by Josef Weiss
June 1, 2021
A significant benefit of an effective cybersecurity program is that organizations will improve business continuity and confidence when dealing with security threats. Steps to building such a program include following information security best practices and maintaining a high level of awareness. Key program elements include identifying and mapping assets, leveraging threat intelligence, and remediating critical risks. These are the building blocks of a solid cyber security program and the foundation of Cyber Exposure Management.
Organizations are under attack and security breaches are constantly making headlines. In today’s rapidly evolving technology landscape, new cyber risks emerge daily. Security operations teams must be able to detect these new risks and receive alerts when threats create new security vulnerabilities in their network.
Operations teams are typically responsible for not only monitoring the organization’s infrastructure, but also for patching and remediating risk. An organization’s operations team requires vulnerability details which easily identify the most significant vulnerabilities and provides guidance towards mitigation. The ability to act quickly in mitigating vulnerabilities requires information to be presented in a manner which focuses on findings that pose the greatest risk and should be prioritized and mitigated first. As a result, vulnerability remediation is more successful, the attack surface is reduced, and efforts can be visually tracked and measured against established goals to report to various stakeholders.
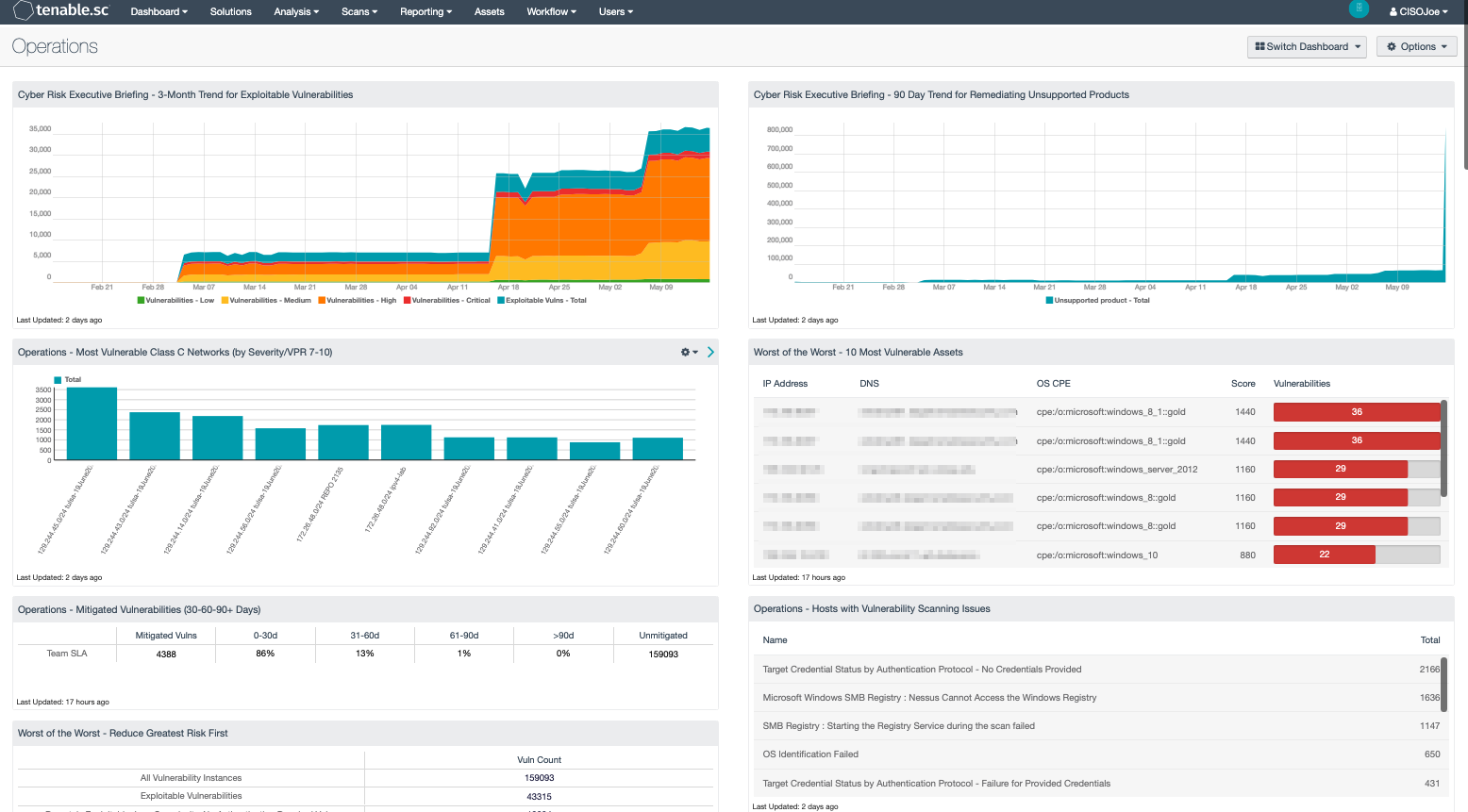
Tenable.sc provides a risk-based view of your IT, security and compliance posture, allowing operations teams to analyze findings, remediate identified risk, track progress, and measure success. Designed with the principles of the Cyber Exposure Lifecycle in mind, this dashboard assists operations teams in maintaining a high level of awareness and security vigilance. The dashboard is tailored to guide the operations team in detecting, predicting, and acting to reduce risk across their entire attack surface. Components not only include detailed vulnerability findings, but also provide guidance on remediation actions that will reduce the greatest risk first. Utilizing Tenable’s Predictive Prioritization technology of combining vulnerability data, threat intelligence and data science, this dashboard directly benefits operations teams in determining where to start when navigating a sea of vulnerabilities.
Organizations often have teams within operations groups that focus on information, relevant to the groups own assets; or area of operational focus, such as Windows, Linux, databases, or network infrastructure. The dashboard components do not require specific asset list filters to be applied prior to use. However, organizations that have teams that do focus on a specific group of assets will benefit from using custom asset lists. Operations teams can visualize findings against assets that are “owned by” or “assigned to” specific teams within the organization using this method. Additionally, setting an Output Assets filter provides greater insight into where additional resource need to be allocated to mitigate vulnerabilities.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessments.
The dashboard requirements are:
- Tenable.sc 5.18.0
- Nessus 8.14.0
Components
This dashboard contains a number of components that provide Operations teams with vulnerabilities that present the greatest risk, track VPR, mitigation efforts, CVE vulnerabilities, missing patches, host/application counts and more, across 36 components. This extensive collection provides a single resource or One-Stop-Shop for Operations teams to uncover risk and reduce the attack surface.