Cybersecurity Snapshot: Experts Issue Best Practices for Migrating to Post-Quantum Cryptography and for Improving Orgs’ Cyber Culture

Check out a new roadmap for adopting quantum-resistant cryptography. Plus, find out how your company can create a better cybersecurity environment. In addition, MITRE warns about protecting critical infrastructure from cyber war. And get the latest on exposure response strategies and on CISO compensation and job satisfaction.
Dive into five things that are top of mind for the week ending June 6.
1 - Group releases roadmap for adopting post-quantum cryptography
Is your organization looking for guidance on how to carry out its migration to post-quantum cryptography (PQC)? A group that includes MITRE, Microsoft and IBM just released a roadmap designed to help organizations plan and execute their adoption of PQC.
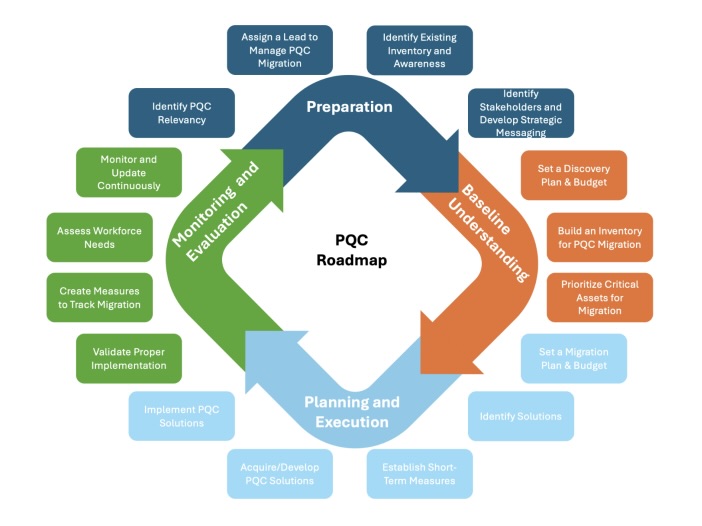
Titled “Post-Quantum Cryptography (PQC) Migration Roadmap,” the 20-page document from the “Post Quantum Cryptography Coalition” breaks down PQC migrations into four major stages:
- Preparation, which includes identifying the transition’s main goals, assigning a project leader and identifying key stakeholders
- Baseline understanding, which includes a comprehensive inventory of the data and assets to be protected, as well as determining required resources and budgets
- Planning and execution, which includes collaboration with internal and external partners to either acquire or develop the necessary tools for the migration
- Monitoring and evaluation, which includes establishing metrics for tracking the project’s progress and for reassessing cryptographic security, based on the evolution of quantum capabilities
"This roadmap empowers CIOs and CISOs to act decisively, taking proactive steps to protect sensitive data now and in the future,” Wen Masters, MITRE’s VP of cyber technologies, said in a statement.
Transitioning to PQC, also known as quantum-resistant cryptography, is a complex process that’s expected to take the typical enterprise multiple years to complete and, as such, it will require exacting planning and ultra-precise execution.
Embarking on the process to adopt PQC is necessary because when quantum computers become generally available — expected to happen at some point between 2030 and 2040 — they’ll be able to crack today’s public key cryptographic algorithms, which protect all types of digitally stored and transmitted data
Algorithms for quantum-resistant encryption are already available. The U.S. National Institute of Standards and Technology (NIST) released three quantum-resistant algorithm standards in 2024 and expects to release a fourth in 2026. There’s another PQC standard called Covercrypt from the European Telecommunications Standards Institute (ETSI). Earlier this year, NIST picked its fifth PQC algorithm, expected to be available for use in 2027.
Other resources designed to help organizations with PQC adoption include NIST’s white paper “Considerations for Achieving Crypto Agility” and the U.K. National Cyber Security Centre’s (NCSC) “Timelines for migration to post-quantum (PQC) cryptography.”
For more information about how to protect your organization against the quantum computing cyber threat:
- “How to achieve crypto-agility and future-proof security” (TechTarget)
- “Moody’s sounds alarm on quantum computing risk, as transition to PQC ‘will be long and costly’” (Industrial Cyber)
- “Post-quantum cryptography migration use cases” (IETF)
- “US unveils new tools to withstand encryption-breaking quantum. Here's what experts are saying” (World Economic Forum)
- “You need to prepare for post-quantum cryptography now. Here’s why” (SC World)
- “Quantum and the Threat to Encryption” (SecurityWeek)
2 - How to establish a great cybersecurity culture in your org
Corporate culture can have a major impact on the success or failure of a company’s cybersecurity efforts. So how do you create an organizational environment that boosts cybersecurity?
That’s the question the U.K. National Cyber Security Centre (NCSC) tackled with the publication this week of its “Cyber security culture principles” guidance. The document unpacks six core recommendations aimed at getting the staff to embrace cybersecurity processes.
“The principles describe cultural conditions that are essential underpinnings for an organisation to be cyber secure and offer an approach to developing that culture,” reads an NCSC blog.

Here’s a high-level view of three of these principles:
- Frame cyber as an enabler: Foster a sense that cybersecurity is everyone’s responsibility by clearly positioning it as a “shared purpose.” Demonstrate how cybersecurity isn’t a barrier to but rather a facilitator for achieving business goals.
- Encourage openness: Make it easy for employees to report security issues and to ask questions. Investigate issues fairly and transparently, with the goal of fixing problems and sharing lessons learned, as opposed to affixing blame.
- Embrace change: Stay attuned to emerging cyber risks and be ready to modify cybersecurity processes accordingly. Show how this capacity to adapt to new cyber threats helps strengthen the organization’s resilience.
For more information about creating a healthy cybersecurity culture in your organization:
- “How to Create an Enterprise-Wide Cybersecurity Culture” (Information Week)
- “A new age of cybersecurity culture” (KPMG)
- “Signs Your Organization's Culture Is Hurting Your Cybersecurity” (Dark Reading)
- “How to turn around a toxic cybersecurity culture” (CSO)
- “Creating a Culture of Cybersecurity Awareness” (IT Executives Council)
VIDEO
Improve Your Cyber Security Culture (SANS Institute)
3 - MITRE: U.S. critical infrastructure must be ready for cyber war
In addition to preventing and mitigating standalone cyber threats and attacks, U.S. critical infrastructure organizations must have a plan in case a lengthy, widespread cyber war breaks out.
That’s the call from MITRE, which has published a fact sheet with key actions for getting critical infrastructure organizations ready for an all-out cyber conflict that disrupts multiple essential services for a sustained period of time.
Titled “5 Steps To Prepare Critical Infrastructure for a Cyber War,” the document is aimed at critical infrastructure operators; federal, state and local governments; businesses; and communities.

The fact sheet is based on a classified tabletop exercise held at MITRE’s headquarters in December in which 70 government and private-sector organizations participated in a simulated cyber war.
“The event revealed the urgent need for infrastructure owners/operators, government agencies, and communities to shift from addressing isolated cyber incidents to preparing for large-scale cyber conflicts lasting weeks to months,” the document reads.
Here are five steps MITRE views as necessary for critical infrastructure organizations to get ready for a cyber war scenario:
- Create a civil defense mindset: Make citizens aware that basic services like electricty, water, telecom and transportation may be impacted. Stakeholders should plan how to issue emergency responses and how to prioritize restoration efforts.
- Manage limited resources: Critical infrastructure operators should test their incident response plans, while governments must plan with businesses how to address service outages.
- Plan to operate under extreme conditions: Recovering from the impacts of cyber war requires planning for coping with devastating outages that last weeks. Measures should include training staff for manual, disconnected operations, and boosting cyber resilience.
- Strengthen emergency communications systems: Develop communication systems and processes that’ll withstand a cyber war’s disruptions, along with ways to authenticate the identity of those involved.
- Ensure workforce readiness: Because the workforce will likely shrink during a cyber war emergency, contingency plans should be made to operate with a smaller staff, including training workers for this scenario.
Full details about the tabletop exercise are available to U.S. critical infrastructure owners and operators, as well as to government agencies. Those interested can request access by writing to this email address: [email protected].
For more information about cyber warfare:
- “Preparing for Cyber Warfare: 6 Key Lessons From Ukraine” (Dark Reading)
- “Cyberwarfare: The new frontlines” (Cybersecurity Guide)
- “‘Russia can turn the lights off’: how the UK is preparing for cyberwar” (The Guardian)
- “The Growing Threat of Cyberwarfare from Nation-States” (PaymentsJournal)
- “Russia’s Most Notorious Special Forces Unit Now Has Its Own Cyber Warfare Team” (Wired)
4 - Tenable webinar poll spotlights exposure response strategies
During our recent “Tenable Vulnerability Management Customer Update, June 2025” webinar, we polled attendees on their exposure response strategies and challenges. Check out what they said.
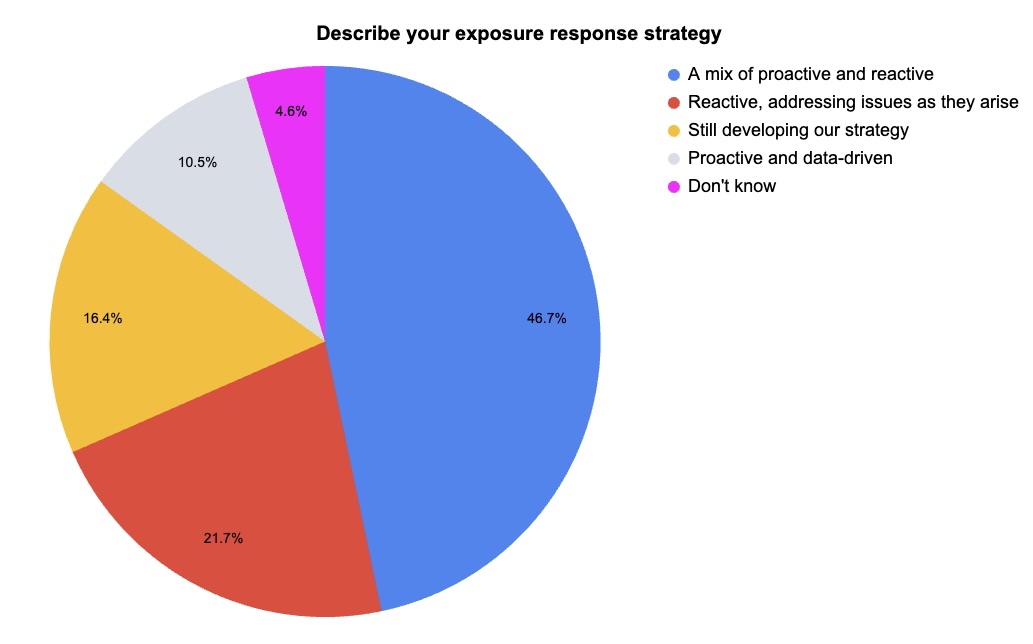
(152 webinar attendees polled by Tenable, June 2025)
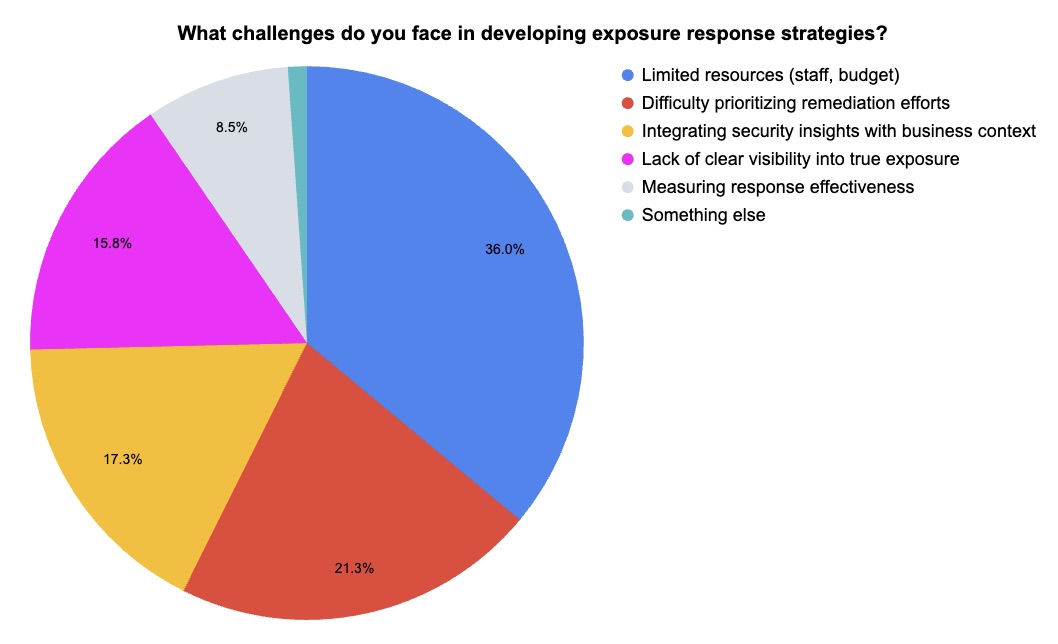
(145 webinar attendees polled by Tenable, June 2025. Respondents could choose more than one answer.)
Watch this on-demand webinar to get the latest on Tenable Vulnerability Management and to learn how to develop exposure response strategies.
5 - Despite high salaries, many CISOs at large orgs are dissatisfied
With median salaries north of $500,000 and top earners making $1.3 million-plus annually, CISOs at large enterprises are making bank, but, ironically, job dissatisfaction among them is high.
That’s according to the “2025 Compensation and Budget for CISOs in Large Enterprises Benchmark Report” from IANS Research and Artico Search, which also found that a large percentage of these CISOs are actively looking for new jobs.
“Large enterprise CISOs might be among the highest paid across industries, yet our report reveals that many CISOs feel stretched too thin, and low job satisfaction keeps them open to new opportunities,” reads an IANS Research blog about the report.
Specifically, many of these CISOs are unhappy with their team’s budget and, to a lesser extent with their compensation. It’s also common for them to struggle broadening their focus from overseeing cybersecurity technology to supporting business initiatives.
“When elevating an enterprise CISO role, the position is less about technical acumen and more about business risk and business alignment,” Matt Comyns, Artico Search co-founder and president, said in the blog.
“In some respects, the market is training technical leaders in a way that is mismatched from the aspired job of CISO,” he added.
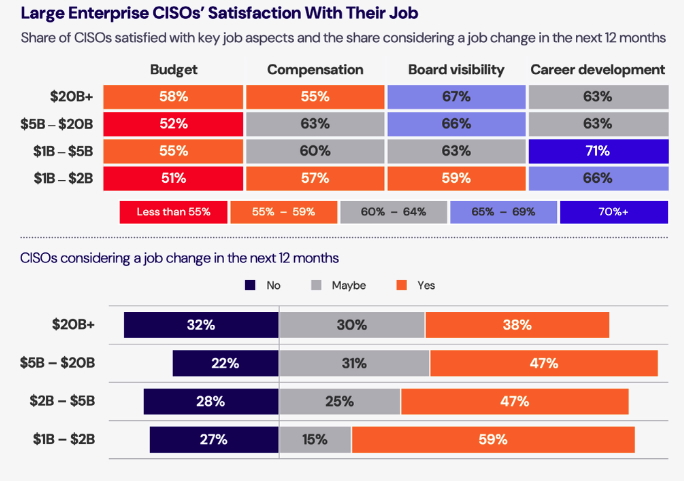
(Source: “2025 Compensation and Budget for CISOs in Large Enterprises Benchmark Report” from IANS Research and Artico Search, May 2025)
The report defines these CISOs as those who work at enterprises with more than $1 billion in revenue. They make an average of about $700,000 in total compensation annually.
For more information about CISO trends:
- “Why Security Leaders Are Opting for Consulting Gigs” (Dark Reading)
- “CISO Burnout Is Increasing — Here’s How to Help Them” (Reworked)
- “CISO Paychecks: Worth the Growing Security Headaches?” (Dark Reading)
- “Has the CISO finally been accepted as a key strategic player?” (Deloitte)
- “CISOs in 2025: Evolution of a High-Profile Role” (Information Week)
- Cloud
- Cybersecurity Snapshot
- Exposure Management
- Exposure Response
- Federal
- Government
- Incident Response
- NIST
- OT Security
- Recruiting
- SANS
- Security Frameworks
- Security Policy
- Threat Management



