by Cesar Navas
December 26, 2019
System integrity is a key to maintaining a healthy network. An integral part any security program is maintaining anti-malware controls, and understanding the risk to network should malware be encountered. This dashboard provides summary status on anti-malware efforts and risk exposed to malware.
The CIS ControlsTM are a prioritized set of actions that collectively form a defense-in-depth set of best practices that mitigate the most common attacks against systems and networks. These controls were developed by IT professionals using operational experiences and generally accepted best practices; this dashboard will focus on Control 8 CIS v7.1 (Malware Defenses).
Historically CIS has referred the first six CIS controls as cyber hygiene to focus an organization’s cybersecurity activities. The designation of cyber hygiene brought up the fact that these practices may be difficult for organizations with resource and/or expertise limitations. To address any resource or expertise limitation, CIS now recommends following Implementation Groups (IG) to help prioritize CIS control utilization. There are three IG’s, which describe organization by size. The IG specifies a subset of the controls that have been assessed to have a similar risk profile and resources to implement. The IG’s are also meant to be prioritized in IG order regardless of the IG organization size; for example, organizations should implement Sub-Controls in IG1, followed by IG2 and then IG3. The IG’s are described as organizations with limited resources and cybersecurity expertise (IG1); Organizations with moderate resources (IG2); Organizations with significant resources (IG3).
Control 8 requires the installation and maintenance of the Anti-malware systems, also the prevention of malware proliferation. Organizations need to have controls in place to block malicious application activity, Tenable.sc has the ability to detect the installation and status of anti-virus programs. In addition, Tenable.sc is able to track the vulnerabilities that are exploitable by malware and other exploit frameworks.
There are 3 sub controls that apply to all three IG’s. The sub controls describe enforcing anti-virus (AV) deployments, disabling Auto Run, and automating AV scans. Tenable.sc displays in this dashboard all systems with Auto Run settings enabled, the AV status, and many other parameters described throughout all sub controls. Using Tenable.sc customers from all IG’s can effectively track and report on sub controls 8.1, 8.2, and 8.5. Sub Control 9.4 requires organizations to enable host-based firewalls or port-filtering tools on end systems. This dashboard displays systems with host based firewalls configured, and enumerates the firewall rules for further analysis.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Executive.
The dashboard requirements are:
- Tenable.sc 5.12.0
- Nessus 8.8.0
Tenable.sc Continuous View (CV) is the market-defining On-Prem Cyber Exposure Platform. Tenable.sc CV provide the ability to Analyze assets for anti-malware and common exploitable vulnerabilities and misconfigurations. Tenable.sc provides customers with a full and complete Cyber Exposure platform for completing an effective Cyber Hygiene program prescribed by CIS Controls framework.
This dashboard contains the following components:
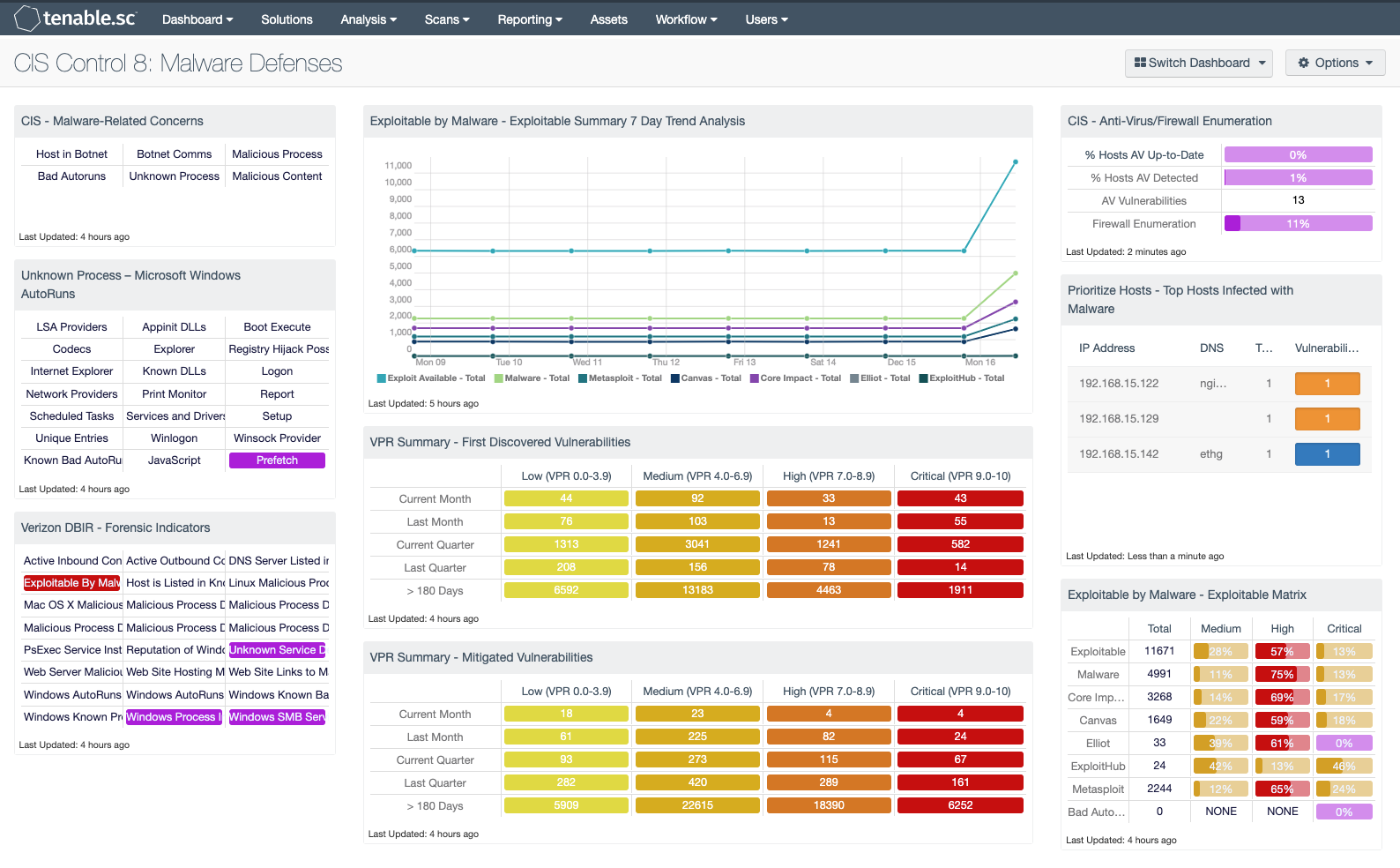
CIS - Malware-Related Concerns: This matrix displays warning indicators for potential malware-related vulnerabilities that are detected, such as botnet interactions, malicious processes and web content, and bad Windows autoruns. Clicking on a highlighted indicator will bring up the analysis screen to display more details and allow further investigation. In the analysis screen, setting the tool to IP Summary will display the systems on which the detections and events occurred. For vulnerability detections, setting the tool to Vulnerability Details will display the full details for each vulnerability, including a description, the solution to fix the vulnerability, and in some cases, links to more information.
Unknown Process – Microsoft Windows AutoRuns: This component presents 21 indicators that will alert on a variety of Windows AutoRun and startup service issues detected on the network. Corrupted or unauthorized startup services can be an indication of compromise. Windows Prefetch data can be useful information during a forensics investigation to allow an analysis of software usage on a host. AutoRun is a feature is found on Windows systems that will allow mounted portable devices such as USBs, CDs, and DVDs to launch programs automatically without user intervention. Disabling AutoRun is best practice as leaving this feature enabled can allow for malware and other malicious programs to infiltrate the network. Indicators will turn purple when a system has detected activity on a host.
Verizon DBIR - Forensic Indicators: This component provides several indicators useful during a forensic investigation. Identifying threat information sources such as bot-net activity, forensic artifacts such as AutoRun settings, schedulers, and malicious processes provides the analyst with key methods to identify IOCs. There are other indicators that monitor AutoRun settings, exploitable by malware, PSExec, and several other indicators mentioned in the Verizon 2015 DBIR and the Mandiant M-Trends 2015 report. Many of the indicators will turn purple when a match is found, indicating a match but not a severity. Other indicators will turn red, which indicates a critical severity.
Exploitable by Malware - Exploitable Summary 7 Day Trend Analysis: This component displays a detailed trend analysis for exploitable vulnerabilities, by exploit framework. Each trend line shows the vulnerability for the respective exploit framework. The trend analysis provides data points every 24 hours over the past 7 days, showing an additive count of vulnerabilities.
VPR Summary - First Discovered Vulnerabilities: This component provides organizations with a view of vulnerabilities over a period of time. The columns are grouped using the VPR score levels, ranging from least risk to the greatest risk. Each row uses the Vulnerability First discovered filter to track when a risk first appeared on the network. The rows progress from the current month, last month, current quarter, last quarter, to vulnerabilities first discovered over 180 days ago. Most SLA’s allow for the vulnerability to exist on the network for 30 days, due to a standard 30-day patch cycle. Organizations can modify this matrix to support the SLA as defined by their risk management officer.
VPR Summary - Mitigated Vulnerabilities: This component provides organizations with a view of vulnerabilities that have been mitigated, showing progress towards risk management SLA’s. The columns are grouped using the VPR score levels, ranging from least risk to the greatest risk. Each row uses the Vulnerability Mitigated filter to track when a risk first appeared on the network. The rows progress from the current month, last month, current quarter, last quarter, to vulnerabilities first discovered over 180 days ago. Most SLA’s allow for the vulnerability to exist on the network for 30 days, due to a standard patch cycle. Organizations can modify this matrix to support the SLA as defined by their risk management officer.
CIS - Anti-Virus/Firewall Enumeration: This matrix assists the organization in monitoring anti-virus (AV) solutions and firewall settings. The "% Hosts AV Up-to-Date" column displays the percentage of total systems that have AV installed and are working properly; the "% Hosts AV Detected" column displays the percentage of total systems on which AV has been detected, whether or not the AV is working properly. The "AV Vulnerabilities" column displays the number of detected vulnerabilities related to AV. The Firewall Enumeration provides all the devices where the host based firewall rules have been collected. Clicking on a highlighted indicator will bring up the analysis screen to display details on the detections for further investigation.
Prioritize Hosts - Top Hosts Infected with Malware: This table displays the top hosts on the network that have actively or passively detected malware infections. The list is sorted so that the host with the worst malware problem is at the top. A count of malware detections and a bar graph indicating the severity of the malware are given for each host. Use this table to determine the hosts with the biggest malware problems on the network.
Exploitable by Malware - Exploitable Matrix: This component is an indicator matrix of exploitable vulnerabilities. There are 4 columns showing the total exploitable vulnerabilities, followed by columns for severity levels. The rows are organized by exploit framework, including the tag 'Exploitable by Malware'.