by Ben Smith
March 31, 2020
The United Arab Emirates’ (UAE) National Electronic Security Authority (NESA) Information Assurance Standards state that an organization should appropriately secure communications. Secure communications are required by the NESA standard. Tenable.sc includes many indicators about encryption used. This dashboard allows a risk manager to easily understand the organization’s use of encryption for communications and areas where data leakage may occur.
The Analyze phase of the Cyber Exposure lifecycle requires understanding exposures in context, prioritizing remediation based on asset criticality, threat context and vulnerability severity. In order to understand asset criticality, threat context, and vulnerability severity, an organization needs to understand the security of communications on their network.
The most prevalent types of network communication encryption are SSL/TLS and SSH. Data transferred internally, externally, and used for online transactions needs to be protected in transit from exposure to unauthorized third parties. Understanding where good encryption is used, and where good encryption isn’t is imperative to Cyber Exposure and to NESA. Tenable.sc can identify plugins that indicate the usage of SSL/TLS and SSH. Tenable.sc also shows common cryptographic compliance concerns that help identify areas of exposure.
While an organization may use encryption extensively, the organization should also identify areas where encryption is weakened. Tenable.sc identifies SSL/TLS vulnerabilities and common cryptographic compliance concerns so the risk manager can identify where to focus remediation efforts. NESA requires the risk manager to locate sensitive systems and ensure they use a high level of encryption. This is essential to maintaining the confidentiality, authenticity or integrity of information processed by these systems. Reference NESA controls M5.2.6, T1.2.4, T4.1, T4.2, T4.3.2, T7.1, T7.4, T7.4.1, T7.4.2, and T7.6.4.
Beyond using strong encryption, another key to communications security is Data Leakage / Data Loss Prevention (DLP). DLP products help identify when sensitive data inadvertently or maliciously crosses trust boundaries. Sensitive information can include trade secrets, cryptographic keys, network architecture, and Personally Identifiable Information (PII), like credit card or social security numbers. Tenable.sc can utilize name filters for various plugins to identify areas of DLP concern. This dashboard utilizes these plugin name filters but organizations with Log Correlation Engine (LCE) or Nessus Network Manager (NNM) deployments can also add many components utilizing that data for DLP. These components can be found by searching for the prefixes “Data Access and Integrity,” and “Data Leakage Monitoring.” NESA controls T4.2 and T7.6.4 are specific to DLP.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment.
The dashboard requirements are:
- Tenable.sc 5.12.0
- Nessus 8.9.0
- Compliance Data
Tenable.sc Continuous View (CV) is the market-defining On-Prem Cyber Exposure Platform. Tenable.sc CV provides the ability to continuously Assess an organization’s adherence to best practice configuration baselines. Tenable.sc provides customers with a full and complete Cyber Exposure platform for completing an effective Cyber Hygiene program prescribed by NESA standard.
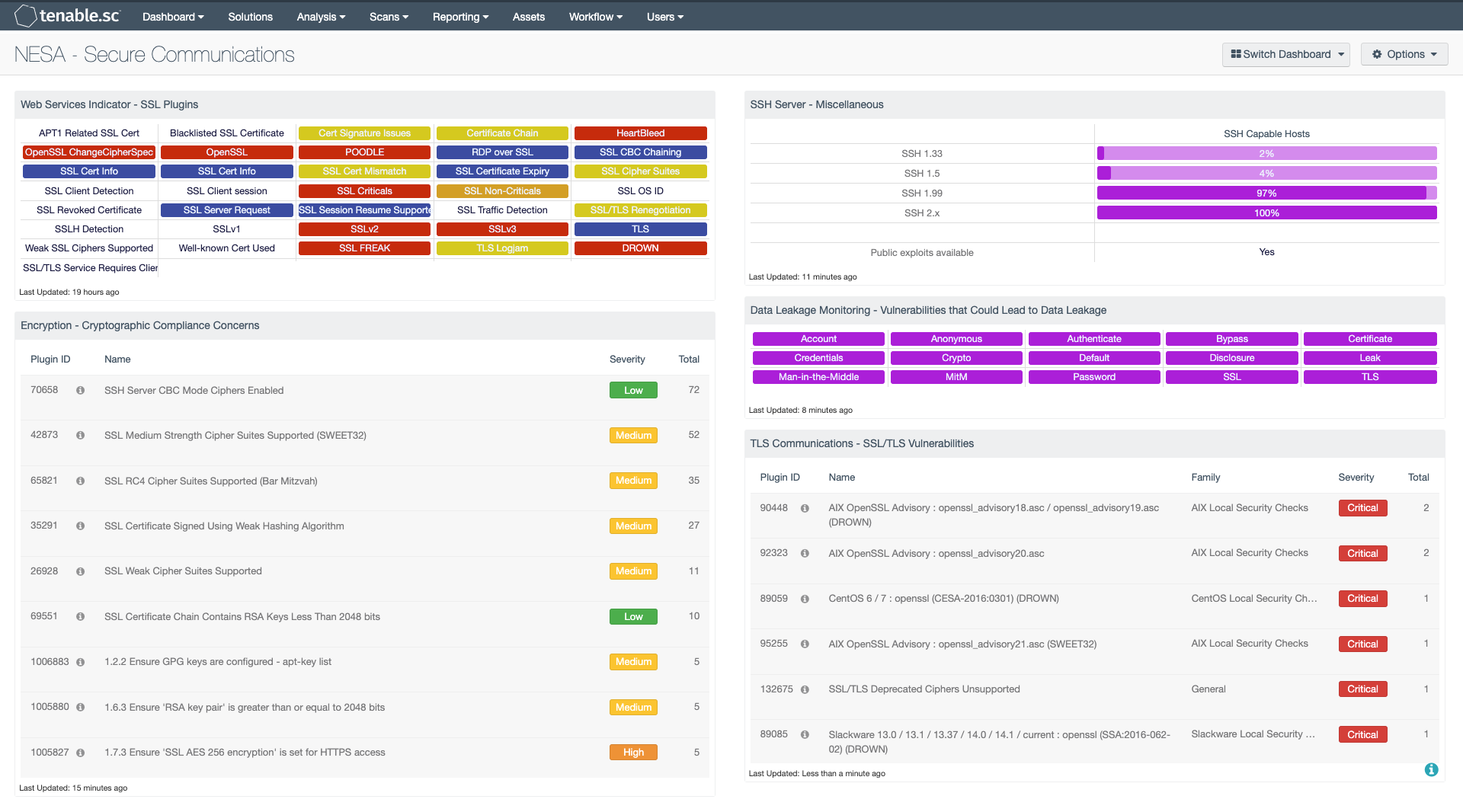
Web Services Indicator - SSL Plugins: All the plugins that refer to SSL or certificates have been grouped into these indicators. An indicator will not be highlighted if no matches are found; however, if a match is found, the color will change. If all the plugins applied to the indicator have a severity of info or low, then the indicator will turn blue. If any of the selected plugins are medium, high, or critical, the color of the indicator will change to yellow, orange, or red accordingly. However, if there is a mix of info, low, medium, and high, the indicator will be purple. Indicators with a critical severity plugin will always be red.
Encryption - Cryptographic Compliance Concerns: This table presents a summary of both compliance concerns and vulnerabilities associated with encryption and cryptographic issues. Information presented in this component can highlight issues such as weak hashing algorithms and keys as well as the use of insecure encryption ciphers, including SSLv2, SSLv3, and TLSv1.0.
Data is sorted by the highest number of compliance and vulnerability concerns at the top, which can assist in prioritizing remediation efforts. Many of these issues are the result of misconfigurations or use of outdated encryption methods. This component also includes vulnerabilities that can be exploited by attackers. Security teams should review the data to determine the risks to the organization.
SSH Server - Miscellaneous: This matrix component displays the count of different versions of SSH server software detected within the organization. Nessus plugin 10881 is used to detect the SSH versions in the organization. The SSH protocol versions detected with this plugin are 1.33, 1.5, 1.99 and 2.0 (including future 2.x versions). The numbers represented in the matrix are in ratio format of the version detected to the total number of SSH versions detected. SSH versions that were detected and have exploits available are also indicated in the matrix component.
Data Leakage Monitoring - Vulnerabilities that Could Lead to Data Leakage: This component presents indicators by keyword for actively and passively detected vulnerabilities that could lead to data leakage. Vulnerabilities at all severity levels except Informational are included. The keywords cover disclosures, cryptographic issues, man-in-the-middle vulnerabilities, and weak authentication concerns. A purple indicator means that one or more vulnerabilities contain the keyword. Clicking on the indicator will bring up the analysis screen to display details on the vulnerabilities. In the analysis screen, setting the tool to IP Summary will display the systems on which the vulnerabilities are present. This component can be used to investigate vulnerabilities that could lead to data leakage.
TLS Communications - SSL/TLS Vulnerabilities: The SSL/TLS Vulnerabilities component displays a list of SSL and TLS-based vulnerabilities on the network. The table is filtered by SSL and TLS-based plugin names, and is sorted by severity. Both Nessus and NNM will scan systems that are vulnerable to DROWN, POODLE, Logjam, and Heartbleed attacks that exploit weaknesses in older SSL versions. This will allow for both analysts and security teams to identify web applications and enterprise software with SSL/TLS vulnerabilities, expired certificates, self-signed certificates, and more.