CVE-2021-21148: Google Chrome Heap Buffer Overflow Vulnerability Exploited in the Wild

Following reports of in-the-wild exploitation, Google released a patch for the third browser-based zero-day vulnerability of 2021.
Background
On February 4, Google published a stable channel update for Chrome for Desktop. This release contained a single security fix to address a critical zero-day vulnerability that had been exploited in the wild.
Analysis
CVE-2021-21148 is a heap buffer overflow vulnerability in V8, Google Chrome’s open-source JavaScript and WebAssembly engine. Its discovery is credited to Mattias Buelens, who reported the flaw to Google on January 24. As part of this release, Google notes that they are “aware of reports that an exploit” for this vulnerability “exists in the wild,” which we interpret to mean that in-the-wild exploitation attempts have been observed.
In-the-wild vuln in Chrome just fixed. CVE-2021-21148 https://t.co/PRtcxAXn8p
— Maddie Stone (@maddiestone) February 5, 2021
A detailed bug report for the vulnerability is unsurprisingly restricted at this time in order to allow users time to apply the relevant patch.
Third browser-based zero-day vulnerability disclosed in 2021
CVE-2021-21148 is the third zero-day vulnerability we’ve observed to be browser-based in 2021. In late January, Apple released iOS and iPadOS 14.4, which contained fixes for two WebKit zero-day vulnerabilities (CVE-2021-1870, CVE-2021-1871) that were exploited in the wild.
In our 2020 Threat Landscape Retrospective report, we noted that the majority of zero-day vulnerabilities disclosed in 2020 were browser-based, accounting for over 35%.
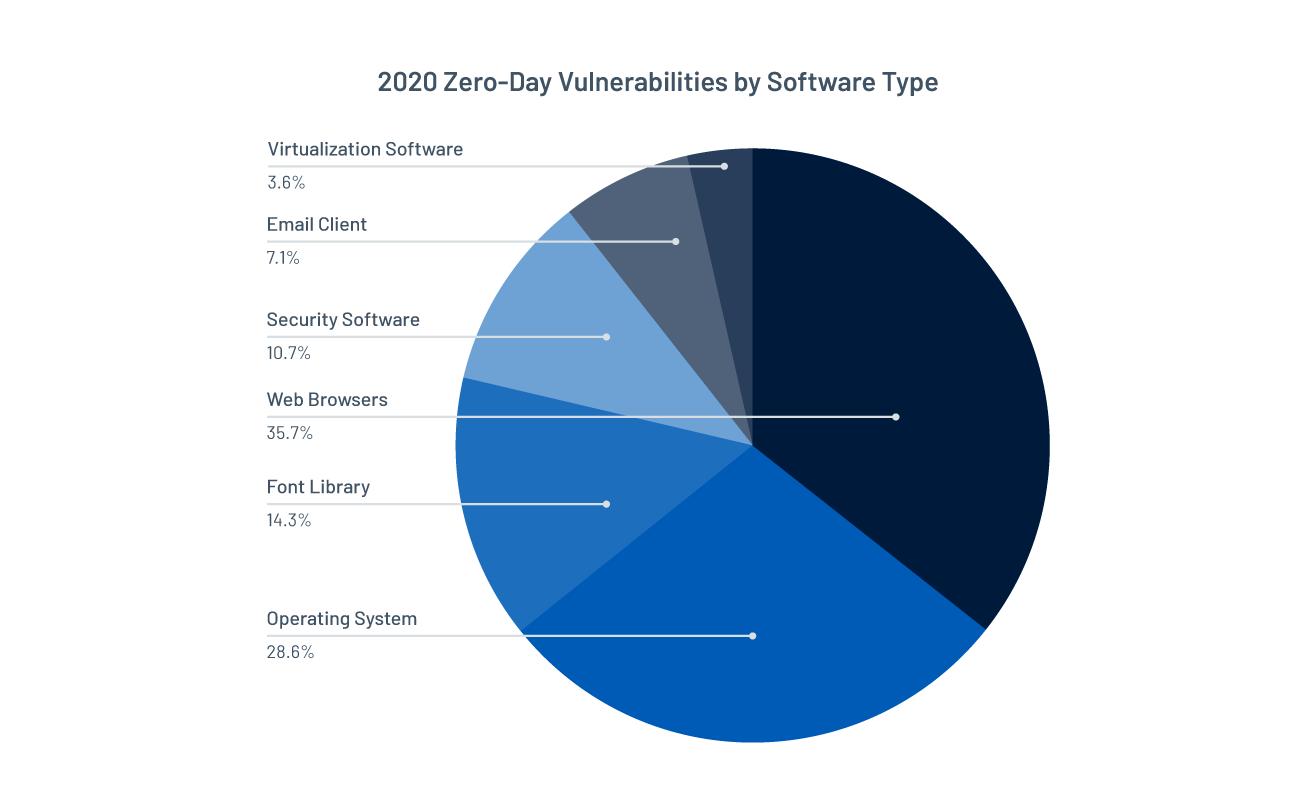
Source: Tenable’s 2020 Threat Landscape Retrospective
In 2020, Google patched three Chrome zero-day vulnerabilities in the V8 engine that were exploited in the wild, two of which were patched within two weeks of each other:
| CVE | Vulnerability Type | Patch Date |
|---|---|---|
| CVE-2020-6418 | Type Confusion | February 24, 2020 |
| CVE-2020-16009 | Inappropriate Implementation | November 2, 2020 |
| CVE-2020-16013 | Inappropriate implementation | November 11, 2020 |
Based on our observations in 2020, we anticipate this trend in browser-based zero-day vulnerabilities will remain consistent in 2021, as browsers remain a popular attack vector for cybercriminals.
Speculation surrounding timing of vulnerability disclosure
In a bit of interesting timing, CVE-2021-21148 was disclosed to Google just one day prior to a massive revelation from Google. On January 25, Google’s Threat Analysis Group published a blog post detailing the discovery of an ongoing campaign conducted by nation-state actors to target security researchers interested in collaborating on vulnerability research. The report specifically mentions that the threat actors circulated a link to their potential victims to a malicious website that led to successful exploitation on systems that were fully patched for both Windows and Google Chrome. This was corroborated by Microsoft, which published their own blog post about the attacks, surmising that a Google Chrome zero-day was likely used to target researchers.
Naturally, speculation has emerged that there may be a connection between these attacks and the disclosure of CVE-2021-21148. However, so far, we’ve not seen any definitive connection made between the two. Maddie Stone, a security researcher on Google’s Project Zero team, has requested anyone to share any additional details about CVE-2021-21148.
Proof of concept
Despite reports of in-the-wild exploitation for CVE-2021-21148, we have found no public proof-of-concept code at the time this blog post was published.
Solution
Google addressed CVE-2021-21148 in Google Chrome version 88.0.4324.150 for Windows, macOS and Linux clients. Updated versions for most desktop systems should be available, while others (particularly Linux-based releases) should become available in the near future.
Identifying affected systems
A list of Tenable plugins to identify this vulnerability can be found here.
Get more information
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management



