by Cesar Navas
November 18, 2015
Recently, the Executive Office of The President issued the Cybersecurity Strategy and Implementation Plan (CSIP) for the Federal Civilian Government. The CSIP was a result of comprehensive reviews of the Federal Government’s cybersecurity policies, procedures, and practices by a Sprint Team that was led by the Office of Management and Budget (OMB) and comprised of representatives from the National Security Council (NSC), the Department of Homeland Security (DHS), the Department of Defense (DoD), and other Federal and civilian agencies. The document, in its entirety, may be referenced here: Cybersecurity Strategy and Implementation Plan Memorandum
Three main focus points of the CSIP are:
- Strengthening government-wide processes for developing, implementing, and institutionalizing best practices.
- Developing and retaining the cybersecurity workforce.
- Working with public and private sector research and development communities to leverage the best of existing, new, and emerging technologies.
The CSIP is organized in the following manner:
- Objectives: What needs to be achieved.
- Actions: How and where to focus efforts to achieve these objectives.
The CSIP follows the central principles of the Cybersecurity Framework Core. The Framework was prepared by the National Institute of Standards and Technology (NIST) with extensive private sector input. The Core represents industry standards, guidelines, and practices, from the executive level to the operations level, that enable better management and reduction of cybersecurity risks. The Framework Core consists of five concurrent and continuous functions - Identify, Protect, Detect, Respond, and Recover. The CSIP also contains two additional functions: Human Resources and Technology.
Tenable security experts examined these and other standards and distilled the recommendations into five core controls that make it easy to draw from the industry’s best practices. By adopting the Tenable Critical Cyber Controls, organization’s strengths and weaknesses can easy be highlighted, allowing action to be taken to prevent malicious activity. A continuous network monitoring solution like Tenable.sc Continuous View allows organizations to leverage automation and easily detect how well these basic security controls are being performed.
Many Tenable.sc dashboards, reports, and ARCs are designed with Tenable’s core controls and other industry standards as the basis for vulnerability reporting. These Tenable.sc components allow analysts and executives to monitor the effectiveness of the organization’s IT security controls continuously.
The first objective of the CSIP prioritizes identification and protection of high-value information and assets. To protect Federal Government information and assets, agencies must first identify the value and impact of the information on their systems and networks. Agencies must also identify the IT assets used to store, process, and transmit that information. Furthermore, agencies must identify those assets and capabilities that enable mission essential functions and ensure delivery of critical services to the public.
Accordingly, the Office of Management and Budget (OMB) directed agencies to initiate processes to identify their High Value Assets (HVAs). Agencies are to review and improve the security practices and controls around their HVAs. To assist agencies with this process, a working definition of a “high value asset”, and a list of attributes to consider when determining whether an asset, dataset, or repository is of high value were developed. Federal Information Processing Standard (FIPS) 199, Standards for Security Categorization of Federal Information and Information Systems, also provides relevant guidance and requires Federal agencies to categorize their information and information systems to determine the worst-case adverse impact to operations, assets, individuals, other organizations, and the Nation if their information or systems are compromised. The effort to identify HVAs builds on FIPS 199 and seeks to implement lessons learned from cyber incidents involving personally identifiable information (PII) by asking agencies to give special consideration to the capability, intent, and specific targeting of high value data repositories by potential or actual adversaries.
Tenable’s first critical cyber control aims to track the authorized inventory of hardware and software. Discovery of all assets is a critical first step. This step includes the identification of all authorized or unauthorized hardware and software, transient devices and applications, unknown endpoints, BYOD devices, network devices, platforms, operating systems, virtual systems, and cloud applications and services. The optimum solution should include a combination of automated discovery technologies running in near real time.
Tenable addresses this critical first step with the following dashboards and ARCs:
- CSIP Asset Discovery Dashboard
- Network Mapping Dashboard
- Cybersecurity Framework Audit Summary Dashboard
- Cybersecurity Asset Management Dashboard
- CCC 1: Maintain an Inventory of Software and Hardware
Utilizing these components helps the organization to better understand, manage, and reduce its cybersecurity risks. This/these dashboard(s) can assist organizations in determining which activities should be prioritized to maximize each dollar spent on cybersecurity risk management and improve awareness among IT analysts and executives throughout the organization.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. This dashboard can be easily located in the Tenable.sc Feed under the category Security Industry Trends. The dashboard requirements are:
- Tenable.sc 5.0
- Nessus 8.5.1
- LCE 6.0.0
- NNM 5.9.1
Tenable.sc Continuous View (CV) provides continuous network monitoring, vulnerability identification, risk reduction, and compliance monitoring. Nessus is continuously updated with information about advanced threats and zero-day vulnerabilities, and new types of regulatory compliance configuration audits. The Nessus Network Monitor (NNM) performs deep packet inspection to enable discovery and assessment of operating systems, network devices, hypervisors, databases, tablets, phones, web servers, cloud applications, and critical infrastructure. The Log Correlation Engine (LCE) performs deep log analysis and correlation to continuously discover and track systems, applications, cloud infrastructure, trust relationships, and vulnerabilities. By integrating with Nessus, NNM, and LCE, Tenable.sc CV’s continuous network monitoring is able to detect systems and vulnerabilities across the enterprise.
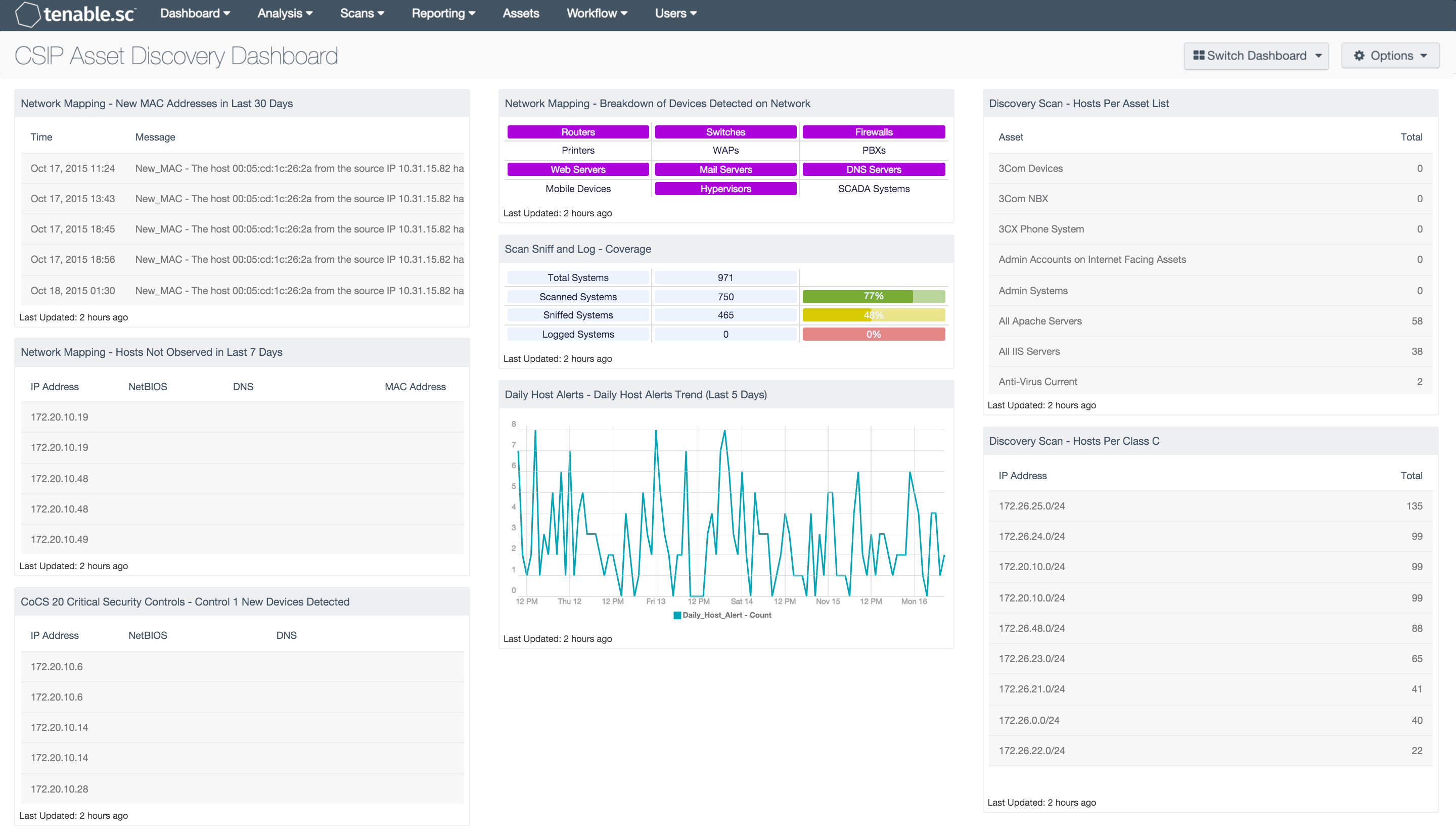
This dashboard contains the following components:
- Network Mapping - New MAC Addresses in Last 30 Days: This table lists all the new MAC addresses that have never been observed before on the network and that were first observed in the last 30 days.
- Network Mapping - Hosts Not Observed in Last 7 Days: This table lists those systems that were last passively observed on the network more than 7 days ago.
- CoCS 20 Critical Security Controls - Control 1 New Devices Detected: This component presents newly detected hosts within the last 48 hours.
- Discovery Scan - Hosts Per Class C: This table component displays live hosts across /24 network blocks.
- Network Mapping - Breakdown of Devices Detected on Network: This matrix presents a breakdown of detected network systems by type.
- Scan Sniff and Log - Coverage: This matrix presents the total number of systems, along with the total number of scanned, sniffed, or logged systems and corresponding percentages.
- Daily Host Alerts - Daily Host Alerts Trend (Last 5 Days): This component presents a line graph of Daily_Host_Alert events by time for the last 5 days.
- Discovery Scan - Hosts Per Asset List: The 'Hosts Per Asset List' table component lists the live host counts distributed across Tenable.sc assets.