Are you Vulnerable to the IPv6 SLAAC Attack?
Recently, Neohapsis published a tool named “Sudden Six” to test if your network is vulnerable to the Stateless Address Auto Configuration (SLAAC) attack. The tool leverages latent IPv6 connectivity that may be present in your IPv4 networked devices to alter the flow of traffic for collection and potential modification for targeted attacks.
Nessus supports discovery of IPv6 interfaces during IPv4 scans. If you have IPv6 connectivity supported on an IPv4 network, you are likely vulnerable to SLAAC attacks unless you have layered firewalls and routers that prevent IPv6 communication. The following Nessus plugins support IPv6 interface enumeration:
- 25202 – Enumerate IPv6 Interfaces via SSH
- 24272 – Network Interfaces Enumeration (WMI)
- 45405 – Reachable IPv6 address
In addition to these checks, the Passive Vulnerability Scanner (PVS) supports native discovery of IPv6 addresses. When combined with active Nessus IPv6 scans, PVS provides a very powerful IPv6 monitoring tool.
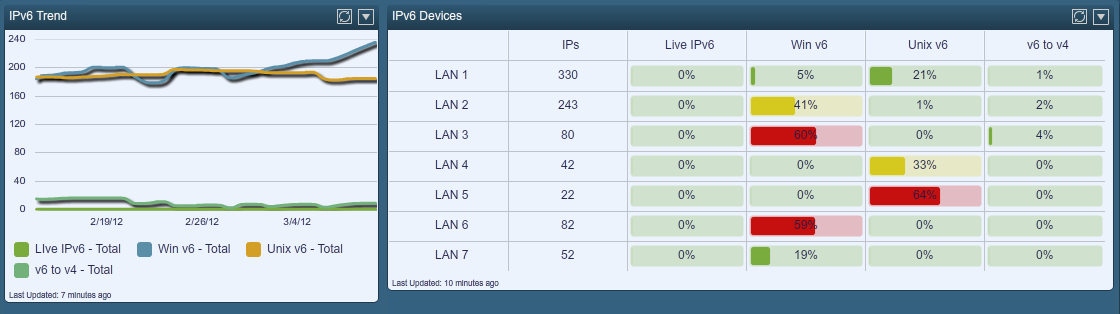
Many Tenable customers perform active and passive IPv6 monitoring with the SecurityCenter Continuous View solution. They leverage real-time dashboards and reports, such as the “IPv4 Systems with IPv6 Interfaces and Addresses” dashboard shown below.
To learn more about Tenable’s IPv6 monitoring solutions, please watch one of our recorded webinars on the topic, or read more about our Continuous View solution which supports real-time scanning and sniffing of IPv6 systems and vulnerabilities.