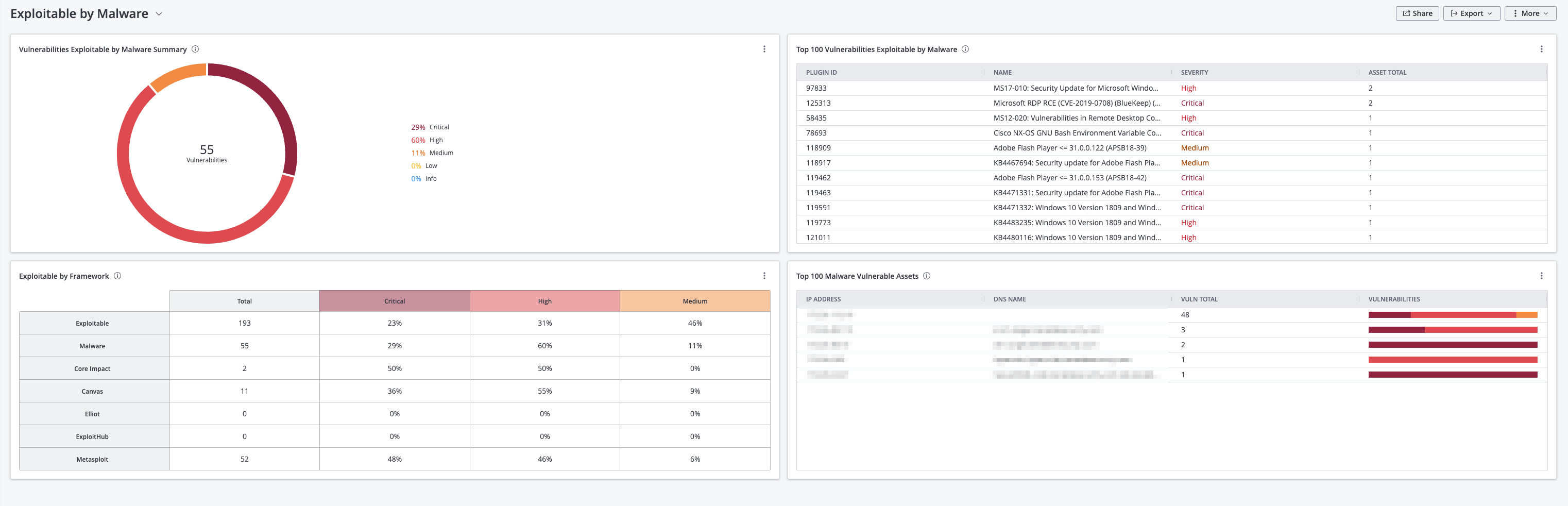
Malware can exploit weaknesses and vulnerabilities to make software or hardware perform actions not originally intended.Tenable.io easily identifies assets most vulnerable to malware and other exploitation frameworks. This dashboard provides the necessary context to understand which assets are vulnerable to malware exploitation.
Vulnerabilities can also be widely exploited shortly after publication as malware authors reverse engineer the fix and develop "1-day exploits" that can be used to attack organizations. Tenable.io easily identifies assets most vulnerable to malware and other exploitation frameworks. This dashboard provides the necessary context to understand which assets are vulnerable to malware exploitation. Organizations can better communicate cyber risk to the business by supplying context and associated metrics.
Organizations can use the dashboard to gain operational awareness of assets on the network with exploitable vulnerabilities. Analysts need to prioritize vulnerability remediation or mitigation, depending on risk. Focusing on vulnerabilities that are actively being exploited by malware helps to reduce the risk to the organization and provides guidance on which vulnerabilities to remediate first. Vulnerabilities can also be exploited through common software applications. Products such as Metasploit, Core Impact, and exploits listed in ExploitHub can be used by anyone to perform attacks against vulnerabilities. Vulnerabilities that can be exploited through these means are highlighted in this dashboard.
Modern ransomware and malware can be initially developed with the assistance of an exploit framework. This dashboard provides some context on exploitability using frameworks such as CANVAS or Core Impact.
Security leaders need to SEE everything, PREDICT what matters most and ACT to address cyber risk and effectively align cybersecurity initiatives with business objectives. Tenable.io discovers and analyzes assets continuously to provide an accurate and unified view of an organization’s security posture. The requirements for this dashboard are: Tenable.io Vulnerability Management (Nessus, NNM).
Widgets
Vulnerabilities Exploitable by Malware Summary – This widget displays a summary of the top vulnerabilities that are exploitable by malware. Tenable recommends prioritizing remediation to reduce the organization's overall attack surface. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
Top 100 Vulnerabilities Exploitable by Malware – This widget presents the top 100 vulnerabilities that have been identified to be exploitable by malware. The table is sorted by the total host column, which counts the total vulnerabilities identified. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
Exploitable by Malware – This widget provides a summary of exploitable vulnerabilities by malware framework. Exploitation frameworks, such as Metasploit, and Canvas, are designed to detect and exploit software and hardware vulnerabilities in target systems. This widget helps security teams discover risks that may require prioritization over other vulnerabilities. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
Top 100 Malware Vulnerable Assets - This widget provides a list of the top 100 assets with vulnerabilities that are known to be exploitable by malware. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).