by Cody Dumont
November 25, 2014
A long-running malware called “Regin” is a backdoor Trojan and is a state-sponsored piece of “espionageware”. Using SecurityCenter Continuous View (CV), customers can detect infections across the network. Regin seems to be a new piece in the class of malware that is being sponsored by states to spy on other states, and may not adversely impact regular computer and Internet users. While some of its functions (such as acting as a proxy for other Regin infected hosts) may impact the machine they are hosted on, this malware is not targeted at the end user.
The dashboard and its components are available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the SecurityCenter Feed under the category Threat Detection & Vulnerability Assessments.
The dashboard requirements are:
- SecurityCenter 4.7
- Nessus 5.2.7
Read more about Regin on the Tenable Blog.
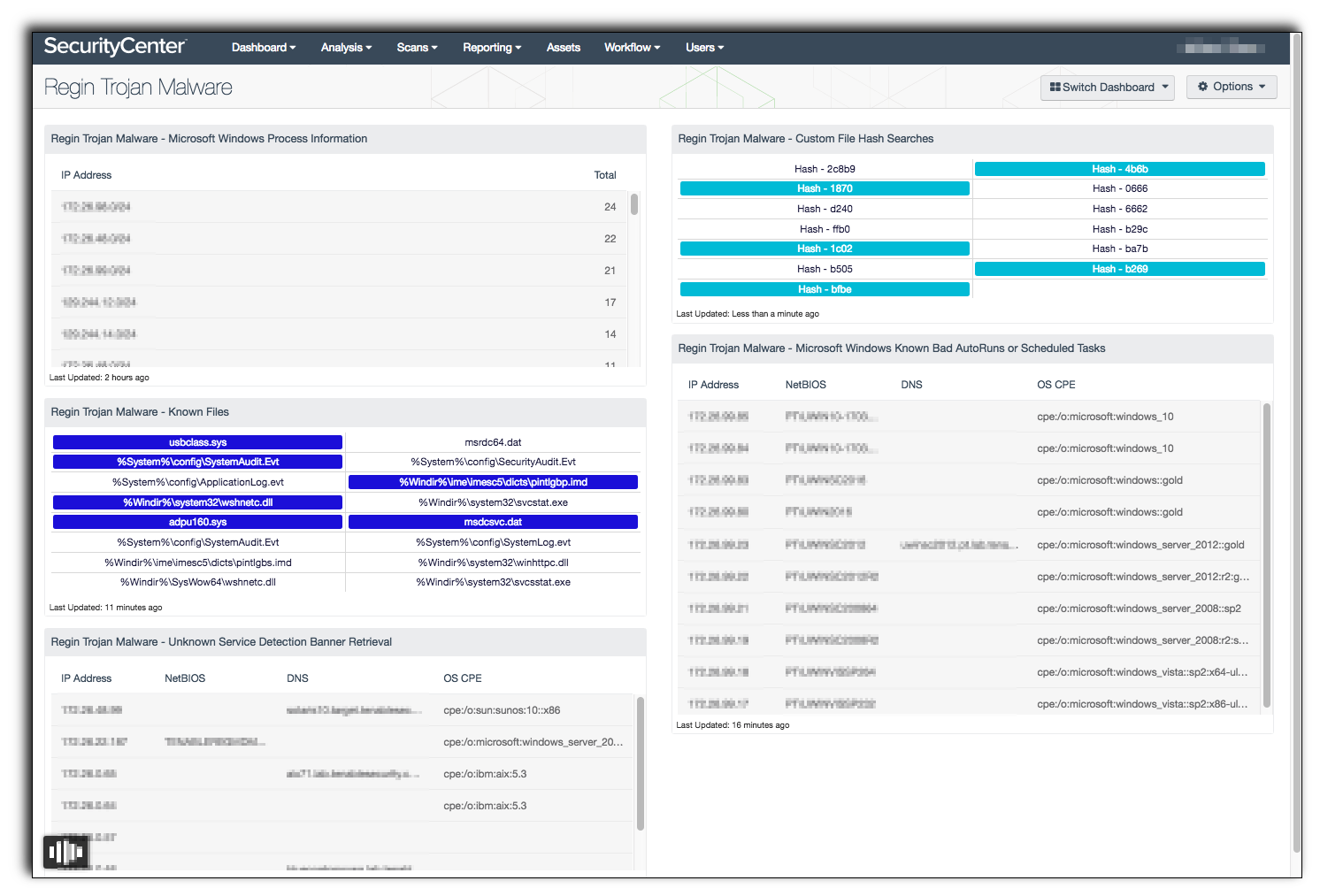
By monitoring the AutoRun settings, the analyst can monitor for known files and known malware with hashes provided by Tenable’s research team. This dashboard is comprised of five components, two of which focus on the Windows Process information. The next two look in the registry for known malware, and the final component identifies unknown services using banner recognition.
SecurityCenter CV allows for the most comprehensive and integrated view of network health. SecurityCenter CV provides a unique combination of detection, reporting and pattern recognition utilizing industry recognized algorithms and models. SecurityCenter CV also enables you to react to advanced threats, zero-day vulnerabilities and new forms of regulatory compliance.
Regin Trojan Malware - Known Files: This component provides indicators of Regin malware discovered in the running processes. This component uses plugin 70329 (Microsoft Windows Process Information). The plugin detects details about the running processes on a Microsoft Windows machine, and can be used for forensic investigation, malware detection, and to that confirm your system processes conform to your system policies. Each indicator looks for known file names associated with Regin and will turn purple when a match is found.
Regin Trojan Malware - Microsoft Windows Process Information: This component provides a list of networks and systems where process information has been collected. The component uses plugin 70329 (Microsoft Windows Process Information). The plugin detects details about the running processes on a Microsoft Windows machine, and can be used for forensic investigation, malware detection, and to that confirm your system processes conform to your system policies. The table provides the subnet based on a 24 bit mask and a total of systems with process information collected.
Regin Trojan Malware - Unknown Service Detection Banner Retrieval: This component uses banner retrieval techniques to list systems with an unknown banner. These systems could be running an unauthorized service or malware. The table uses plugin 11154 (Unknown Service Detection: Banner Retrieval). SecurityCenter CV uses Nessus to identify the service banners. However, for these systems the scanner was unable to identify a service on the remote host even though it returned a banner of some type. The table provides the IP address, hostname, NetBIOS name and the OS CPE.
Regin Trojan Malware - Custom File Hash Searches: This component provides indicators of possible malware using the reputation Microsoft Windows Known Bad AutoRuns / Scheduled Tasks plugin. The first four letters of the hash are displayed as part of the indicator and will turn purple when a match is found. Plugin 74442 (Microsoft Windows Known Bad AutoRuns / Scheduled Tasks) detects processes known to be associated with known malware. This indicates that the system may have been compromised by malware. These indicators are known to be part of the Regin malware.
Regin Trojan Malware - Microsoft Windows Known Bad AutoRuns or Scheduled Tasks: This component provides a table of systems running processes detected using the Microsoft Windows Known Bad AutoRuns / Scheduled Tasks plugin. The table provides the IP address, hostname, NetBIOS name and the OS CPE. Plugin 74442 (Microsoft Windows Known Bad AutoRuns / Scheduled Tasks) detects Windows systems that have one or more registry entries that are known to be associated with known malware. This indicates the system may have been compromised by malware.