by Cody Dumont
January 26, 2021
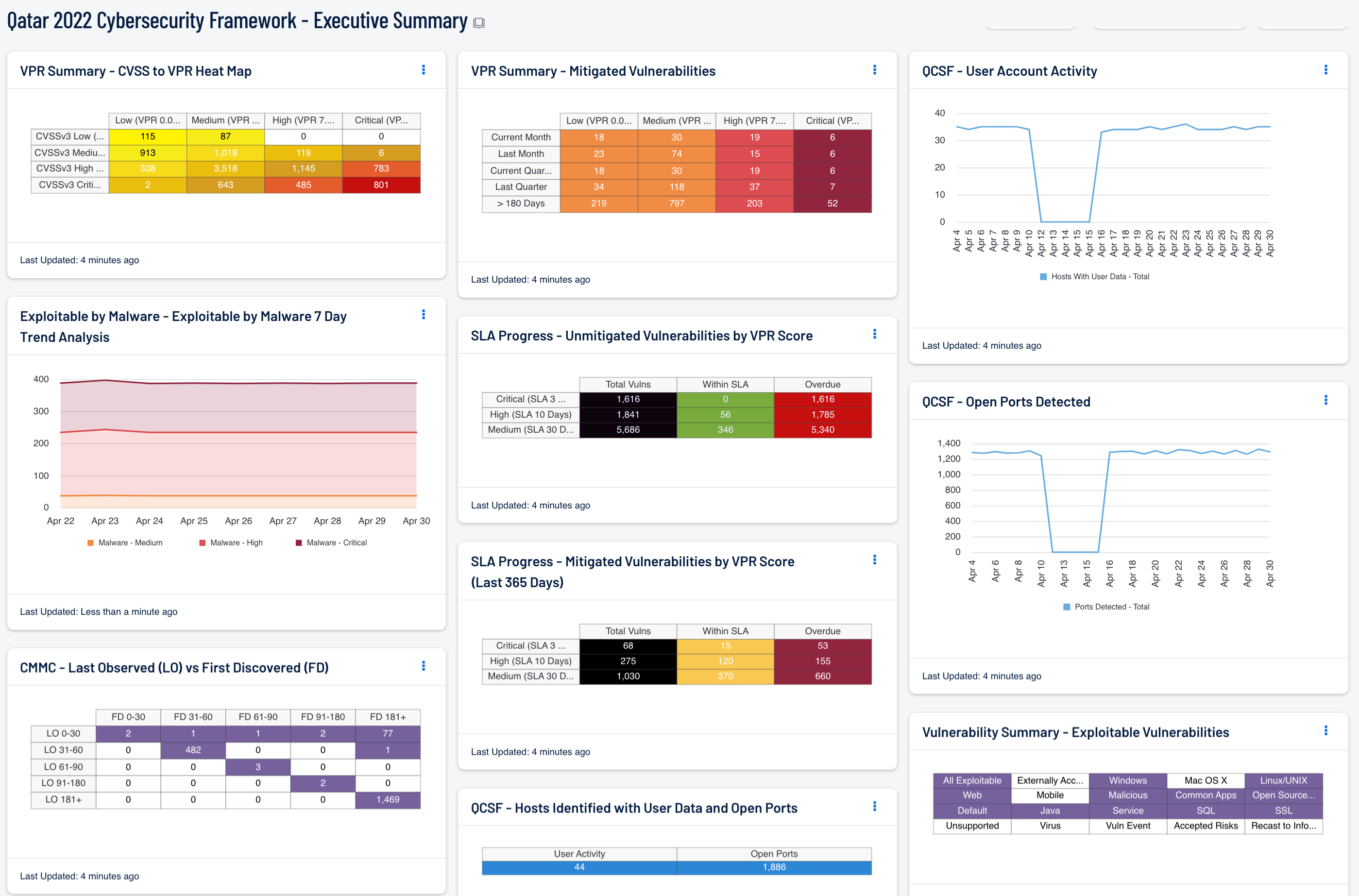
The Qatar 2022 Cybersecurity Framework, The Capability Description – Cybersecurity Governance section (Chapter 2) focuses on overall cybersecurity strategy. Strategic procedures empower effective implementation and compliance for requirements defined by the framework. Therefore, CISOs will be able to ascertain a succinct snapshot of overall risk and their organization’s efforts to mitigate that risk.
The Cybersecurity Governance capability outlines the process by which an entity can assess their risk to create a proper risk management plan. Entities can use this dashboard to gain an understanding of their current risk, and use that data when identifying critical business services, or generating the Business Impact Analysis (BIA). The exploitability related data exists to help entities map critical assets to other mitigation requirements outlined in other sections of the framework.
For entity response needs, user data and port information are tracked for the change in trends over time. CISOs can use this information to understand whether or not there have been any changes to infrastructure, or if user and port activity has spiked during scans. This data can be used to create investigative action items for solving potential malware issues that could be present on an entity’s network.
With the present information, risk can be assessed, management plans can be formed, and possible breaches can be investigated. These tools offer CISOs a decisive way to confidently make decisions regarding the enterprise that they manage. Armed with proper knowledge and tools, CISOs can guarantee that their entity’s needs are fully met.
This dashboard is available in the Security Center Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Security Center Feed under the category Compliance & Configuration Assessments. The dashboard requirements are:
• Security Center 5.15.0
• Nessus 8.11.1
Security Center is the market-defining On-Prem Cyber Exposure Platform. Security Center provides the ability to continuously Assess an organization’s adherence to best practice configuration baselines. Security Center provides customers with a complete Cyber Exposure platform for completing effective cybersecurity practices.
Components
- VPR Summary - CVSS to VPR Heat Map - This component provides a correlation between CVSSv3 scores and VPR scoring for the vulnerabilities present in the organization.
- Exploitable by Malware - Exploitable by Malware 7 Day Trend Analysis - This component shows an additive trend analysis of vulnerabilities that can be exploited by malware.
- CMMC - Last Observed (LO) vs First Discovered (FD) - This component compares First Discovered and Last Observed dates which gives insights into scan health.
- VPR Summary - Mitigated Vulnerabilities - This component provides organizations with a view of vulnerabilities that have been mitigated, showing progress towards risk management SLA’s. The columns are grouped using the VPR score levels, ranging from least risk to the greatest risk. Each row uses the Vulnerability Mitigated filter to track when a risk first appeared on the network.
- SLA Progress - Unmitigated Vulnerabilities by VPR Score - The matrix provides a summary of vulnerabilities based on the VPR score and the SLA of 30, 60, 90 days.
- SLA Progress - Mitigated Vulnerabilities by VPR Score (Last 365 Days) - This matrix provides a summary of the mitigated vulnerabilities discovered over the past 365 days based on VPR score.
- Vulnerability Summary - Exploitable Vulnerabilities - This matrix displays warning indicators for exploitable vulnerabilities actively and passively detected on the network.
- QCSF - User Account Activity - This component shows an additive trend analysis of hosts that have contained some kind of user account data. The data provides a way to identify if new assets have been added to the network, or if new user accounts have appeared across devices that did not previously have any.
- QCSF - Open Ports Detected - This component shows an additive trend analysis of hosts that have contained some kind of open port data. The data provides a way to identify if new assets have been added to the network, or if new open ports have appeared across devices that did not previously have any.
- QCSF - Hosts Identified with User Data and Open Ports - This matrix displays hosts that have either had some form of user account data, or open ports detected in scans. By clicking on an individual cell in the matrix, a list of those hosts will be displayed for more detailed analysis. Hosts that have previously had account and port data will also be available, and additional information can be gleaned from the plugin output of the various detection plugins.