Tenable.io is a great package that takes the powerful Nessus scanner and adds a web-based front end to it that provides a wealth of information about your vulnerabilities and assets. Having full access to the data in a dashboard makes searching it easy. Roles within ...
Tenable
Vulnerability Management
Expose and close your cyber weaknesses with the market-leading vulnerability management solution
The solution that created the category continues to raise the bar to protect enterprises from critical cyber exposures that increase business risk.

The world’s #1 vulnerability management solution
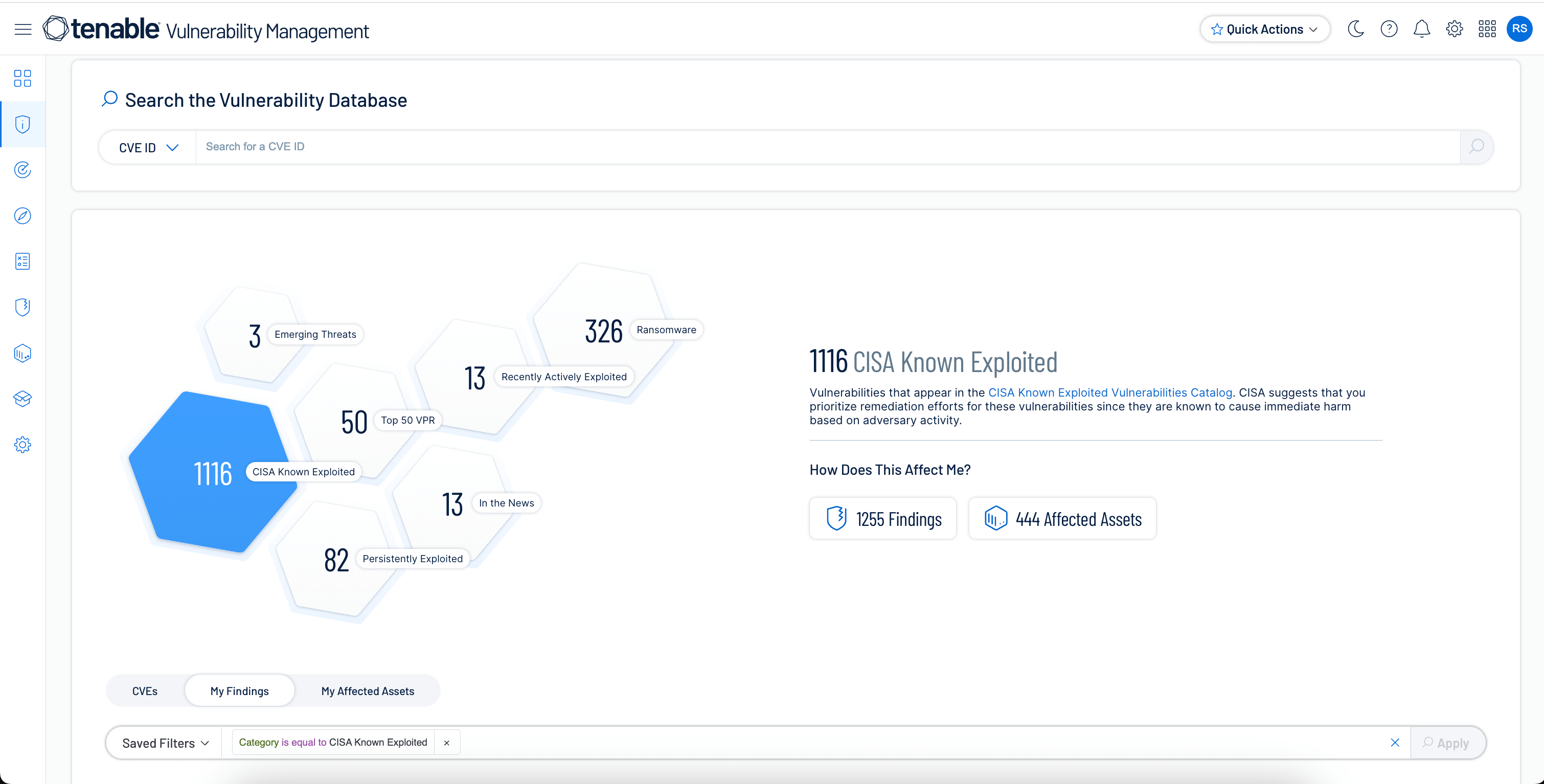
Know your vulnerabilities
Get full visibility into all your vulnerabilities with continuous asset scanning and automated risk prioritization capabilities.
Expose priority gaps
Quickly find highly exploitable, business-impacting exposures using risk-based threat intelligence and critical asset identification.
Close critical exposures
Take rapid, decisive actions to address high-risk vulnerabilities with guided best-practice remediation steps.
Know, expose and close your critical vulnerabilities
See everything
Find hidden vulnerabilities with continuous, always-on asset discovery and assessment of known and unknown assets in your environment, even highly dynamic cloud or remote workforce assets and cyber-physical systems (OT/IoT).
Take a self-guided tourThis self-guided demo showcases key functionality that enables our customers to know, expose, and close critical vulnerabilities.
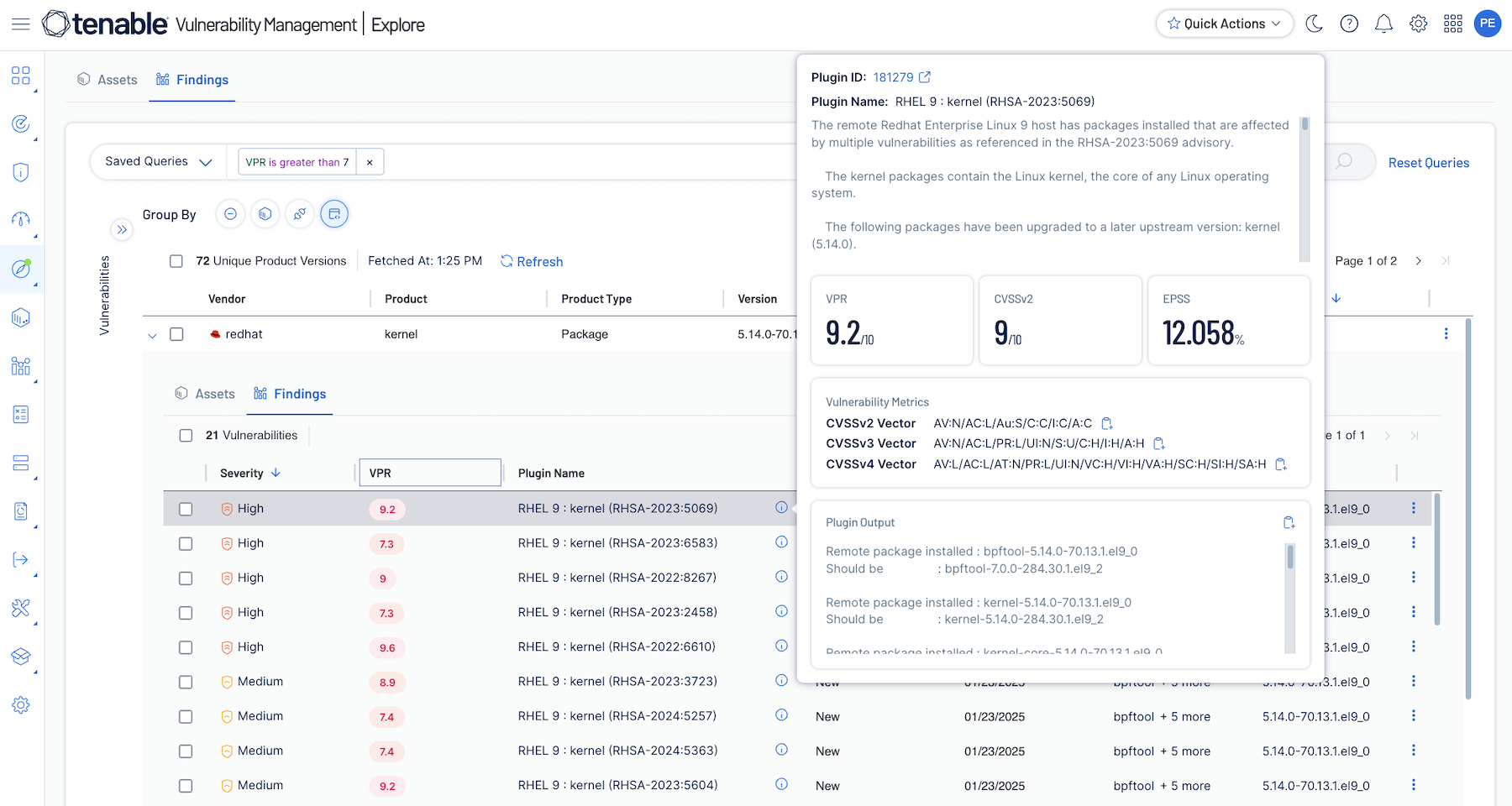
Proactively contextualize threats
Search, contextualize and respond to vulnerabilities based on the industry’s richest sources of data and intelligence provided by Tenable Research.
See howPrioritize vulnerabilities
Sharpen precision and focus on risks that pose the greatest threat with Tenable’s Vulnerability Priority Rating (VPR). Powered by generative AI, enriched threat intelligence and context-aware scoring, VPR enables organizations to instantly understand vulnerability impact, weaponization and precise remediation actions.
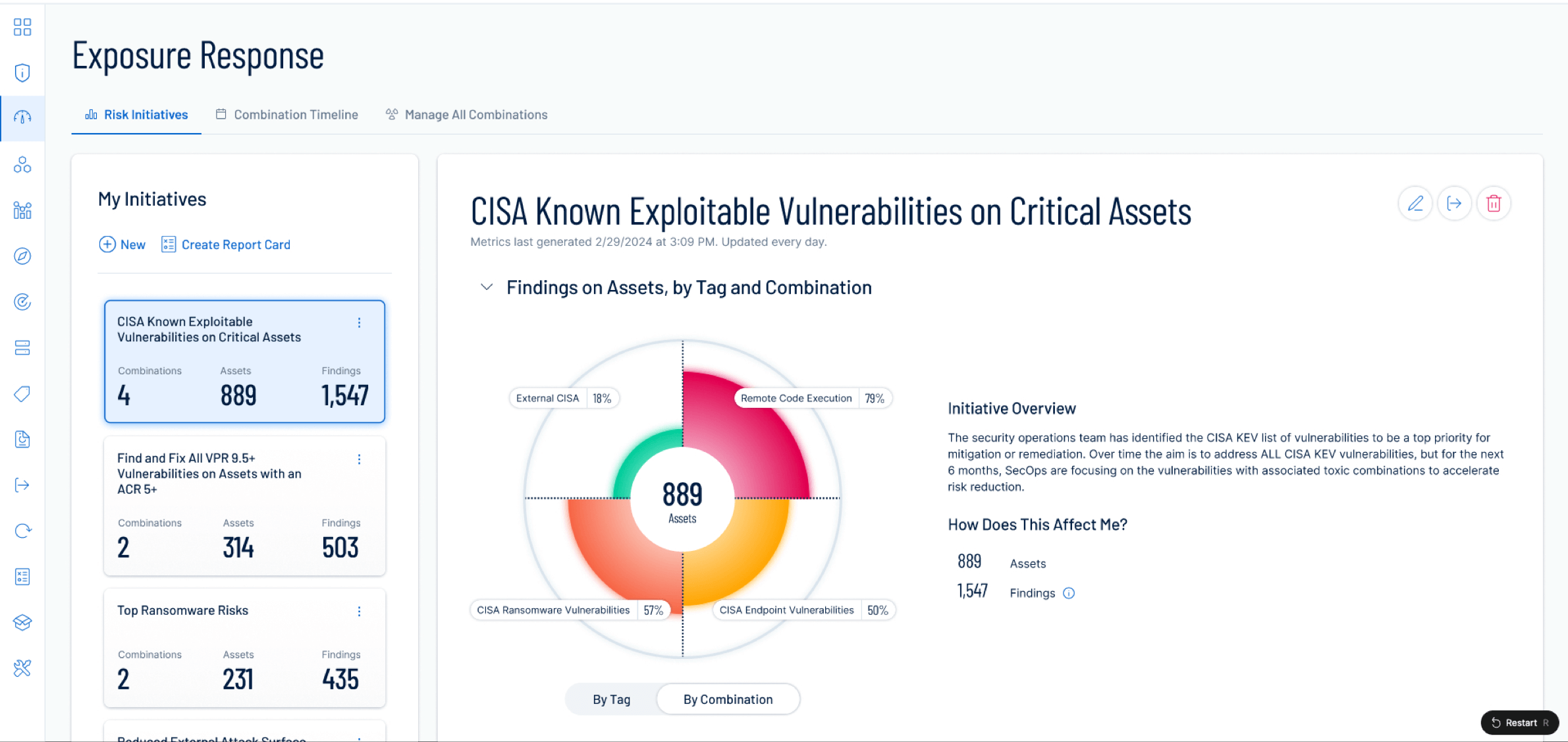
Learn moreOptimize response
Prioritize asset exposures, mobilize remediation directly with bi-directional ticketing, and benchmark progress for efficient, goal-oriented exposure management.
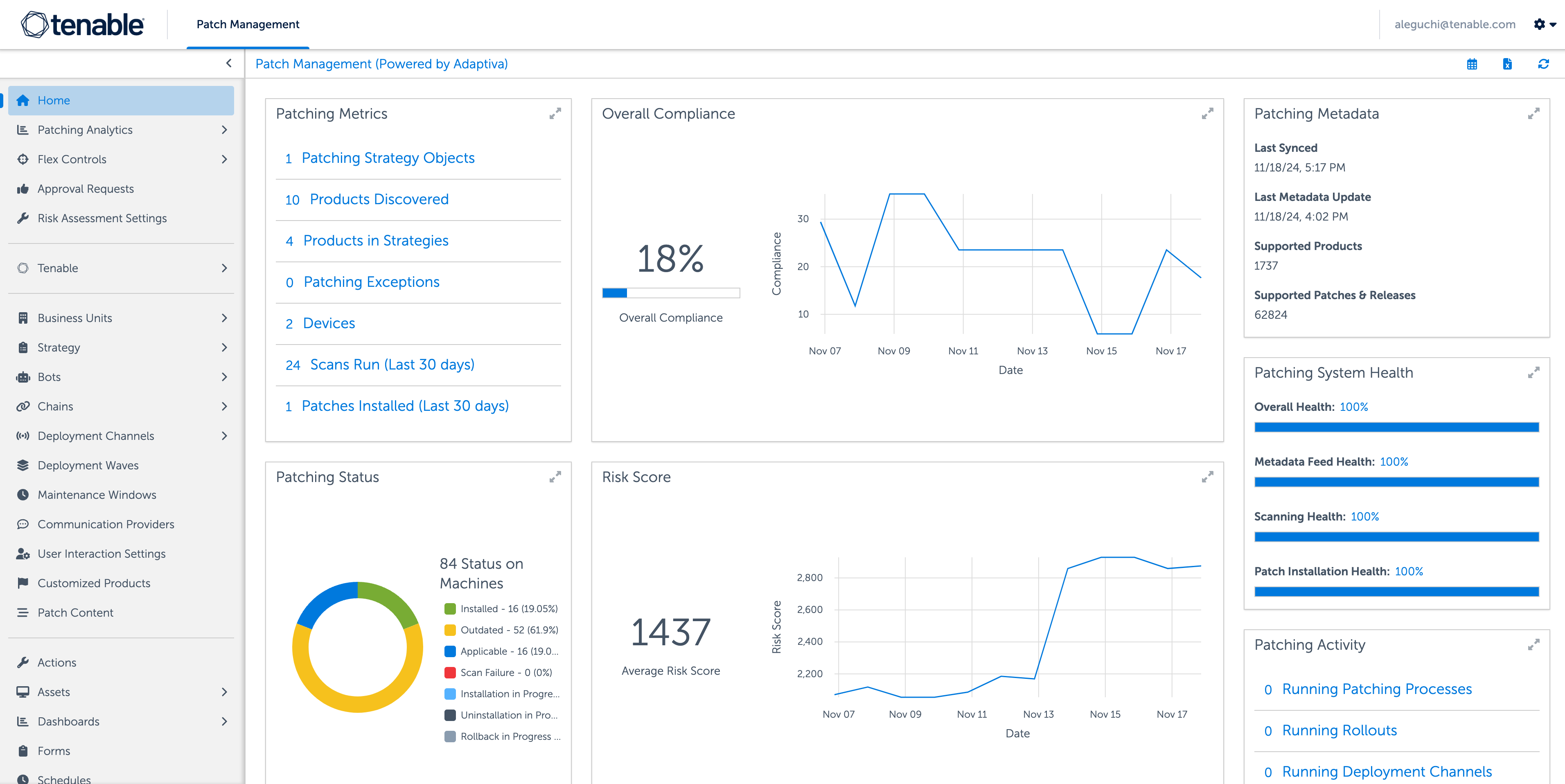
Explore moreClose your vulnerability exposure
Pair autonomous patch functionality with Tenable’s leading vulnerability coverage, built-in prioritization, threat intelligence and real-time insight to shorten the mean time to remediate (MTTR).
See howTenable Vulnerability Management reviews
Tenable is the only vendor to be named a Customers’ Choice in the 2025 Gartner® Peer Insights™ Voice of the Customer for Vulnerability Assessment

Available through Tenable One: The world’s only AI-powered exposure management platform
Tenable One solves the central challenge of modern security: a deeply divided approach to seeing and doing battle against cyber risk. We remove risk by unifying security visibility, insight and action across the attack surface to rapidly expose and close gaps. Customers use Tenable One to eradicate priority cyber weaknesses and protect against attacks—from IT infrastructure to cloud environments to critical infrastructure and everywhere in between.
Learn more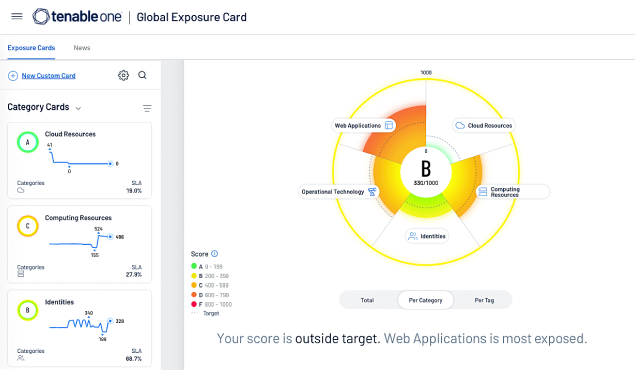
FAQs
What is Tenable Vulnerability Management?
-
Tenable Vulnerability Management is a risk-based vulnerability management platform that gives you full network visibility to predict attacks and quickly respond to critical vulnerabilities. Continuous, always-on discovery and assessment provide the visibility you need to find all assets on your network, as well as hidden vulnerabilities on those assets. Built-in prioritization, threat intelligence and real-time reporting help you understand your risk and proactively disrupt attack paths. Built on leading Tenable Nessus technology and managed in the cloud, you get complete visibility of the assets and vulnerabilities on your network so you can quickly and accurately understand your risk and know which vulnerabilities to fix first.
What is the difference between Tenable Vulnerability Management and Tenable Security Center?
-
Tenable Vulnerability Management and Tenable Security Center are both leading vulnerability management solutions that give you a comprehensive view of all the assets and vulnerabilities on your network so you can understand cyber risk and know which vulnerabilities to fix first. The key difference between the solutions is how they are managed. Tenable Vulnerability Management is managed in the cloud, while Tenable Security Center is an on-prem solution. For a comprehensive understanding of the differences between the products, contact your Tenable certified partner or Tenable representative for more information.
What is the difference between Tenable Vulnerability Management and Tenable One?
-
Tenable Vulnerability Management is available as a critical component of the Tenable One platform or as a stand-alone product. Tenable Vulnerability Management powers the Tenable One Exposure Management Platform with vulnerability management capabilities such as:
- Continuous discovery and assessment with always-on sensors
- Built-in threat intelligence
- Automated vulnerability prioritization
- Real-time visualization of risk, and tracking of vulnerabilities, assets and remediations
- Built-in vulnerability risk scores to identify risk
- Fully documented API and pre-built integrations
Tenable One is a comprehensive exposure management platform that translates technical asset, vulnerability and threat data into clear business insights and actionable intelligence for security executives and practitioners. The platform combines the broadest vulnerability coverage spanning IT assets, cloud resources, containers, web apps and identity systems, builds on the speed and breadth of vulnerability coverage from Tenable Research, and adds comprehensive analytics to prioritize actions and communicate cyber risk.
What is Tenable AI Aware?
-
Tenable AI Aware is a feature within Tenable Vulnerability Management and Tenable Security Center that helps organizations monitor and mitigate the risks associated with the rapid adoption of AI technologies. It leverages advanced detection technologies, including agents, passive network monitoring, dynamic application security testing, and distributed scan engines, to identify unauthorized AI solutions, detect AI vulnerabilities, and illuminate unexpected AI or Large Language Model (LLM) development. AI Aware provides a comprehensive security-first approach to managing AI-related risks by offering deep visibility into AI software, libraries, and browser plugins across an organization’s digital ecosystem. Learn more about Tenable AI Aware here.
What is Tenable Patch Management?
-
Tenable Patch Management is a patch management module pairing Tenable’s industry-leading prioritization capabilities with autonomous patch functionality. Automated correlation between vulnerabilities and the most up-to-date remediation action help your teams overcome the bottleneck that can occur between vulnerability prioritization and remediation. Built to scale up or down to fit any organization, Tenable Patch Management enables your organization to precisely manage settings with granularity around deployments, testing, approvals, applications and more.
To leverage Tenable Patch Management, you need a license for Tenable Vulnerability Management, Tenable Security Center, Tenable One or Tenable Enclave Security. Learn more here.
What does Tenable do to protect my data?
-
Tenable is committed to protecting the confidentiality, integrity and availability of all customer data. Tenable Vulnerability Management data is encrypted in transit and stored using TLS Encryption ciphers. AES-256 Encryption is applied to application infrastructure layers.
The Tenable cloud platform is built on isolated, private networks and uses multiple network controls such as container isolation, inbound/internal traffic restrictions, monitoring of traffic rates, sources and types at multiple network points.
Tenable also implements multiple access controls to help customers control data access, as well as performs frequent vulnerability, docker container and web application scans to conduct periodic security assessments.
For detailed descriptions of the applied security measures, review the Tenable Trust and Assurance webpage or the Data Security and Privacy data sheet.
How is Tenable Vulnerability Management priced and licensed?
-
Tenable Vulnerability Management is licensed by annual subscription and priced by asset, rather than by IP address. Our proprietary asset-counting algorithm leverages multiple asset attributes to programmatically identify unique assets to reduce duplication.
What is an asset?
-
An asset is:
- A physical or virtual device with an operating system connected to a network
- A web application with an FQDN
- An active (not terminated) cloud resource
Does Tenable offer a service level agreement (SLA) for Tenable Vulnerability Management?
-
Yes. Tenable provides the vulnerability management industry’s first uptime guarantee of 99.95% through a robust service level agreement (SLA) with service credits offered if the SLA is not met.
Tenable uses the AWS platform and other leading technologies to ensure high availability for customers. Using fault tolerant and redundant components, Tenable ensures you get the best possible service with minimal downtime.
Where can I find documentation and release notes on Tenable Vulnerability Management?
-
Technical documentation for all Tenable products, including Tenable Vulnerability Management, is at https://docs.tenable.com.
How can I learn more about Tenable Vulnerability Management?
-
To learn more about Tenable Vulnerability Management, please visit the Tenable Vulnerability Management product page, register for a free evaluation or contact your Tenable certified partner or Tenable representative for more information.
How can I purchase Tenable Vulnerability Management?
-
To purchase Tenable Vulnerability Management, you can work with your local certified partner, contact your Tenable representative or visit tenable.com.
Related products
Related resources
Get started with Tenable Vulnerability Management
We found the solution in Tenable which gives us much needed actionable insight into our entire infrastructures security risk
- Tenable Vulnerability Management
Get a demo of Tenable Vulnerability Management
Please fill out this form with your contact information. A sales representative will contact you shortly.