CVE-2025-31324: Zero-Day Vulnerability in SAP NetWeaver Exploited in the Wild

SAP has released a out-of-band patch to address CVE-2025-31324, a critical zero-day vulnerability in SAP NetWeaver that has been exploited by threat actors. Organizations are strongly encouraged to apply patches as soon as possible.
Update May 21: The blog has been updated to include additional information including CVE-2025-42999, the availability of PoC code and updates on active exploitation.
Background
On April 22, ReliaQuest published details of their investigation of exploit activity in SAP NetWeaver servers. Initially it was unclear if their discovery was a new vulnerability or the abuse of CVE-2017-9844, a vulnerability that could lead to a denial-of-service (DoS) condition or arbitrary code execution. ReliaQuest reported their findings to SAP and on April 24, SAP disclosed CVE-2025-31324, a critical missing authorization check vulnerability with the highest severity CVSS score of 10.0.
On May 13, SAP released an additional update for a newly reported CVE affecting SAP NetWeaver servers as part of its May 2025 SAP Security Patch Day.
| CVE | Description | CVSSv3 | VPR |
|---|---|---|---|
| CVE-2025-31324 | SAP NetWeaver Unauthenticated File Upload Vulnerability | 10.0 | 9.4 |
| CVE-2025-42999 | SAP NetWeaver Deserialization of Untrusted Data Vulnerability | 9.1 | 9.2 |
*Please note: Tenable’s Vulnerability Priority Rating (VPR) scores are calculated nightly. This blog post was updated on May 21 and reflects VPR at that time.
Analysis
CVE-2025-31324 is an unauthenticated file upload vulnerability affecting the Metadata Uploader component of SAP NetWeaver Visual Composer. Successful exploitation of this vulnerability could allow an unauthenticated attacker to upload malicious files which can be used by an attacker to achieve code execution. The flaw is the result of missing authorization checks to the “/developmentserver/metadatauploader” endpoint. According to ReliaQuest, this vulnerability has been exploited in the wild as a zero-day by threat actors who have abused the flaw to upload malicious web shells to affected hosts. These webshells were used to deploy malware and establish communications with command and control (C2) servers.
CVE-2025-42999 is a deserialization vulnerability affecting SAP NetWeaver Visual Composer development server. An authenticated attacker could exploit this vulnerability to achieve code execution on affected hosts. The vulnerability was identified by researchers at Onapsis who were able to reconstruct attack payloads during their investigation of the CVE-2025-31324. They reported CVE-2025-42999 to SAP and the vulnerability was patched during the May 2025 SAP Security Patch Day release. According to Onapsis, this vulnerability remained an underlying issue for exploitation and was not addressed in the update for CVE-2025-31324.
Exploitation in the wild has continued to increase
Based on several reports released since this blog was first published, several advanced persistent threat (APT) groups and ransomware groups have been observed actively exploiting CVE-2025-31324.
Proof of concept
At the time this blog was published, no proof-of-concept (PoC) code had been published for CVE-2025-31324. However, shortly after this blog was posted, several scanning tools and PoCs have been released on GitHub.
Solution
SAP has released patches for affected versions of SAP NetWeaver. At this time, the SAP security note #3594142 is not publicly accessible, so we are unable to provide a list of affected and patched versions. It is important to note that these patches were released after SAP’s April 2025 Security Patch Day published on April 8. So even if those patches were applied, you will still need to apply the out-of-band patches released for CVE-2025-31324.
In addition, SAP released security note #3604119 on May 13 to address CVE-2025-42999. To be fully protected from these vulnerabilities, we recommend that you apply both updates and refer to the SAP security patches for further information.
Identifying affected systems
A list of Tenable plugins for these vulnerabilities can be found on the individual CVE pages for CVE-2025-31324 and CVE-2025-42999 as they’re released. These links will display all available plugins for these vulnerabilities, including upcoming plugins in our Plugins Pipeline.
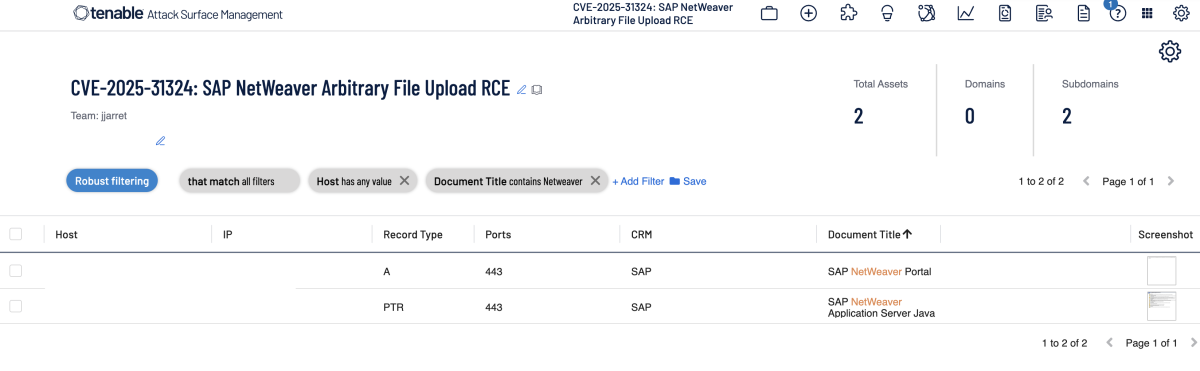
Additionally, customers can utilize Tenable Attack Surface Management to identify public facing assets running SAP NetWeaver by using the following filters:
Get more information
- ReliaQuest Blog: ReliaQuest Uncovers New Critical Vulnerability in SAP NetWeaver
- SAP Security Patch Day - April 2025
- SAP Security Patch Day - May 2025
- Onapsis Blog: SAP NetWeaver Flaw Lets Threat Actors Take Full Control: CVE-2025-31324 and CVE-2025-42999 Explained
Change Log
Update May 21: The blog has been updated to include additional information including CVE-2025-42999, the availability of PoC code and updates on active exploitation.
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
- Exposure Management
- Vulnerability Management



