by Andrew Freeborn
December 2, 2015
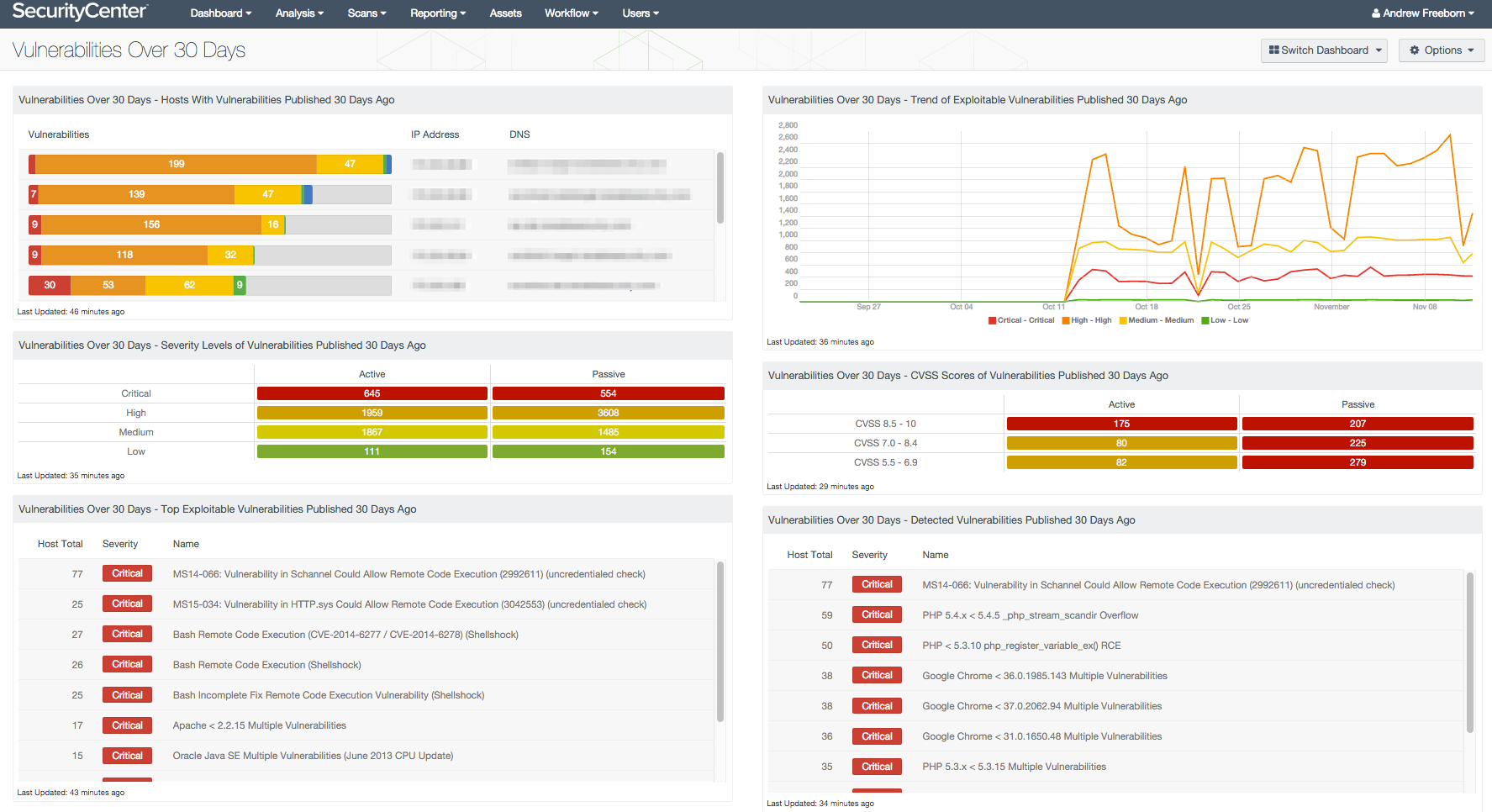
Many organizations have a difficult time keeping software completely up to date with patches due to the frequency in which they are released. Outstanding vulnerabilities can be exploited by attackers, which can result in business outages or loss of revenue. This dashboard identifies hosts in the organization with vulnerabilities published more than 30 days ago.
Despite best intentions, not all vulnerabilities are patched on a constant basis throughout the organization. For example, analysts may find vulnerabilities through active scanning or passive monitoring, but may not have the immediate resources or time to address the issues found. Vulnerabilities increase risk to the organization and could be responsible for business outages, data leakage, or loss of revenue without remediating the issues. Having this dashboard helps to keep analysts informed of vulnerabilities in the environment that have been published more than 30 days ago. Not only are vulnerabilities present in the organization listed, but analysts also get detailed information about the vulnerabilities and how to remediate the issues found. From this information, analysts can work with administrators to quickly remediate the vulnerabilities and reduce the risk in the organization.
As this dashboard can provide a comprehensive view of vulnerabilities on the network, information is provided in different views. A count of hosts with vulnerabilities is helpful, but may not help prioritize efforts for remediation. Analysts can quickly see the vulnerabilities that are exploitable, have a high CVSS rating, or affect a large number of hosts. Resources can be better utilized when they are effectively remediating hosts in the organization by using a risk-focused approach.
This dashboard combines active scanning capabilities provided by Nessus and passive monitoring capabilities provided by the Nessus Network Monitor (NNM). Organizations may not be able to continually scan the complete environment with Nessus for reasons such as limited access to remote networks or internal scan policies. These scenarios may offer a way for Nessus Agents to assist in this regard by providing vulnerability information to Tenable.sc. Using Nessus Agents along with active scanning and passive monitoring can help organizations focus on remediating vulnerabilities regardless of the organizational structure.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Threat Detection & Vulnerability Assessments. The dashboard requirements are:
- Tenable.sc 4.8.2
- Nessus 6.4.3
- NNM 4.4.0
Tenable provides continuous network monitoring to identify vulnerabilities, reduce risk and ensure compliance. Our family of products includes Tenable.sc Continuous View (CV), Nessus and NNM. Tenable.sc CV performs log normalization from hundreds of unique data sources. Nessus is the global standard in detecting and assessing network data. NNM provides deep packet inspection to continuously discover and track users, applications, cloud infrastructures, trust relationships, and vulnerabilities.
This dashboard contains the following components:
- Hosts With Vulnerabilities Published 30 Days Ago: The Hosts With Vulnerabilities Published 30 Days Ago component displays a list of hosts with detected vulnerabilities that have been published over 30 days ago
- Severity Levels of Vulnerabilities Published 30 Days Ago: The Severity Levels of Vulnerabilities Published 30 Days Ago component provides an overview of both active and passive vulnerabilities detected in the environment
- Top Exploitable Vulnerabilities Published 30 Days Ago: The Top Exploitable Vulnerabilities Published 30 Days Ago component displays a listing of vulnerabilities with publicly available exploits that have been published over 30 days ago
- Trend of Exploitable Vulnerabilities Published 30 Days Ago: The Trend of Exploitable Vulnerabilities Published 30 Days Ago component displays vulnerabilities over the last 50 days that have a published date of over 30 days ago
- CVSS Scores of Vulnerabilities Published 30 Days Ago: The CVSS Scores of Vulnerabilities Published 30 Days Ago component displays a matrix of both active and passive vulnerabilities grouped by CVSS score
- Detected Vulnerabilities Published 30 Days Ago: The Detected Vulnerabilities Published 30 Days Ago component displays vulnerabilities that have a published date more than 30 days ago