Cr8escape: How Tenable Can Help (CVE-2022-0811)

CrowdStrike discloses container escape vulnerability affecting CRI-O for Kubernetes. Here’s how Tenable.cs can help you detect vulnerable pods.
Background
On March 15, CrowdStrike published technical details and a proof-of-concept for CVE-2022-0811, a vulnerability they have named cr8escape, in the CRI-O Container Engine for Kubernetes. CRI-O is an open source container runtime engine that is used to share kernel resources among applications running on a container node. There have not been any reported exploitations in the wild of this vulnerability at the time of publication.
CrowdStrike identified Red Hat’s OpenShift 4+ and Oracle Container Engine for Kubernetes as two products that integrate CRI-O and warns that other software and platforms may deploy the engine by default.
Analysis
CVE-2022-0811 is a container escape vulnerability in CRI-O that can lead to elevation of privileges. According to CrowdStrike, this vulnerability was introduced in CRI-O version 1.19 and allows an attacker to bypass the standard security controls that typically prevent one pod from changing the kernel parameters of others, allowing them to set arbitrary kernel parameters to the host.
An attacker with “rights to deploy a pod on Kubernetes cluster that uses the CRI-O runtime” could elevate their privileges and potentially execute code on other nodes in the cluster with root permissions. This could further allow the attacker to spread malware or exfiltrate sensitive data, making it a useful flaw for ransomware groups in particular.
Proof of concept
As part of their technical write up, CrowdStrike walked through a proof of concept that exploits CVE-2022-0811 to execute malware.
Solution
The vulnerability was introduced in CRI-O version 1.19 in September 2020 and impacts all versions since. On March 15, version 1.22.3 was released to address CVE-2022-0811. Both Oracle and Red Hat have deployed the fixed version as part of updates to Oracle Linux and OpenShift.
How Tenable.cs can help
To exploit this vulnerability on clusters running vulnerable versions of CRI-O, an attacker has to create a pod with a ‘sysctl’ containing “+” or “=” in the value.
Tenable.cs can help you detect such misconfigurations in your Kubernetes clusters by scanning your infrastructure as code (manifests, helm, or kustomize), as well as your runtime cluster.
Tenable.cs uses policy as code (open policy agent Rego) to find the misconfigurations in all your cluster workloads. Let’s take a look at the code that helps detect this misconfiguration.
Before CVE-2022-0811 was reported, Tenable.cs was already scanning your workloads against kernel level syscalls. The policy to check for these misconfigurations looks like this:
kernelLevelSysCalls[pod.id] {
pod := input.kubernetes_pod[_]
forbiddenSysctls = ["kernel.*"]
sysctl := pod.config.spec.securityContext.sysctls[_].name
forbidden_sysctl(sysctl, forbiddenSysctls)
}
forbidden_sysctl(sysctl, arg) {
arg[_] == sysctl
}
forbidden_sysctl(sysctl, arg) {
startswith(sysctl, trim(arg[_], "*"))
}
In the above policy, we are checking for the name of sysctl if it includes “kernel.” However, to detect CVE-2022-0811, we have added another policy which will first verify for kernel level calls through name as in the above policy, then it will check for the value in the sysctl and alert you if it contains [“=”, “+”].
{{.prefix}}{{.name}}{{.suffix}}[pod.id] {
pod := input.kubernetes_pod[_]
forbiddenSysctls = ["kernel.*"]
sysctl := pod.config.spec.securityContext.sysctls[_].name
forbidden_sysctl(sysctl, forbiddenSysctls)
disAllowedValues := ["=", "+"]
sysctlValue := pod.config.spec.securityContext.sysctls[_].value
contains(sysctlValue, disAllowedValues[_])
}
Note: The above policies are an example used just for kubernetes pods, Tenable.cs can scan the same for all different kinds of workloads, such as, Deployment/ReplicaSet/DaemonSet etc.
Now, let’s look at the Tenable.cs results for the scan of the pod used by CrowdStrike in its proof of concept.
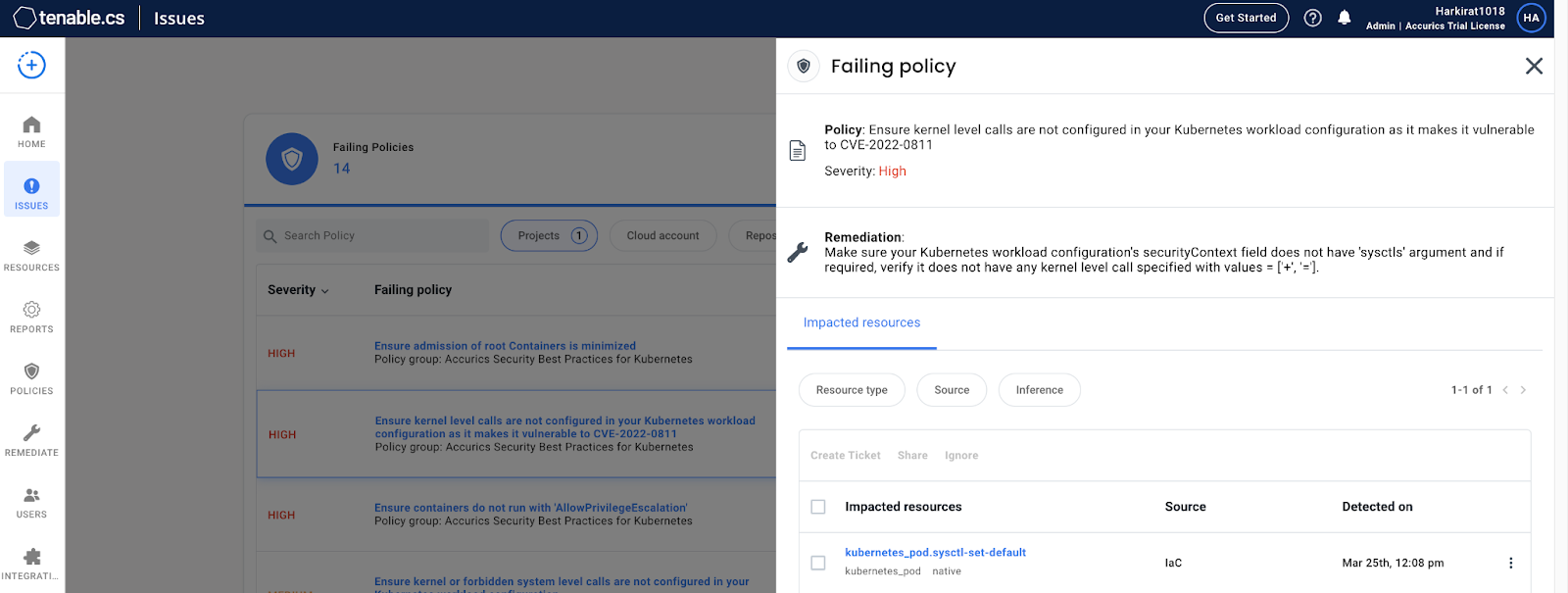
Tenable.cs provides an issues tab with all the violations specific to the infrastructure one has scanned. The screenshot above shows the results of a failed CVE-2022-0811 policy check in Tenable.cs. For every violation, Tenable.cs provides technical details and remediation advice.
Identifying affected systems
A list of Tenable plugins to identify this vulnerability can be found here.
Get more information
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Cloud
- Vulnerability Management



