by Stephanie Dunn
February 26, 2016
Most organizations today utilize removable devices for convenience and productivity, however many may not be controlling portable device use or even be aware of what devices are being used. Any type of relaxed, insecure, or nonexistent security policies that an organization has will increase the potential for data leakage, along with the number of threats and attacks against a network. This dashboard will assist organizations in monitoring and tracking the usage of Windows based removable devices, removable device history, and perform audit checks on removable media.
The Cybersecurity Framework (CSF) provides guidance based on existing standards, guidelines, and practices that can be tailored to specific organizational needs. The Protect function is divided into multiple subcategories that address specific security requirements with Access Control, Awareness, Data Security, Policies and Procedures, Maintenance, and Technology Protection. The Protective Technology category (PR.PT) states that technical security solutions are managed to ensure the security and resilience of systems and assets, consistent with related policies, procedures, and agreements. This dashboard focuses on the PR.PT-2 subcategory, which states that removable media is protected, and its use is restricted according to a specified policy.
Removable media and portable devices are one of the biggest threats an organization can have. Many devices are plugged into a host without being monitored or scanned properly by an organization, which can introduce malware and infect other hosts. Any type of attack or data leakage can start with just one device. Malicious and negligent acts among internal employees can allow sensitive data to be exposed through data leakage, lost devices, and social engineering practices. Data theft is not limited to just internal employees. Outsiders such as contractors, temporary employees, and building staff could potentially gain access to network resources by plugging in a portable device to a networked computer. This can allow unauthorized users to access and copy classified or restricted data, and can disrupt network resources. By using this dashboard, organizations can monitor the effectiveness of security policies, keep track of authorized and unauthorized devices, and can reduce gaps within current security measures.
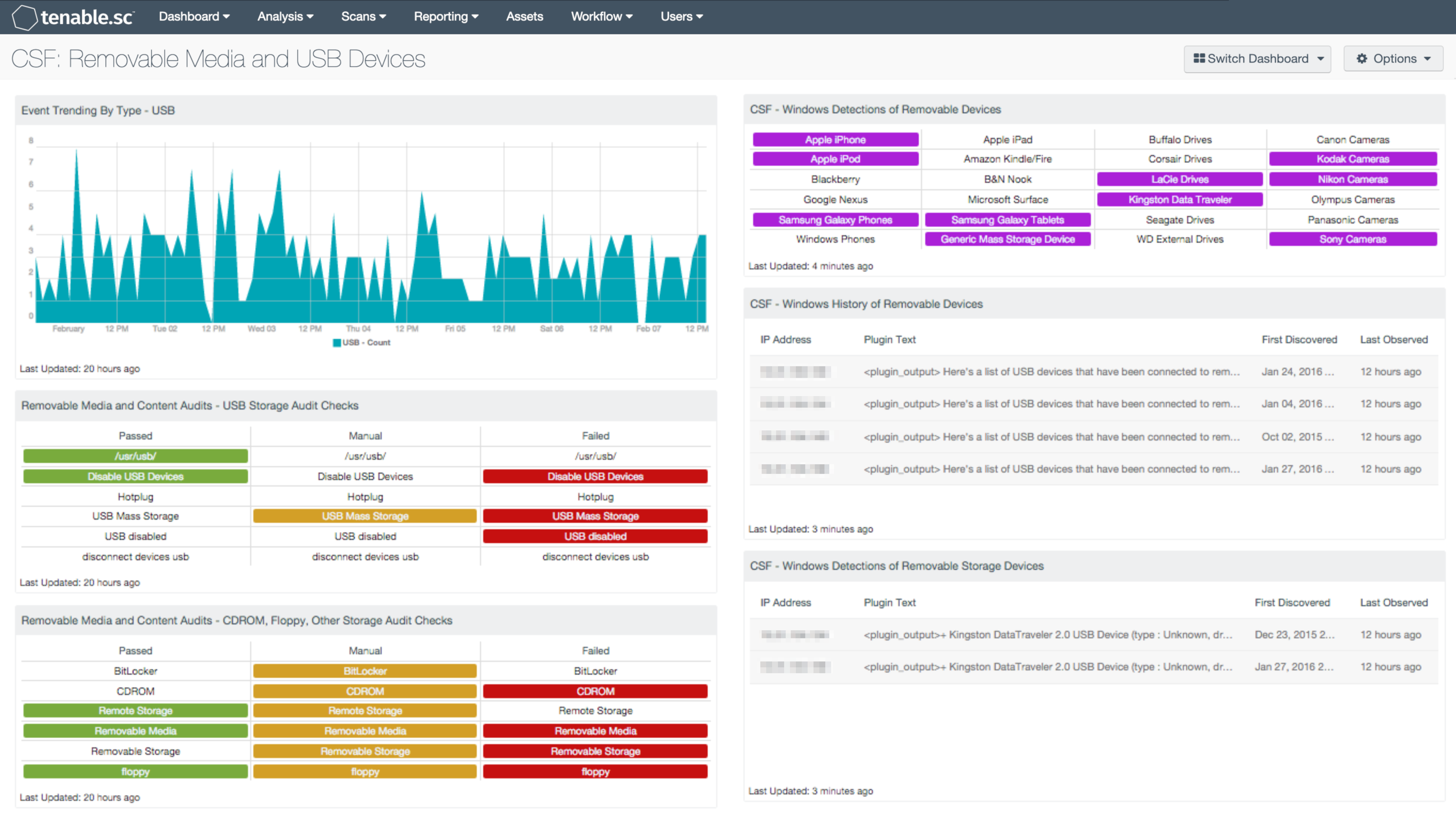
This dashboard focuses on identifying and tracking the use of removable media and USB devices. The Windows registry provides valuable information on connected and previously connected USB devices. Several components within this dashboard utilize plugins that will detect the device type, vendor, and when the device was first connected. Along with USB's, external drives, mobile phones, tablets, and digital cameras all have the ability to store data. Detected devices from some of the top vendors and devices types are presented, and can be modified to fit organizational needs. Analysts are also alerted to audit checks on removable devices and media, which include CD-ROM’s, floppies, and USB Devices. Lastly, a trend chart that will detect any USB removals or insertions into Windows hosts over the past seven days is included.
The audit checks for removable media can be performed with several audit files. Listed below are some examples of files supporting CD-ROM and USB checks. The organization should review the audit files and create a specific audit file that applies directly its policies.
- financial_microsoft_windows_os_audit_guideline_v2.audit
- USGCB_Win7_Desktops_v2_official.audit
- PCI_2.0_Redhat.audit
- VMware_vSphere_5.x_Hardening_Guide.audit
Monitoring the use of removable devices alone won’t completely reduce the risk of data loss, threats, or attacks against a network. Incorporating additional security solutions for monitoring removable devices is not only best practice, but also recommended to protect against the continuously evolving threat landscape. Implementing additional security solutions such as device blocking policies, whitelists for approved devices, and encrypting removable devices are recommended. This will provide additional layers of enforcement and protection across all network endpoints. Together, organizations can gain complete visibility and control of removable devices, and ensure that sensitive data remains secure.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 5.2.0
- Nessus 8.5.0
- LCE 6.0.0
- Content Audit Files
- Audit Files with Checks for USB, CDROM, and other types of media
Monitoring portable devices should also include file integrity checks to determine if data was added, modified, or deleted. In addition, Cloud storage accounts should also be monitored to control internal data usage, as most are personal cloud storage accounts. Tenable has two dashboards that can assist with monitoring internal data usage. The File Integrity Monitoring dashboard will allow the analyst to readily identify data changes on a network. The Cloud Services dashboard will monitor for cloud activity among internal users.
Tenable.sc Continuous View (CV) provides continuous network monitoring, vulnerability identification, risk reduction, and compliance monitoring. Nessus is continuously updated with information about advanced threats and zero-day vulnerabilities and new types of regulatory compliance configuration audits. LCE correlates real-time events on USB usage. Tenable.sc CV allows for the most comprehensive and integrated view of network health.
The following components are included in this dashboard:
- Event Trending By Type - USB: This component displays a 7-day trend analysis of USB events. The LCE Windows Client can detect USB and CD-ROM insertions and removals. The logs generated by these events are normalized to the USB event type.
- Removable Media and Content Audits - USB Storage Audit Checks: This component focuses on compliance data, filtering on several strings containing 'USB' in the plugin name. When an audit file is imported into Tenable.sc, the 'description' line for the check becomes the plugin name. The description for each check provides a descriptive statement of the audit check. There are several audit files that contain checks for USB storage devices; the most common strings were compiled and used in this component.
- Removable Media and Content Audits - CDROM, Floppy, Other Storage Audit Checks: This component focuses on compliance data, filtering on strings containing CDROM, floppy, and other removable storage devices in the plugin name. When an audit file is imported into Tenable.sc the 'description' line for the check becomes the plugin name. The description for each check provides a descriptive statement of the audit check. There are several audit files that contain checks for CDROM, floppy, and other removable storage devices; the most common strings were compiled and used in this component.
- CSF - Windows Detections of Removable Devices: This component presents a matrix of Windows detections of removable storage devices. The matrix utilizes the Windows Portable Devices plugin, which detects portable devices based on their Vendor ID, Device ID, or by Windows registry string. Some of the more popular portable devices are displayed within this matrix, however the analyst can modify this list as needed. An indicator will turn purple when a specific portable device has been detected. The analyst can click on the indicator, and drill down to obtain additional information on hosts that the removable device has been detected on.
- CSF - Windows History of Removable Devices: This table presents a list of detected USB devices that have been connected to a Windows host at least once in the past. This component can provide a point of origin for unauthorized devices, malware infections, and possible data leakage events. Information on IP Addresses, vendor, device type, and drive letter are all included. Additional details such as when the device was first discovered and last observed are also presented. The data provided within this component can assist organizations with discovering and tracking data leakage, and can aid in refining security policies.
- CSF - Windows Detections of Removable Storage Devices: This component presents a list of connected removable devices on Windows hosts. Information such as IP Addresses, vendor, device type, and drive letter are all included within this table. Additional details such as when the device was first discovered and last observed are also presented. The analyst can utilize this information in detecting unauthorized devices on a network.